Perform Email Forensics in Outlook Mac OLM File – A Brief Guide
Nowadays, as the rate of digital crimes with several email clients is increasing rapidly, the need for forensics investigation of mailboxes under suspicion is also increasing. One of the popular email clients which is also the prime target of cybercriminals is MS Outlook. It is available for both the operating systems i.e., Windows and Mac systems. Email forensics in Outlook Mac OLM file is crucial to counter such crimes.
In this write-up, we are going to discuss “how investigators can perform the email forensics of OLM file associated with Outlook for Mac system?”
What is the Need for Outlook for Mac Forensics?
Development of advanced features within the updated versions of email clients has provided ease for communication across the globe. On the other hand, it also increases the number of cybercrime attacks. Outlook for Mac is widely using for business purposes within organizations. It allows users to setup server-based rules for MS Exchange and integrates with Lync (Skype for Business) using in many large-scale associations. This is because there is a high chance of Mac Outlook being involved in cyber-based criminal activities like illegal sharing of confidential data, theft of intellectual property, identity theft, etc.
Nowadays, cybercriminals are using Mac Outlook for illegal activities, often there exists a false belief that a deleted email message from Outlook cannot be restored. However, advanced inbuilt techniques in forensic tools help examiners in the recovery of deleted email data to ensure the retrieval of evidence. Forensic analysis of Mac Outlook has become a matter of high concern to reach suspected facts and evidence against the accused to provide justice to victims.
Email Forensics in Outlook Mac OLM File Manually
Considering the aspects of investigation teams, firstly it is necessary to understand the structure of Outlook data files. These files should primarily go under to analyzation and study to carry out the forensic investigation. The location path of Mac for Outlook data files in the user’s system is varied from one version to another. Mac Outlook 2011 is different from other versions because it archives data files in OLK14msg file format.
The emails, contacts, and other data items with Mac Outlook 11 profile are there in the user’s system under the local directory path, as follows:
“Documents/Microsoft User Data/Office 2011 Identities/Main Identity/Data Records/..”
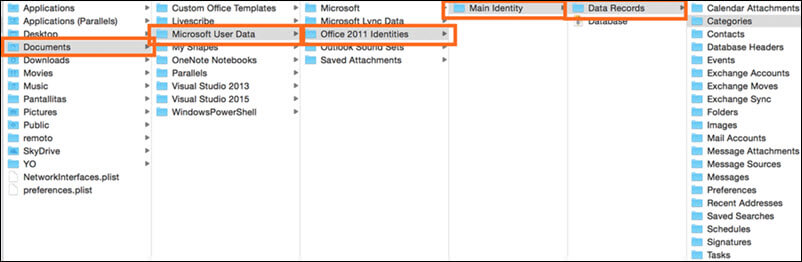
Mac for Outlook lists its user profiles under the folder “Main Identity”. Single identity can have one or more email accounts associated with it. Identity stores all the emails, contacts, calendar entries etc. under the “Data Records” folder. The only file format that can be used for archiving Mac Outlook data is OLM file i.e., Outlook for Mac Data File.
Contents of Outlook for Mac Profile are as follows:
– DATA RECORDS
As stated above, Identities are used in Outlook for Mac system and it contains a directory called “Data Records” containing all the data items or files of the particular Outlook profile. Multiple file directories are present under this folder such as Calendar attachments, contacts, messages, message source etc.
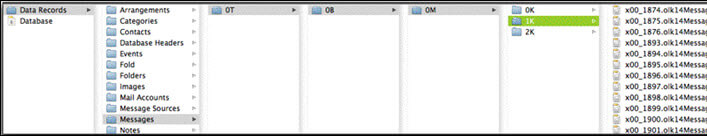
– nK DIRECTORY
When the Message folder inside the “Data Records” directory is opened, users can see many other folders before reaching the main message in the format of the nK directory. Here, n defines the sequence, and K is used to denote thousand according to the default naming convention used by Microsoft for naming folders such as T – Trillion; B – Billion; M – Million and K – Thousand.
