Hotmail Forensics – Explore the Perfect Tactics
Summary: This blog focuses on the importance of examine emails along with the techniques that help to swiftly analyze Hotmail emails. The different elements of the Hotmail emails to execute the Hotmail investigation thoroughly has been well-explained here.
Overview of Hotmail
Windows Live Hotmail or Hotmail is a free web email application. With the help of an internet connection, one can easily access the emails from any web browser. In the year 2012, the Windows Live Hotmail service name changed to Outlook.com. Outlook.com offers numerous advanced features to its end-users such as unlimited storage for free, Skype connections, social media services like Facebook, Twitter, Google, etc.
Hotmail as a Weapon to Initiate Cybercrime
The rapid increase in the number of email attacks by cybercriminals using Hotmail/Outlook.com accounts is a subject of concern. The overall investigation of Hotmail mailbox components for analyzing evidence is what we call Hotmail Forensics Analysis.
One of the most important elements that help investigators in cyber findings is “Email Header Analysis”. Additionally, Hotmail email forensics includes analyzing server logs, and application through which email communicates. These are some of the tactics that play a vital role in the forensic investigation of the Hotmail application.
So, let’s start by knowing the best approaches to perform Hotmail forensics!
Analyzing Hotmail Email Information
From Hotmail email information, the investigation officers may be able to identify the Hotmail IP address that can be useful to determine the sender’s details. In some cases, masking, redirecting, and spoofing techniques are beneficial for the sender to prevent accurate information.
Hotmail Email Contains Two Header Categories:
- Envelop Header: This is comparatively more important in Hotmail forensics as it is difficult to spoof the information that comes under this section. This information contains Hotmail header message ID, sender’s mail server information as well as X-Message information fields.
- Message Header: The Hotmail header information under this section is what the user defines. In addition, it is easy to spoof. This section contains fields such as To, From, Subject, Return-Path, Content-Type, etc.
Hotmail, which is now Outlook.com, the header information from the emails can be accessible by following the upcoming procedure:
- On the webpage, log in to your Hotmail account and open the message list.
- Right-click the message and then select the “View Message Source” option.
This will navigate to the source code page of the email message which looks like the following image.
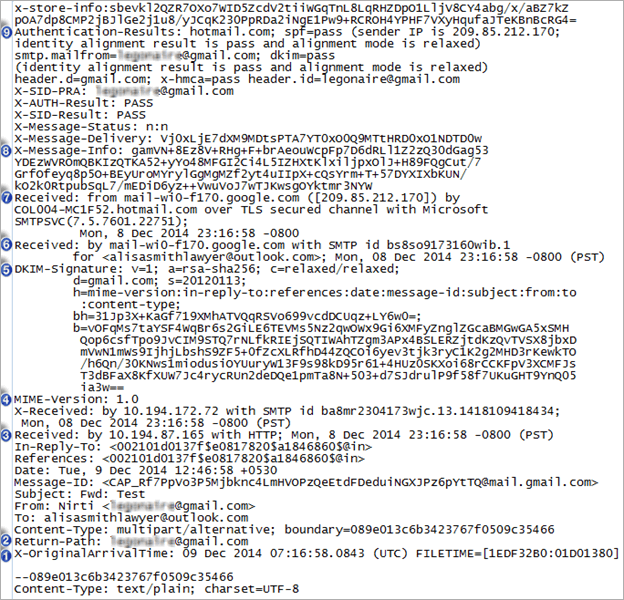
Crucial Attributes of the Hotmail Header
- Return- Path:
This attribute helps to investigate officers to identify hidden evidence. This element of the Return-Path is similar to the email address of the sender. It provides the address i.e., “Reply to” in the front end for replying. - Received:
In the source code, we can clearly see that the ‘Received’ section occurs thrice. Investigators study these parameters from bottom to top to view them forensically during Hotmail email forensics. It shows the transaction path through which the email message has been traversed. The last ‘Received’ value is first in the queue of Hotmail forensics analysis. - MIME-Version:
This section of the header text shows that the formatting of the email is in MIME (Multi-Purpose Internet Mail Extensions) style. It ensures that the sent email message is compliant with RFC 1341 standard formatting. - DKIM-Signature: Domain Keys Identified Mail
If an email is sent by an organization with a DKIM signature on the mail. It denotes that the message is not spam and the signing authority is directly responsible for it. - X-Message-Info
As a result, investigators do not take this section lightly during Hotmail email forensics investigation and analyze it by considering all associated factors. - Authentication-Results: (SPF)
If an email is sent using a domain, it is the responsibility of the SPF (Server Policy Framework) to check whether the specified Mail Server is authorized to send email messages. The possible result set could be ‘PASS’, ‘FAIL’ or ‘NONE’.
However, in case, if the domains’ registration is not under that particular Mail server, the value may display as ‘NONE’. Additionally, if the sender’s Mail server fails to deliver a message to the recipient, the value might return as ‘FAIL’.
