Yahoo Email Forensics – Best Tactics to Analyze Data
Yahoo Mail is one of the popular web-based email application used by countless users to meet their personal and business needs. With the rapid increase in net surfing and internet usage, users associated with a wide array of illegal activities have also enlarged. Security loopholes in Yahoo emailing have ultimately raised the need for Yahoo email forensics investigation.
Yahoo mailbox analysis and email investigation process involves different stages such as collection, analysis, preservation, and reporting. One can perform a detailed analysis of web-based emails like Yahoo! Mail by implementing Yahoo mail forensics. With the help of this blog, we will focus on the need for Yahoo email investigation along with the suitable approaches to perform the investigation. Before that, let’s first understand what exactly is email along with its attributes.
What is Email and Its Various Components?
E-mail is the method of exchanging email messages among different users through electronic devices. Moreover, it comprises of four main components; Mailbox, Domain Name, Message-ID, and ENVID. These are globally unique identities, which are used in an email. Mailbox is a conceptual storage entity with the basic identity of the email address. Email address comprises of user name and domain name separated by “@”. Domain names can be defined as a global reference to an Internet resource like the host, network, or service. Coming to the header part, Yahoo mailbox analysis is the most important part that helps to investigate officers to find the culprit.
How to Perform Yahoo Mailbox Analysis?
In Yahoo email forensics can be manually analyzed by extracting header information of suspicious email and going through its details. This can be done by following the below-mentioned steps one by one.
