Why Choose MailXaminer Over Free Email Forensics Tools?
With the development of the internet, emails have emerged as the most common application for communication, document transfers, and transactions from computers. But what occurs when email is used maliciously in fraud or cybercrime, to distribute malware in email, or send phishing scams? Attackers often embed harmful links, making URL analysis a crucial part of identifying and mitigating such threats.
One turns to Email forensics
The Growing Need for Digital Communication Analysis
Email forensics involves collecting, analyzing, and reviewing email data to detect fraud or misconduct. By identifying the origin of the mail, recognising the sender, going through the metadata for processes like fraud, breach or IP theft, forensic investigation finds the source of the person or the system sending out the harmful data.
It is an important digital forensic investigation technique that helps in finding the kind extent of crimes, identifying the security flaws and improving current security standards. It helps companies to identify possible threats like phishing, compromised credentials, or social engineering. Forensics provides information that courts or legal authorities can use, ensuring the client has an advanced legal database in cases of fraud or data breaches.
What Makes Message-Based Investigations Crucial?
There are various sources via which a user can apply Email investigations on the present data; the sources are open or paid.
Open sources offer a range of features supporting forensics, such as –
- Solution that extracts data without processing file systems or file system architecture by scanning files, directories, or disk images.
- Manage digital data in nearly any format of social network forensics, which involves examining digital evidence to retrieve data like URLs and addresses.
- We provide a histogram using compiled word cloud and commonly used email addresses..
- To protect the evidence it discovers, the kit safely scans the primary disk and a variety of file formats in a read-only fashion.
Free Tools – Capabilities and Their Boundaries
General Features Offered by Free Solutions
The features provided by the open-sourced software are helpful in looking into problems and trends at a surface level and to perform superficial analysis.
Where Basic Tools Fall Short
But they have limited functionality with the user interface, deep forensic data analytics, and lack user friendliness. They provide a slow, resource-constrained mechanics and a steep learning curve for new users. The majority of these are not suitable for complex network investigations, relying on pattern matching and may generate false positives. Free Email examination tools might lack features for comparing hashes or identifying duplicates, require specialized hardware, and may not be portable.
Moving Beyond Limitations with Advanced Solutions
In order to overcome these shortcomings, one needs to focus on software and tools which help in providing detailed results and robust outcomes. One needs to look towards more advanced and reliable email examination software built specifically for Email forensics, i.e MailXaminer.
A Purpose-Built Platform for Communication Review
This software stands out with its analytical capabilities, integrity of the digital evidence, and the presentation of the results in a legally and forensically sound manner compared to other software present.
Key Features that Give Software an Edge While Choosing an Email Forensics Tool
To understand what sets a tool apart, it’s essential to look at the core features that enhance forensic efficiency.
Powerful Search and Filtering Mechanisms
Users may search by a keyword, sender/recipient, subject matter, period, and more using its sophisticated search criteria. Deep-dive investigations are very effective and focused because of advanced search methods like regular expressions, fuzzy logic, proximity searches, and Boolean operators.
Deep Analysis of Data Headers and Origins
The program provides comprehensive information on the headers of emails and data, including time zone differences, IP analysis, and hop tracing. This aids in identifying the real sender by detecting fake emails and recreating the precise delivery path.
Analysis of Attachments and Links
Suspicious email attachments and hidden URLs are automatically identified and flagged by this software.
Recognition of Optical Characters
Images having text contained in them, such as screenshots or scanned documents, are frequently included in emails. Few forensic tools provide investigators with the ability to accurately determine and evaluate text from photos, as this software is built with advanced OCR analysis to know how to identify location from photo or any text included in the photo.
Managing Complex Cases with Multi-User Support
In law enforcement or business compliance teams, this smart solution’s role-based access restriction, tagging, commentary, and shared case review features are crucial for extensive or cooperative investigations.
Exporting Results in Reliable Report Formats
Audit trails, chain-of-custody records, email verification records, and all inquiry results are produced in court-admissible formats (PDF, HTML, and CSV). The reporting system is suitable for presentation in courtrooms as it ensures authenticity and reliability.
Controlling Sensitive Content with Privilege Features
Limit email transfers at the opponent’s end while displaying your list of supporting documents. The option may be used to select and privilege confidential information that requires protection.
Examine Calendar Artifacts
After looking at emails, experts can use the software’s built-in calendar analysis feature to look at the suspect’s calendar data. The scan settings tab should highlight the Calendar choices.
Verifying Data Using Cryptographic Hashing
The software’s forensic hash algorithm option allows and analyzing the artifacts in a database heap. Under the Scan Settings tab, choose to see and filter emails based on SHA1, MD5, and SHA256 hash values.
Table of comparison
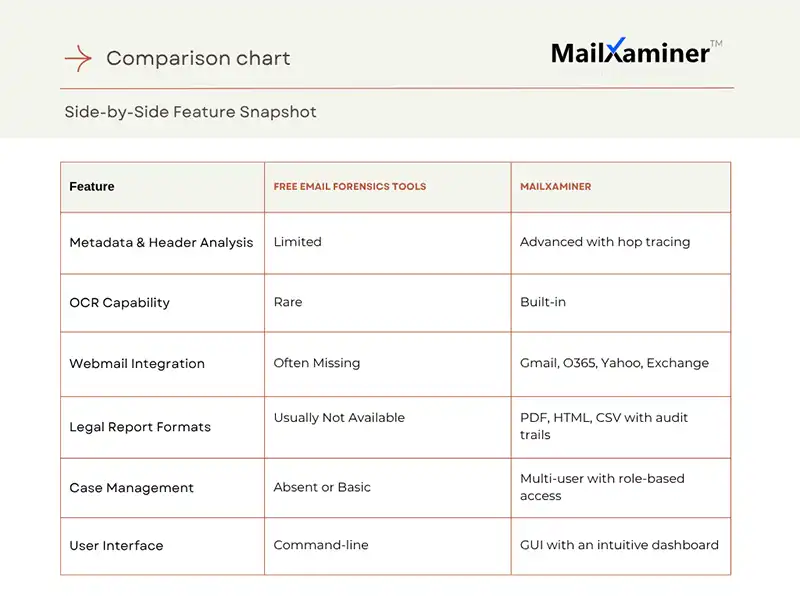
Wrapping Up
Free tools can be useful for basic checks, but they often come with limitations like slow performance, limited features, and a complex interface. Use a professional solution designed to handle complex investigations for more reliable and in-depth analysis.
Advanced tools like MailXaminer offer more accuracy, better reporting, and features that support teamwork and legal processes. It provides you with the next-generation level of technological benefit in one software. It consists of advanced link analysis and timeline analysis features, which make the investigation smoother and more concise. Choosing the right tool depends on your needs, but investing in a dependable and user-friendly solution ensures better results and saves time in the long run.

