What is Email Spoofing? How to Identify and Detect Fake Email Spoofing
In today’s digital landscape, email spoofing in cybersecurity is one of the most widespread threats facing individuals and businesses alike. But what exactly does email spoofing mean, and why is it so dangerous?
Email spoofing occurs when an attacker manipulates the “From” address in an email to make it appear as if the email is coming from a trusted or legitimate source. It’s a tactic to trick the recipient into opening an email, clicking on harmful links, or to download or check suspicipus email attachments.
Have you ever received an email message from the bank asking you to share all that crucial information, such as ATM PIN, account number, etc.? If yes, then you are at risk! This is because the bank never asks its client to share such details; instead, it can be a spam email having a spoofed email ID. This is done just to convince the user to give sensitive information.
It can be difficult to detect, especially when the sender appears to be someone you know or a company you’re familiar with.
As a result, we have come up with this, which will be invaluable for recognizing and protecting against this growing mail spoofing threat.
Definition of Email Spoofing in Cybersecurity?
The literal meaning of the word “spoof” is “falsified.” An email that is spoofed denotes that the sender has purposely altered some parts of the email for masquerading. Moreover, it appears to have originated from someone other than the actual source.
This fake mailer method isn’t just a nuisance, it’s a serious cybersecurity threat. Email spoofing is a technique that can have devastating consequences. Attackers may use spam mailers to impersonate executives, vendors, or even friends who lure them into taking actions that lead to financial losses, data breaches, or worse.
Usually, senders’ names/addresses, as well as message bodies, are commonly formatted to appear to be from some legitimate sources. These emails might have come from some banks or some other legitimate companies, etc. Most of the time, the spoofed email pretending to be an authorized email may ask the recipient to provide sensitive information such as a credit card number, password, etc. In most cases of email spoofing, the email that is spoofed is a part of a phishing attack, and must identify Phishing Email. In other such cases, spoofed emails are utilized for dishonestly marketing some online service or selling some bogus products like shareware, etc.
Why are Emails Fraudulently Spoofed by the Attacker?
One purpose behind email spoofing could be that the email spoofers may be attempting to “phish” the passwords as well as login names. Forgery or phishing is where dishonest senders hope to lure people into trusting their emails. Spoofed websites are disguised in a manner that users them appear quite legitimate to users, such as online banks or paid web services, etc.
Many times, it happens that victims easily believe these spoofed emails and tend to click on these false websites. Trusting spoofed websites, the victims enter their login ID and password credentials and then start receiving false error messages like “website unavailable”, etc. During this time, dishonest spoofers capture victims’ confidential information and proceed towards withdrawing their funds. Additionally, the attackers perform various other types of dishonest transactions for monetary gain.
Another purpose behind email spoofing is that the email spoofers are spammers who are trying to hide their true identities. Most of the spammers utilize mass-emailing software. It allows the attackers to change the source email addresses that will appear to be from innocent citizens, legitimate companies, or government entities. The purpose could be forgery, which is to get users to trust their emails. The impact is that the user opens and reads their spam ads inside those emails.
How Email Spoofing in Cybersecurity Works
If you truly want to understand email spoofing in cybersecurity from the core, then it’s essential to know how it works under the hood. Essentially, email spoofing exploits vulnerabilities in email protocols to impersonate trusted senders. This manipulation allows cybercriminals to send spoofed emails that look convincingly legitimate, tricking recipients into taking harmful actions.
Malicious or dishonest users tend to alter various sections of emails to disguise the sender as somebody else. Some properties can easily be altered by using users’ settings in their Hotmail, Gmail, Outlook, etc. email profiles. Furthermore, IP addresses can be altered to conceal fraudulent emails. However, it requires sophisticated user-level intelligence and more knowledge to trace email sender IP addresses.
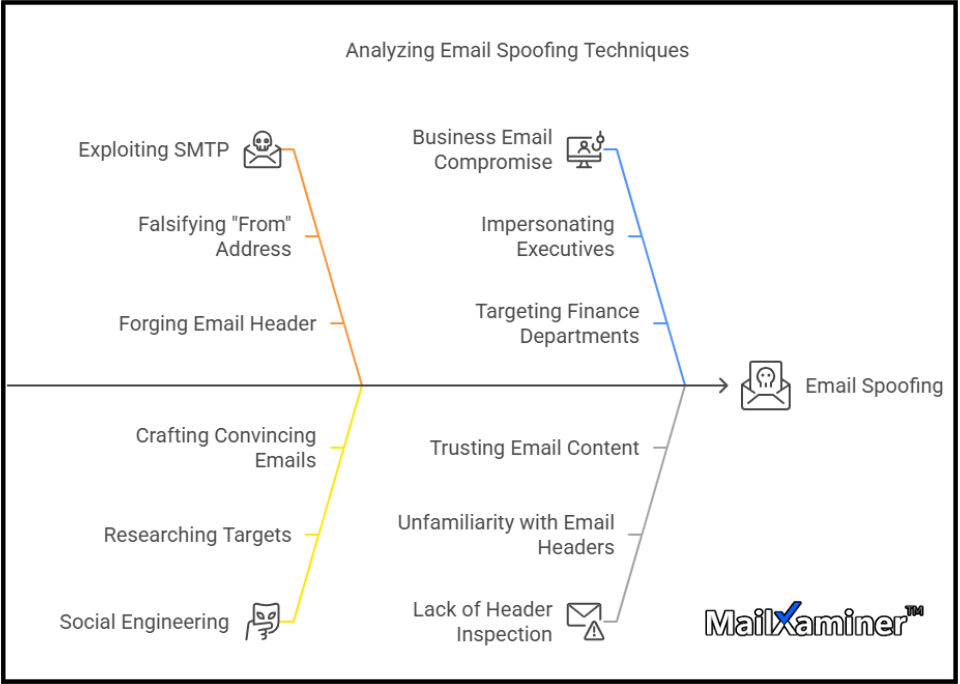
Can an attacker spoof My Email Manually?
