Gmail Email Forensics Analysis – Explore Internet Header
Being the popular emailing platform with more than 1 billion users, Gmail has, unfortunately, become the prime medium for executing online fraud. Studies reveal that approximately. While doing forensic analysis of emails, studies show that 60 to 70% of digital frauds are happening through Gmail. Thus, to frame the culprit and trace out digital evidence, performing a foolproof Gmail personal account mailbox analysis is the first thing an investigating officer needs to do.
But, what are the techniques one can follow and the tools that can be used for successful analysis? Let’s study them in detail.
Forensics analysis of Gmail is no different than other emailing platforms. It’s just that as an investigator you must know different techniques to follow for the investigation.
Different Possible Ways to Use Gmail Forensics
Various ways exist to execute forensic analysis of Gmail emails. Email Header Forensics, Bait Tactics, Gmail Server Investigation, Network Device Investigation, etc. are a few to name. However, to perform an in-depth investigation of every minute of email data, it is recommended to use automated software. It can not only speed up the process but also give an accurate result in a court-admissible format.
Gmail Email Forensics Analysis of Internet Header
Header analysis is one of the prime things an investigator does while gathering digital evidence. And, whether an email contains or doesn’t contain an attachment, analysis can be done for either of them.
- Analysis of Gmail Email without Attachments
Gmail email internet header forms one important and valuable source of information in the forensic analysis of emails. It consists of the actual sender’s address, the recipient’s address, and the exact date & time when the email was sent and received. Apart from that, the server paths the message took, IP address, etc., can also be identified. The metadata can also be stored on the server, which can be retrieved later. Though it’s possible to manually trace header information without the existence of an email message, using professional software is always suggested. - Explore Gmail Mailbox for Analysis with Attachments
For Gmail emails with attachments, the internet header also includes detailed information about attachments such as images, text file attachments, etc. For example, the metadata content of digital images contains information like picture size, color, image resolution, creation date, and other details. Whereas metadata of text documents includes information about the length of the file, author, written time and date, summary, etc.
Here is the procedure to perform Gmail email forensics analysis manually.
Step 1. Extract Header Information
Follow the steps below to know the header details for the Gmail email message.
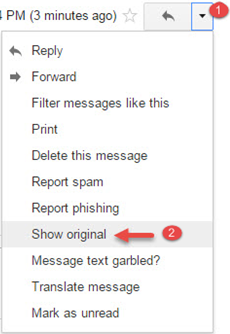
Note: The process to find headers of an email in a Gmail account can be summarized in the below picture.
- Open the Gmail email message you want to investigate.
- Now, click on the down arrow located next to the reply button.
- Choose the “Show Original” option.
Step 2. Extracting Information Through Gmail Email Analysis
As a part of Gmail email forensics analysis, the description of each section of the header is mentioned below:
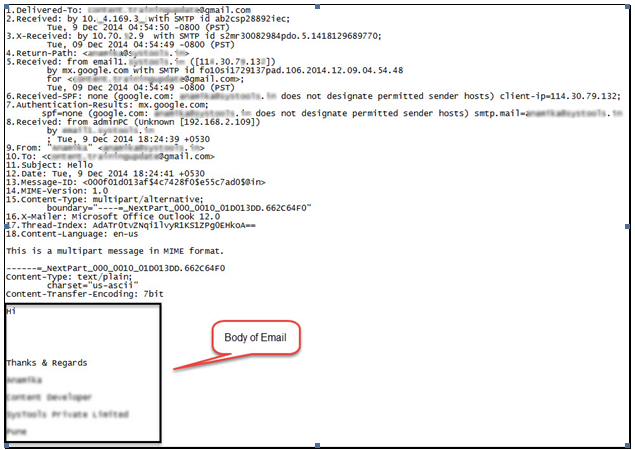
Delivered-To: This line displays the delivered email address i.e. the destination or receiver’s email address.
Received: This line shows the time the message reached the server of Gmail i.e. the receiver’s /destination ID’s email provider.
X-Received: This line displays the X-Received information. It contains the IP address of the name of the server used to send email.
Return-Path: This line displays the Return-Path and shows the address from which the message was sent. Technically it can be said that it contains the address recorded by Mail / Message Delivery Agent (MDA) from the MailFrom SMTP command. But the problem is that this information can be spoofed easily by an expert criminal. Hence, it is not considered reliable and taken into account until examined by professional analyzers during Gmail forensics.
Received: This line in the header shows that the message was received from the sender’s email provider by a Gmail server on a particular date and time i.e., received date and time.
Note: Stay tuned to learn an automated approach for Gmail personal account mailbox analysis.
Received-SPF: The line displays Received-SPF, which represents the type of email service used for sending the email message. It also includes an ID that can be utilized to analyze logs from transmitting mail servers. This helps in examining the legitimacy of the email whether it was sent from the same service or not. Moreover, if the ID is not available, then there are chances of an email message being spoofed.
From, To, Subject, Date: These lines display the date and time when the email was composed, the sender’s email address, the destination email ID, and the subject, respectively. All information displayed here is entered by the sender except the date and time at which the email application was composed.
Message ID: It is a globally unique string assigned to a particular email by the sender’s email provider for the identification of an email message. Message ID forensics can be done to track the specific email on the initiated email server which consists of email logs information.
MIME-Version: It displays the Multi-Purpose Internet Mail Extensions message format, which plays a significant role in the MIME header analyzer. Several pieces of information and evidence can be extracted for further investigation. Here, in this case, the version of the mail is 1.0.
Content-Type: It displays the Content-Type, which stores information about MIME Header fields. It describes multiple aspects of the body of the message, including signatures.
X-Mailer: It displays the X-Mailer header information. It identifies the software handling the email at the client side or the sender’s side. The information about the client PC of the sender can then be used by the investigating officers to devise an effective plan to reach the culprit.