– MESSAGE SOURCE
Now, moving forward in email forensics in Outlook Mac OLM file, there comes the message source. It contains the most important part of the content as far as forensics investigation is concerned. Message source stores the email content located under the “Data Records” directory. In order to access the message Source, select the message and right-click on it and choose ‘View Source’
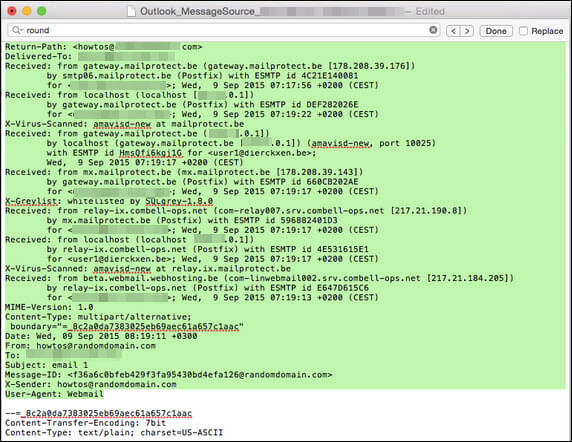
The message Source of the email in Outlook for Mac looks like this:
– OLK14MESSAGE
It consists of email file header portion, but not the whole body content. It’s to properly analyze and investigate emails. after the download of the email message, the user gets a local copy of it. Message Source contains many details about the email and related data in terms of forensics. It can be useful to extract important information related to the message like sender details, IP address, receiver details, MIME version, etc.
The collected email data from the suspect’s Outlook OLM file can be compiled together. The resultant information can be studied manually or with the help of an efficient Email Forensics Tool .
Outlook Mac OLM File Forensics Using Automated Tool
MailXaminer is an efficient email forensic software, containing a wide variety of powerful advanced features. The tool provides multiple functionalities like search mechanisms based on algorithms, recover deleted data, multiple preview modes of emails and attachments, export evidential files, and many more. Using these advanced features, forensic examiners can analyze Outlook OLM files to search for the evidence. Further, we will discuss the process of investigation and searching for evidence in OLM data files using an efficient digital software.
Email Forensics in Outlook Mac OLM File – Step by Step
Step-1. At first, users need to add the suspected file into the software to start the examination process. For this, select the Add New Evidence button. A new window will open, now select the file type and provide the location of file from the system.
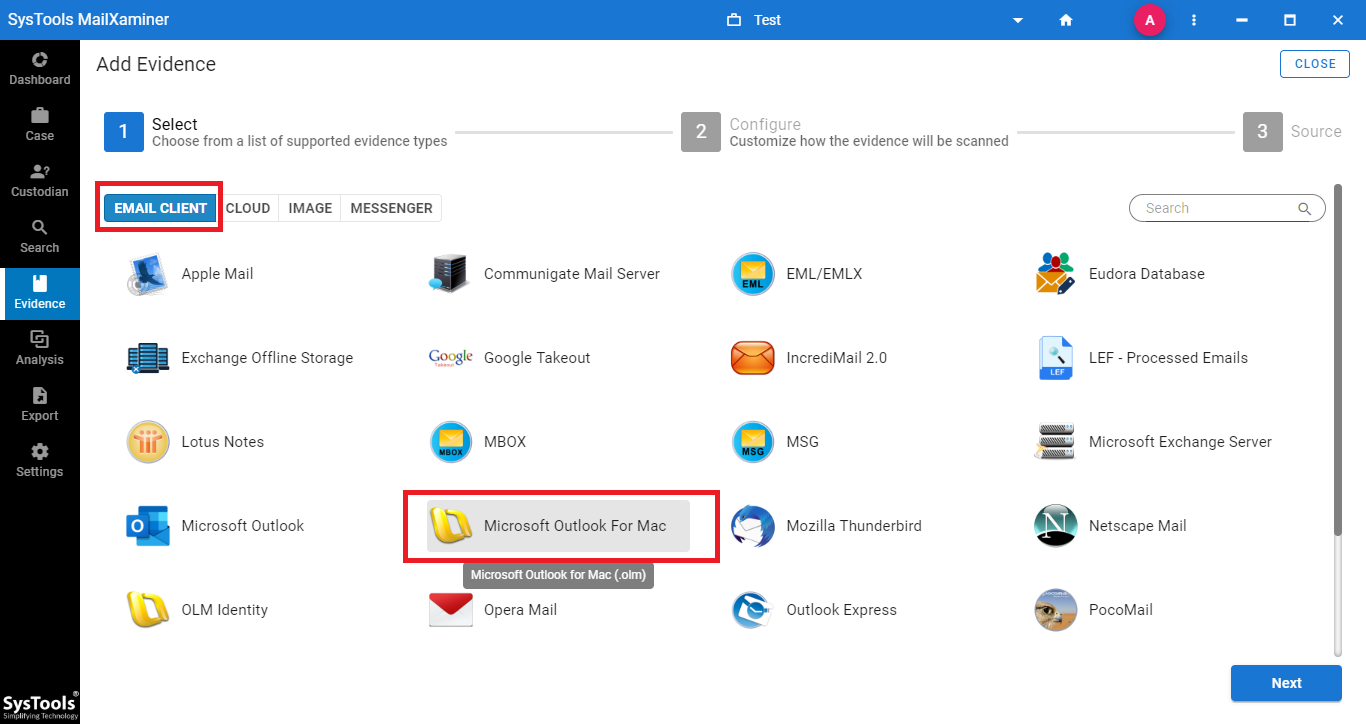
Step-2. Now, under the Emails tab, users can view all the email data files including recovered deleted files in red color.