Step 1: Save Header Data in Another File
- Sign in to your Yahoo! Mail account and go to the Inbox to view the email messages
- Open the email message to be analyzed. Click on More options and go to Drop-down Menu
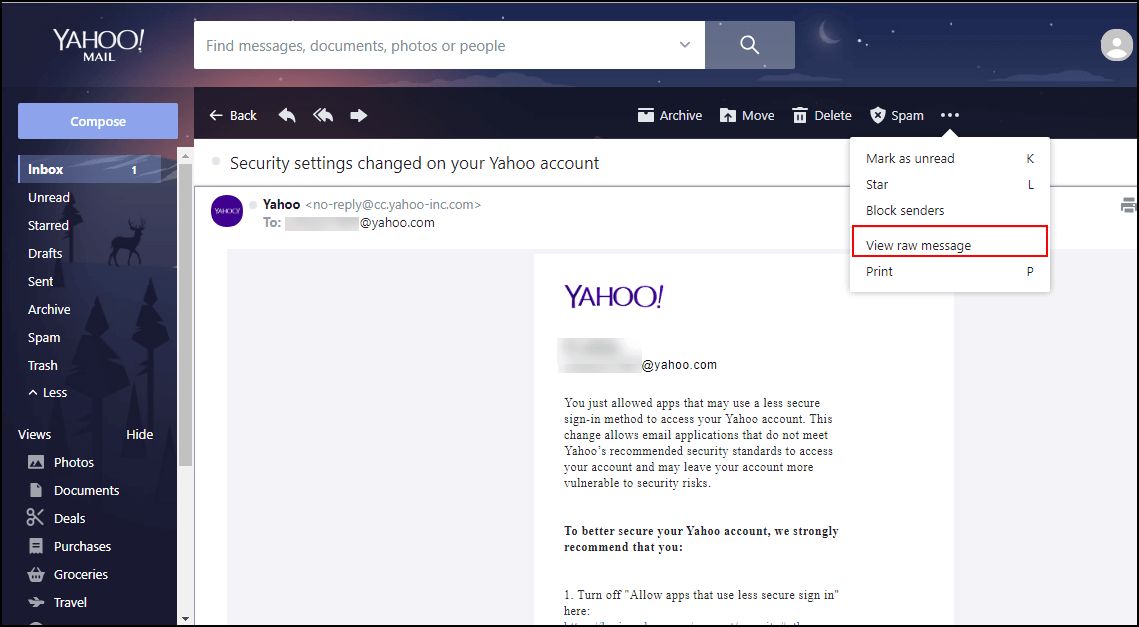
- Select the “View raw message” option from the more options menu
- Another Windows will open with header details for that particular email through which you can manually perform Yahoo email analysis on the header
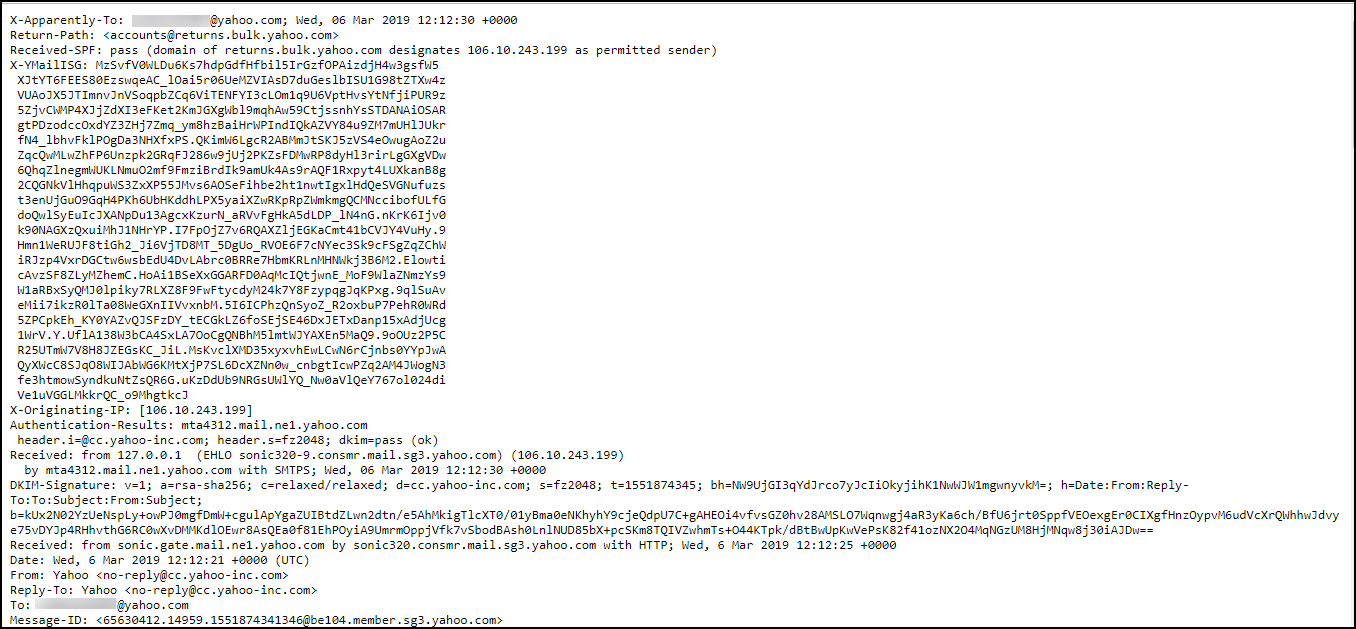
- Copy it to another text file and save it safely to perform Yahoo email header analysis.
Step 2: Analyze the Header Information
Open the .txt file which was saved initially during Step 1 and go through the different components. The first few lines show the E-mail Servers through which email message traveled.
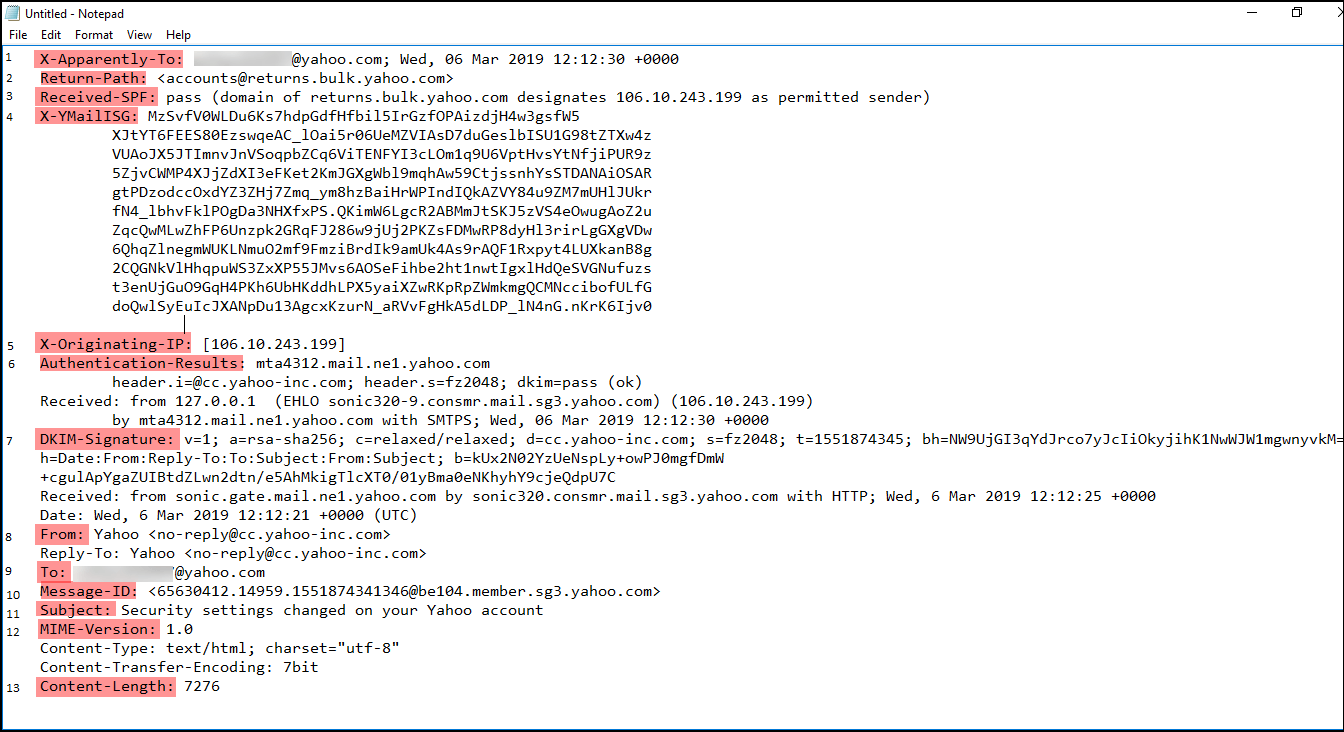
- X-Apparently-To: This discloses the recipient’s email address. In Yahoo email forensics, one can validate this field with an e-mail service provider. This email ID must match the ID used by the victim. This field can be referred to as “To, BCC or CC”.
- Return-Path: It denotes the value which is used during the SMTP session. This indicates the address for replying which is termed as “Reply to” in the front end. Moreover, the attributes of the Return-Path is similar to the sender email address. However, this field can be easily spoofed and hence not be trusted unless analyzed by professionals.
- Received-SPF: Here, SPF stands for Sender Policy Framework. It shows the type of email service used for sending email. An ID number is also involved here, which can be used to examine logs form, transmitting e-mail server determining the genuineness of an email if it was sent from the same service. If this ID is unavailable, the email message has chances of being spoofed. It includes two value i.e., pass and fail. “Fail” denotes that MTA (Message Transfer Agent) must be rejected from the settled connection. Whereas, “Pass” indicates that MTA must add a header.
