Zoho Mail Forensics Techniques to Analyze Zoho Mailbox
Overview: This blog will shed light on the analysis of Zoho Mail for email examination. It also focuses on the best-in-class approach which is utilized to effortlessly investigate the suspected emails from Zoho webmail.
If you are an investigating officer who is looking for a suitable solution to examine Zoho Mail, then this blog states the ultimate solution for the same.
Come, let’s get started by following the best tactic to perform Zoho Mail forensics!
A Brief Knowledge About Zoho Mail
Zoho Mail Suite is a simplified web-based email application. It renders multiple features such as sophisticated email organization, option to collaborate with the team, and much more.
Then, What is Zoho Mail Desktop?
On the other hand, Zoho Mail Desktop Lite client is a free installable application that allows users to access Zoho Mail from the desktop/laptop system. This desktop client is synchronized with the web version that allows easy transition between both of them. Furthermore, Zoho Mail Desktop client can be easily availed for Windows, Linux, and Mac operating systems.
Why There is a Need for Zoho Mail Forensics?
Zoho Mail is a free email service, which provides unlimited storage capacity. As there is an increase in the number of users using the Zoho Mail application, it has also led to an upsurge in email attacks. Hence, there arises a need for Zoho Mail forensics to analyze and investigate the emails in depth. Moreover, by examining each attribute from Zoho mailbox, it will help the investigators to precisely track the motive behind the attack.
Now, the question arises on how to analyze suspected emails from Zoho Mail?
Different Traces Found in Zoho Mailbox Investigation in Web Browsers
During the Zoho mail analysis, the potential evidence can be either found in system files or in the web browser(s). The local file storage of a web browser used for logging in and out of the account might carry some traces such as:
- The activities carried out in the account
- Timestamp of login/logout
- Redirection to links
- History of the links/URLs visited
- Downloads performed on it/from the account
- Search words list
- Images
- Account credentials
Therefore, by analyzing the web browser activities, one can easily carve out the evidential data. Besides this, cache files of a web browser may consist of images of the visited web pages.
What All Can be Analyzed from the Browser Data?
The following are the lists of attributes that help to find out the suspected data.
- History
- Search Words
- Cache
- Download
- Cookies
- Last Session
- Login Data/Web Data
- Visited Links
100% Proven Approach to Perform Zoho Mail Forensics – Let’s Dig In!
Well, there are numerous email forensics applications that let users to potentially examine the email data file. However, most of them fail to support analyzing different email clients such as Zoho Mail. As a result, here we are going to introduce a foolproof solution to examine Zoho mailbox using MailXaminer.
By availing this utility, one can efficiently refine the doubtful emails using its varied customized options. The tool helps to perform powerful search operations, provides support for Zoho database analysis, investigation of emails using multiple preview options. So, the features incorporated in the software are countless.
Isn’t it worthwhile software? Let’s proceed further by understanding its working procedure!
Zoho Mail Forensics with Advanced Software
When it comes to analyzing Zoho emails, this Email Forensics Software works wonder by examining every minute of email attributes in a thorough manner. Below-mentioned is the steps to effortlessly perform Zoho Mail forensics.