Step 3. Correlating Collected Information
While implementing the Gmail email forensics analysis, the scattered data is obtained. The collected information can be correlated to make the collected data useful for the study of forensic analysis of email artifacts. Correlating the gathered information is an important step that forms the basis of an email forensics study.
This is because the gathered header information yields the entire document and citations. Nevertheless, the collection is the first step in the investigation process, but their correlation is indeed necessary. The yielded records, such as date, subject, recipient, sender, IP address, etc., should be interrelated because, without interrelation, exact information cannot be attained.
A Professional Solution to Perform Gmail Email Forensics Analysis
MailXaminer is one of the trustworthy and reliable email analysis tool to easily analyze Gmail email data during digital forensic investigations. It is 100% error-free software that can be quickly installed on the system for email analysis. The software provides various options to carry out an in-depth analysis of Gmail attributes efficiently.
Further, it proves to be the best in the market for its different features.
1. Identify Gmail Email Evidence In a Forensically Sound Manner With Different Views
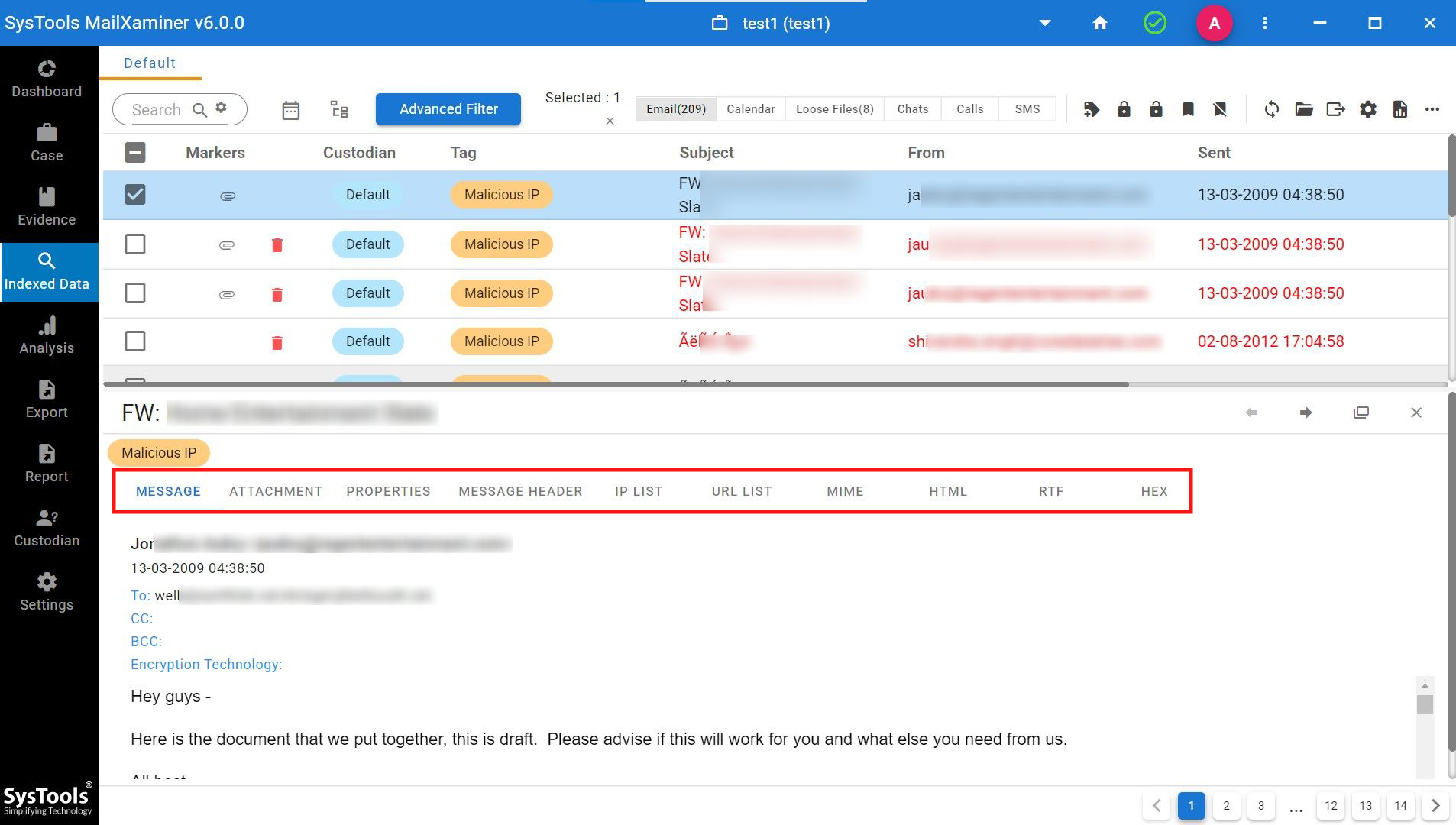
The professional software provides an option for forensic analysis of Gmail artifacts in different preview modes. This includes “Mail, Hex, Properties, Message Header, MIME, Email Hop, HTML, RTF, and Attachments.” Each view offers different information corresponding to the email message. These different views help forensic experts to find and extract hidden information from Gmail data smartly.
- Mail: This view provides information on email messages with their common header data such as “Path, From, To, Cc, Bcc, Subject, Attachment”. This Gmail email forensics view provides information from the user’s perspective.
- Hex: This view helps the digital forensic expert to examine the email data in the hexadecimal value. It provides the offset value, hex code, and text value of the email data. Mapping the character in hex code will help to identify whether anyone has ever tried to change the content of the Gmail message.
- Properties: It provides a short view of the Gmail information such as “Body details, Dates, Message flags, Recipients, Represent sender, Sender details, Subject & Additional information”. This will help to investigate officers to obtain the summarized data to fasten the email analysis process.
