PDF File Analysis: How to Investigate Malicious PDF Professionally?
Portable Document Format (PDF) is the most commonly used format in today’s digital world. This is due to its compatibility, fixed formatting, and ability to store various content types, including text, images, hyperlinks, and embedded objects. This is why PDF forensics and PDF file analysis are critical components of modern cybersecurity and digital forensics investigations.
Table of Contents
- What is the Structure of the PDF File Format?
- What is PDF File Analysis & Why is it Important?
- Common Threats Found in Malicious PDF Files
- Key Aspects of PDF File Forensics
- How to Perform PDF File Forensics Professionally?
- Steps on how to Analyze Malicious PDF Files Easily
- Conclusion
- Frequently Asked Questions
In every domain where you have been working, you have to know how to do PDF file analysis, extract metadata, and ensure document authenticity to help detect vulnerabilities. Whether as a cybersecurity expert, a forensic analyst, or a professional handling sensitive digital documents.
However, the PDF format includes so many authentic features that help users in each discipline. But, on the other side, it also makes PDFs susceptible to manipulation, malware injection, and authorized modifications. As far as the digital evidence part is concerned, the PDF is one of the authorized file formats that is legally accepted in the courts as evidence.
So, here is the complete guide for you to know the exact process of how to analyze malicious PDF files and utilize PDF analyzers in a more advanced way. Let’s begin by understanding the core structure of a PDF file.
What is the Structure of the PDF File Format?
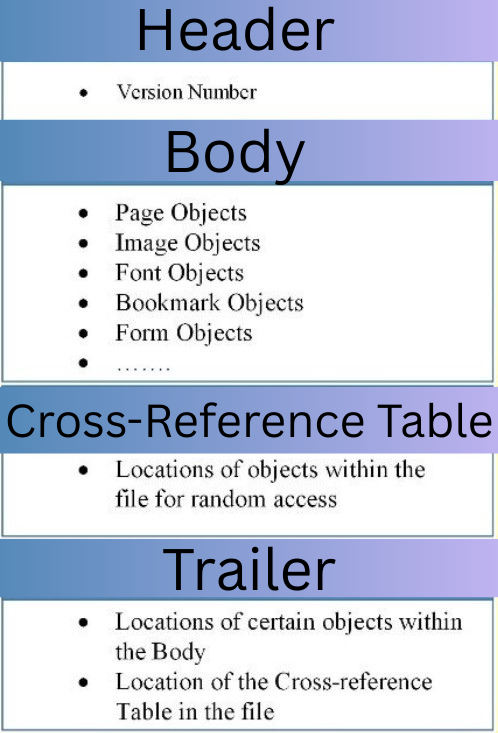
A PDF file consists of distinct components that define its structure and functionality. Understanding these elements is crucial for performing detailed PDF file analysis and identifying potential security risks.
Key Components of a PDF File
- Header- Specifies the PDF version, PDF creator app, page count, page size, and provides essential file information.
- Body- Contains the actual content, including text, images, and embedded objects.
- Cross Reference Table (XREF)- Maintains a directory of object locations, allowing for quick access.
- Trailer- Marks the end of the PDF and provides a pointer to the cross-reference table.
What is PDF File Analysis & Why is it Important?
PDF document analysis is the process of examining PDF files to extract valuable information, hidden data, and assess the security risks. PDFs are a highly used file format, and by conducting PDF file forensics, you can uncover crucial data. This is crucial for industries like cybersecurity, digital forensics, legal investigations, and data recovery.
PDFs are often used in cyberattacks, especially in phishing campaigns and email-based malware delivery. That’s why malicious PDF scanner tools and thorough PDF forensic techniques are essential.
It may also contain hidden text, timestamps, or even encrypted content, which can pose significant risks if left unchecked.