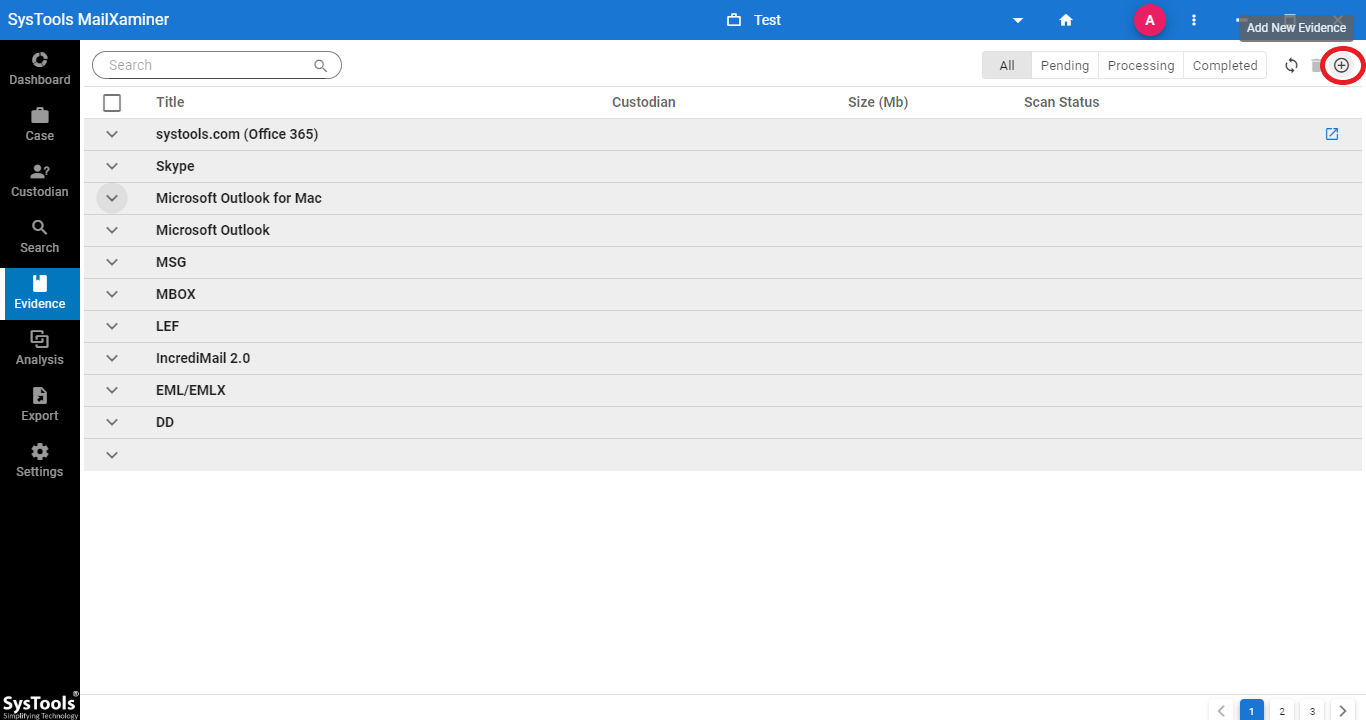
Step 1: To begin with, you need to click on Add New Evidence button to start Zoho mail analysis.
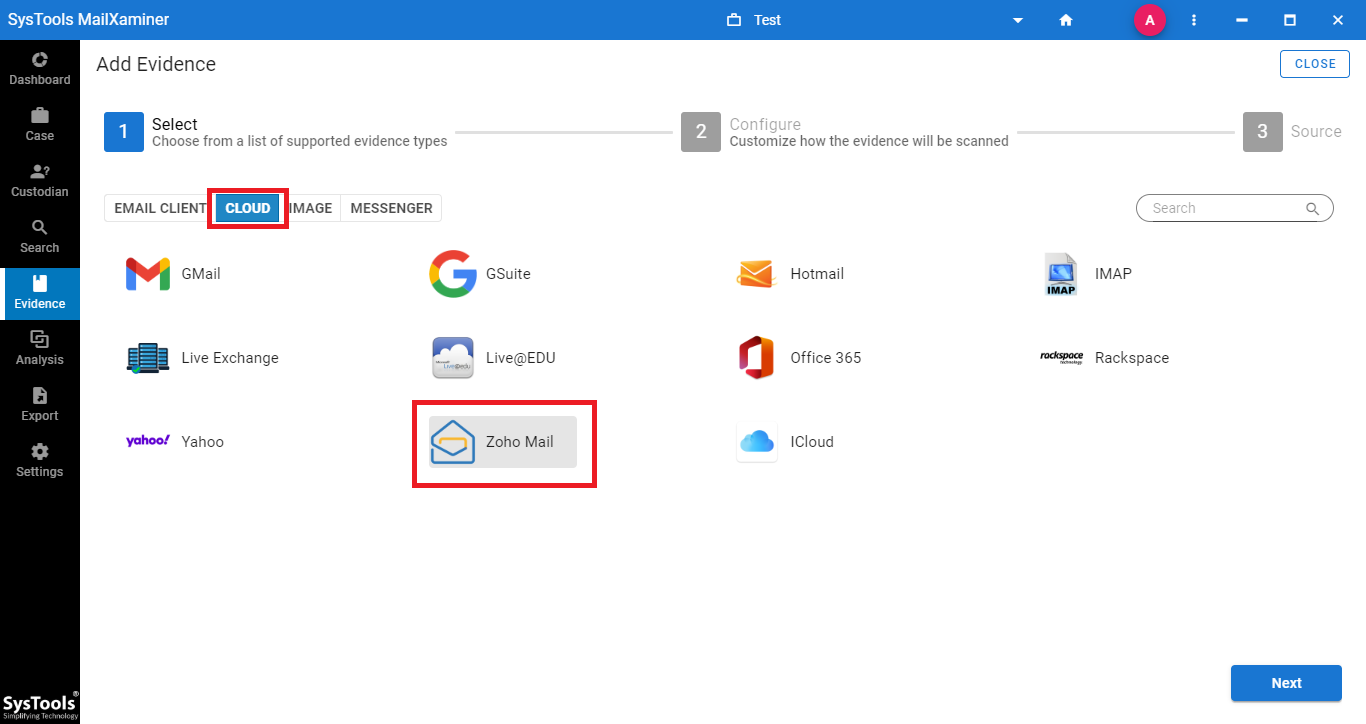
Step 2: From the window, navigate to the Cloud tab and select Zoho Mail from the given