Current Challenges in Digital Forensics Investigations- Explained
Digital forensics is the critical term used in modern cybersecurity and investigations. Various digital forensic investigation techniques are used today to analyze evidence. These are like identifying, collecting, preserving, validating, analyzing, interpreting, and presenting electronic evidence from digital sources.
So, to combat these cybercrimes, a modern-day investigation approach is required. But, the thing is, there are some digital forensics challenges that investigators face during the practical implementation of digital forensics investigations.
Let’s explore them in detail.
Different Digital Forensics Investigation Challenge Types
Mainly, the challenges in digital forensics investigation are categorized into 3 parts.
Technical Challenges in Digital Forensics Investigation
We’ve seen immense growth in the field of technology. However, the usage of technology has been identified as both positive and negative. While some developers use technology to invent things to benefit mankind, cybercriminals also use technology to fulfill their malicious intent.
The digital forensics domain has witnessed these major computer forensics challenges. That is when a technology is developed to identify & investigate criminals, at the same time another technology helped criminals hide themselves.
In the technology world, digital evidence is different from physical evidence. Unlike physical evidence, electronic evidence can be easily manipulated, removed, and/or hidden without leaving any traces that might identify the culprit.
So, we can say that anti-forensics has become the prime enemy of the digital forensics investigation process.
How Anti-Forensic Techniques Become Challenges in Computer Forensics?
Here are some of the anti-forensic techniques that cybercriminals follow, making the task of an investigator more challenging.
- Encryption: Information is scrambled via encryption, which can only be read and decoded by someone who has the right decoding key. On the compromised system, encryption is utilized to conceal or render the evidence illegible. Investigators must decrypt the encrypted material to make it usable because attackers employ a wide variety of encryption techniques. It takes time, and occasionally, it is impossible to decrypt the encrypted data. For example, According to a 2024 cybersecurity report, 68% of cybercriminals use encryption to hide evidence.
- Residual Data Wiping: A few unnoticed hidden processes (such as temporary files and command histories) are running when the attacker utilizes a computer to accomplish his objective. However, a clever attacker can minimize this danger by erasing the traces left by his activity and tricking the system into functioning as if it had never been used for that purpose.
- Data Hiding in Storage Space: Data are concealed by attackers inside storage spaces and rendered invisible to standard system instructions and programs. It complicates and lengthens the inquiry, and occasionally data corruption also occurs. One of the most often utilized methods for concealing data in storage is the rootkit.
- Covert Channel: Attackers can disguise data on the network and potentially get around intrusion detection systems by using covert channels in communication protocols. The header of a network protocol is typically altered to leak messages between attackers, taking advantage of the fact that only a small portion of the header is changed during transmission. Attackers make use of these covert channels to keep a covert connection going between themselves and the compromised system. It is harder to recognize.
- Tail Obfuscation: These terms may sound technical, but obscuring the attack’s source is the most widely used approach by criminals. In this case, the attacker changes the file extension and utilizes fake information to deceive the investigator. In light of this, the investigator occasionally risked missing information with forensic significance.
- Steganography: As an extra secure form of data protection, steganography, an encryption technique, can be used in conjunction with cryptography. It’s a method for concealing any information inside a file carrier without altering its outside appearance. Using this steganography, attackers can conceal their payloads (hidden data) inside the infected system. An investigator must locate this concealed data when looking into computer crimes to make it public and make it available for future use.

Legal Digital Forensics Challenges in Digital Investigations
Privacy is important to everyone – for business organizations as well as individuals. In many situations, the computer forensics expert may need to reveal the data or violate privacy in order to discover the truth.