Server Investigation in Hotmail Email forensics
This is referred to as the detailed analysis of server logs and the delivered email messages. The emails that are deleted from senders or recipient’s end can be requested from Hotmail Server or Internet Service Provider (ISP). This is because the replica is stored by them for each delivered email message.
Thereafter, the analysis of logs can be easy by tracking the original address of the sender’s computer. Here, the limitation is that the replica for email logs and the messages are maintained by the server for a stipulated period of time. Because of this, it may create an obstacle for the investigators while performing Hotmail forensics.
Instantly Perform Hotmail Forensics With Email Investigation Tool
With the help of Email Examiner Software, the investigators can easily access and analyze the Hotmail data in a precise way. All you need is the credentials of the suspected Hotmail account in order to thoroughly investigate the emails.
To perform Hotmail email forensics with the help of the tool follow the below-mentioned steps:
Step-1. After the software is launched, click on Add New Evidence >> Cloud >> Hotmail >> Input the Credentials
Note: It allows to add multiple accounts as bulk through the CSV file, which contains the login credentials. It also provides a date filter option to access the email data from the specified date.
Step-2. The Hotmail email analyzer software displays a list of emails. It displays information such as Subject, From, To, Sent & Received date etc. This view of the data helps to obtain brief details of an email message without opening it
Step-3. The software also provides the option to precisely preview the emails using 7+ preview options. For that, just click on the email message. The different view mode includes Mail, Hex, Properties, Message Header, MIME, HTML, RTF.
Detailed Explanation for the Technical Terms
- Mail: It will show the email body message with Subject, Tag, attachment, From & To address in user perspective for the analysis of email message
- Hex: This will help to examine the email data in Hexadecimal value. The character mapping in the hex value will help to identify the changes done in the original data.
- Properties: This view helps the investigator to obtain the summary of email data which provides information such as “Body details, Message flags, Dates, Recipients, Sender details, Subject & Additional information”.
- Message Header View: It enables forensic experts to examine the Hotmail message information.
- HTML: It provides the HTML script view of the email message. This view helps the investigator to examine the data through different browsers during Hotmail email forensics.
- RTF: If the email is composed using RTF editor, then the tool lets investigators preview the emails precisely using this view. Moreover, it consists of different encoding types, so this view also helps to know the encoding type of the RTF email.
- Attachments: It will provide the list of attachments available within the email and help to easily preview those attachments.
Phase Two of the Hotmail Forensics Operation
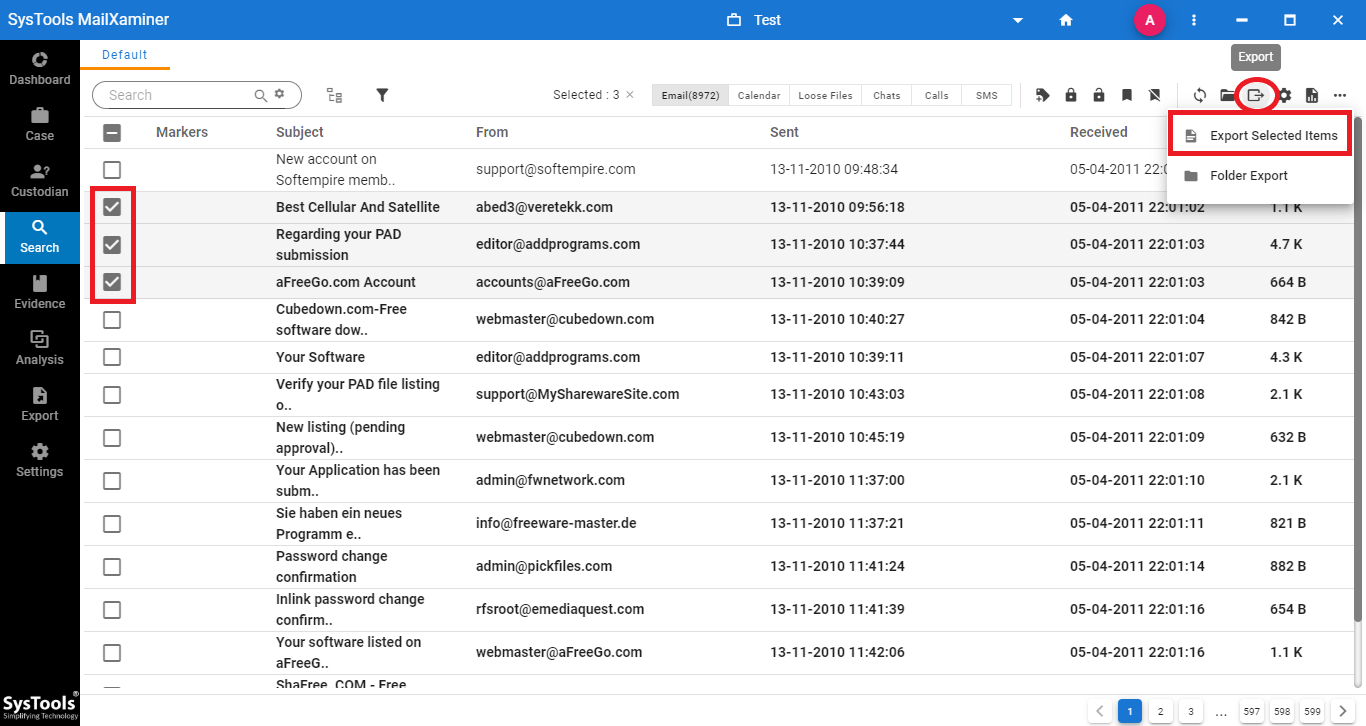
Step-1. To convert the Hotmail emails, firstly you need to Select the Emails >> Export >> Export Selected Items option as shown in the below screenshot.