This is just identifying threats or verifying document authenticity. It’s a multifaceted process of wide-ranging importance that touches on efficiency, precision, and risk management in various domains. Below are several deeper reasons why PDF analysis is a critical skill:
One of the primary reasons to analyze a PDF is to verify its authenticity. PDFs serve as official records, contracts, or legal documents, as we discussed. So, any alterations or negligence can lead to serious consequences.
This is the highly demanded file format, which is commonly used by the examiner in Digital Evidence Collection in Cyber Security. There are various techniques which is used by malicious actors to attack these files. It’s important to analyze spam emails containing PDFs to protect the eviences consisting in the PDF.
It helps in investigations and identifying document tampering, verifying authenticity and also the digital footprints. PDF analysis process enables the retrieval of lost or hidden data as well from the corrupted or encrypted PDFs. This is so because in the forensics of PDF document files, there a huge changes of privacy attached to the PDFs.
Common Threats Found in Malicious PDF Files
Suspicious PDF Files often look completely normal, but they may hide dangerous content inside. While using the advanced tools like a malicious PDF scanner or PDF analyzer, an investigating officer is often able to discover:
- Some PDFs contain hidden JavaScript code. These codes can automatically be run when the file is opened, just like on websites. Hackers use this trick to exploit weaknesses in your PDF reader and take control of your system or steal data.
- Some PDF files are designed to run commands or scripts as soon as you open them. These commands may launch external programs or install malware silently in the background.
- The attackers can attach dangerous files, such as EXE or ZIP to PDFs. This makes them look like innocent documents or images, but when user open them they may unknowingly launch harmful software.
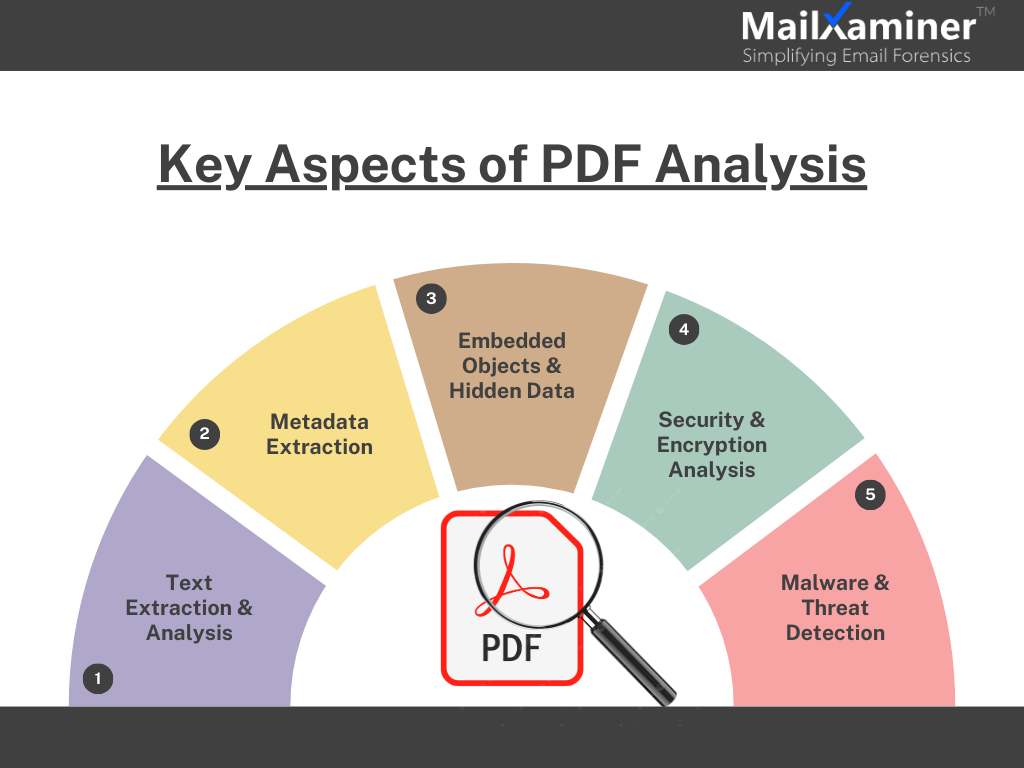
Key Aspects of PDF File Forensics
It is crucial to understand the core elements of PDFs before handling the crucial evidence that PDFs identify hidden risks, extract valuable information, and ensure document integrity.