Privacy laws and regulations differ worldwide, posing significant challenges in digital forensics investigations. Regions like Europe, the United States, and Asia have strict legal frameworks that forensic experts must navigate to access and analyze digital evidence.
| Region | Key Regulations & Challenges | Impact on Digital Forensics |
|---|---|---|
| Europe [EU] | GDPR (General Data Protection Regulation) |
– Strict data access, storage, and processing rules. – Heavy fines (up to €20 million or 4% of global turnover) for non-compliance. |
| United States [US] | CLOUD Act & Fourth Amendment |
– Allows access to overseas data under legal agreements. – Protects individuals from unlawful searches, complicating evidence collection. |
| China [CN] | Cybersecurity Law |
– Strict data localization laws restrict cross-border evidence sharing. – Government control over digital data storage. |
| India [IN] | Data Protection Bill (Draft) |
– Limits forensic access to personal data. – Data localization rules may prevent international forensic collaboration. |
| Global | Budapest Convention on Cybercrime |
– Facilitates cross-border cooperation in cybercrime investigations. – Not all countries have ratified it, causing legal conflicts in investigations. |
In the course of daily use, a private company or a single user may produce a lot of private information. Therefore, allowing forensic investigators to look over their data runs the danger of exposing their privacy.
It becomes difficult when the investigator “accidentally” discovers or comes across information about the crime but is prohibited from using this information against the perpetrator owing to privacy concerns. This has an impact on the entire digital forensics investigative process and makes it more challenging.
Resource Challenges in Digital Forensics Investigation
The amount of data involved in a case may be large depending on the circumstances. In that situation, the investigator must review all of the data that was gathered to compile evidence. The probe could take longer than expected. Time constraints are yet another difficult task and pose a challenge in digital forensics investigation.
In the case of memory forensics, since the data stored in volatile memory is transient, user activities are rewritten in the volatile memory. Therefore, only recent data saved in volatile memory can be examined by investigators. As a result, the data’s forensic usefulness for the inquiry is diminished.
There are various digital forensics challenges in evidence handling in digital forensics for an investigator. When gathering information from the source, an investigator must ensure that nothing is altered or overlooked during the course of the inquiry and that the information is properly protected.
Investigative work is tough due to damaged data sources. Therefore, it is a serious problem when a researcher discovers a useful source that cannot be used.
Now, apart from the above, some other factors make digital forensics investigation challenging.
Digital Forensics Investigation Challenges – Some Other Factors
Three such aspects are there that are becoming obstacles in the investigation process.
1. High Volume
Large-scale data acquisition, storage, and processing issues have been a problem for at least ten years. But, they are currently getting worse due to the accessibility and broad marketing of digital data.
For instance, in the case of live network data analysis, this is especially important because the investigator might not be able to record and preserve all the essential traffic. An explosion in the amount of data that needs to be kept and processed for gathering evidence or detecting occurrences is caused by the availability of gigabit-class networks and multimedia-rich material.
2. Case Complexity
It is required to perform forensic case management to analyze evidence. This is because evidence is dispersed throughout numerous physical or virtual places, including cloud resources, personal network-attached storage devices, and online social networks, as opposed to being contained within a single host. For this reason, it takes more knowledge, resources, and time to completely and accurately rebuild the evidence.
To manage the complexity and find the required evidence, investigators need to automate their approach.
Additional Information: Since most cybercrimes involve emails, investigators can find email evidence by using robust software like MailXaminer. It solves the challenges in digital forensics investigation, especially in the field of email analysis to a great extent by performing different Keyword searches.
3. Development of Standards
Files continue to be the most common digital artifacts to be gathered, organized, and studied, despite technological advancements. Therefore, the research community has attempted to come to terms with common formats, schema, and ontologies. But, so far with little success.
The Best Way to Deal with Every Digital Forensic Challenge
To deal with such issues, an examiner should opt for the best techniques used to investigate emails. It is suggested tp opt for the global leader software Email Investigation Tool. This is the advanced software that is especially designed for the examination of emails. Not only these, but it has consisted of various advanced features as well.
As far as challenges in evidence handling in digital forensics are concerned, it allows you to add the case and add files as evidence. Afterthat, it provides you a complete data in a dashboard. You can see an all-indexed that now.
- The software will provide you with a smart option to see the links between the email IDs.