options. Now, enter the Zoho Mail credentials into the software.
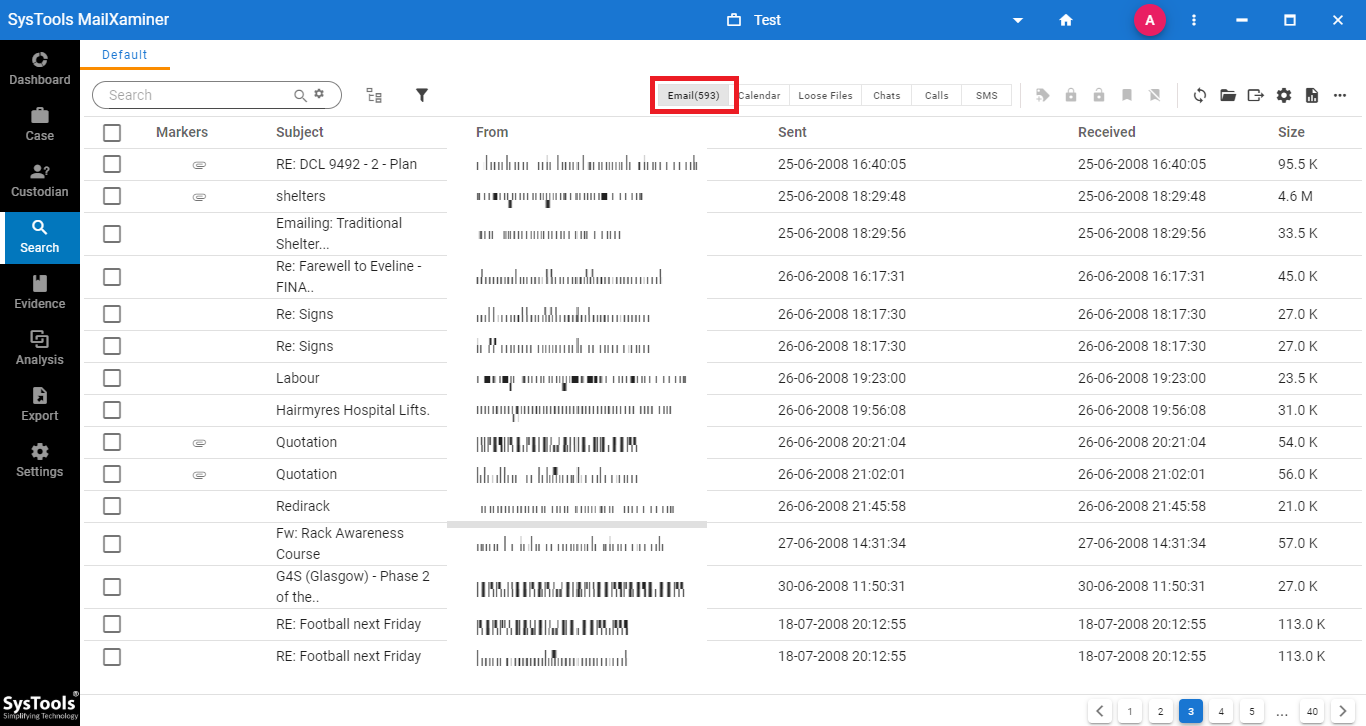
Step 3: Now, the software will enlist the entire emails which belong to Zoho Mail. One can efficiently search the suspected emails using the powerful search functionality.