- MIME: This email view provides the inner details of the email messages and also includes the textual or non-textual attachment & header information.
- Email Hop: It will help to analyze the path of the email message. It shows the information such as router, gateway, and switches through which the email data has been passed. This will help to clearly understand the path between the email source and destination.
- Message Header: This view of the software provides header-related information of the email data such as “Sender-Receiver Address, Message-ID, Feedback ID, MIME-Version, Content-Type, Cc, Bcc, etc.”
- HTML: This will provide the HTML script view of email data. This will help the investigating officer to examine the Gmail email in different browsers. It will also help identify if any changes have occurred in the data.
- RTF: This view helps to analyze the font and formatting of the email evidence if it is available within the email. This view helps to recover the email evidence by comparing it with the original email.
- Attachment: This view provides the list of attachments available within the respective email message. Also, it allows us to preview & analyze the attachment in detail.
Here is one screenshot for you from the software dashboard
2. Multiple Keyword-Search Options for Forensic Gmail Artefact Analysis
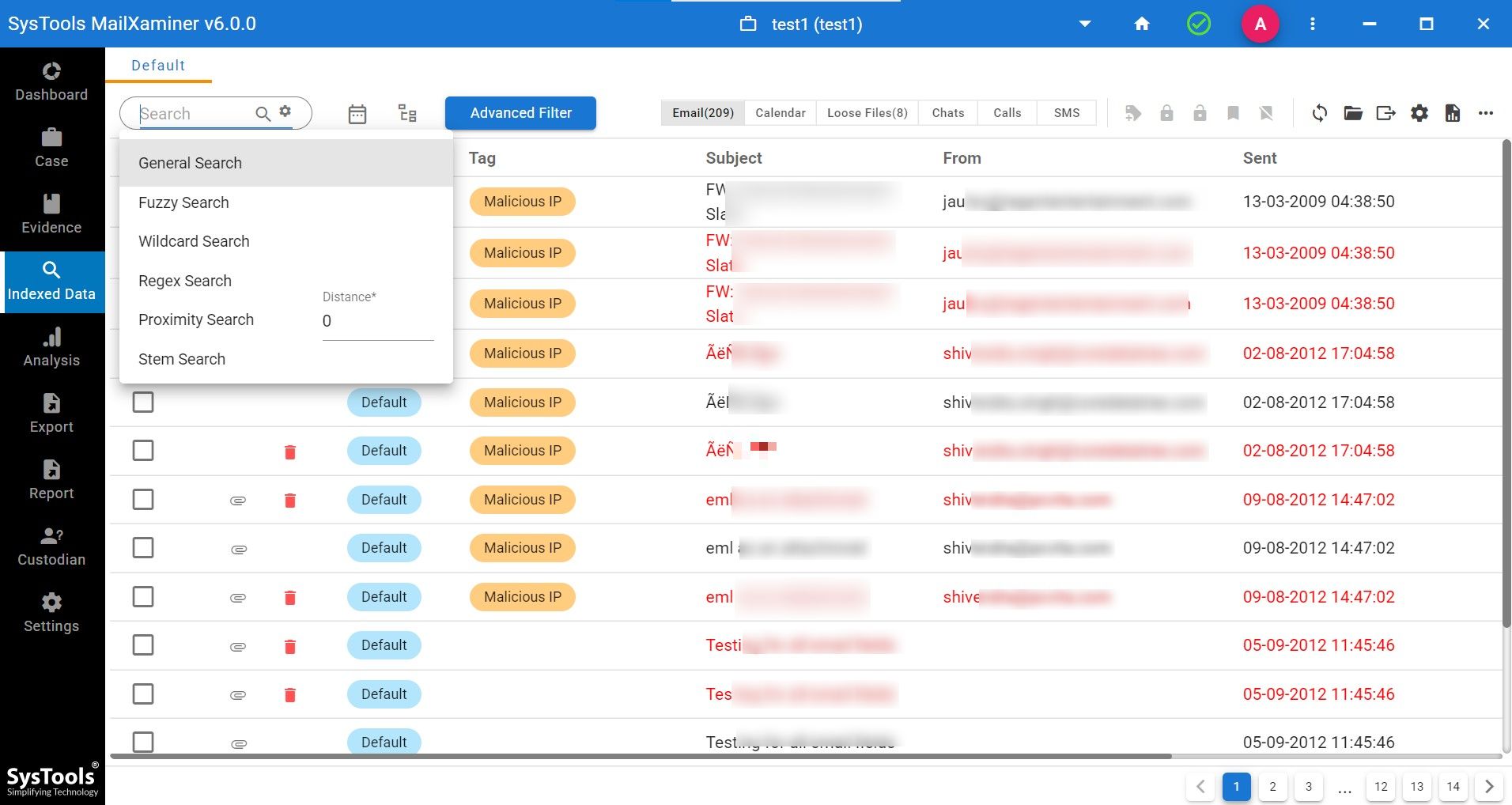
The software facilitates an amazing search option that helps the investigating officers instantly fetch the results out of bulk Gmail emails.
This includes General Search, Proximity Search, Regular Expression, Stem Search, Fuzzy Search, and Wildcard Search. While availing any of these search operations, one can also make the best use of logical operators like “AND, OR, and NOT”.
3. Find the User’s Relation Using Analytics Functionality
Using the analytics feature, one can track the frequency of words or emails which are connected between each email user. This will help the investigating officers to efficiently find the relationship between the users. The various options that fall under the analytics option include Word Cloud, Timeline Analysis, Link Analysis, and Entity Analysis.
- Link Analysis: It enables the investigating officer to detect Gmail email user relationships. It provides the connection between particular users for the specified keywords.