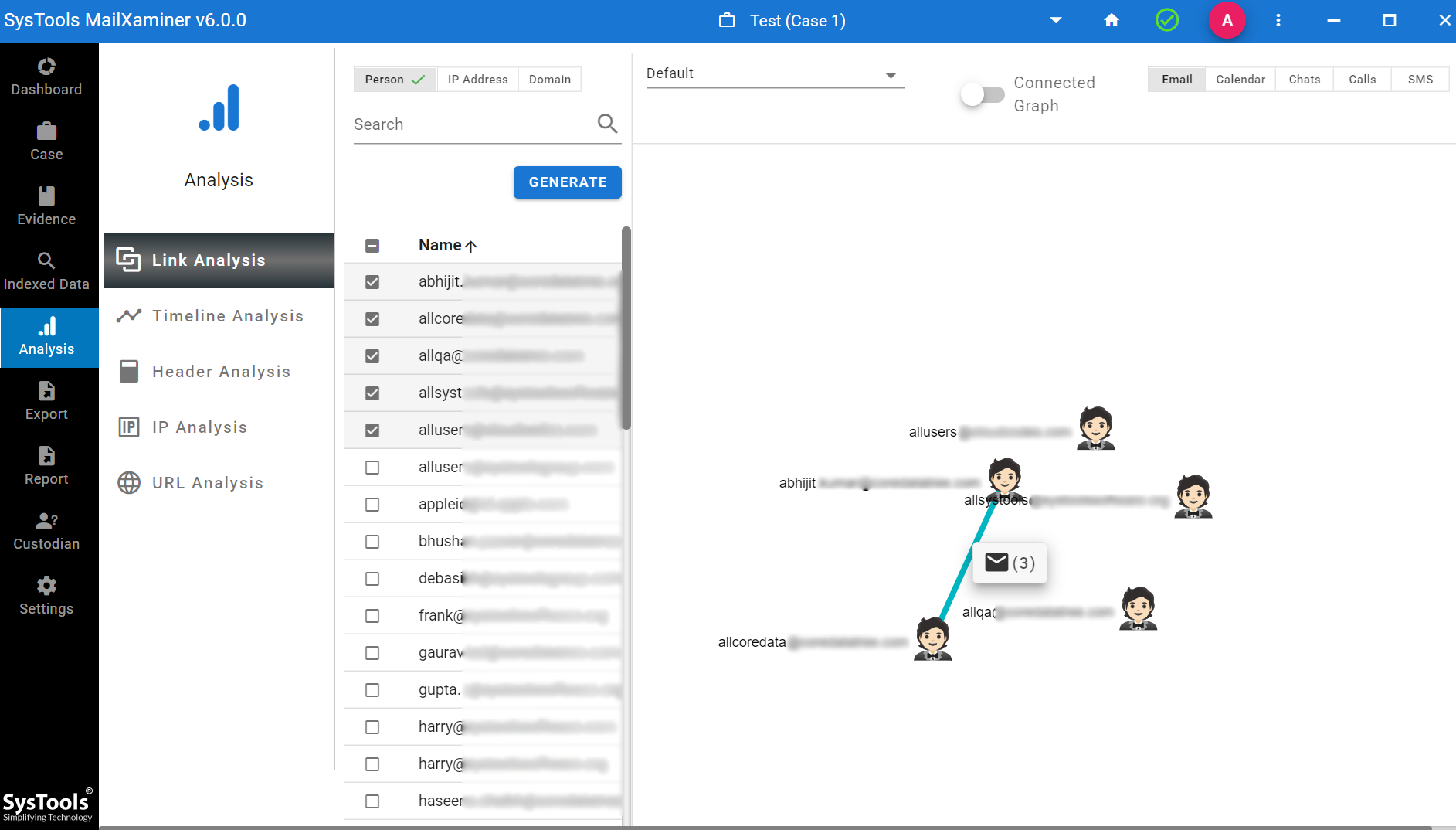
- This tool allows a digital forensic investigator to view the complete email data, such as attachments, HEX, HTML, Message Header, MIME, Properties, and URL Analysis.
