Analyze Comprehensive Range of Email Types

The tool is robust enough to handle native email clients and web based email services with the same proficiency. Irrespective of the email client that is being used, be it desktop - based email client or web – based email services, the tool will discover the smoking guns for you, thus, providing the every trace of available Inculpatory Evidence.
Supported Email Categories
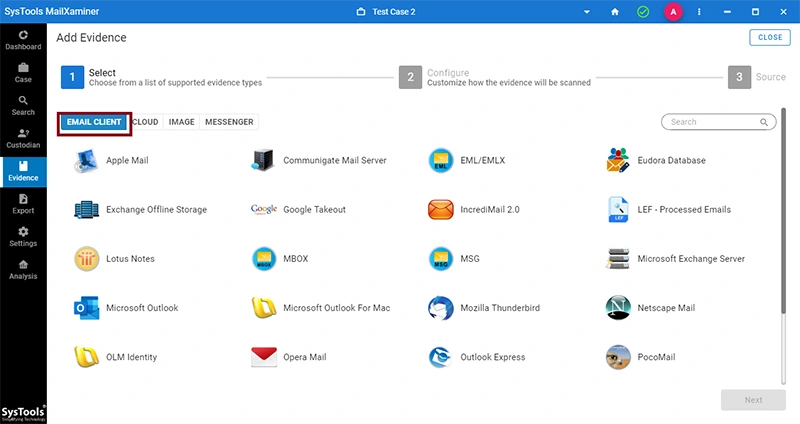
- Desktop - Based Email Formats : Outlook PST, Lotus Notes NSF, Thunderbird, Exchange Server, Sea Monkey, MBOX, The Bat, Exchange Offline Storage, Outlook Express, EML, MSG, IncrediMail 2.0, and many more.
- Web - Based Email Services : Gmail, Google Apps, Google Apps Admin, Hotmail, Live Exchange, Office365, Yahoomail, IMAP, Rackspace, iCloud and many more.
- Image Files : DD, DMG, LEF, Zip Archived file and E01 (Enacase Image File) Files.
- Messenger Data : Skype call, Chat, SMS Files (.db files).
- Bulk Mode : Through the Add file & Add folder option user can add bulk set of email files.
Add Examine Email Data Files in Bulk via MailXaminer
Analyze Native Email File Formats
File: The File tab shows various email file formats that can be thoroughly examined using the software. With the launch of the latest version of the tool, now, more than 20 renowned email file formats can be traversed and examined forensically. Some of the renowned email formats include:
- EML: EML is the standard file format used to save single email message either as a backup or for sharing. User can easily analyse and export the data EML file.
- EDB: Allows to search for email evidence from the exchange server through the analysis of Unmounted EDB file.
- PST: The Microsoft Outlook email data can be easily analyse through the direct import of PST file.
- DBX: DBX file folder is created by the Microsoft Outlook Express to save its email data corresponding to each mailbox.
- TBB: TBB is the file format used by the The Bat email client to store its email messages.
- OST: Offline Storage file of Microsoft Outlook allows the user to access the data in Offline mode, which is the cache replica of Exchange Server mailbox on local machine.
- MSG: It is the file format used to store emails individually in Microsoft Outlook email client. Which allows the analysis of emails individually.
- NSF: Through the analysis of the NSF file data the tool allow to forensically examine the Lotus Notes email data.
- LX01: LXO1 file is used to store the smaller collection of Logical Evidence File without loading the entire image file.
- EMLX: EMLX is the data file used to save the single email message of Apple/ Mac Mail in Mac OS.
- IMM: IMM file format is used to store the mailbox data of Incredible Mail. Through the Analysis of Incredible email message can be analyse through IMM file.
- MBOX: MBOX analysis help to acquire the email evidences from the email messages and attachment which are stored in it.
- OLM: Direct import of the OLM data allows the analysis of Outlook for Mac without the MAC machine.
- MBX: MBX file is the high performance replacement for the MBOX file format. This allows to examine communication take place through Eudora email.
- MBS: MBS is the file format used by the Opera Mail to store its single email message along with the attachments.
