Guide on Apple Mail Forensics: Detailed Analysis
Before moving ahead with the Apple Mail forensic, let’s first understand what Apple Mail is. Apple Mail, or simply Mail, is an email client that is built for all Apple operating systems, such as Mac OS, iOS, etc. Mbox is a compatible file format.
Given the popularity of Mac devices and the increased number of Apple users, cybercriminals have shifted their interest in carrying out email crimes using Apple Mail. Since the security options in Mac devices are robust and hard to bypass, an investigation on these devices without knowing the user’s admin password becomes challenging for digital forensics investigators.
So, let’s discuss the core attribute through which one can perform Apple Mail forensics to bring out vital evidentiary information.
Heart of Apple Mail Forensics – Apple Mail Email Header
One interesting thing about Apple Mail is that it can be configured with email clients like Gmail, Yahoo Mail, Exchange, and iCloud. Currently, for sending emails, the running version of Apple Mail uses email verification records in cyber forensics like SMTP protocol. Plus, for retrieving emails, it uses IMAP and POP3.
That means whenever a user tries to send/receive emails via Apple Mail, those email messages will contain some block of text, which is commonly referred to as the header in the email client.
This email header plays an important role in Apple Mail forensics. Cause it holds all the necessary and crucial information for email analysis that can help investigators find clues to solve a case.
Different Attributes in Apple Mail Header
For carving out evidence from an Apple Mail, digital forensics investigators need to analyze every component of the header. That includes:
- Message ID: Every email message has a special ID, which is made up of a mix of letters and numbers with a web extension. This ID is unique to a certain email message and is helpful in Message ID analysis.
- MIME-Version: This Apple Mail characteristic displays the MIME version that is currently being used in that specific email message.
- X-Originalarrivaltime: In Apple Mail headers, this element displays the email’s first arrival time together with the current date and time.
- From: This Apple Mail characteristic displays the email ID of the user who received the email.
- To: This Apple Mail characteristic displays the email ID to which the email message was sent.
- Date: This Apple Mail feature displays the date that a specific email message was sent.
- Delivery Date: This Apple Mail feature contains information about the delivery date and time.
- X-Mailer: This feature of Apple Mail lists the email client and the IP address from which it received the email.
- Apple Mail’s Content-Type: This header field identifies the type of email message content. Additionally, it shows the data and character set that were included in that specific email message.
- X-eopatrributedmessage: It contains the value regardless of whether the user has received any messages or not. Its value can be either 0 or 1.
Now comes the question of how you can view the header information.
Steps to View Apple Mail Email Header Information
It’s obvious that when you open an email on an Apple Mail client, you won’t be able to see the header data directly. So, to view the header, you need to follow the steps below;
- Select any email message where the headers need to be read after starting the Apple Mail program.
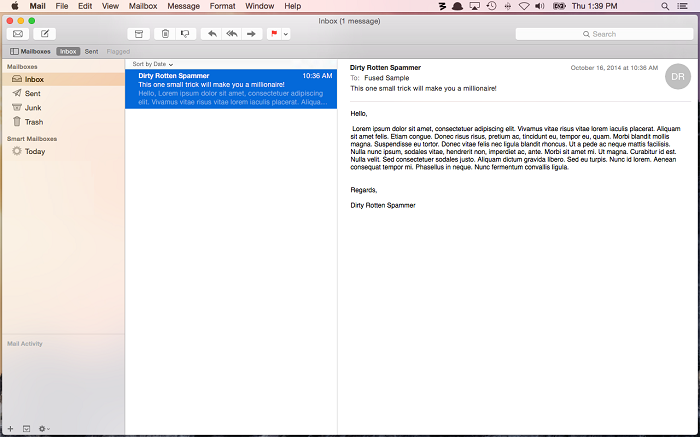
- Now select the Message option from the View tab’s menu, and then under Message, choose Raw Source.
