DMG File Forensics Using MailXaminer
DMG is an acronym for Disk Image File that is created on Macintosh operating system. A DMG file is denoted with the extension .dmg. These files were created with the aim of transferring Mac applications over the internet. They are used as mountable disk images that are accessed with a default file manager of Mac machine. The DMG files can be created in accordance with the structure of Universal Disk Image Format (UDIF) or other file systems like HFS, HFS+, and FAT.
In addition to this, it can also use New Disk Image Format (NDIF) for its structure. When it comes to the security of these DMG files, they can be protected by AES-256 and AES-128 encryption. Moreover, they can be compressed by compression formats like ADC, bzip2 and Zlib. Thus, the compression and security imposed on these DMG files have made it an ideal disk image format for sharing data (distribution of software) over the internet.
Different Kinds Of DMG Files
Before we learn that how to view DMG files in Windows, it is to be noted that there are different kinds of DMG files available. We have listed only a few DMG files that a user can mostly come across:
Read Only
This type of DMG file will prevent the users from making any alterations in the content of the file. When this read-only DMG file is created, the free space of the original file is not omitted. Therefore, the volume header will assume the size of the DMG file to be larger than it originally is.
Compressed
The data residing in the read-only file when compressed is referred as the Compressed DMG files. Although, this compressed DMG file is not as secure as the read-only file since there is no protection to the data stored in it.
Read/Write
This DMG File will contain both the data and the free space of the original file from which it was taken. This type of DMG file is similar to that of a raw disk drive image. You can even rename the .dmg file to .dd and vice versa.
Hybrid Image
This is a cross platform image that contains fore file systems. The data of the image is saved between all the four files equally. The data, which remains unique to each file system, is the directory information and the volume data.
Deep Analysis of A DMG – DMG File Forensics
When it comes to forensically analyze the structure of DMG files, the first step is to mount them in order to view the contents residing in the file. Moreover, the content can only be viewed if the forensicators have access to a Finder that enables to read this file. Before accessing these DMG file, the files need to be locked first in order to maintain their authenticity and protect them from any changes from the forensicator’s end. The biggest challenge, which the examiners face, is that a DMG file cannot be accessed on Windows machine. Therefore, in order to perform an effectual forensic analysis of DMG file, the forensicators usually deploy professional forensic tool such as MailXaminer.
The software enables dedicated forensic analysis of DMG files even when the message storage source has been deleted permanently. This is the strongest feature of the software that enables the forensicators to restore the DMG file data, view DMG files in Windows and perform further investigation on it. The forensic experts can recover the data and build the artifacts in their native form, without compromising with the data integrity at any stage of the investigation.
Adding DMG File
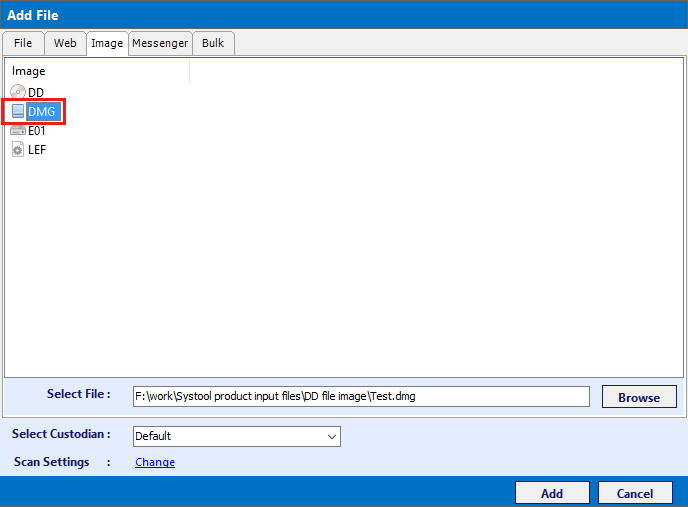
Scanning of DMG File
Once the DMG file is selected, it is completely scanned by the software.