Understanding the core elements of PDF file analysis is crucial for identifying hidden risks, extracting valuable information, and ensuring document integrity. Whether for PDF file forensics, cybersecurity, or compliance, a detailed analysis helps uncover crucial insights.
How to Perform PDF File Forensics Professionally?
A large number of PDFs may hamper your storage capacity. So, start by organizing suspicious PDFs. Compress them into a ZIP file for better management and file integrity during transfers. This also helps examiners in the PDF file analysis process, as it can minimize the risk of corruption during uploads and downloads.
You can analyze the PDF through the advanced email forensics software globally known as MailXaminer. This is the best tool for PDF forensics that provides comprehensive PDF file forensics capabilities.
Steps on how to Analyze Malicious PDF Files Easily
The process of PDF malware analysis involves extracting, inspecting, and verifying data for threats or unauthorized changes.
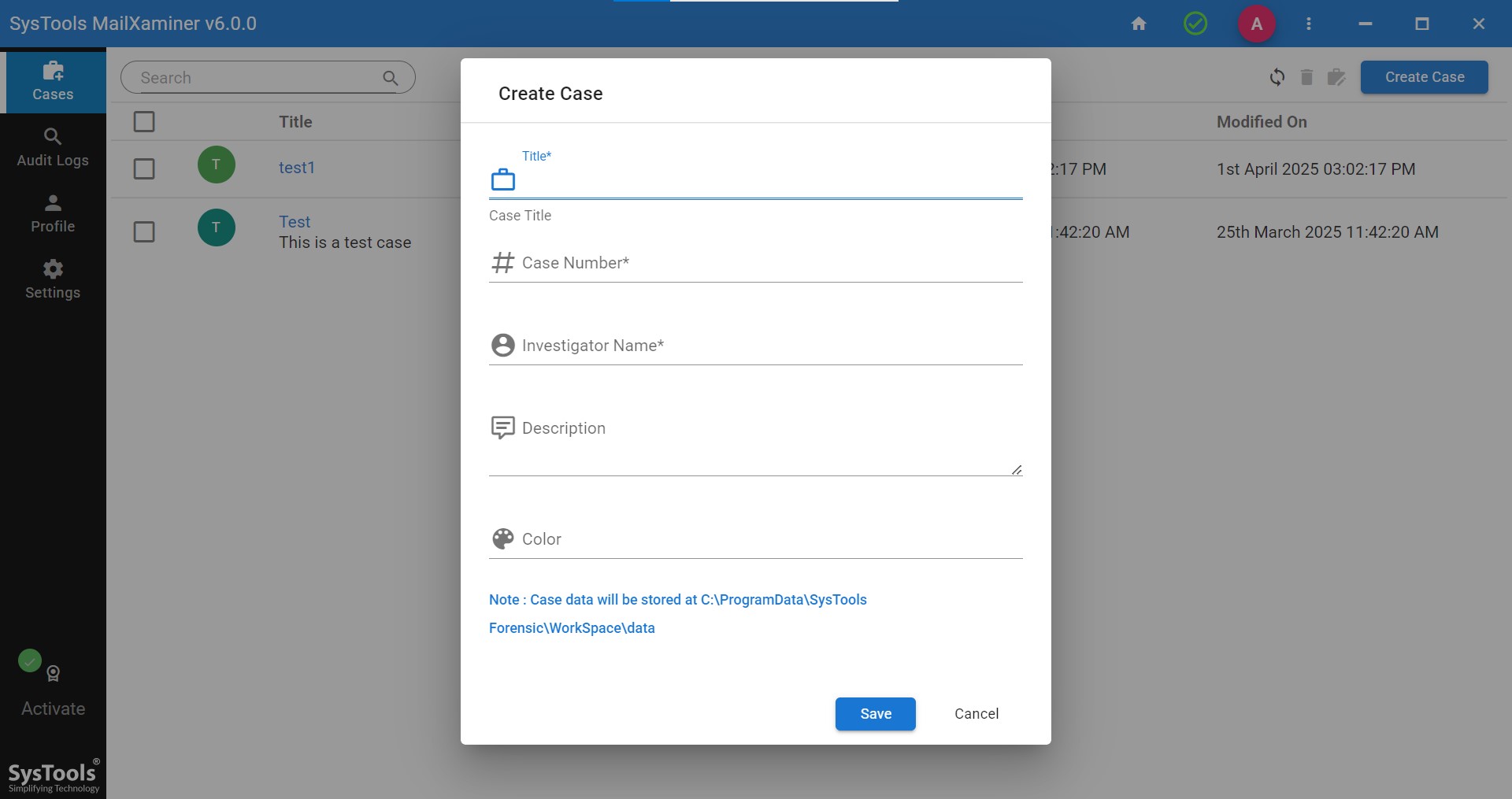
Step 1. To start an investigation of PDF files. For that, first select Create case.
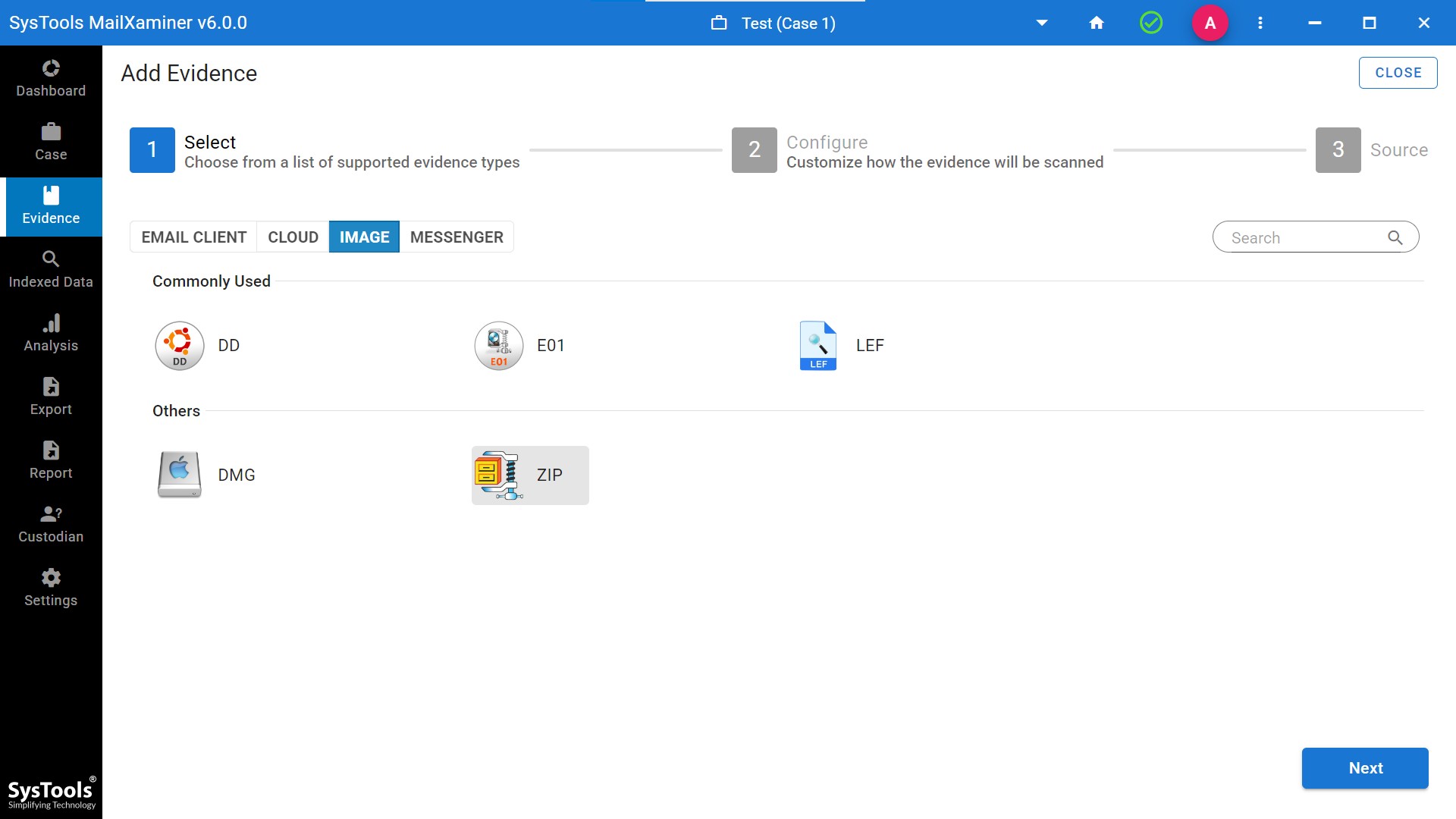
Step 2. Add PDFs as evidence in a zip file format into the software.
Step 3. After adding the evidence, allow some general setting options like image analysis, OCR analysis, etc, for deep analysis of the PDF document file.
Step 4. The evidence is added successfully, and you will get a pop-up of successful import of evidence.
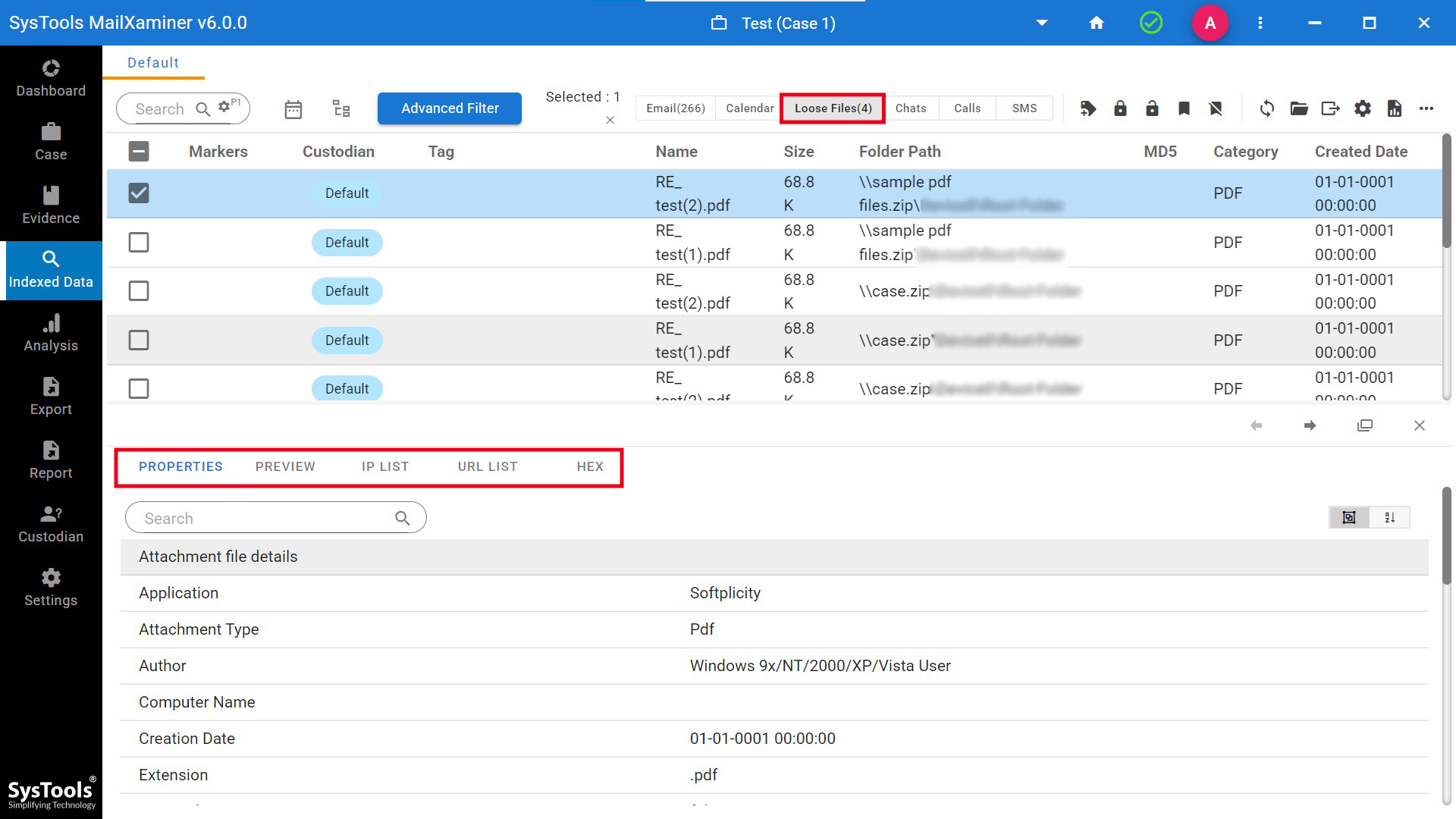