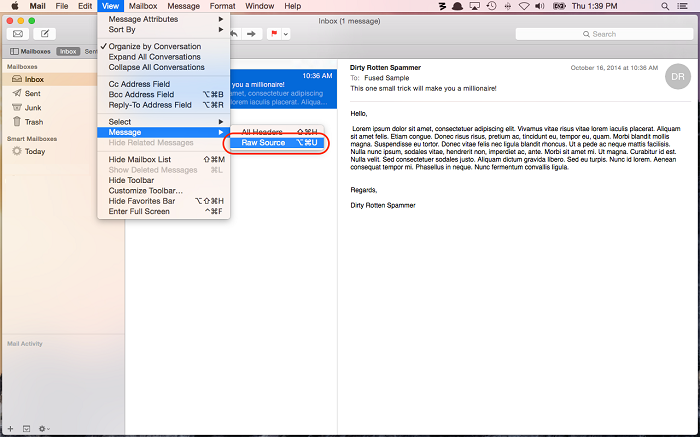
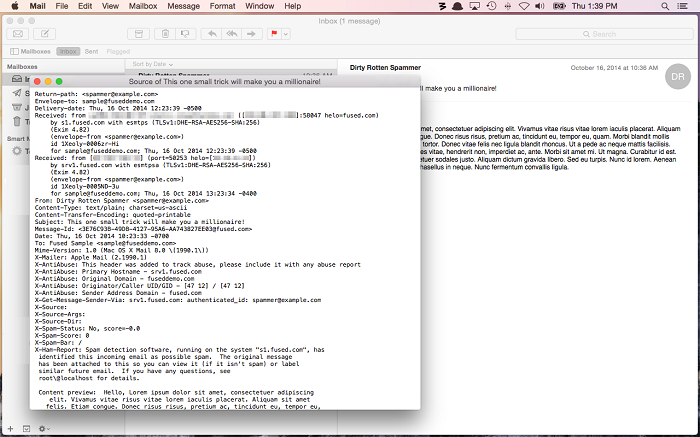
- The user can then examine all the information in the email headers located at the top of the email message. The email headers contain all the necessary details, such as the mail server, content type, employed IP address, etc.
Undoubtedly, you can manually view the header components of one email at a time. But, if you like to enhance your experience and want to view the header data on a professional dashboard, then look no further than Email Forensics Tool by MailXaminer. This tool can even let you view the header information of deleted emails. So, you can say that it is capable of performing Apple Mail Forensics from every angle.
Examination of Apple Mail Using a Professional Investigation Tool
The software works as an Apple Mail MBOX analyzer that emerges as a standalone provision during the investigation. The application extends a unified platform for reading MBOX files along with their contents in a detailed manner. Moreover, the application comes integrated with an additional range of investigation-friendly options like Bulk Mailbox Processing, Multiple Views, Evidence Searching, Extraction, and Reporting in other formats etc. In the section below, we will discuss the advanced features of this software in detail.
Bulk Mailbox Processing
This software allows the processing of a huge amount of data for investigation. Users can add single as well as bulk files by providing the CSV with the location path of files or folders. Along with this, the tool supports a wide variety of email file types, including MBOX related to several web-based or desktop-based email clients.
