eM Client Forensics – Analyze the Mailbox Data of eM Client
eM Client is an email client application that was developed in 2006. It rapidly captured many users’ attention compared with several other renowned desktop-based email applications. These Windows and macOS-based specific applications served a vast variety of configuration options and other features. This application is a powerful platform as it doesn’t just serve emailing, but also offers PIM (Personal Information Manager) services along with an IM (Instant Messaging) feature. A unified sidebar enhances user experience by centralizing virtual assistants and tools on a single screen.
Along with the support of Windows configuration, the client also supports all major email services used heavily worldwide for communication. eM Client makes it easy to migrate users’ messages from Gmail, Outlook, Exchange, iCloud, etc., to eM Client.
Introduction to eM Client and Its Importance in Forensics
Regardless of how fast-paced technology is, emails are still one of the most preferred mediums of electronic communication, as well as the source and target of malicious cyber activities. This article discusses the construction and operation of eM Client forensics and how to analyze it to extract crucial information for eDiscovery search.
Understanding eM Client’s Data Storage Format
eM Client mailbox has a default database storage for all of its components, such as Attachments, Category, Contact_data, Contact_Index, Event_data, Event_Index, Folders, IM, Mail_data, Mail_fti, Mail_index, Mail, Privacy_list, Task_data, Task_index, Timezones.
The path for the storage of the component data and information is as follows:
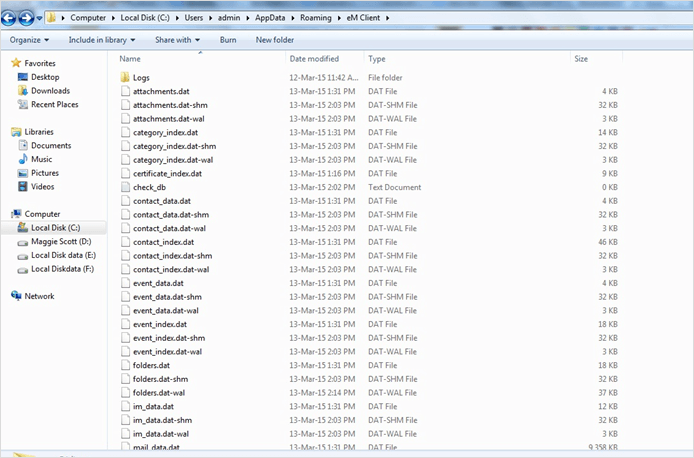
Forensic Relevance of eM Client File Types
eM Client consists of three types of file formats used for storing the component data and information associated with the client. The three file types that are generated by default in the store folder that help in eM Client forensics are as follows:
1. .DAT: This is the standard data file format consisting of data that is accessed or composed by eM Client. DAT files can be opened easily in case of some specific programs like eM Client. However, DAT files that are created as text files can be opened and viewed without client availability. Therefore, it can be accessed by some manual means, but eM Client analysis is the only application that can use and operate it. There are mainly three components for which a DAT file is created, i.e., Certificate, Telemetry, and Security.
2. .DAT-SHM: An SHM or shared-memory DAT file consists of no persistent information. The sole purpose of an SHM file is to render a shared memory block that can be used by multiple numbers of processes to access a common database under WAL mode. Shared memory files only exist while running in a WAL mode. Both WAL and Shared-Memory files are interrelated, i.e. both share the same lifetime. An SHM is created when a WAL file is generated and if SHM is deleted then it’s corresponding WAL will be deleted too. When a WAL file is being recovered, the SHM file is also recreated but from scratch which depends on the recovered contents of the WAL file.
3. .DAT-WAL: SQLite started supporting a new type of control mechanism for transactions, i.e. WAL (Write-ahead log). .dat-wal file or a database suffixed with –wal denotes that file is in WAL mode. This means that connections made to the respective database are using WAL as well. A WAL file is located in the same folder as the database and has the same filename with a string appended to it – “-wal”. Forensically, to examine what is associated with a WAL file, the database is opened and its content is written or checkpointed to the main data. However, this may come with several problems:
- the information extracted from the WAL file could overwrite a. Old information in the main data file. It may have lost the potentially valuable data that can be used as evidence.
- b. The unused spaces within a WAL file could consist of deleted data.
ActiveSync & Unfiltered Spam: Configuration Tip
eM Client can import the user’s data directly from the previous email client program that was installed on the current device. Some of the supported applications are Microsoft Outlook, Windows Address Book, Microsoft Outlook Express, Windows Live Mail, Windows Mail (Vista), Thunderbird, and The Bat!