Investigate Mailbox of Web – Based Email Services
Cloud: The software works in a glean manner by allowing the investigators to go through the mailboxes of the web - based email services too. The emails of web - based email services such as GSuite, iCloud, Hotmail, Yahoo etc. can be analyzed by using the tool. Some of the renowned web - based email services include:
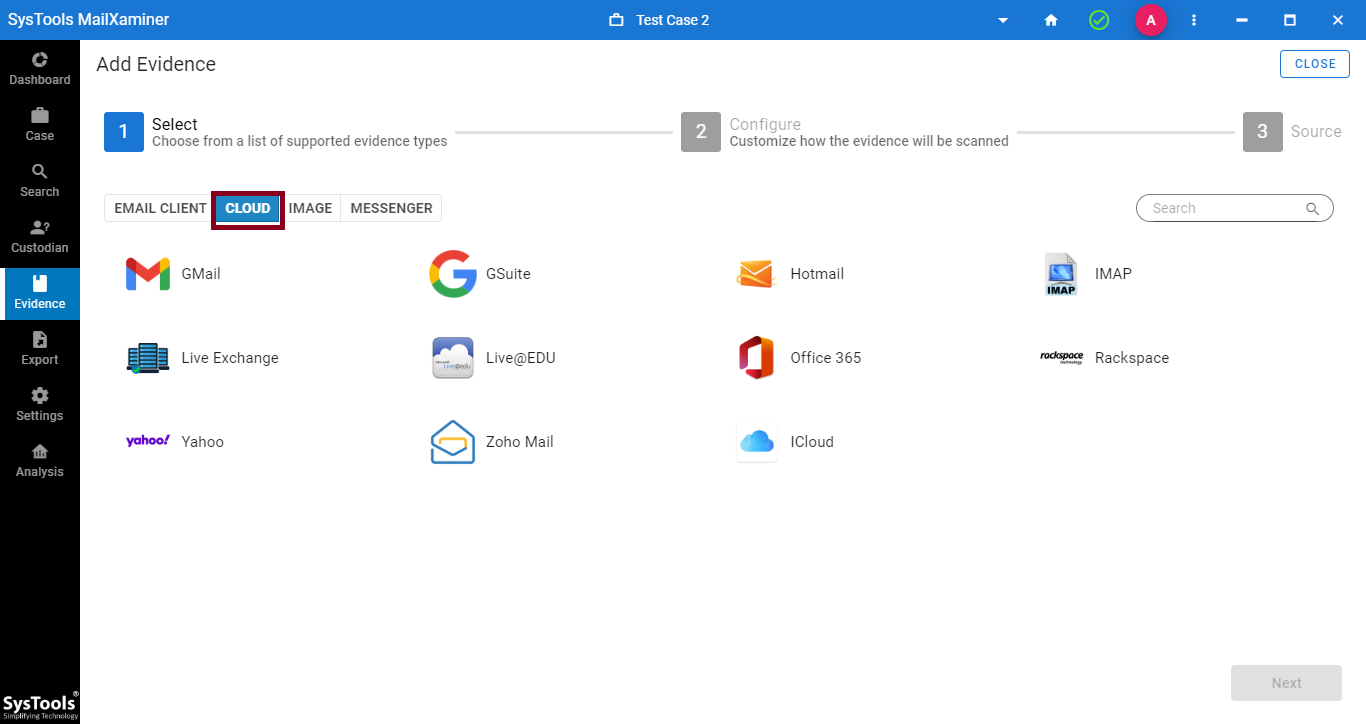
- Gmail: Allows to directly access the Gmail account and extract the email evidence through the advanced search operation.
- IMAP: This option allow to access and extract the evidence from all IMAP supporting Web based email services through forensic analysis of data.
- Office365: It allow to perform the electronic discovery on Office 365 email data through Keyword based & advanced search option and generate court acceptable evidence report.
- Yahoo Mail: Forensically analyse yahoo header and message data to extract the evidence and trace the attacker with the help email hops
- Hotmail: Examiner can easily perform the header& content analysis suspected Hotmail email message and attachment.
- iCloud: Investigator can perform filtered on-filtered examination of the data stored on the cloud storage of iCloud account.
- GSuite: GSuite user data can be easily accessed and forensically analyse. It also allows the user to access account data through admin permission.