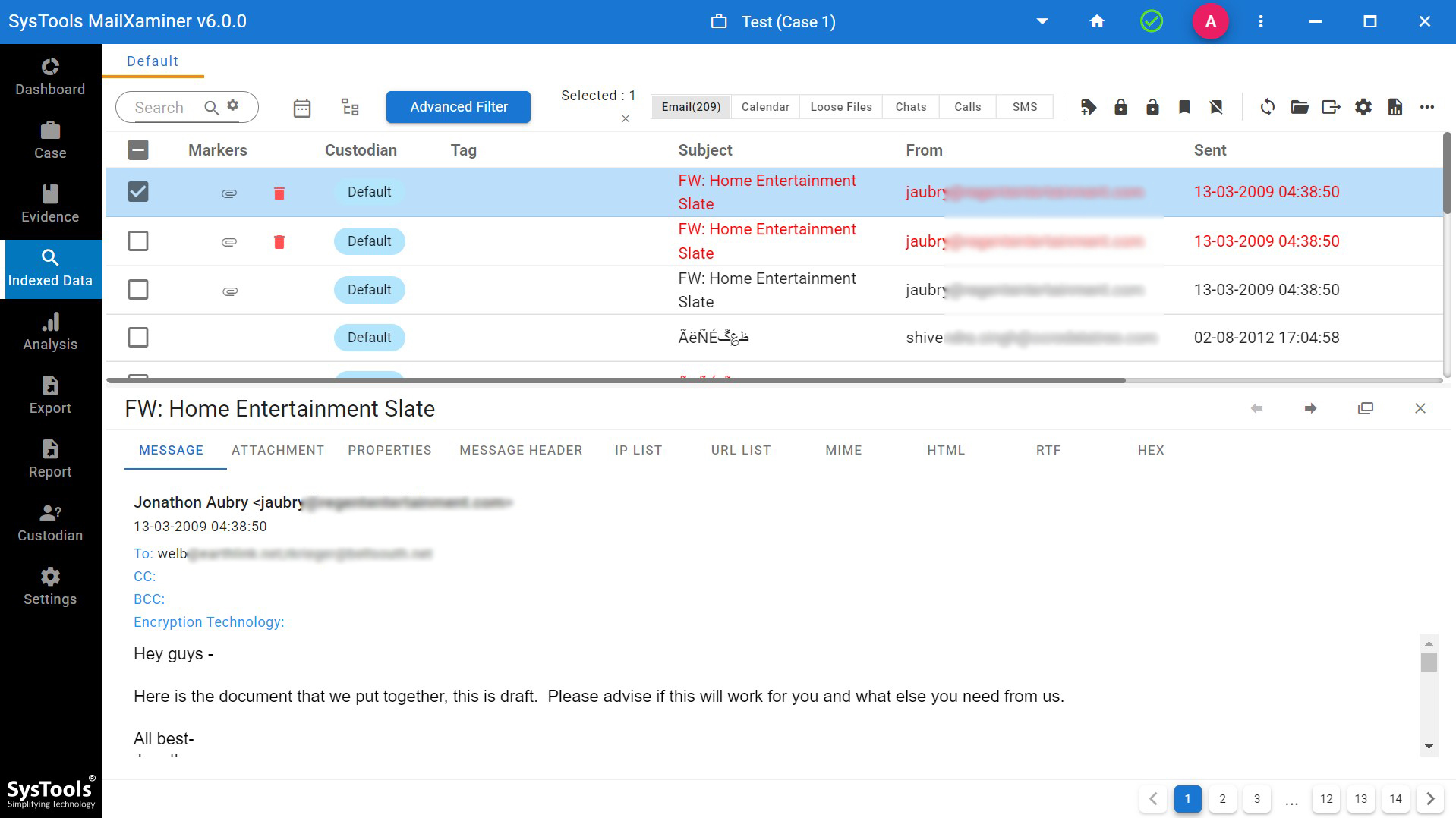
Multiple Views of Evidential File
It provides multiple views of email files, defining hidden artifacts from the email files. The tool provides 7+ preview modes such as Message, Hex, Properties, Message Header, MIME, HTML, RTF, and Attachments. These preview modes help investigators to view and analyze hidden information from the suspected files to extract the evidence.