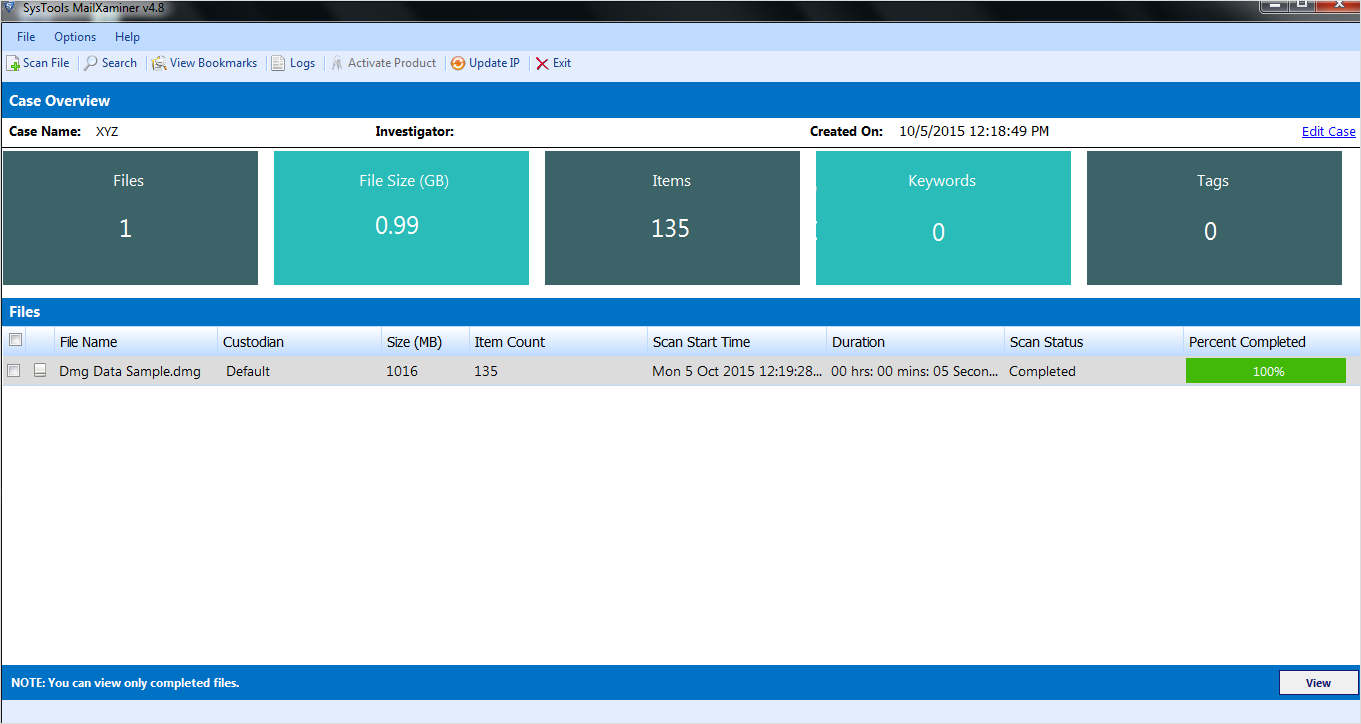
Root Structure of DMG File
Once the DMG file is successfully scanned, the software displays the entire root structure of the DMG file on the left pane. All the kinds of files stored in the DMG fie can be previewed and selected from the root structure.
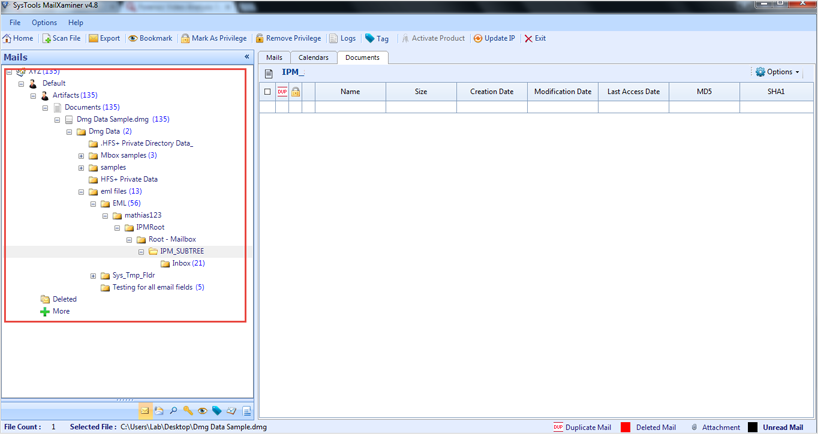
Select & View the Embedded Files of DMG in Windows
In the generated preview, you can see the EML and MBOX files being shown separately. If you click on MBOX and EML, the entire IPM Root AND IPM-SUBTREE structure is displayed.