- Live@EDU: Help to analyse the data used to communicate by the students and teachers to ensuring the security and prevent the unauthorized/ illegal usage of shared data.
- Live Exchange: Investigator can perform the analysis on the exchange server data directly without export or download data as EDB file.
- Zoho Mail: Zoho Mail forensic helps to easily analyse& extract evidence from single emails data other than the entire Zoho Mail database.
- Rackspace: Allow to analyse the Rackspace admin and associated user account data without hampering the workflow and threat to the crucial data of the organization.
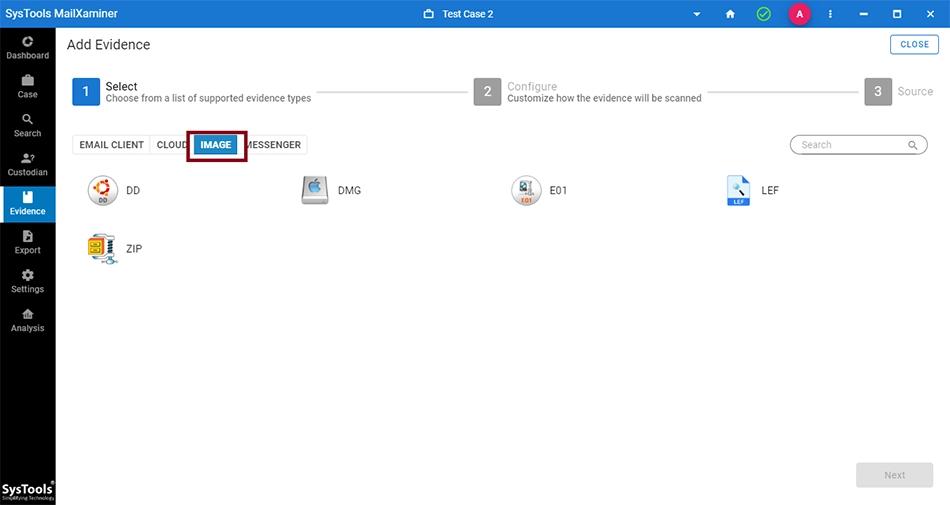
Examine Multiple Image File Formats
- E01: The E01 file keeps backup of various types of acquired digital evidences that includes disk imaging, storing of logical files, etc. You can easily analyze the email data available within the E01 files.
- LEF:Logic Evidence File allows to examine the evidence without loading the entire image file.
- DMG: DMG files contains the disk image of MAC OS. Software allow the dedicated forensic analysis of DMG files even when the message has been deleted permanently.
- ZIP: Through the ZIP file investigator can analyse a bulk set of digital data without considering the file format and email clients.
- DD: DD file contains the disk images and copy files of Linux or Unix OS. This option help to collects the evidence without tampering the data.
Analyze the Messenger Data
The software allows you to add Skype messenger data. Through which investigatore can easily analyze the Skype call, chat, SMS data without accesing the Skype account. The tool provide the option to import the Skype data through the ".db" file.
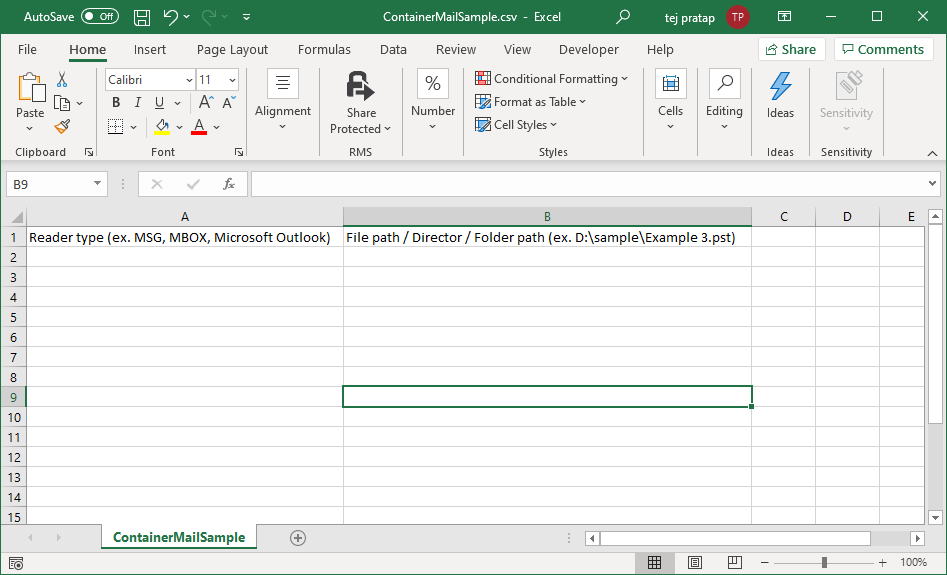
Add Email Data Files in Bulk
MailXaminer tool provides the facility to add a large number of data files into the software for analysis process through a CSV file. This feature helps investigators to examine bulk email files efficiently.