Evidence Searching
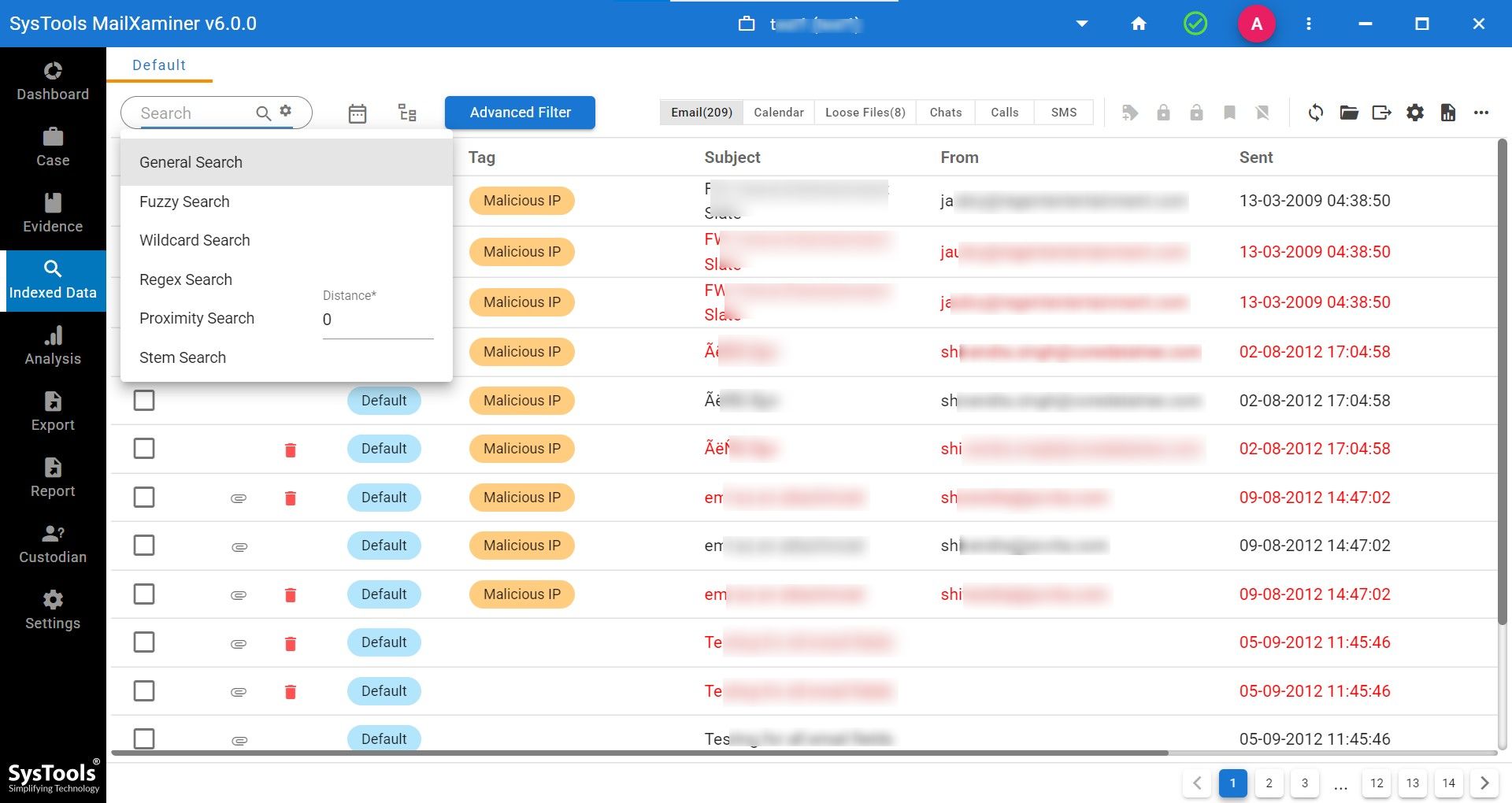
This tried and tested tool allows us to add our filter to search for the required evidence data, and it also provides various inbuilt searches based on advanced algorithms. Search functions such as General Search, Proximity Search, Regular Expression, Stem Search, Fuzzy Search, and Wildcard Search are provided by the tool to filter out the required data. Along with this, users can also avail themselves of logical operators in search filters (AND, OR, NOT).
