E01 Forensics – Examining Structure and Storage of E01 Image File Format
In order to create a backup or imaged file of a USB drive, hard drive, etc., Encase forensic software is utilized which produces the backup file in E01 format. E01 file type is a forensic disk image file format, which is legally denoted as the Expert Witness Format (EWF).
The file was introduced by EnCase from Guidance Software. The major functionality of the software is to create an image file from the suspected hard drive/external storage media, etc.
Forensic imaging is considered to be the most crucial stage of the digital forensic investigation process. According to the norms of digital forensics, the process to acquire evidence in its original form is not considered to be right from a legal standpoint. It may have a high chance of evidence tampering or spoliation. Besides this, there is always a possibility of leaving their traces behind the litigated data, no matter how carefully the acquisition process is being executed.
As a result, cloning or imaging of the evidence comes into the picture, which is of utmost importance to maintain the artifact integrity.
Encase Forensic Image File – Role of EnCase Disk Image
From the above section, now we are pretty much familiar that E01 (Encase Image File Format) creates an image of various acquired digital evidence. The file tends to store a variety of evidentiary contents such as disk image that consists of each bitstream of the seized disk, existing memory, volume imaging, and logical files. Additionally, the Guidance Software owned E01 image file format consists of checksum for each block and footer with MD5 value for the complete bitstream on the disk.
An Overview – EnCase E01 Image File Forensics
Digital Forensics comprises of numerous fields such as server forensics, network forensics, email forensics and much more. The basic motive behind performing forensics is to examine the entire data types that store information electronically.