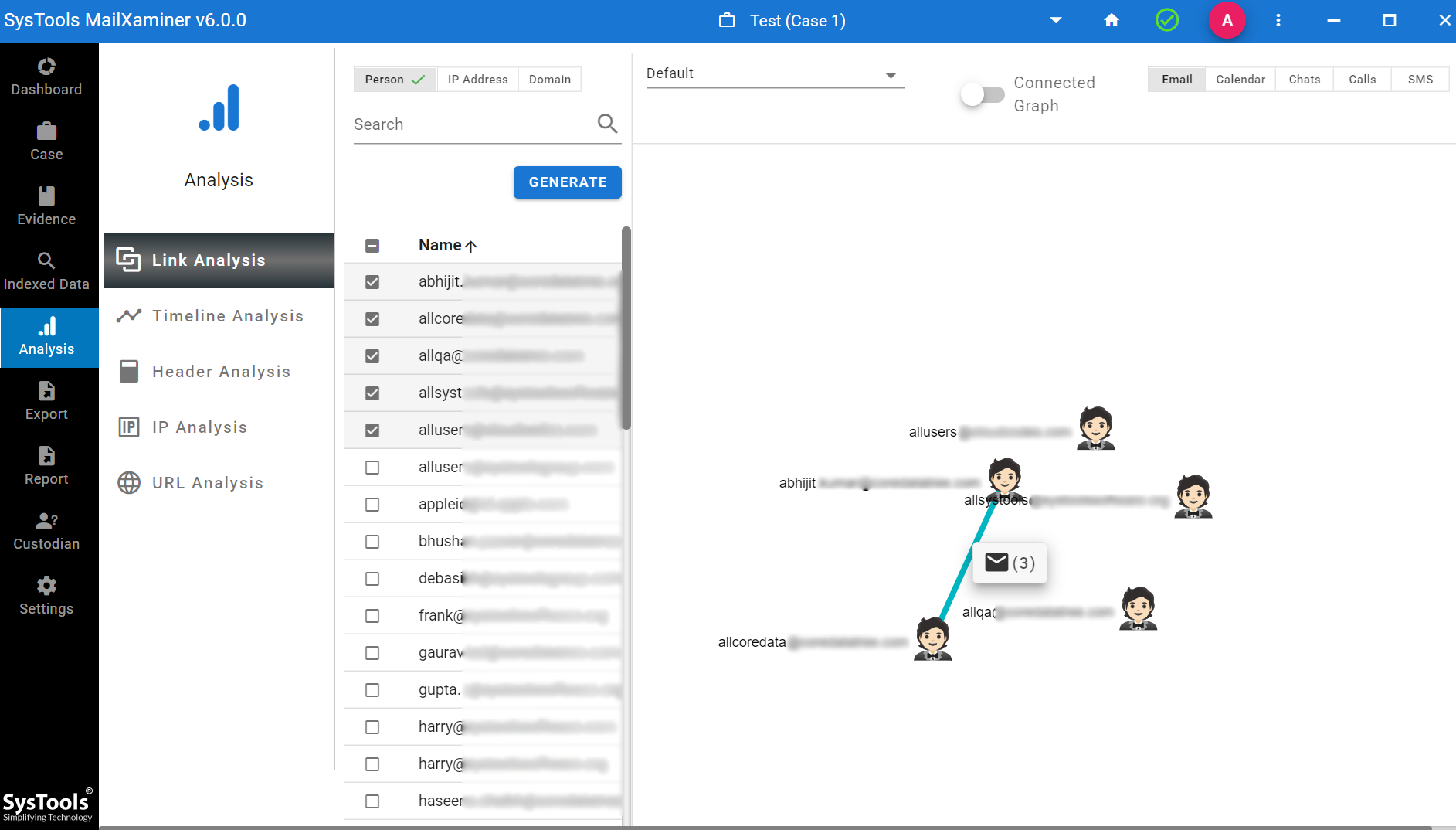
- Timeline Analysis: This helps in the forensic analysis of emails and finding the relation between the users & the frequency of emails on the basis of time. It provides the result in Year, Month, and Date with a graphical representation.
- IP Address Forensics: It renders a representation of all the listed IPs used for any email communications between the gmail account.
- URL Analysis: It provides the flexibility to analyze the URL consists of all the emails marked as accused or those emails which you need to investigate.