Users can also import data from separate files. Options are available to import messages from EML and MBOX files, contacts from CSV and VCF files, and items of the calendar from ICS files. If the user previously had installed eM Client and saved the settings, then the user can also import all eM Client settings from .xml files.
The configuration with other email applications also promotes the unfiltered download of spam messages and junk folders. Downloading the data along with images and attachments promotes the entry of malicious content. It may put the eM Client database under threat of vulnerability that leads to corruption.
NOTE: In case, if the database gets corrupted anyhow then, eM Client can solve the issue itself. eM Client comes with a DB Repair application which is located in its Program Files folder. Running the tool will execute a consistency check on the database to find the problematic issues and repair them.
Nevertheless, eM Client is not responsible for the vulnerabilities of downloading spam along with internal media but ActiveSync is. However, the eM client analysis may download viruses and other malicious programs into the system. They unknowingly execute and may put the database under a more severe threat.
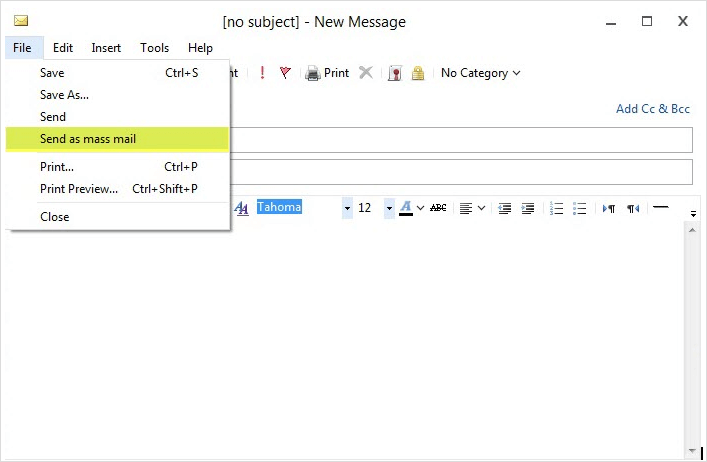
Promotes Spamming & Undisclosed Emailing
The application has a “Send As Mass Mail” option that promotes problematic activities like spamming, email bombing, etc. This makes it worst as:
- Firstly, mass messaging can be done without disclosing the recipients to other recipients.
- Secondly, these facilities are unrestrictedly served in the client’s 30-day free version.
Evidentially Crucial Data: Storage and Backup
Apart from DAT, DAT-SHM, & DAT-WAL file types, eM Client forensics is capable of storing its data in some other file types too:
1. EML: Within the export option of the application, eM client mailbox analysis gives a choice to store each email as a single text message in EML file format.
Traversing an EML Message: Reading the contents and structure of a file with .eml extension is more feasible. Internal information and structure of a single email file with EML file format can be examined using Notepad or any available text editor. For example, an email received in the Inbox of eM Client mailbox can be easily traversed using Notepad. The data file have the following information that may be crucial from an investigative point of view:
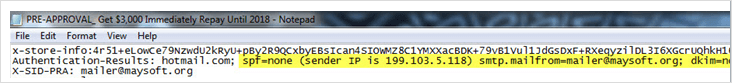
- SPF & DKIM: An SPF always has the purpose of describing the mail server that permits to transmit messages for a particular domain. It can be used to avoid “fail” mail ID. The SPF values are safe when “neutral” or “pass” but if it is “fail” then, the message shall not be received at the receiver’s end as it would have been rejected already by the exchanger. Whereas, a DKIM, i.e. the DomainKeys Identified Mail is a source of related domain with an email. It further allows the organization to be liable for an email in such a way that a recipient can validate it.
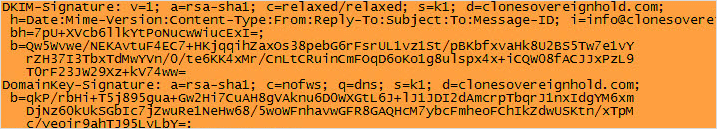
- DKIM Signature: In eM client email forensics, the DKIM signature is used by the SMTP receiver of a message to verify that whether the one claiming to be the sender of the email is genuine or not. Any tampering done with the message can also be detected. The public key can also be retrieved to verify the sender and with the help of its ‘s’ & ‘d’ fields a manual query against DNS can be generated to get a TEXT resource record of the host.
- Message-ID: Each email has a unique ID that can be used to verify its authenticity. It is put into an email header either by the MUA or its first MTA for Message-id forensics.
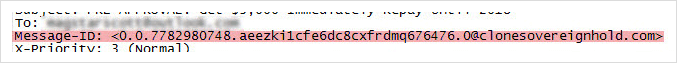
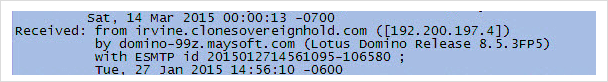
- Received From: The server involved in sending or relaying the message at a given point is shown in this portion of the header.