Step 5. Now comes the loose files analysis part, from here you will be able to get the complete data of the loose files. It will show the properties, Preview, IP list, URL list and HEX of the selected files.
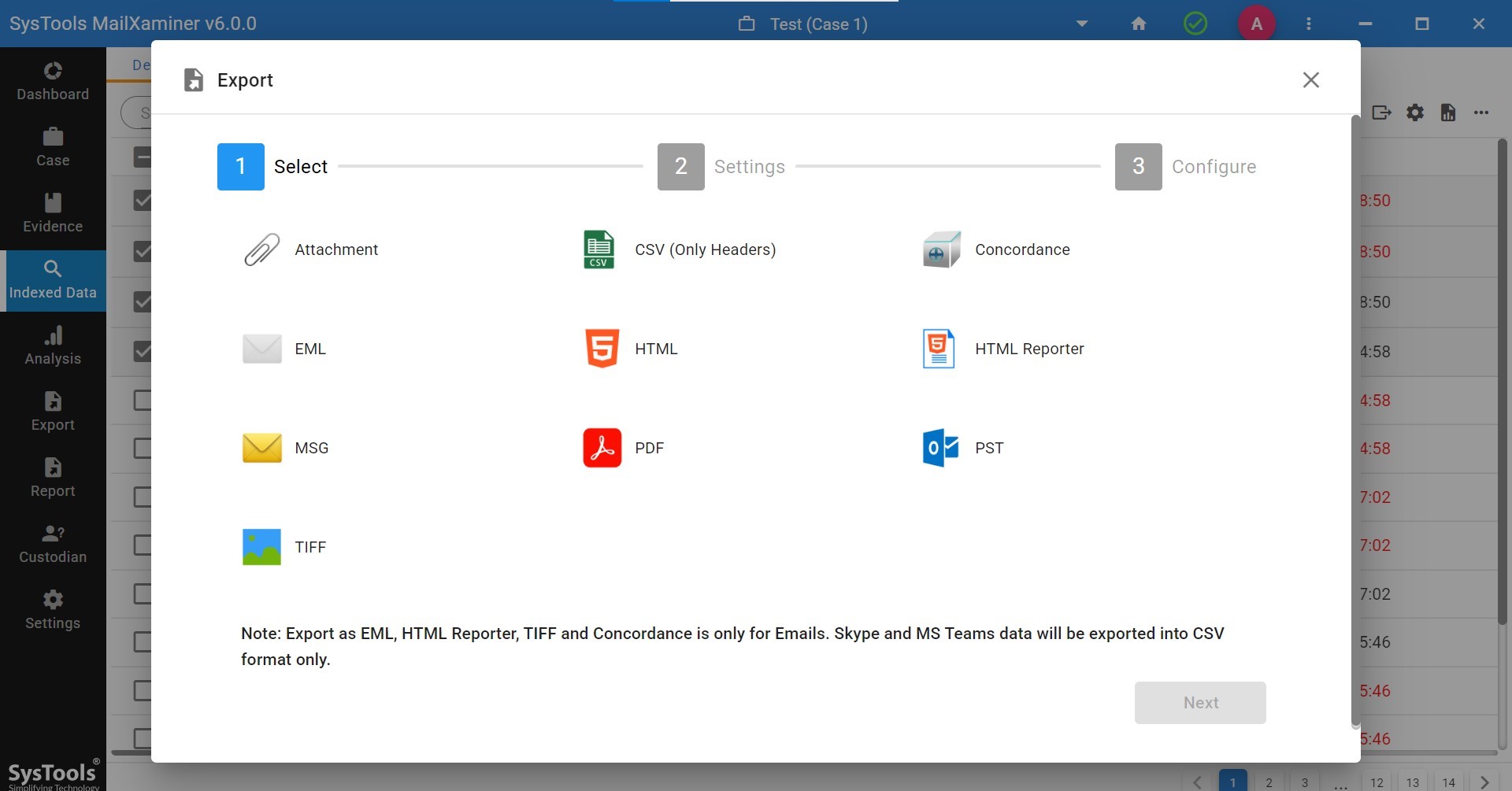
Step 6. Not only this, after analyzing the PDFs, you will be able to export these files into the different preferred file formats as per your choice.
Conclusion
PDF file analysis is an essential skill in digital forensics, cybersecurity, and legal investigations. Understanding the structure, extracting metadata, and identifying potential security threats are crucial steps in ensuring document authenticity and integrity. Given the susceptibility of PDFs to manipulation, malware injection, and unauthorized modifications, leveraging advanced forensic tools makes the process enabling professionals to analyze, verify, and extract hidden information efficiently.