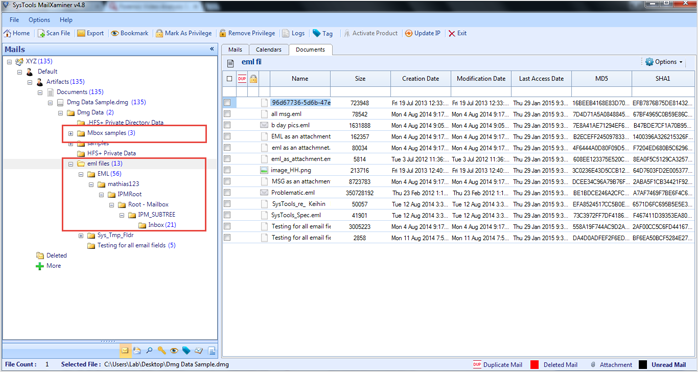
Note: IPMRoot is the main root folder that contains the root structure of the selected file. The IPM_SUBTREE contains folders like inbox, outbox, sent items, etc. We can say it is the child folder of IPM Root folder and folders like inbox, outbox, etc. are its grandchildren folders which contains messages.
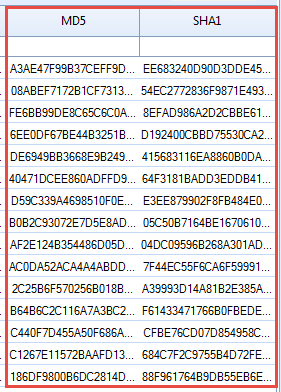
MD5 & SHA1 Hash Values
The software generates a MDF and SHA1 hash values of each message stored in the MD5 file. These hash values enable the forensicators to prove that no fiddling has been done with the evidence during the investigation.
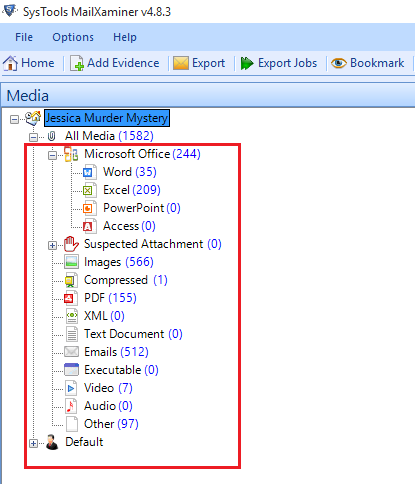
Examining Embedded Attachments
With the software, you can separately examine the associated attachments of the messages stored in the DMG file. All the attached emails, videos, images, audios, etc. are listed along with their count.
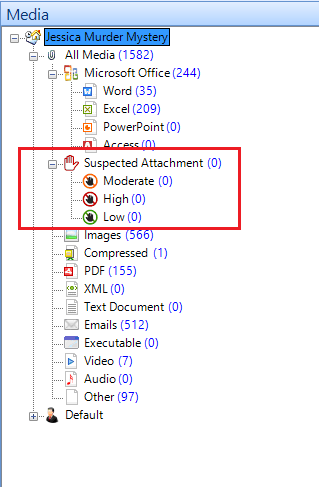
Suspected Attachment
MailXaminer lists all the suspected videos and images under a separate option, Suspected Attachments. All the Videos and images, which contain information related to the suspect, are enlisted here according to the level of sensitivity.
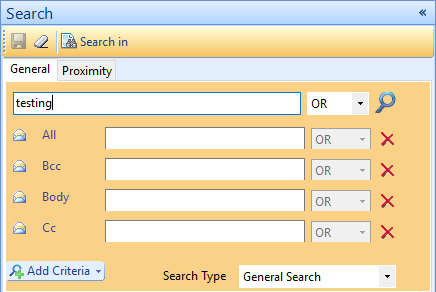
Search for Evidence – In – Depth DMG File Forensics
The search feature embedded in the software enables the user to perform deep searching of the DMG file to get hold of the evidence in a time efficient manner. The different search options provided, assures successful search of the evidence.
MailXaminer enables the forensicators to perform a full-fledged forensic analysis of the Apple DMG file. The variety of options provided by the software enables to get access to the evidence in a timely and precise manner.