- Received By: This column of the header indicates the server name or the IP address to which the message was received.
Recommendations- Investigators during eM Client forensics tend to follow strict methods to cut short the time duration of an investigation. Thus, here we have one advanced best solution for you. MailXaminer is one of the advanced, dedicated, quick, and convenient email forensic tools platforms with full support for EML files & many others, which are also trusted by Law Enforcement.
2. vCard: Contacts of the selected category are exportable into vCard (VCF file). While choosing the file creation type, i.e., single VCF for all contacts or a vCard file, export location for the file can also be chosen.
3. ICS: Similar customization applies to ICS files however, they are generated while exporting both events and tasks. ID’s of the current message and any previous message received from the same sender can be matched to verify whether the sender of the message is the one who it claims to be.
4. XML: Settings, Rules, Accounts, and Save Passwords are exportable into the XML file format at the preferred location. However, note that while saving the passwords, exportation may prompt for a Custom Password to add a layer of security.
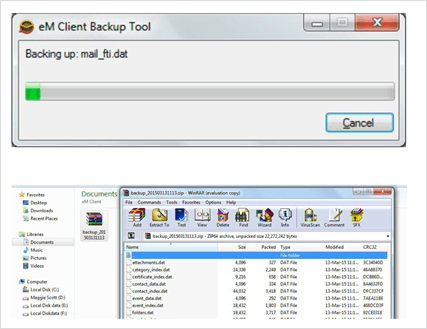
Along with this, eM client forensics also permits the backup of DAT files for all the components in a zipped archive folder at a user-defined location. MailFTI to Mail data along with attachment, contacts, security, certificate, folders, IM Data, etc., included in the backup which can be restored from the client’s File menu even in case of any inconsistency.
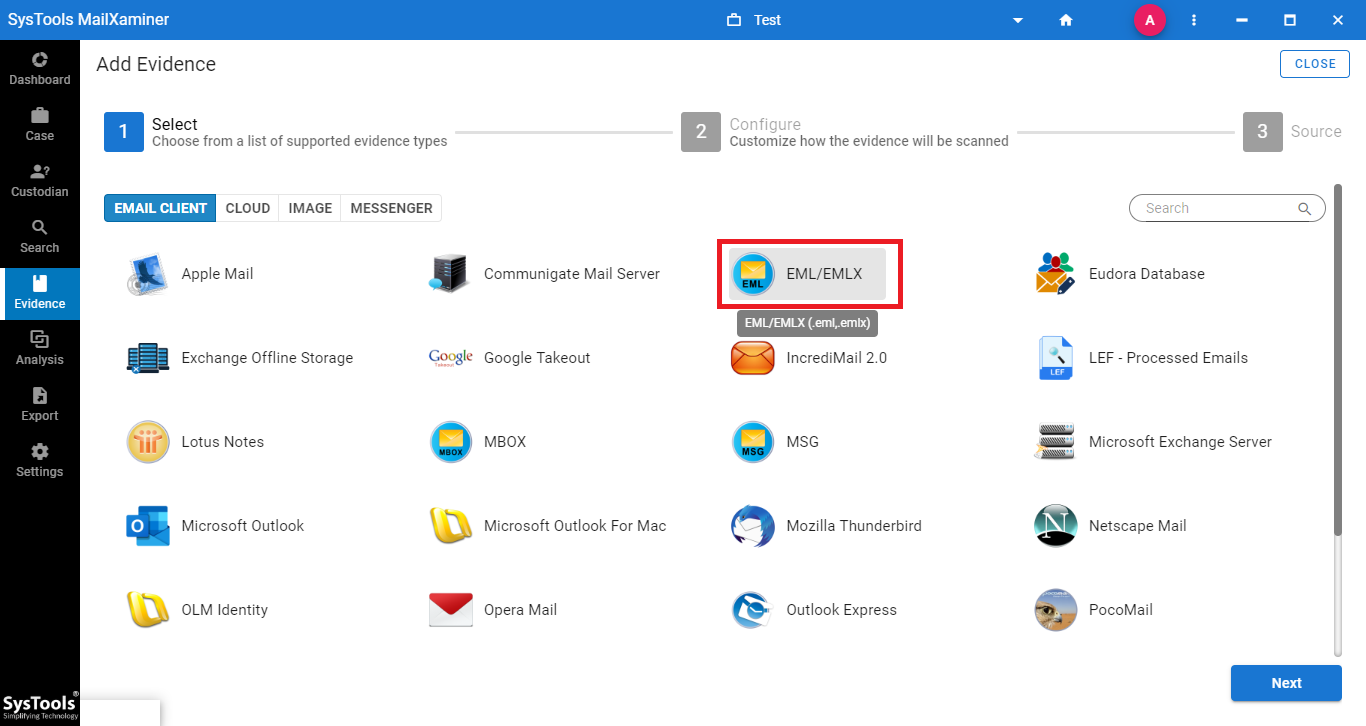
Learn More About the Software
This software isn’t just for viewing EML files, it’s a complete software that supports over 20 different email file formats. Users can add many types of email files to investigate them in one place.