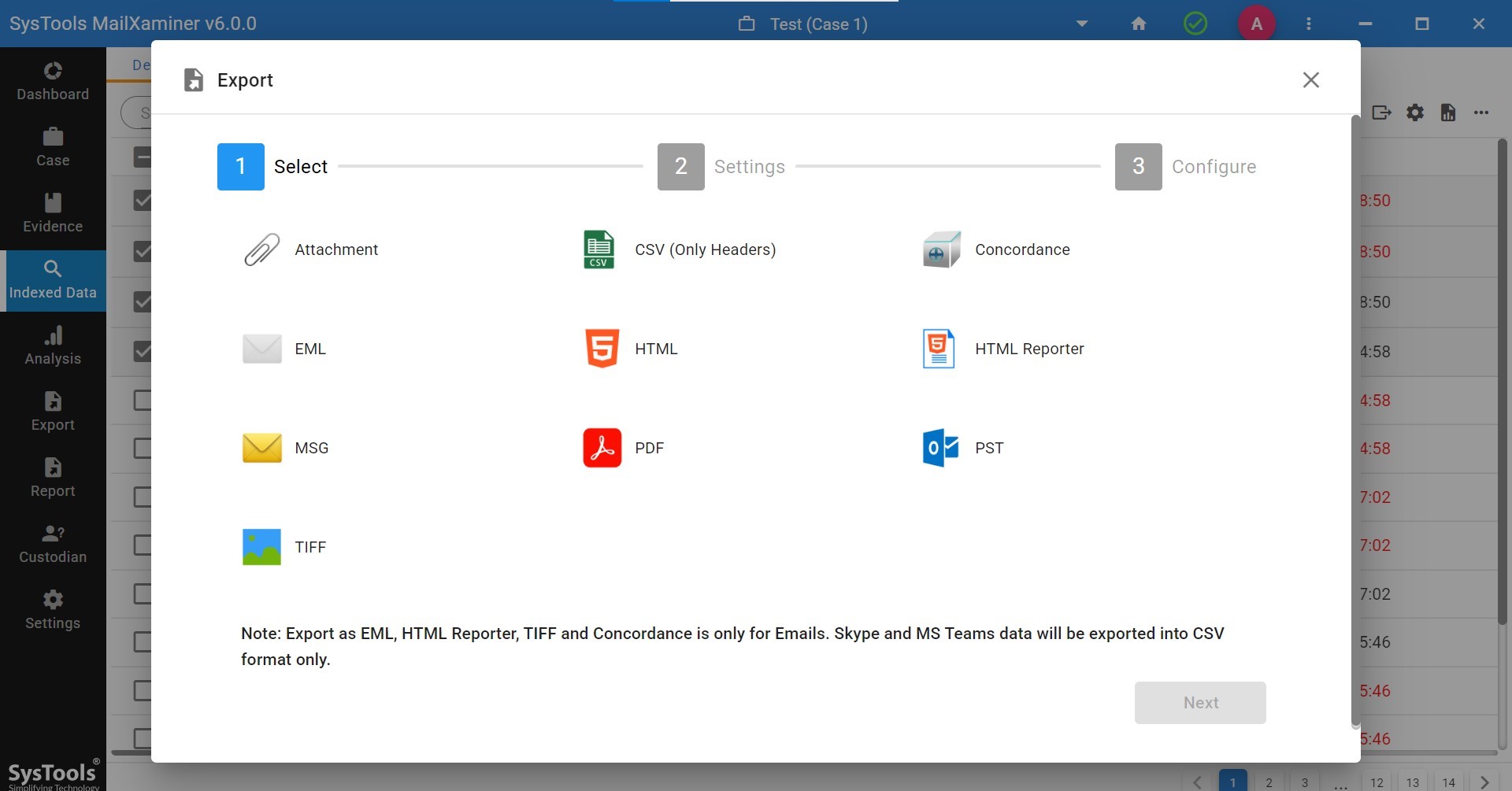
4. Extract/Export Digital Evidence in 20+ File Formats
Even though you examined the evidence of Gmail emails, you can still export the result in more than 20 file formats after analysis. The tool supports multiple extraction formats such as EML, MSG, TIFF, PDF, PST, HTML, CSV, DAT, and more. Also, you can customize the entire export process as per your requirements.
How Can You Use The Professional Tool for Gmail Email Forensics Analysis?
Using the tool is in fact very easy. Here are the detailed steps you can follow to examine Gmail email evidence.