EnCase 5 when launched proved not to be much efficient as a forensic imaging tool. This is because it was not capable enough to tackle email data, which was the major challenge faced by the investigation officers.
With the launch of EnCase 6, the expectations to handle emails grew higher but the hurdle had not been removed yet. The version of EnCase was still unable to tactfully deal with email messages, i.e. the support was provided but only for a limited number of emails. Therefore, many other applications including FTK Imager arrived to serve online for the same imaging facilities and format (E01) but with improved capabilities. Soon after that, EnCase came up with the major advancements and has reached version 7.10 that even supports imaging tablets and smartphone storage.
Analysis of E01 Image Files
MailXaminer Email Examiner Software is one of the best Email Forensics Software that is widely used by the investigating officers for digital forensics investigation purposes. With the help of this software, one can directly process and analyze the email data along with attachments. It incorporates the functionality to examine raw image format files including E01 into the software panel. Users can use various inbuilt functionalities while performing E01 forensics to find the evidence in a smart yet efficient way.
In order to analyze E01 forensic image of email data, simply follow the below-mentioned steps using the proficient email forensic software:
- First of all, click on Add New Evidence. Then, a window will pop-up to Add Evidence. Choose the E01 file format from the Image tab to scan the file into the software
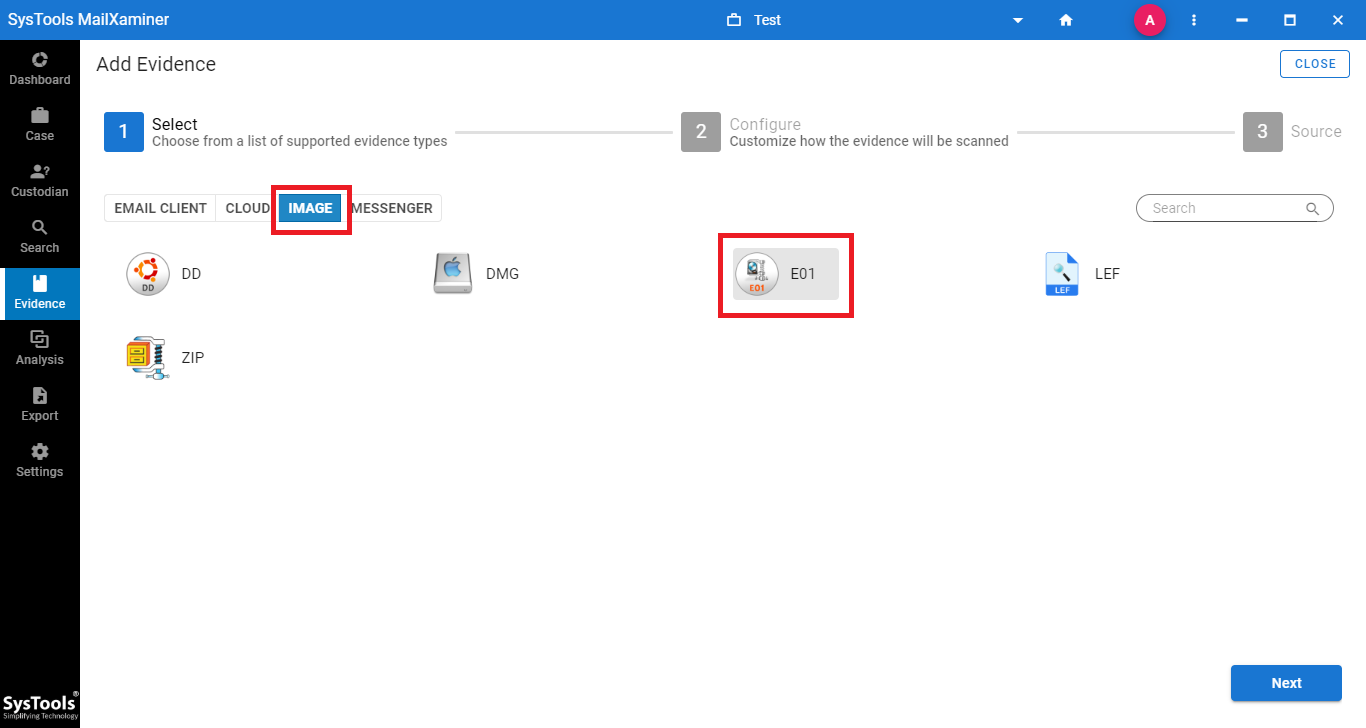
- On the Configure step, mark the checkbox corresponding to Only Loose Files under General Settings section and click on Next.
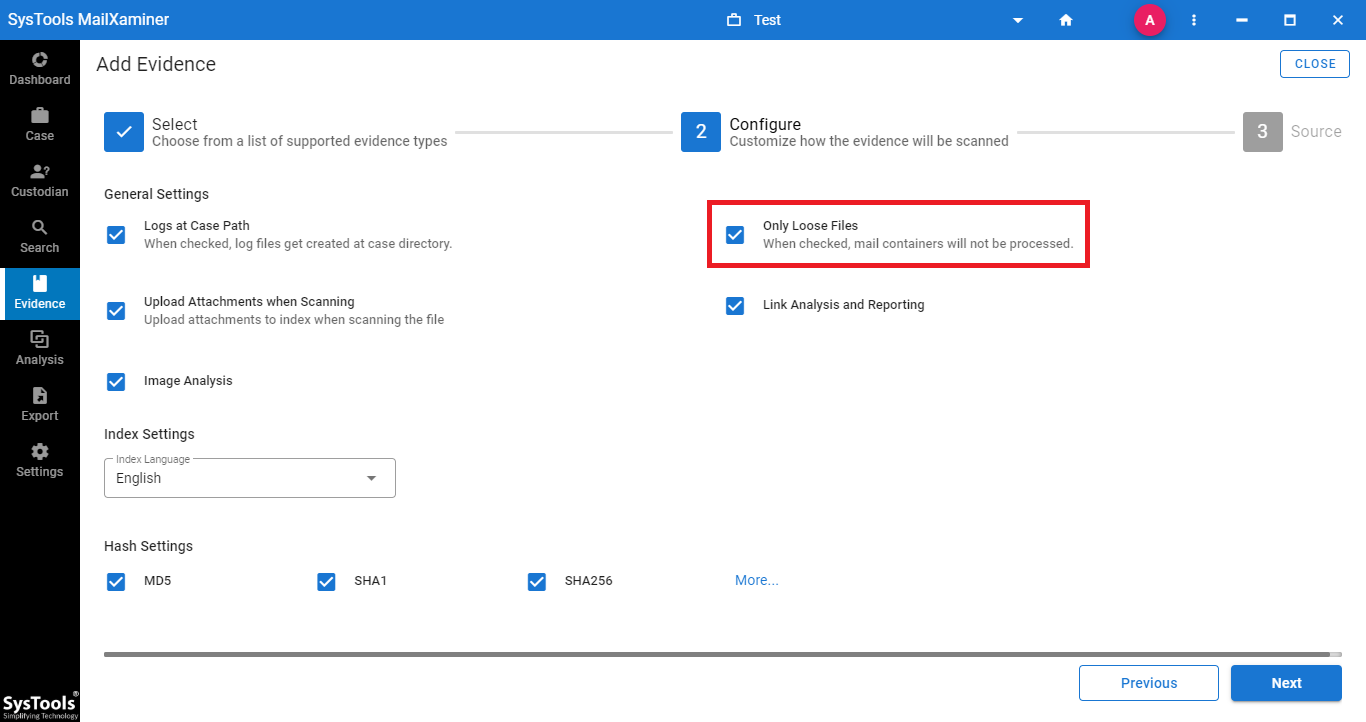
- After that, click Add File to provide the location of the file. Users can choose to import evidence files in bulk by selecting the Add CSV option.