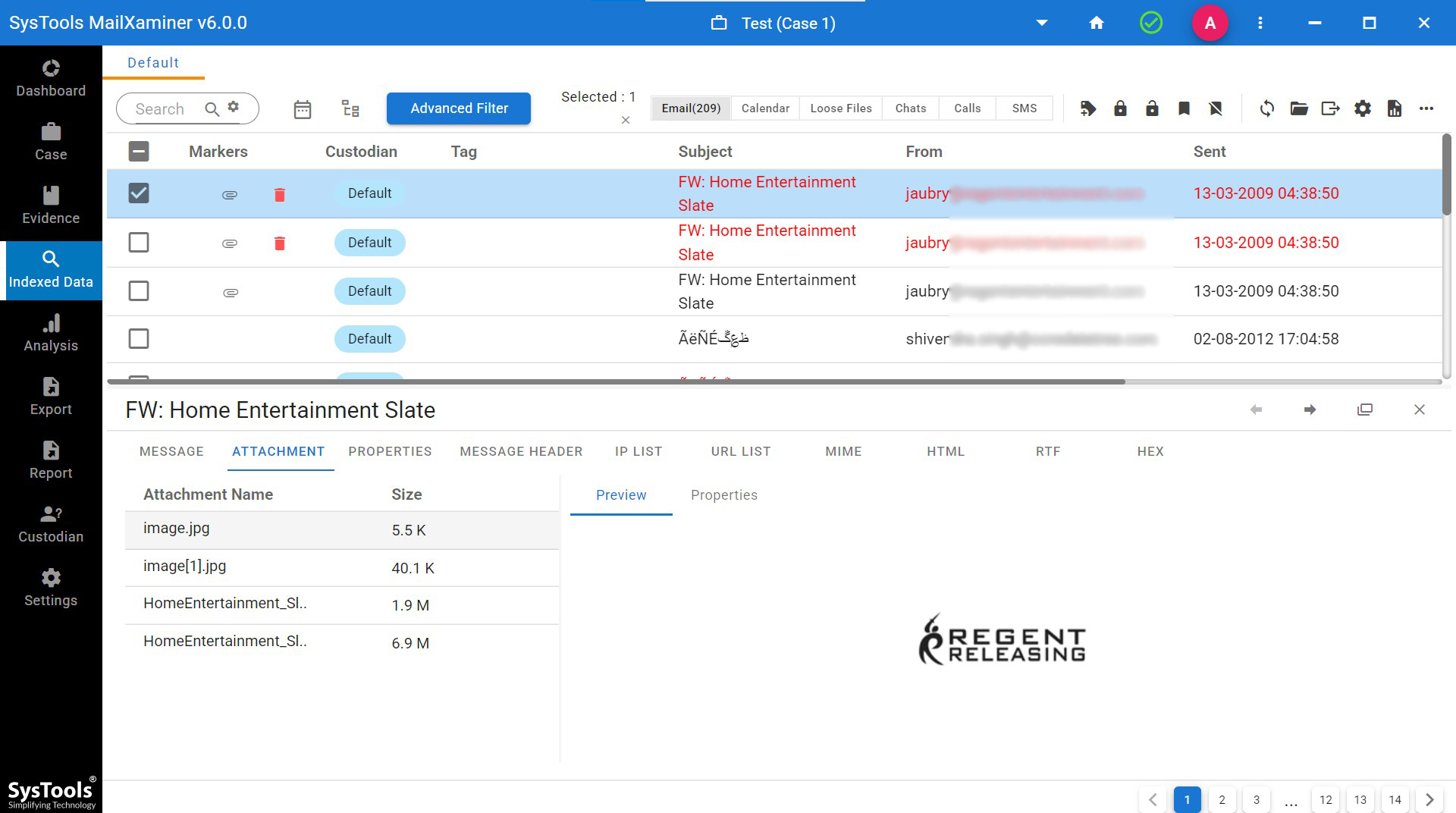
There are various digital forensic investigation challenges we have discussed in this guide. MailXaminer is designed to fulfill all the requirements of an investigator during an analysis of evidence. Try the software and leverage every feature of the software in detail.
Conclusion
The field of cyber forensics is broad in and of itself. The lack of availability of proper guidelines for collection, acquisition and presentation of electronic evidence,use of anti-forensic techniques by criminals, use of free online tools for investigation, etc. are some common challenges in digital forensics investigation that need to be addressed.
The rapid advancement of technology often benefits cybercriminals. This makes it difficult to track and gather accurate evidence. Additionally, the legal landscape, with its varying privacy laws and regulations across regions, further complicates the investigative process.
Despite these hurdles, digital forensics remains essential in combating cybercrime. As technology continues to evolve, it’s becoming super challenging for forensic professionals to stay ahead of emerging threats. Also, to adopt innovative solutions to ensure the integrity and effectiveness of their investigations.