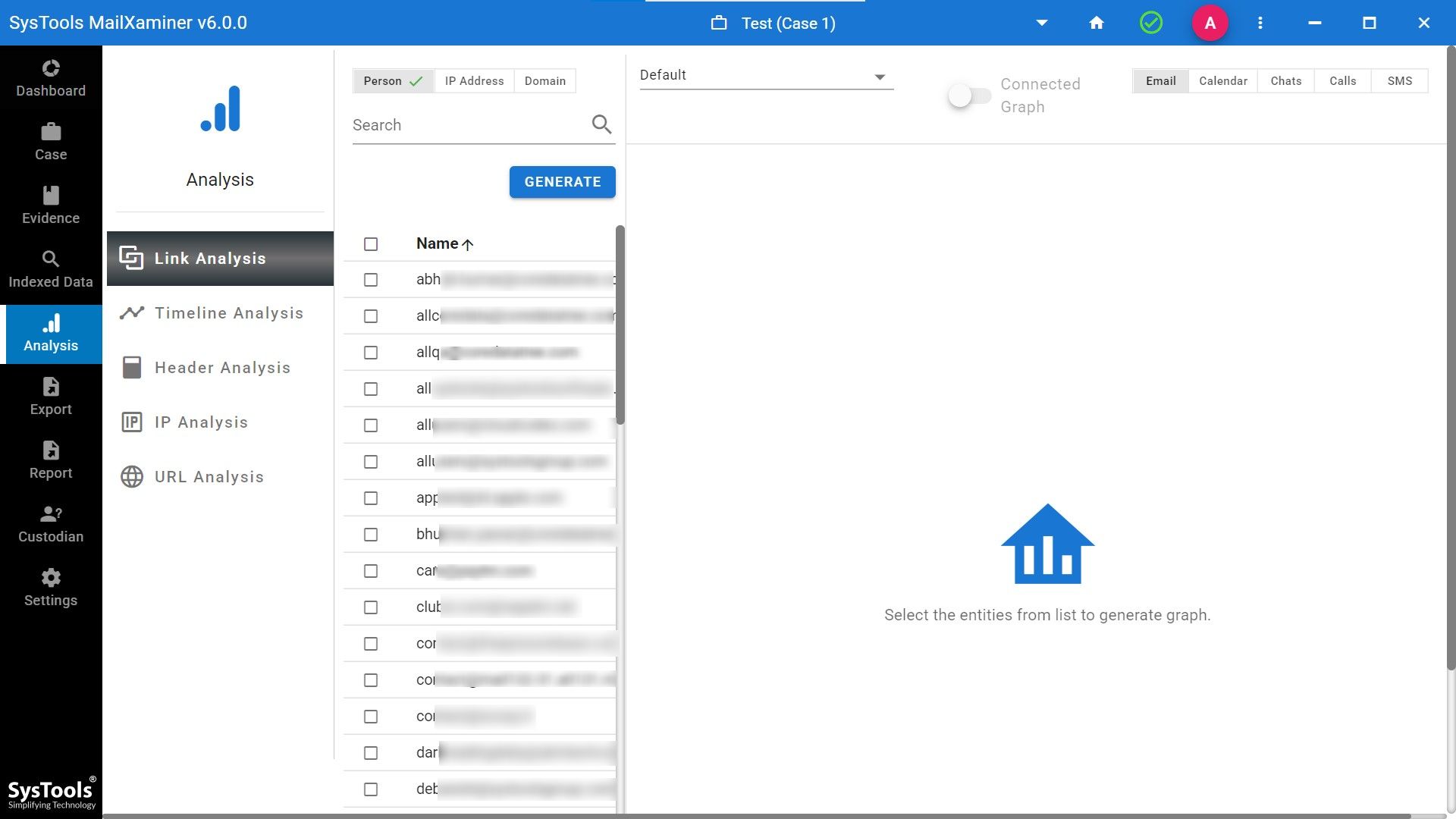
We will provide you with advanced analysis options after you add the EML file as evidence. Options of link analysis, timeline analysis, email header analysis, and many more features are there to analyze eM clients.