By following a structured approach and using the right forensic techniques, investigators can uncover critical evidence, detect tampered documents, and safeguard digital assets. PDF file forensics plays a pivotal role in maintaining digital security and trust, whether you’re handling sensitive legal documents, combating cyber threats, or conducting forensic investigations.
Frequently Asked Questions
Q. Why is PDF file analysis important in cybersecurity?
PDFs are commonly used in phishing scams and malware distribution. PDF forensics helps cybersecurity experts spot phishing emails or code, embedded scripts, and unauthorized modifications. This can ensure the authenticity of PDF documents.
Q. How to analyze a malicious PDF file?
- Upload PDF files in ZIP format
- Create a case in the forensic tool
- Add PDF files as evidence (ZIP format)
- Enable OCR and image analysis options
- Import evidence and confirm successful upload
- Analyze properties, URLs, IPs, and HEX data
- Export results in the desired format.
Q. Can Malware be hidden in the PDF files?
Yes, malware can be hidden using JavaScript, embedded files, or unauthorized links. Attackers exploit PDF structure to deliver payloads or trick users into executing harmful actions.
Q. What is the use of metadata in PDF file analysis?
It can reveal the critical information such as the file creator, modification dates, software used, even GPS or device info. Forensic examiners perform email header analysis to verify document authenticity and track alterations.