- X-YmailISG: X represents “Custom Header”, Ymail means “Yahoo Mail”, and ISG means “Inbound Spam Guard”
- X-Originating-IP & Received: It helps to identify the origin of the client’s IP address that is being connected to the mail’s service’s HTTP front end. The later one is also capable to reveal the name of the server, which was used to send an email.
- Authentication Results: As the name suggests, it provides an authentication report to the receiver. Moreover, it is provided once the email message gets delivered.
- DKIM-Signature: DKIM stands for DomainKeys Identified Mail. It is the signature of the email, which is stored in this field. All the signatures and key-fetching data will be saved here with a simple “tag=value” syntax. For investigators, this DKIM provides a technique to validate and confirm a domain name, identity associated with a message through cryptographic authentication.
- From: This header displays the email ID of the sender, who has sent mail to the recipient’s Yahoo! Mail account.
- To: It displays the email ID of the receiver to which the email message is being addressed.
- Subject: It shows the subject of the email or the reason to open that particular email message.
- Message ID: Message ID is a unique ID authorized to a specific email message by an email server. This Message ID can be used to track the message on the originating email server in email logs.
- MIME Version: It specifies the version of the MIME message format. For example, in this case, it is 1.0 version. This helps in the further Yahoo email investigation.
- Content-Length: It will show the number of characters present within that particular email message.