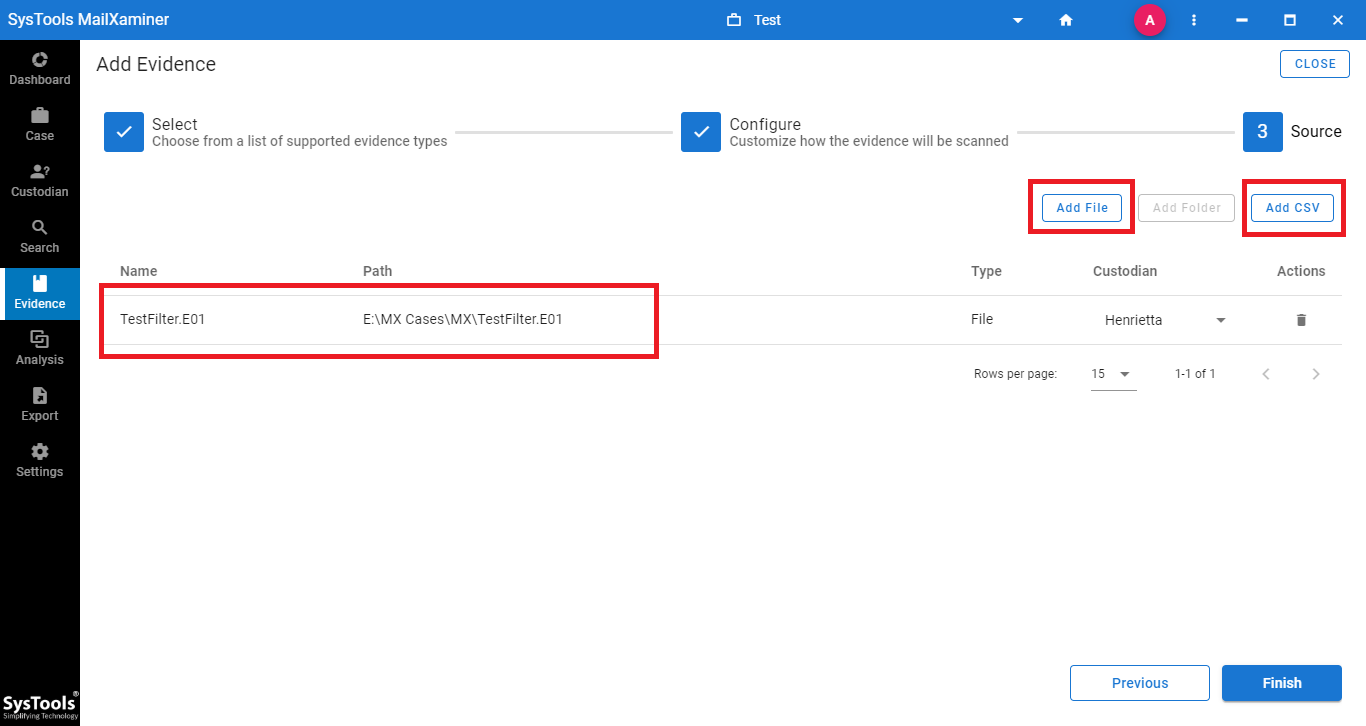
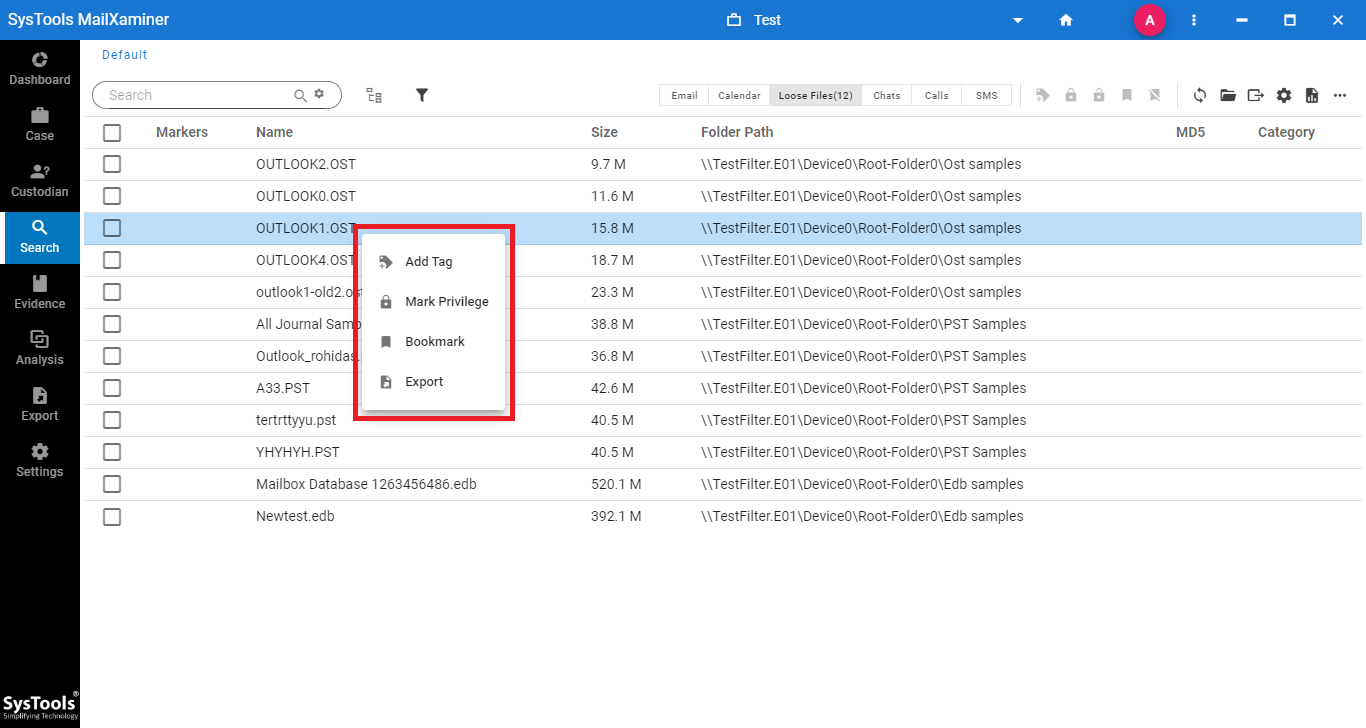
- Now, the files imported as evidence from the E01 file will be displayed in the Search section . Users can avail multiple options by right clicking on the emails, as shown in the below image. It provides the options to Add Tag, Mark Privilege to the Emails, Bookmark Option and Export Option.
- The software provides a preview of the evidence file by clicking on the file with attributes like Properties, Preview and HEX value.
Structure of E01 Image File Format:
- Every E01 image file type structure begins with the Header portion containing Case Information.
- A 64-sector block having a size of 32 KB acts as a separator between each data block. Additionally, it is interlocked with a Cyclic Redundancy Check.
- After that, the footer of the file containing the MD5 value of the data imaged within.
Structural Analysis of Disk Image File E01 Forensics
All the applications that are providers of E01 files are serving the same structure for the file format. E01 file forensics brings out the output of E01 structural analysis that helps to understand the E01 disk image file format for precise examination purpose.
The E01 image files stores whatever is found on the disk (external, internal, or removable). It can be in the form of data files, databases, or even system files. That is how an E01 file type stores data and this makes it unique in storage, structure, and accessibility too.
One of the major peculiarities about forensic E01 file is that it is only the file extension that changes and not the original file name. It divides the complete data into 640 MB of data chunks. Moreover, the file extension changes while the structure remains in one piece (i.e., E01, E02, etc.).
Closing Lines
Undoubtedly E01 is one of the preferred disk imaging file formats to acquire the data from the hard disk for investigation purposes. With this blog, we have highlighted the information that is stored and arranged within the E01 image file format. Moreover, to analyze and investigate the disk image file, this software is best for performing forensic analysis of a disk image file. It is exclusively designed in a manner to support documents of various types including E01 image files.

