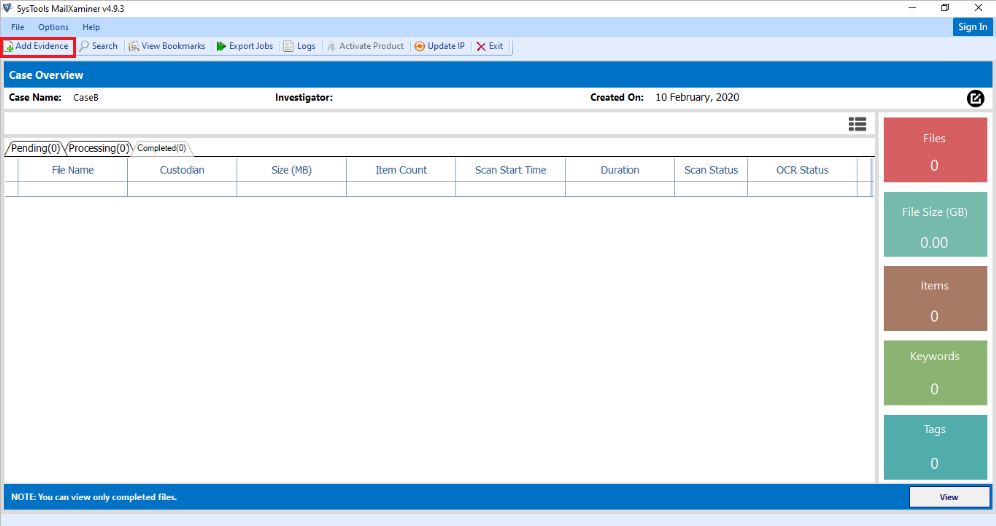
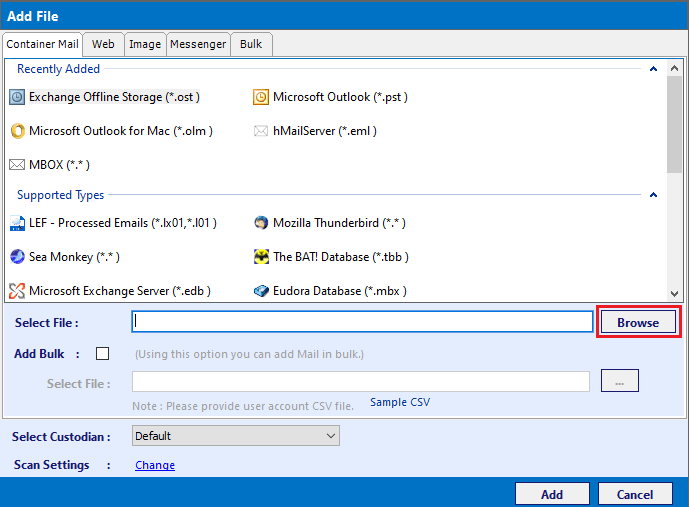
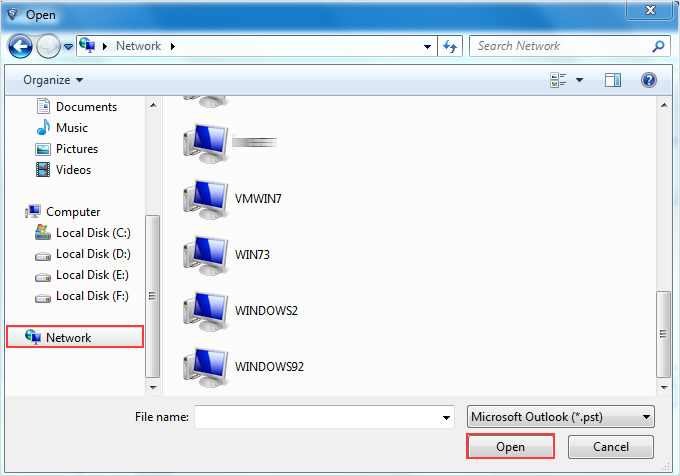
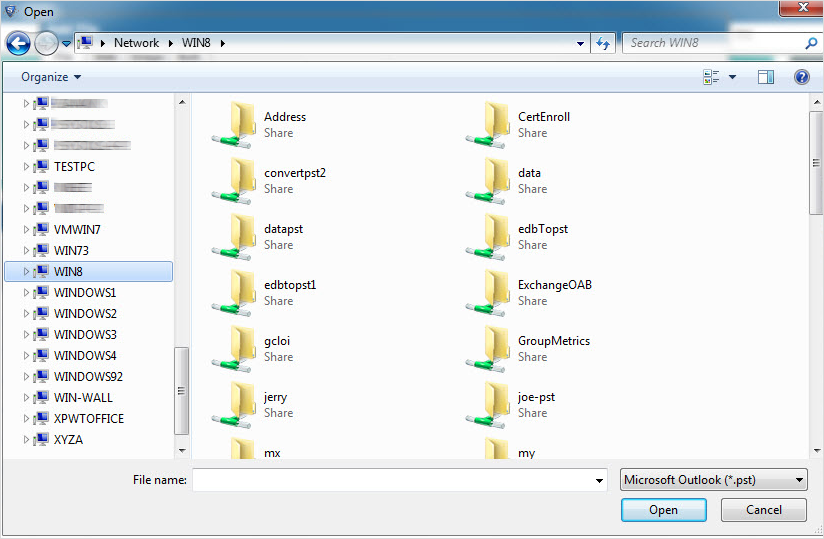
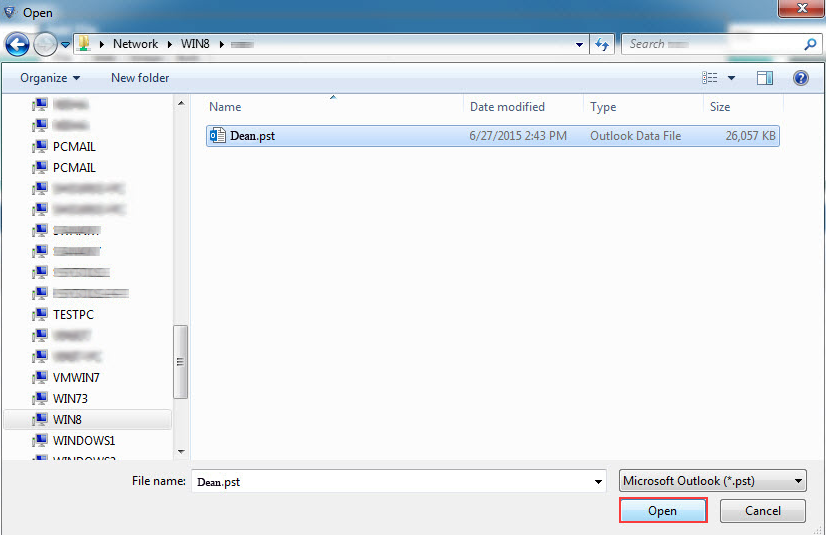
Acquire Email Evidence Across Network

Windows Operating System has this functionality of connecting multiple computers altogether for internal sharing and exchange of data. Microsoft uses two different logical models for this, Workgroups and Domains. Corporates computers are usually connected through such networks. In case of any corporate forensic investigation, it is important to analyze all the connected systems for complete network data analysis in peer to peer file sharing. Investigators must be aware of the arrangement and differences between these two models in order to monitor and examine security vulnerabilities.
Two Different Logical Models
- Workgroup: Workgroup can be defined as an arrangement for peer-to-peer file sharing networks where each computer is independent but are connected through a network used for data exchange. This network has list of authorized users with passwords applied on it along with security rules & permissions applied.
- Domain: Another logical structure model for organizations is Domain. It is a group of computers with centralized administrative authentication and control. The connectors, switches, and routers used for physical connection are same for Workgroup or Domain. However, this eases the administrative tasks with centralized control.
Network Data Analysis in Peer to Peer File Sharing
The peer to peer file sharing networks allow the user to access and share the data within the network. In the corporate level operations they normally use this kind of file sharing method to easily share data and collaborate the works between the peers. How much this method have importance that much risky also it is. The three common categories of P2P file sharing networks are:
Centralized networks
In centralized network one central index server maintain information about all active nodes in that network. If any new nod need to join in the network then it need to send information about itself to the central index server.
Completely decentralized
In completely decentralized P2P network there is no any central index server or directory. All nodes in this network is identical and no nodes containing more information or functions than its peers.
Semi-centralized networks
In semi-centralized networks multiple nodes contains the index information. They are known as the “super nodes or hubs”. These nods need to perform functions in addition to the regular nodes in the network.
Proper understanding of different types of P2P network will help to efficiently perform network data analysis in peer to peer file sharing during the forensic investigation.
Collection of Evidence from P2P File Sharing Local Network
In the corporate world, the use of peer to peer local network is very common to share and integrate the workers in their jobs. When a peer to peer file sharing network contains an information or data file related to any crime or any unethical activity occurred on the file transfering network. It is necessary to perform P2P forensic investigation to identify and analyse the data. With the help of forensic evidence collection tool, the evidence from the computer network can be extract easily.
Challenges in Forensic Investigation of Peer to Peer Networks
During the network data analysis in peer to peer file sharing, several stages of evidence collection is needed. Challenges during the evidence collection can be classified as legal and technical. The legal challenges in peer to peer forensic data analysis includes jurisdiction, spreading of illegal content etc.