A One-Stop Solution to Perform Yahoo Email Forensics
It is quite challenging yet tedious to acquire web-based email while carrying out the investigation process. Although there are numerous forensic analyzer tools available to simplify the process of email evidence extraction and analysis. However, most of the software fail to extract email data directly from web-based emails like Yahoo! Mail. This is the reason, MailXaminer act as a sure-shot solution for the investigating officers to perform Yahoo mail forensics.
Following are the steps to implement Yahoo email analysis using the ultimate software.
Note: To access & perform Yahoo email analysis directly through the tool. Make sure to
- Turn Off Two-Step Verification
- Turn On Allow Apps that use less secure sign in
Step 1: Once Yahoo! Mail is launched, go to Account Info >> Account Security >>
Turn Off Two-Step Verification >> click Generate app passwordStep 2: Now, select Other app option >> enter app name “MailXaminer” >> click Generate
Step 3: Copy the Generated Password and click Done.
Step 1: To begin with, click on Add Evidence button from the left top section of forensic software to acquire the Yahoo email data
Step 2: From the next wizard, navigate to Web tab and select Yahoo from the Web Account section
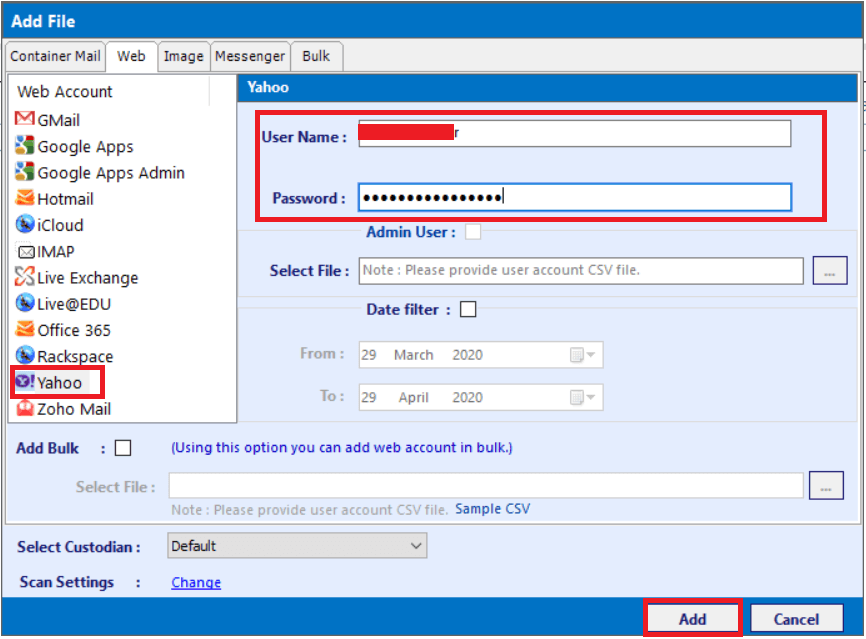
Step 3: Then, provide User Name & the generated Password in the respective fields. One can also add multiple accounts through CSV file and can use the Date Filter option to access the email data in date order
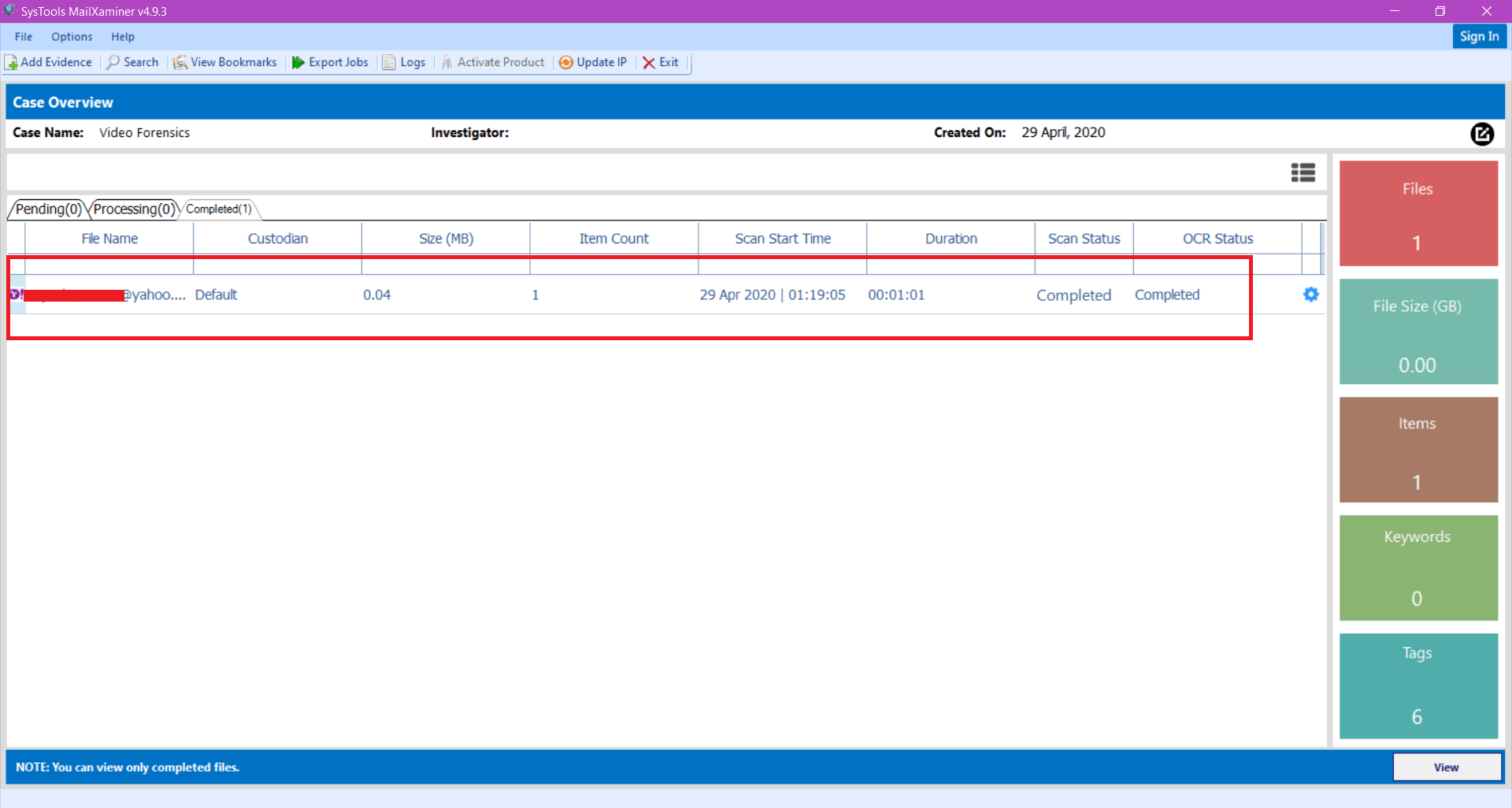
Step 4: Under email tab of the Yahoo email analyzer, it displays a list of Yahoo mails present in the mailbox. User can access the data either folder wise or altogether through recursive listing of items. Additionally, the software provides different preview options like “Mail, Hex, Message Header, MIME, Email Hop, HTML, RTF, Attachments” to analyze the email data forensically. Each view helps to acquire different information related to the Yahoo! Mail.