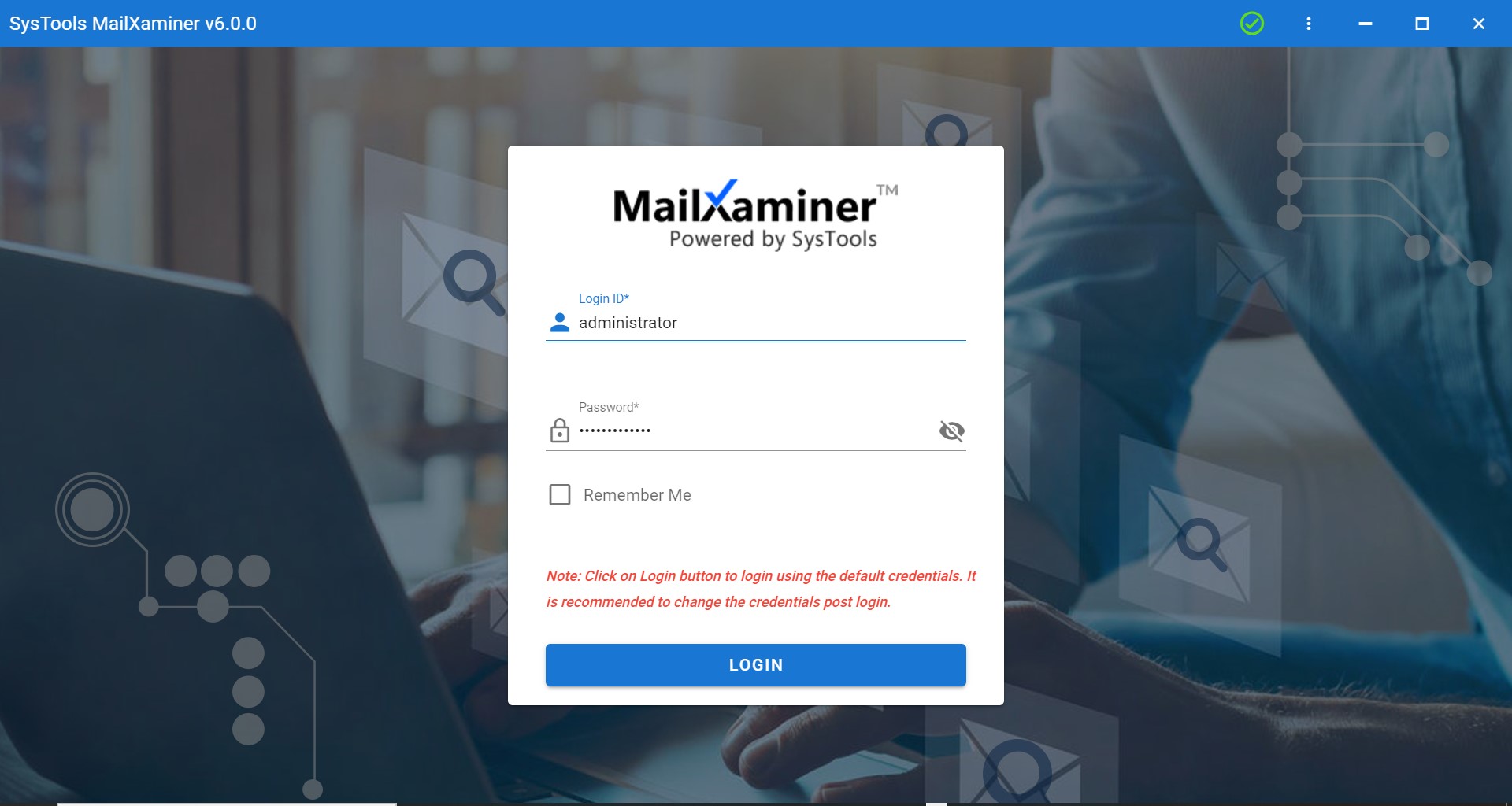
1. Launch the software on your system and enter the login credentials as “administrator”.
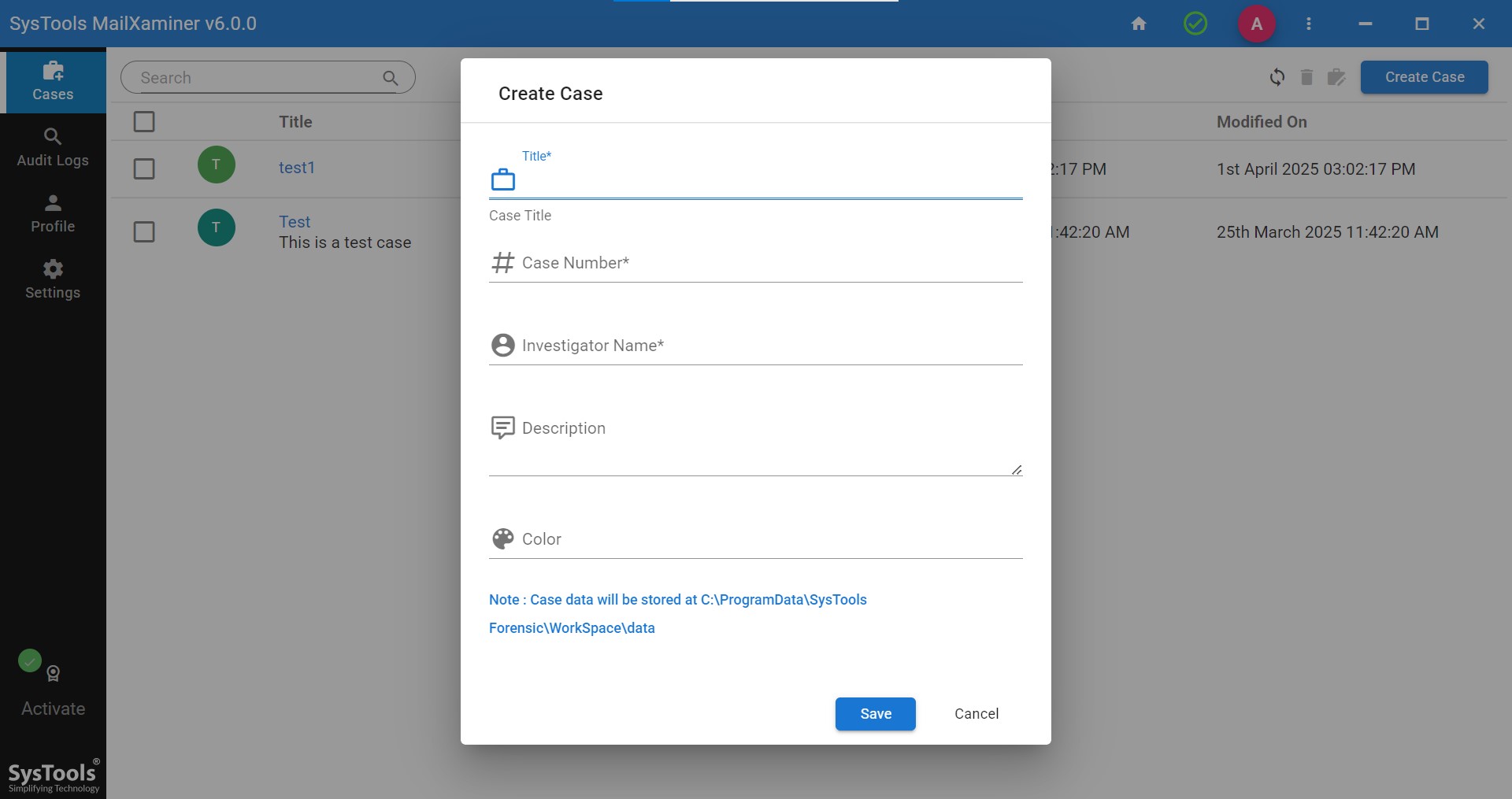
2. After signing in, click on the Create case button as seen in the screenshot. Fill in the necessary details and then click on the case you created.
3. Once you click on the case you newly created, you will be redirected to another window. There, click on the ‘Add New Evidence’ button as shown in the picture.