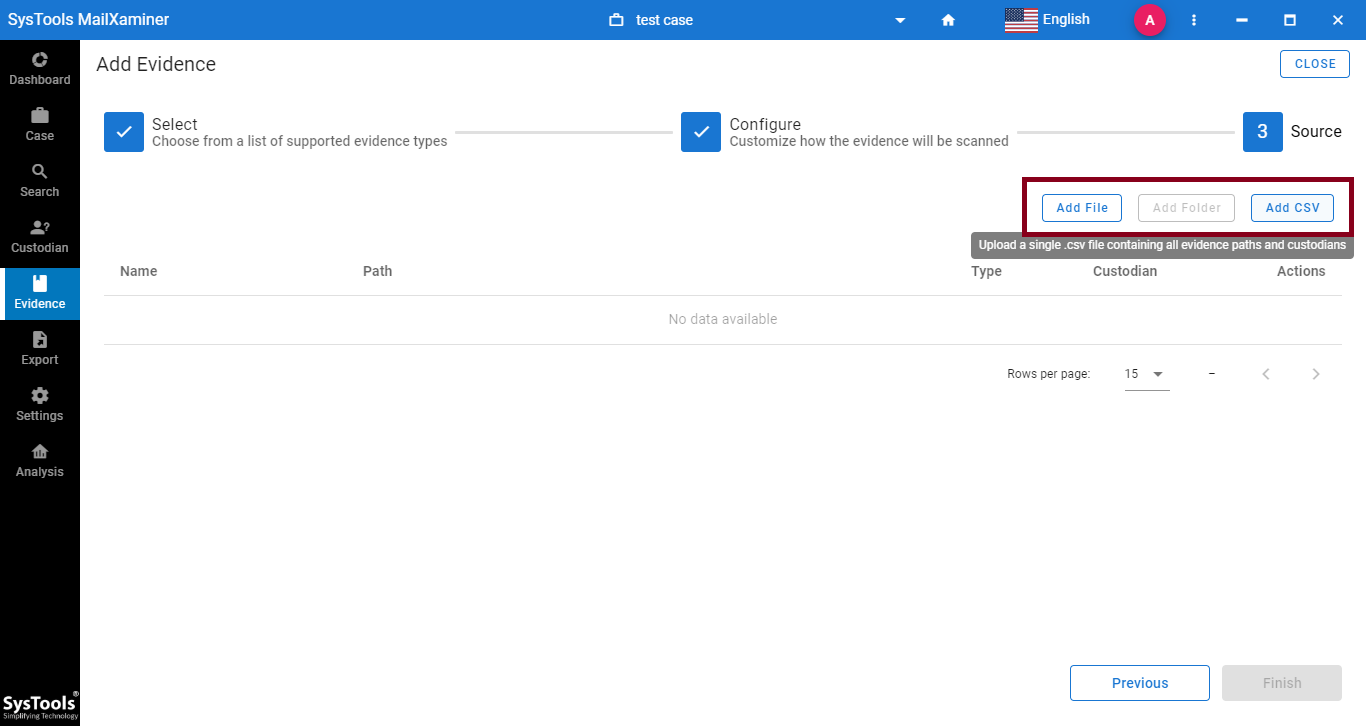
User can browse CSV file having extentions and path of files/folders to examine in a single go. This email investigation tool is reliable enough to investigate on large data files and extract evidences in hassle free way.