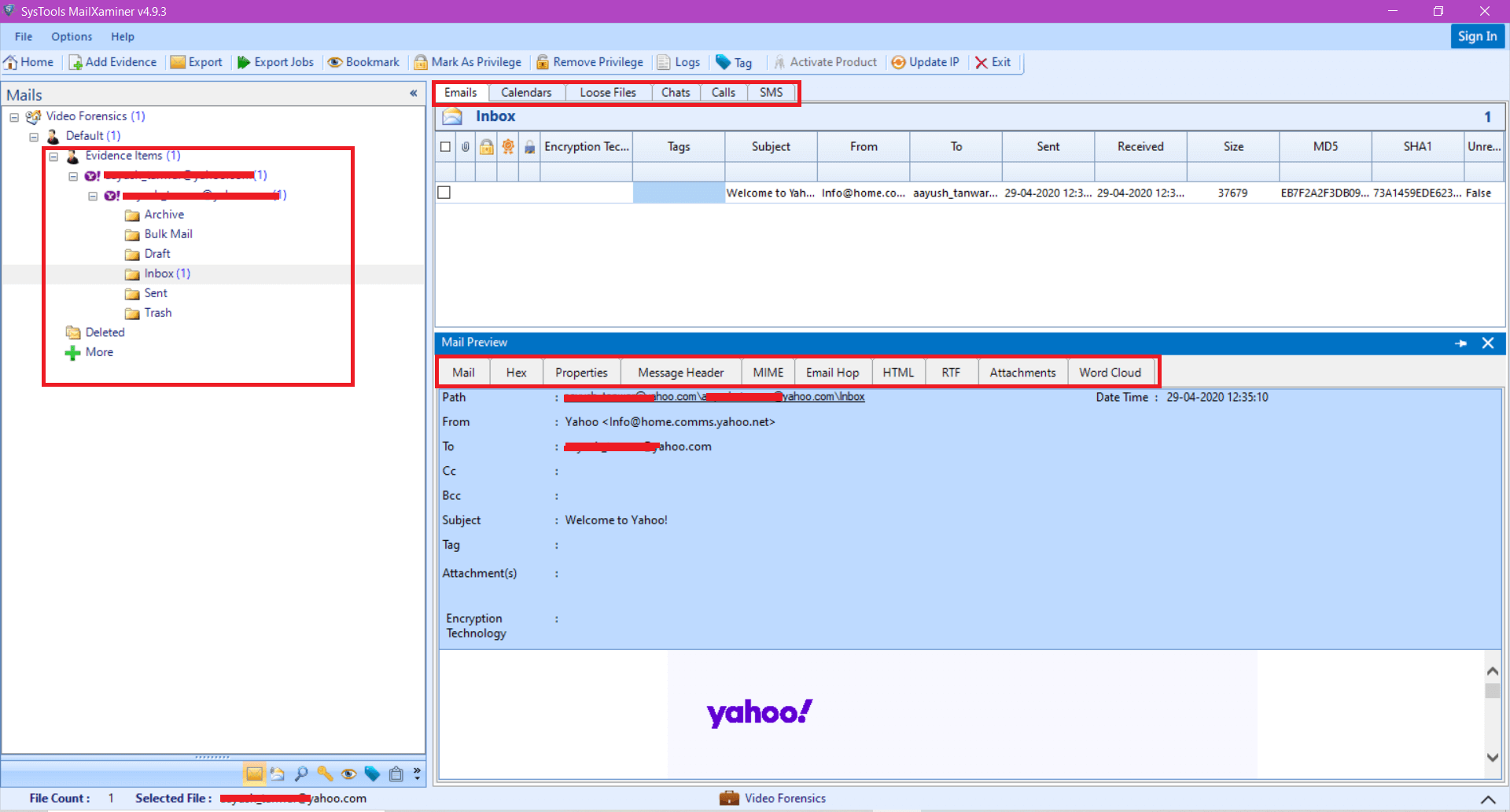
- Mail: This view allows the investigator to examine the basic details of the email message such as Subject, From & To address, Tags, email message, etc.
- Hex: This view allows to examine the entire email data in Hex value that helps to know the information bit-by-bit. Moreover, it provides the offset, hex code and textual value of the email message.
- Properties: It provides the short view of the email attributes which may help investigating officers to analyze and understand briefly about the Yahoo! Mail data.
- Message Header: This header consists of several attributes which corresponds to the respective email message. It includes message-ID, content-type, etc.
- MIME: This view helps to view every minute details of the email message such as content-type, return-path, etc.
- Email Hop: This allows to obtain the actual path through which the email message has travelled. It also shows the gateway, router and switches through which the email passed.
- HTML: This view represents the email data in the form of HTML scripts. This view enables forensic examiners to easily compare and find the changes done in the data.
- RTF: It is helpful to maintain the originality of the mail. This view helps the examiner to analyze the font and formatting of the email message.
- Attachment: In this, one can easily preview and analyze the attachments present within the email data.
Time to Sum Up
The manual method described to perform Yahoo email forensics may not help the investigating officers in terms of providing potential evidence. As a result, it is highly suggested to avail the best yet reliable MailXaminer Email Examiner Software. It is exclusively designed in a manner to support files from both web-based and desktop-based email applications. With this, one can efficiently analyze and identify artefacts out of the emails using 7+ preview modes.