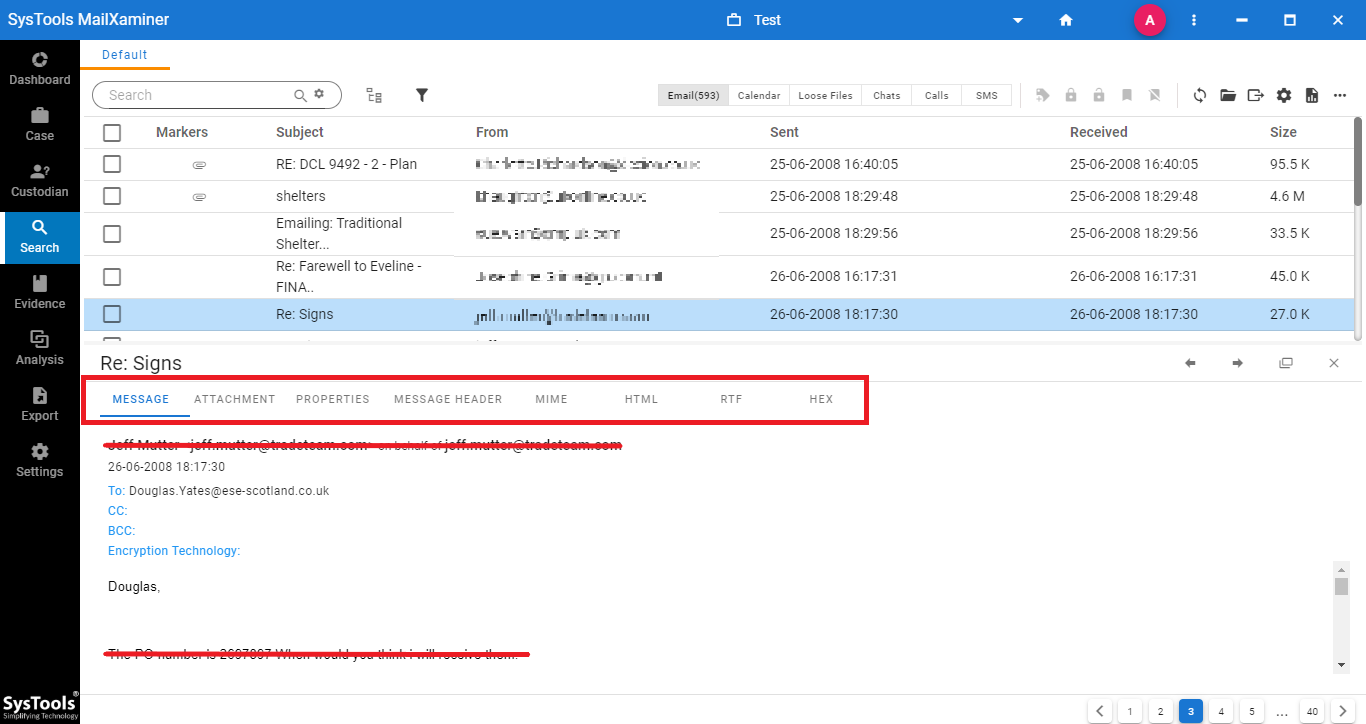
Step 4: Upon selecting individual emails, the software provides a preview in different view modes such as Message, Hex, Properties, Message Header, MIME, HTML, RTF and Attachments. Using these preview options, investigators can smartly analyze Zoho mailbox.