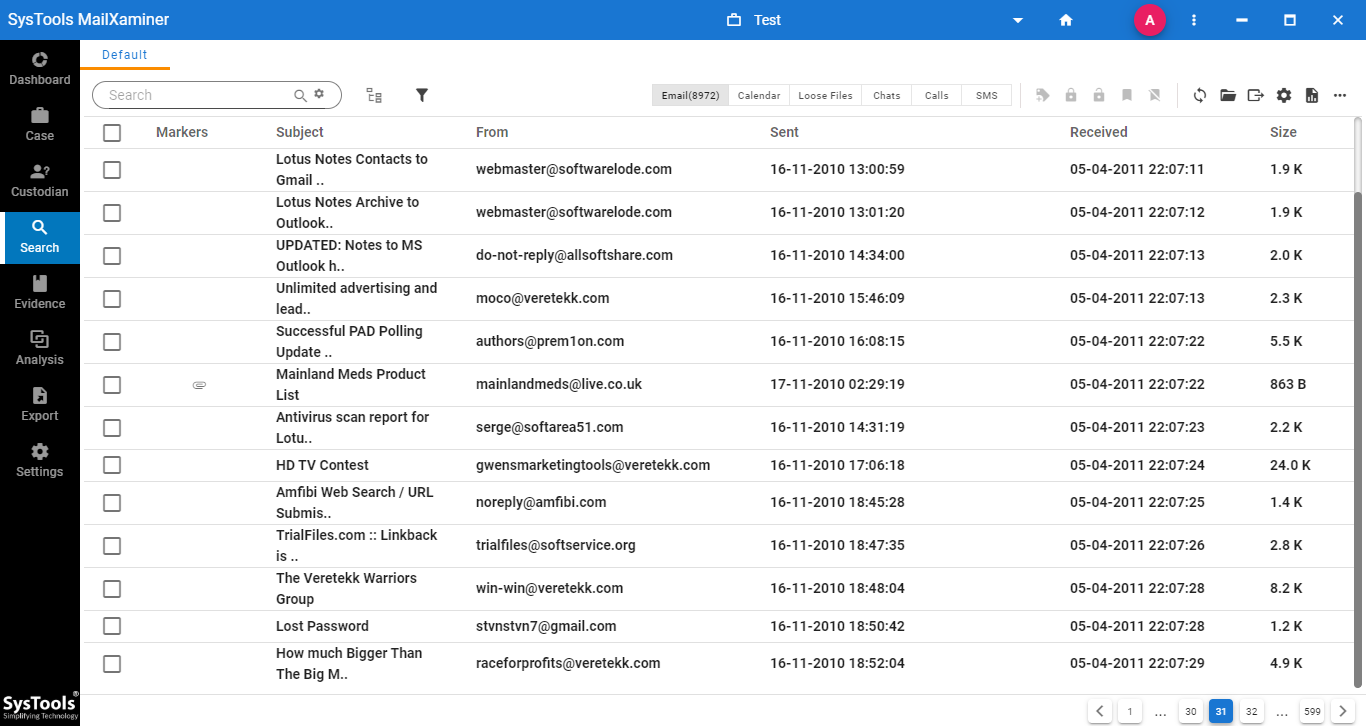
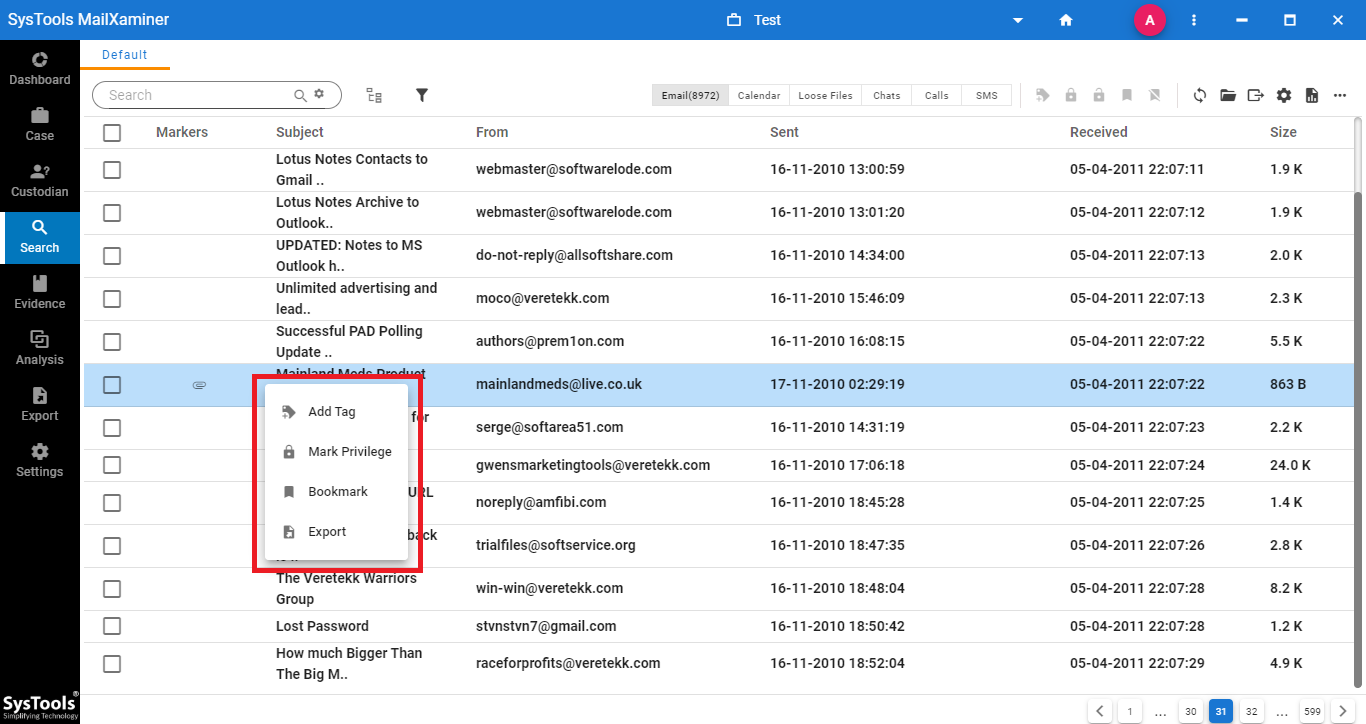
Step-3. The software provides an option to preview selected email files in multiple preview modes that will help the user diligently analyze the data. For this, just click on the email. By right-clicking any email file, user can access a menu containing several options such as Bookmark, Mark Privilege, Add Tag and Export.
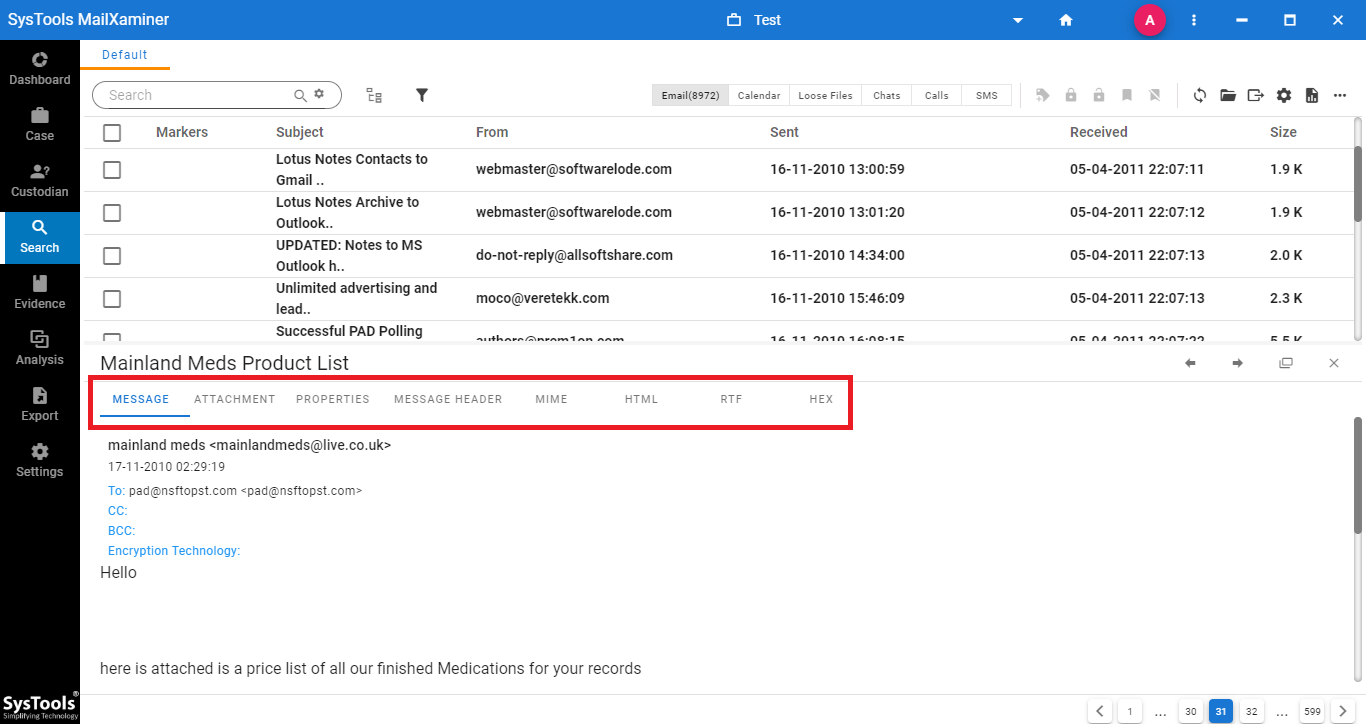
