Message-ID Forensics: Make Analysis Easy with Message ID Analyzer
Email headers play a crucial role in the forensics investigation process. Out of other components of the email header, ‘Message ID’ (commonly referred to as an identifier) is one of the important fields, helpful in finding a particular email log entry within a log file of an email server. In fact, through Message ID Forensics, investigators can carve out the necessary evidence from the emails.
Without further ado let’s see what Message IDs can tell forensic investigators while doing email analysis.
MESSAGE–ID FORENSICS – Dig into the Hidden Artifacts
RFC 2822, the internet email address format states that each email must have a globally unique identifier. This unique identifier is termed as Message-ID or Client-ID which is an integral part of the email header. The RFC 2822 has also defined the syntax of message-ID which looks similar to the normal email address.
Two email messages cannot pursue the same message ID. FQDN (Fully Qualified Domain Name) represents the globally unique MTA (Mail Transfer Agent) that gives the unique message-ID to each email message. The combination of date and time with process ID and some random numbers makes it unique for a particular MTA. The image shown below clearly shows the structure of an email header along with the position of Message-ID (Blue font).
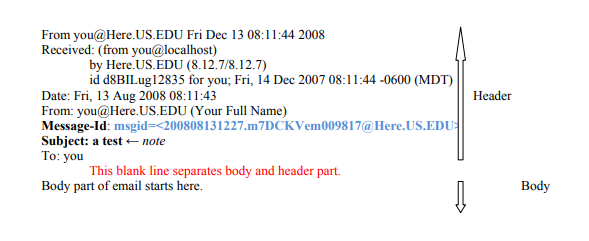
Generation and Format of Email Message-ID
The structure of the message ID is somewhat similar to the structure of the native email addresses, say “abcdefg@xyz.com”. The message ID is always defined between the pair of angle brackets i.e., <abcdefg@xyz.com>.
Let’s decode Message-ID: –
Let’s call the first part #X which is given as (abcdefg) before the “@” symbol. The second part is given as (xyz.com) after the “@” Let’s call it as #Y section. Let’s consider it as #X.#Y
For Example:
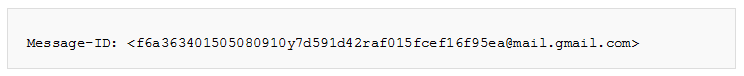
- The #X section of the message-ID contains the timestamp information about the mail such as the date and time of the message when it was sent. This timestamp information can be traced after the first eight digits in the message ID. The date pattern is followed in the following form: – YYMMDDHHMM
In the above-defined message-ID: – 1505080910, which can be written as 15 05 08 0910, means – 2015 (Year) / May (Month) / 08 (Date) / 9 (Hours) / 10 (Minutes) Pacific Day Time
- #Y section of the message-ID consists of FQDN i.e. Fully Qualified Domain Name. In the above-mentioned identifier, the FQDN is gmail.com. The FQDN is a repository of detailed info such as:
- The local hostname
- The source of the email
- The MTA (Mail Transfer Agent) of the source
In the above-considered example, gmail.com is the dedicated localhost that works with Gmail’s server i.e. MTA.
Detect Forged Email Headers via Message-ID Analysis
Just like the hacker can spoof other artifacts of the email header, message-ID spoofing is also possible. We have observed many email headers where the MTA is generated, to create a message-ID that looks legitimate.
For example 200808131227.m7DCKVem009817@Here.US.EDU
While performing Message-ID forensics, we can see that left-hand side of the dot simply shows the date and time whereas the right-hand side of the dot contains 14 characters. The first 8 characters are a combination of numbers and some English alphabets, and the other 6 just numbers.
So before using message ID for forensic analysis, the message ID must be first verified for its validity.
Message-ID Verification
Knowledge of the construction and proper format of message ID will help investigators to verify the message ID. The sequence number and process ID are created dynamically with characters, so verifying them manually is very difficult. Some forensic tools are available that can help to logically examine or verify the Message-IDs.
Spam Identification
Spam identification consists of the spam mail filter process. It is used to check empty illegal message-ID or message-ID patterns in the header of the email. However, the message-ID field in the email header is optional and it is also possible to be spoofed. Therefore, message ID analysis is not a consistent spam-checking method because a good spammer always tries to create such patterns of message ID that it looks legitimate to the user’s eyes.
Read More: To analyze email header visit email header analyzer
Challenges Found in Message ID Forensic Analysis
A distinctive identification called Message-ID aids in classifying emails all around the world. An email forensics professional can dissect it to learn crucial information about an email and its MTA. But there are several difficulties:
- Don’t Have a Standard Algorithm: Every email should have a unique identity, according to the RFC2822 standard, which also offers some suggestions and the message-ID syntax. It does not, however, specify how it should be generated. To create message ids, email software vendors utilize their algorithm. Due to the possibility of encountering many message-id types, the forensic analyst or pertinent technical advisor must be well-versed in the various vendor message IDs.
- The challenge in Identifying Souce MTA: There are numerous MTAs in operation. The source MTA must be known by the investigator to choose the best message-ID analysis method. It will be easier to check the message-ID against bogus IDs if the source MTA is known. If the email already has a message-id, Sendmail won’t produce one. Additionally, certain MUA produce message ids. The message-id may not be sendmail compatible even though the initial MTA is a sendmail. Smtp-id will aid log analysis in this scenario. Researchers must pay particular attention to this topic.
- Versions: Sendmail’s message-id algorithm has already undergone three changes. As a result, it’s crucial for analysis to conduct ongoing research and message-id updates. Before beginning the message-id forensics, it is also important to ascertain the sendmail version.
Try the Best Message-ID Analyzer
At first, information related to email headers may seem confusing, and the challenges associated with analysis may be overwhelming. But, with professional Email Forensics Tool, message-ID analysis as well as in-depth email header forensics feels like a breeze.
You will find a lot of helpful information hidden in the endless lines of text as you start to comprehend the fields in the headers and what they might disclose about the message.
Not just a Message-ID checker, you can use this application for all your email analysis needs as this tool comes with a plethora of features. Some of the highlighted features of this tool are:
- Perform Message-ID analysis of more than 50+ email platforms
- This message analyzer helps you load email data from various desktop and web-based email clients
- Several preview modes to check multiple aspects of email messages
- Multiple search options to find relevant email data
- Offers search operators to apply conditions and extract desired data
- Advanced analysis options to identify hidden links between users
- Comes with export options to find relevant data in desired formats
Summing Up
The above discussion reveals that message ID in the email header plays an important role in the message id forensics investigation process. The global unique feature of message ID helps to distinguish each email and can help in forensic analysis. Message-ID construction part and format will help the investigators to identify spoofed emails and other details like source host, timestamp details, email log file analysis, etc. Last but not least discussed a well-crafted tool that can be used for email analysis.