5. After that, select the Email client.

6. Then, select the required options and customize how you want the evidence to be scanned.
7. Now comes the part where you can add the evidence file to the software by clicking on the ‘Add file’ option.
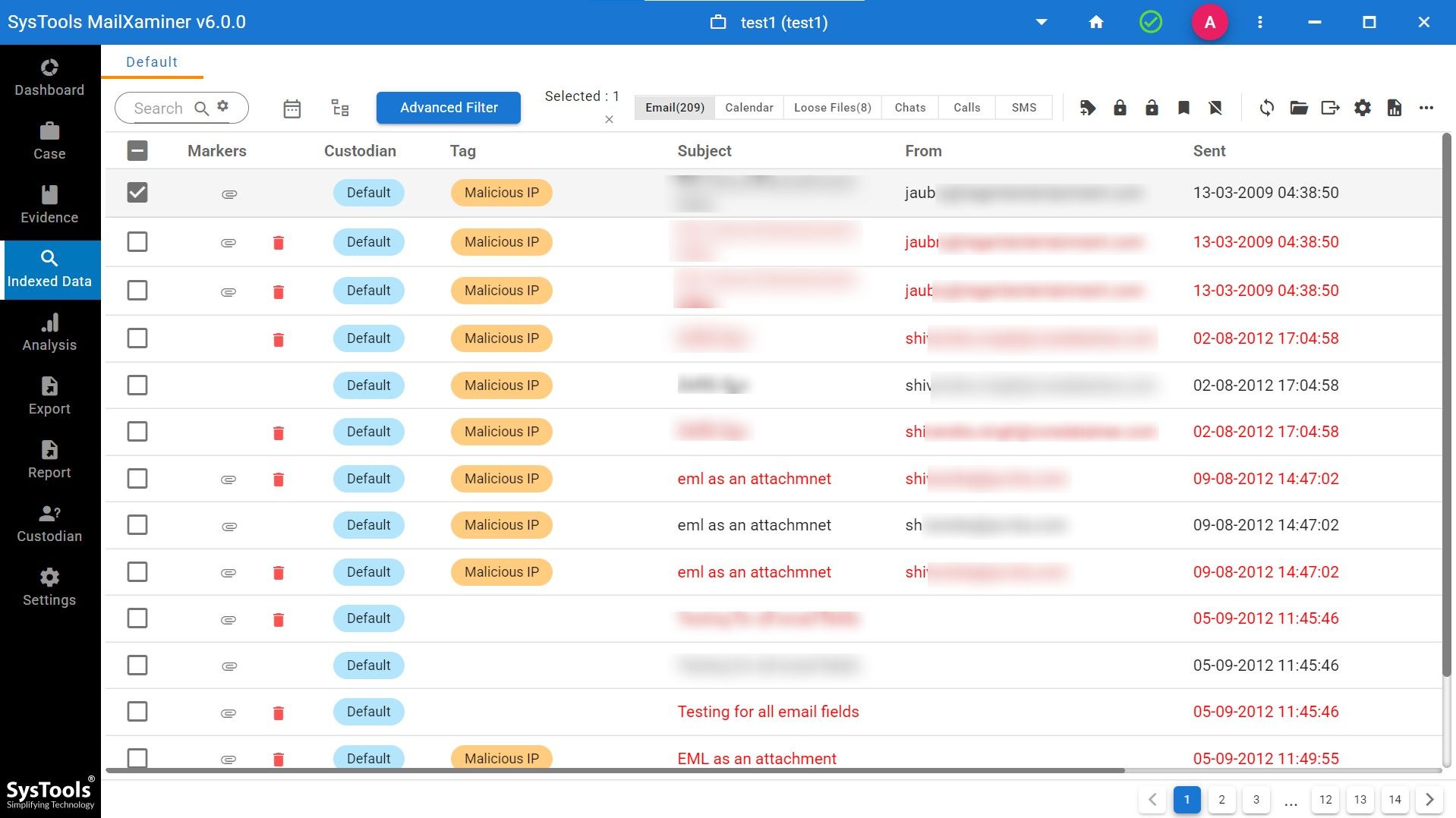
8. Once the file is scanned, you can view the emails (including deleted ones) and start your analysis. This software also allows you to investigate suspicious email that you have added as a file. This will show you information in the tag, as you can see in the screenshot below.
9. After a thorough Gmail Analysis, you can export the result by clicking on the export icon. You will be provided with the different export options.

10. Apply the desired customization before exporting the result.