Step 5: While exporting the suspected emails, the software allows to export of selective emails by marking the checkbox associated with each email. Then, click the Export button.
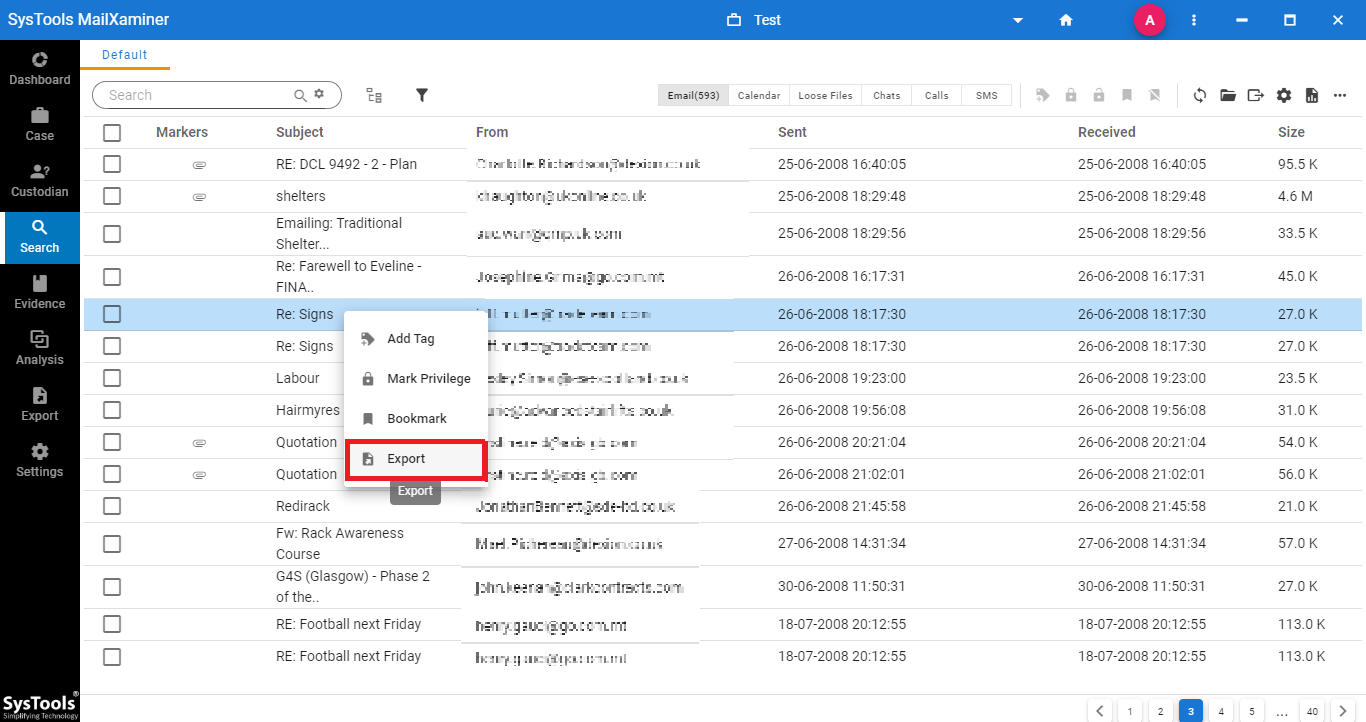
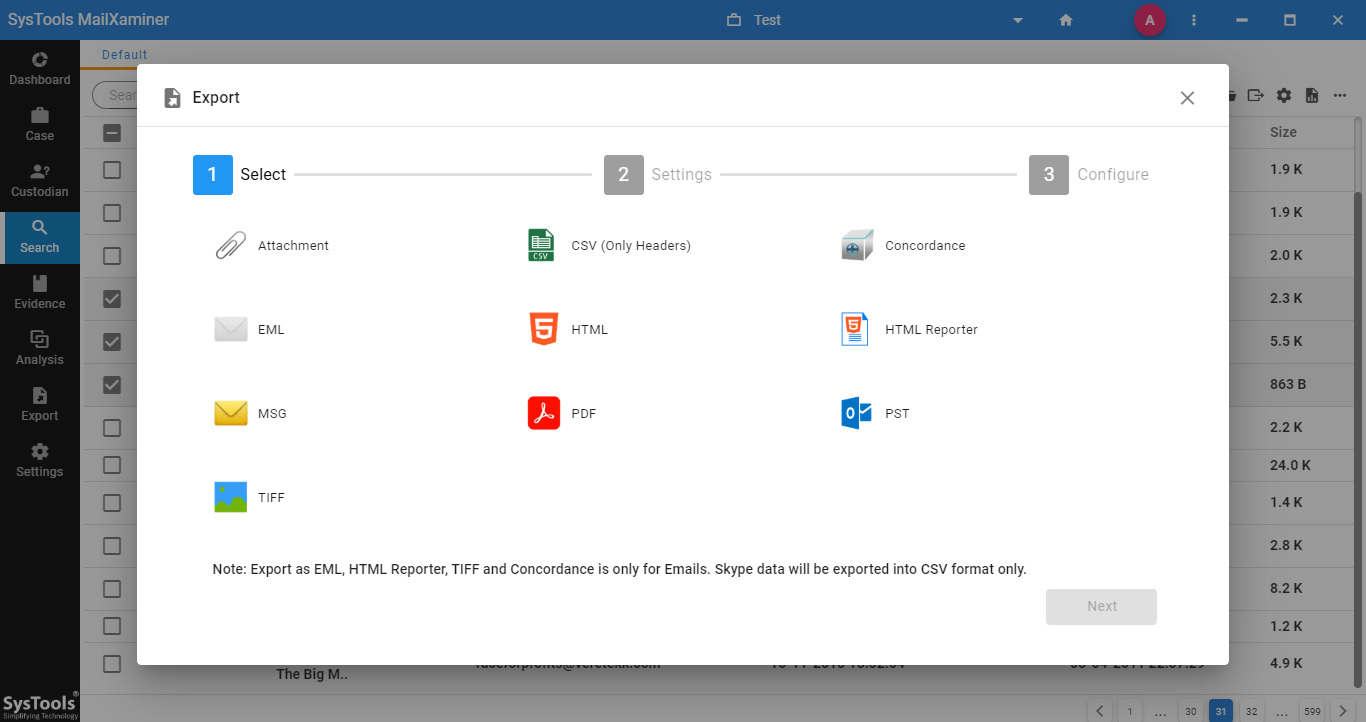
Step 6: Under Export Options, the software provides various export file types wherein users can avail to convert their Zoho emails to the desired file format.
Why Use Zoho Forensic Software?
This is one of the most genuine questions that may arise in the mind of the users before buying investigation software.
Have a look at some of the highlighted features offered by the tool mentioned below.
- Examines emails from 20+ email file formats
- Provides advanced keyword search options
- Supports investigation of Zoho database file
- Facilitates smart analytics options
- Analyze un-editable files using OCR technology
- Examine obscene images using Skin Tone analysis
- Easily investigate corrupted/encrypted/deleted email files and much more!
Time to Sum Up
To overcome the mind-scratching situations which the investigating officers face during Zoho email header forensics. We have described an effective yet proven solution to examine emails from Zoho Mail using the versatile email forensics software.
Using its exclusive features, one can efficiently analyze Zoho Mailbox messages without facing any kind of technical complexities. The best part of the software is that it renders easy-to-use interface enabling non-tech savvy users to easily examine the emails.