Extraction and Reporting in Other Formats
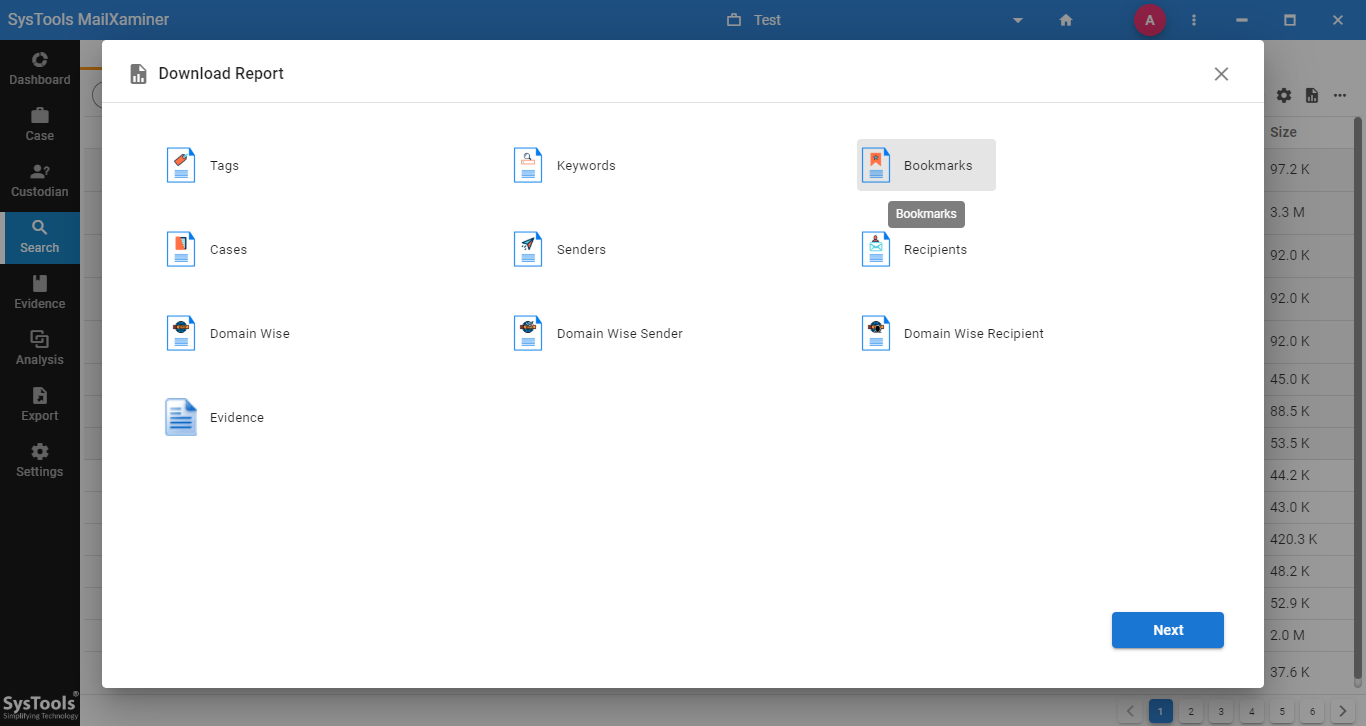
The software provides an option to extract several kinds of reports in different file formats. It helps the user to categorize and extract the evidential data in the desired file format. The report consists of various types, such as Case Reports, Keyword Reports, Tag Reports, Bookmark Reports, etc. Users can also select the files that they want to display on the report. For this, they have attributes like To, From, Cc, Subject, Body, Mail ID, etc.
Final Verdict
Apple Mail application stores emails in .mbox file format. MBOX is a text-based file type that contains a standard structure for the arrangement of data. The above-mentioned software for Apple Mail forensics comes with the standard provisions of investigation, principles, and prerequisites. With this utility, working on the MBOX file is relatively convenient for investigators to investigate the hidden artifacts.