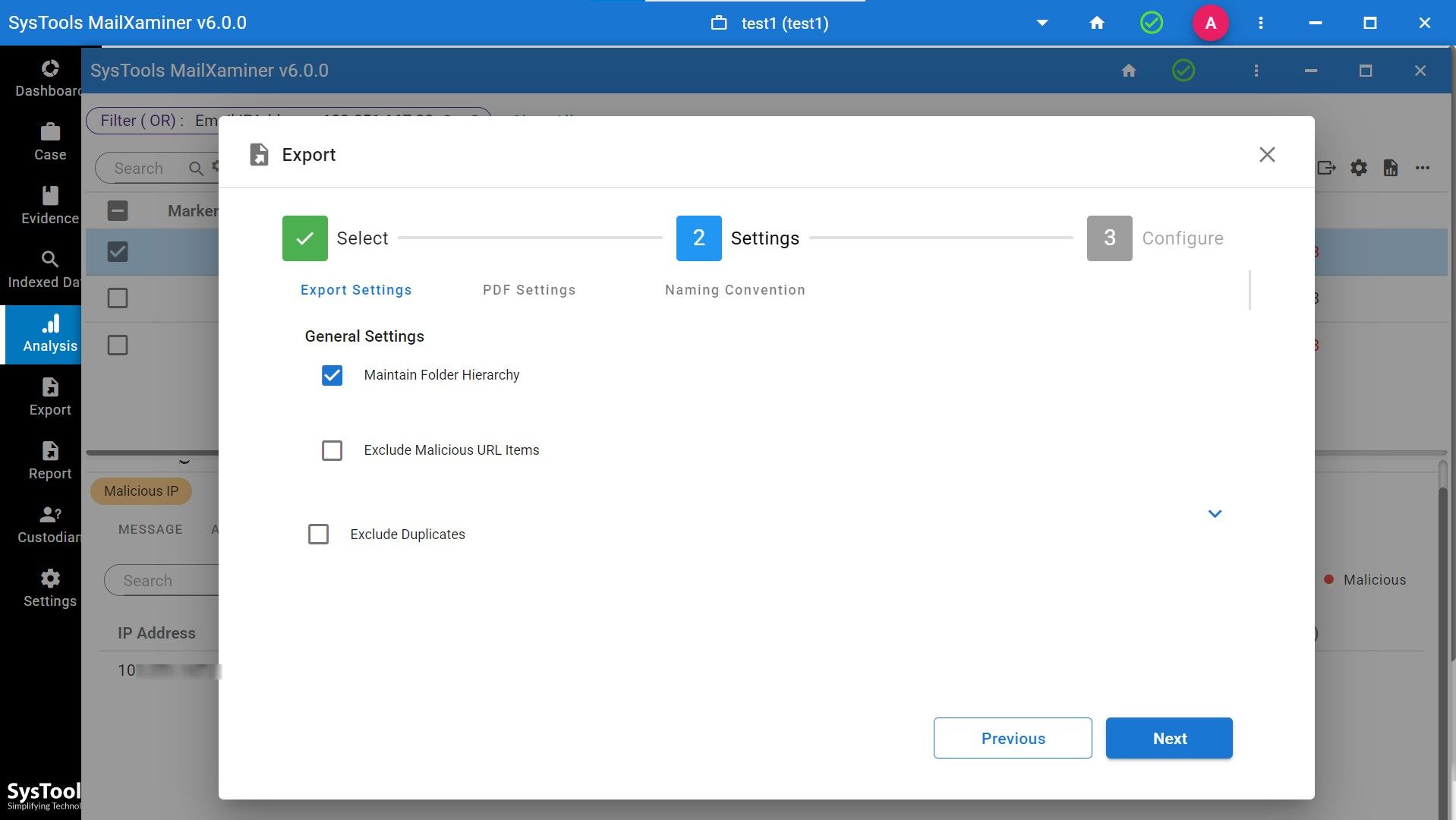
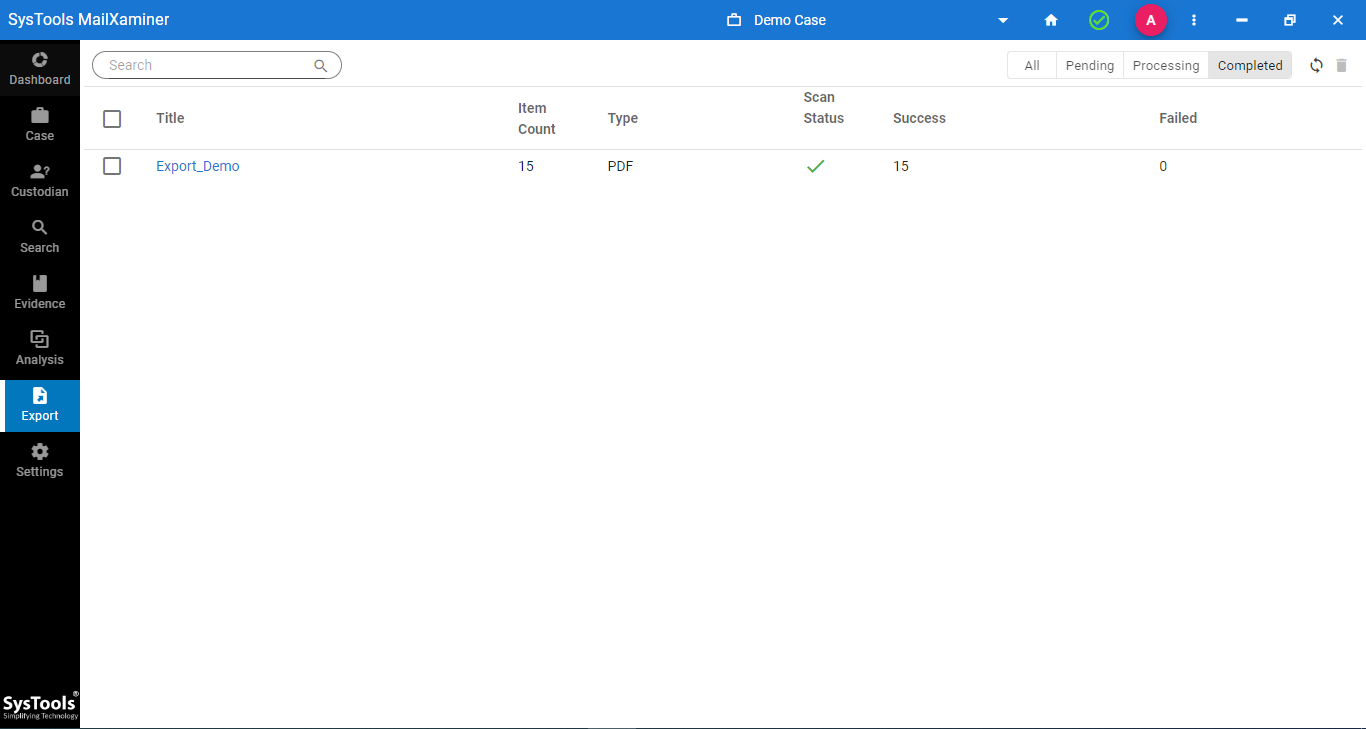
11. At last, export the final result. (You can view the file in the export tab.)
Concluding Thoughts
This blog elaborates on the different procedures that are used to perform Gmail email forensics analysis. However, to navigate the evidence smartly and also to make it admissible in a court of law, an automated approach seems to be a perfect option.
For that, we’ve discussed the tried and tested software, which allows for performing in-depth email analysis while maintaining high standards of forensic integrity. If you are an investigator, forensics analyst, or officer belonging to law enforcement, then download the tool now to make your email analysis journey easier.