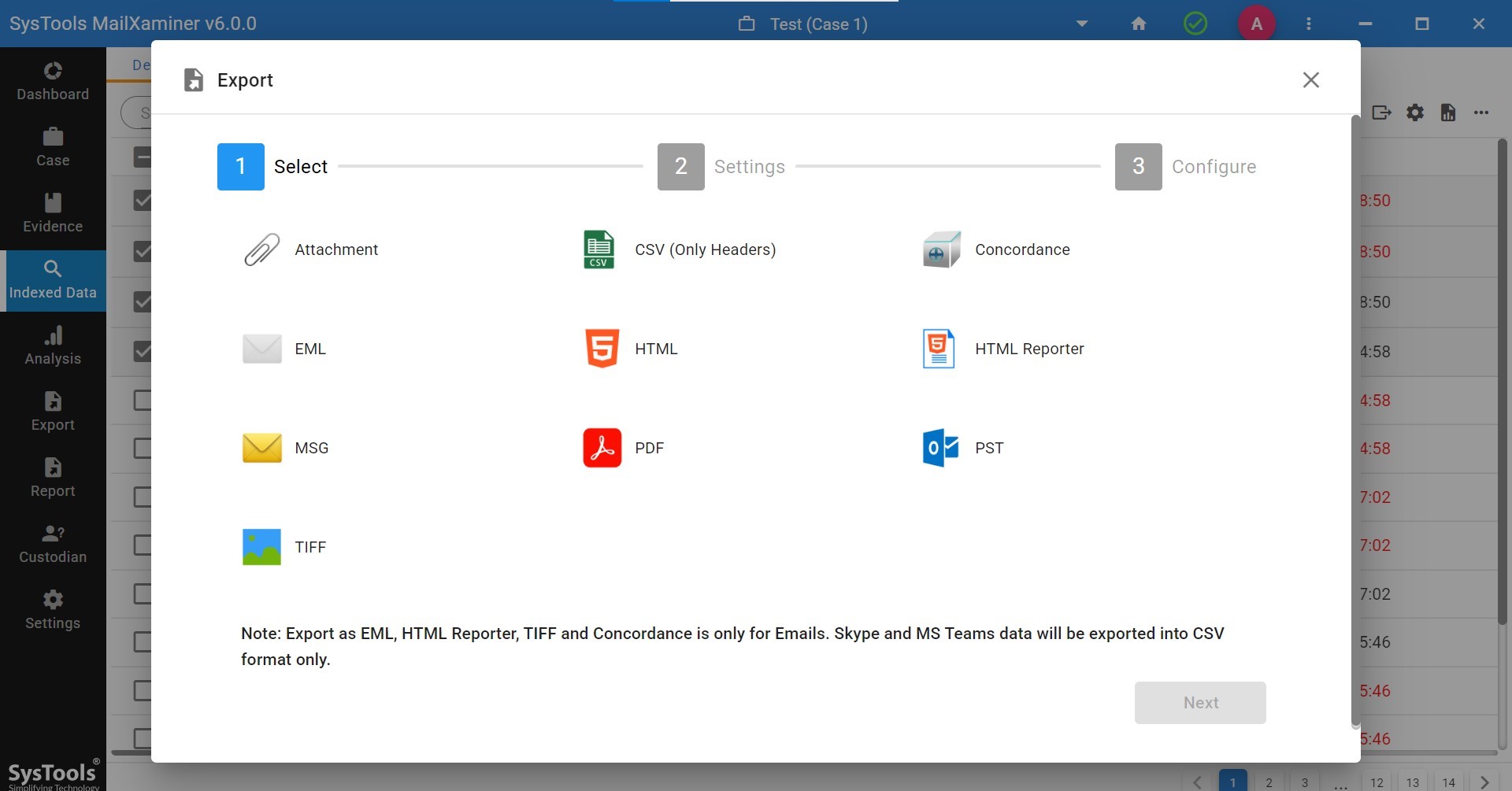
We will also provide you with different export options. Additionally, the option of report generation is available.
Final Observation
eM Client seems to be an extremely user-friendly email platform that comes along with PIM facilities. It provides an easy way for offenders to commit offenses. Some of the examples are like email bombing, spamming, and sharing of intellectual property with an intervening party without letting the recipient know the same. The manipulation of digital information has become unimaginably easier.
But the detection of traces left during such activities has grown stronger & become more feasible. This application helps to trace illegal activities with numerous methods. The platforms available in eM Client forensics such as data files, storage database, and email headers etc.