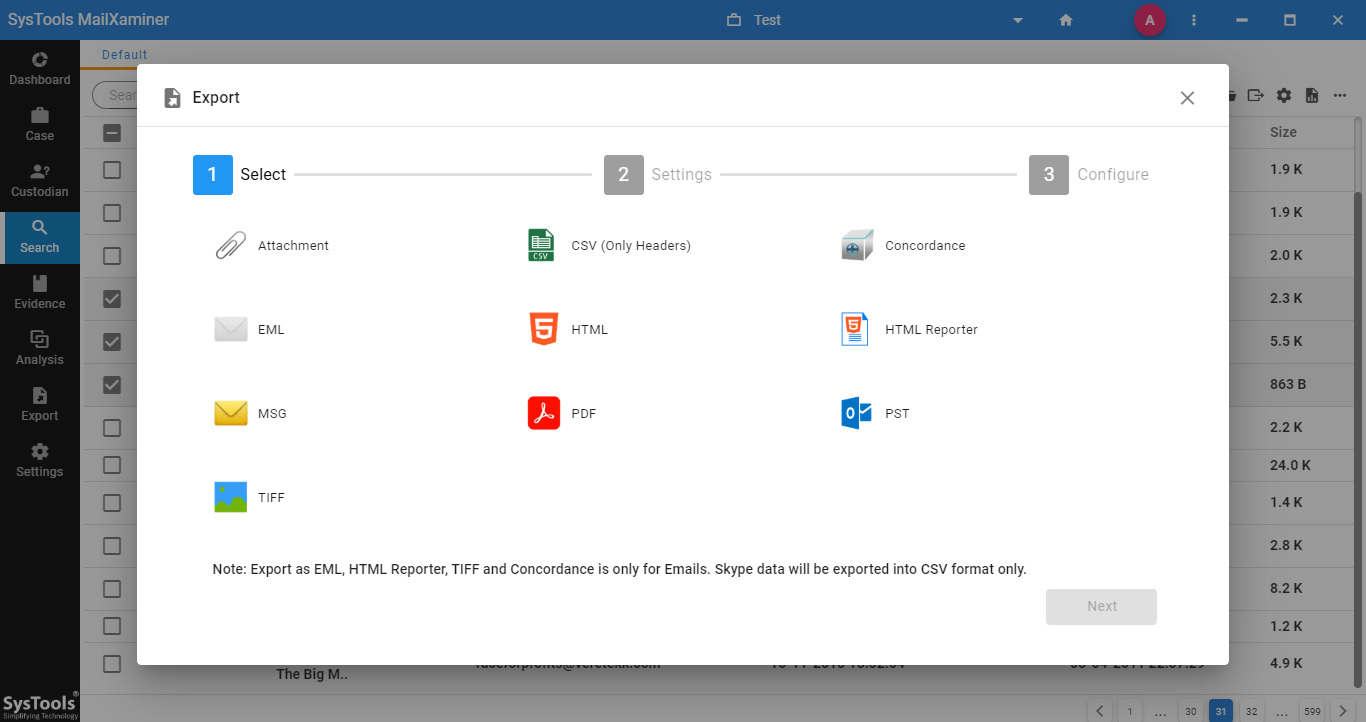
Step-2. Under Export screen, investigators can avail multiple export file types while converting Hotmail emails to the desired format. The various export file formats offered by the tool include EML, HTML, PST, PDF and many more.
Step-3. Finally, the system will keep the emails at the destination location in the chosen file format after exporting them.
The Final Note
Investigating officer deals with several challenges while performing Hotmail forensics. Now, by understanding the various components of the Hotmail email, it becomes easy to identify hidden evidence. This blog has disclosed various techniques to investigate Hotmail emails using the versatile MailXaminer software. The utility provides full-fledged features that help to swiftly examine emails in no time.