Step-4. It provides different preview modes such as Message, HEX, Properties, Message Header, MIME, HTML and RTF. Using these different views of emails, investigators can extract hidden data and search the evidence from email files.
Step-5. Switch to the Attachments tab of the email preview section. Here, one can view all the attachments from the scanned email file.
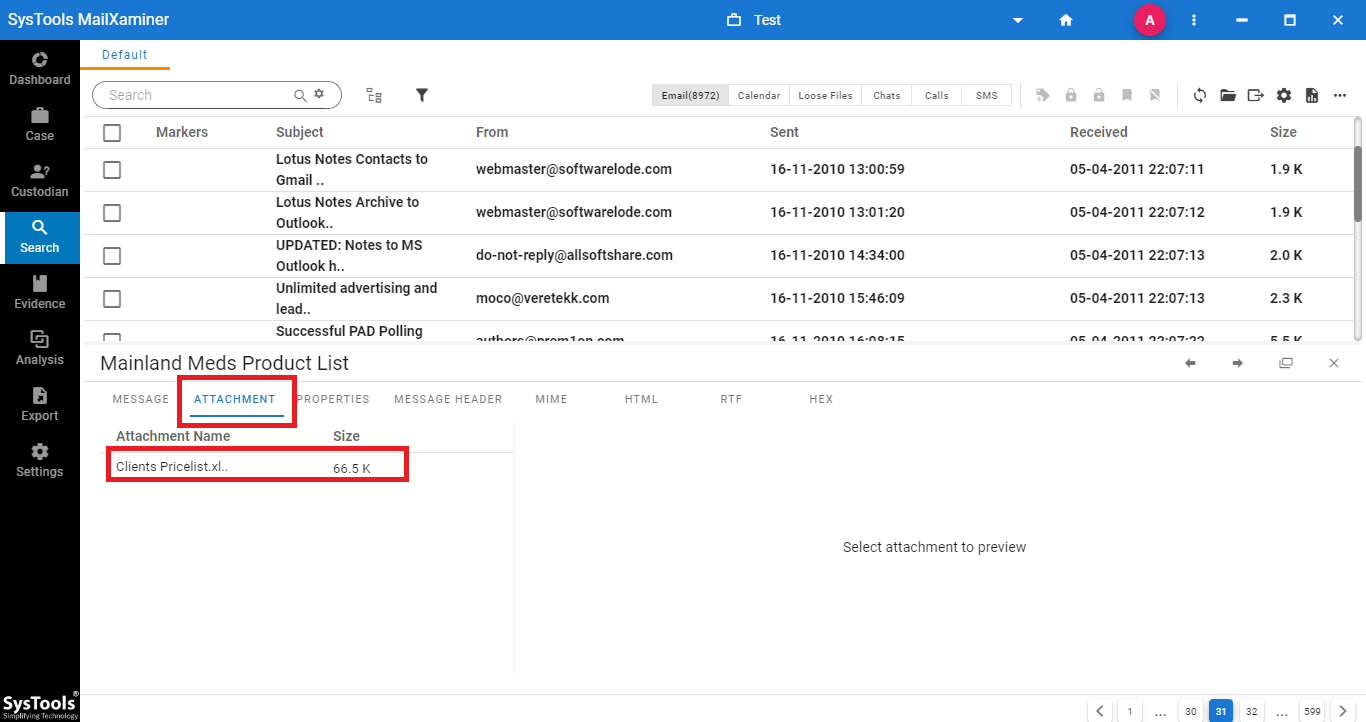
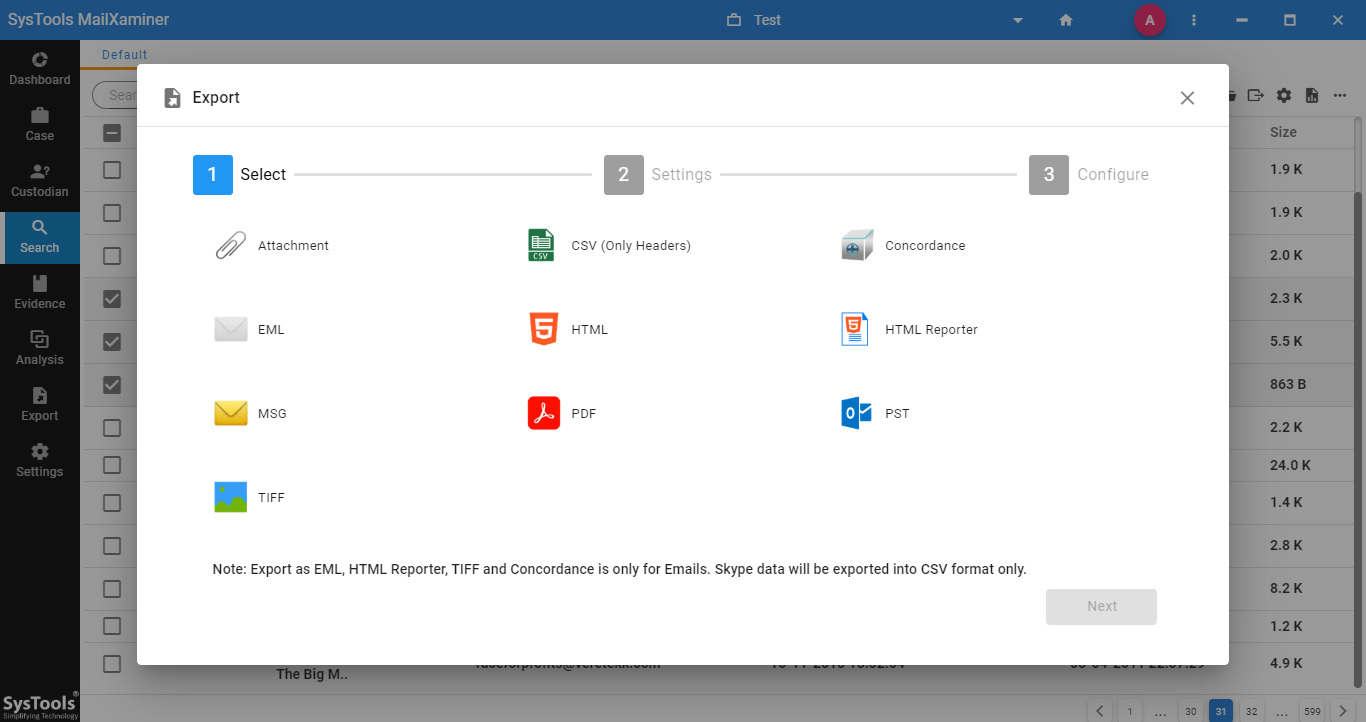
Step-6. The tool also provides an option to export the evidence report in any desired file format. To export the files from the software, just select files, and then click on Export button on the navigation bar. A window will open, select the Output Format and then provide the Destination Location to save the export file.
Observation
The blog has aimed to understand the need for forensic analysis associated with email clients like Outlook for Mac. The in-depth investigation on the Outlook for Mac OLM file takes place after analyzing the contents of the OLM file. Several investigation tools are available in the market to resolve cyber-criminal acts.
The above featured software is an efficient utility that allows deep examination of the emails of Mac Outlook. No other solution can execute email forensics in Outlook Mac OLM file better than this. It has the ability to analyze email data files systematically and extract evidence from the files in a hassle-free way.