Yes, an attacker can spoof your email manually, and understanding how this works is critical for both individuals and organizations concerned with email spoofing threats. However, a majority of such spoofed emails are usually created via specialized software. Spammers commonly use mass-emailing programs like “ratware”.
This program runs massive in-built word-lists for creating numerous targeted email addresses, spoof source emails, etc. Moreover, this program tends to use some illegally acquired email address lists, and then it sends fake emails, which results in performing large-scale spam email analysis to reveal the truth behind the bar. Besides the ratware program, there are several mass-mailing worms as well, which also exist in large numbers. These worms are usually self-replicating programs that act as some types of viruses.
How Email Spoofing Can Happen Manually?
Email spoofing can happen in several ways, and manually spoofing an email is one of them. A cybercriminal with a basic understanding of how email systems work could create a spoofed email by directly editing the “From” field in the email header.
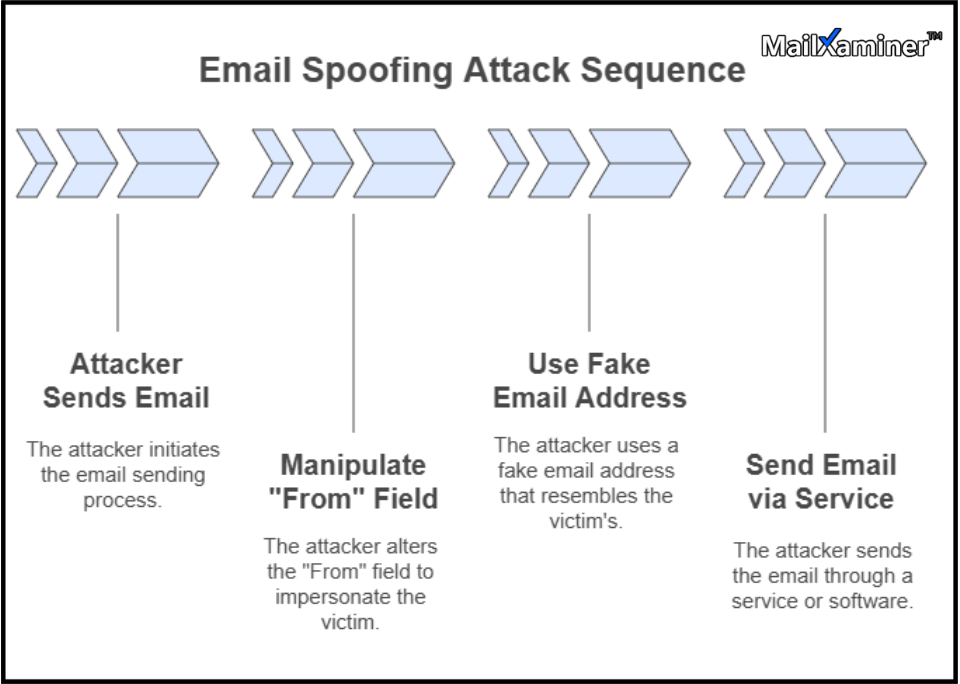
All the emails that seem to be dangerous at first glance are usually designed to trap the recipient into clicking malicious links or downloading malware.
What’s the Risk of Manual Email Spoofing?
There is a significant threat to the manual email spoofing risk, as scammers pretend to?be a trusted source. For example, an attacker could impersonate your email address to trap people in your contact?list into sending money, sharing private information, or clicking on malicious links. If you’re?a business, it could result in business email compromise (BEC), where business employees are duped into sending money or sensitive information.
The problem with?these emails, when they are faked manually, is that we may not detect the same red flags that we might have spotted with automated, large-scale attacks. But the?effect can be as harmful, if not worse.
So, the best way is to opt for the automated software for deep analysis of your files. To examine whether an email is spoofed or not, it is highly recommended to use MailXaminer. It is a remarkable Email Forensic Software which is capable enough to support 20+ email file formats. Additionally, the software is loaded with numerous features that will help to seamlessly analyze the email data files.
It can play a crucial role in helping cybersecurity professionals, forensic investigators, and digital forensics experts. It can identify and trace fraudulent activity in email communications through its advanced feature of link analysis in criminal investigations. Additionally, it consists of various analysis features which you can see on the given screenshot below:
Why Use this Software for Email Spoofing Investigations?
It is advisable to rely on the trusted software. This is so because we are in the era of different types of email threats like email spoofing, which can be used for financial fraud, data breach, etc. This is crucial for everyone involved in cybersecurity or digital forensics, etc.
This software has already set a margin in the field of digital forensics. It has emerged as a global power in email forensics. It can easily process in investigating analyze URL for malware and helps to investigate email files from each angle.
Not only this, but it will provide you with accurate and court-admissible findings.
Time to Conclude
To prevent becoming the victim of email spoofing, users need to be smart enough to recognize spam emails. We have made users aware of what is email spoofing and how to identify that. Also, the different mass-emailing programs that the fraudsters use to send spoofed emails in bulk. Furthermore, to detect the various details for investigating the spoofed emails, it is best to use advanced software.

