Pegasus Forensics: Analyze Mailbox to Carve Out Culpable Evidence
The age of pervasive computing technology has opened the doors for criminal activities. Nowadays, it has been observed that the most common type of litigation case in the court of law is theft of intellectual property. Generally, such type of cases involve an employee who has passed on valuable company-related information to a third party through email messages. To deal with cases where the employee violates organizational norms, the law enforcement agencies take the help of a forensic investigation team, which can carve out suitable evidence to prove the accusatory guilty before the law.
When forensic investigators deal with such types of cases, they need to perform a thorough analysis of the email client and its messages. Now, how can the forensic examiners carve out evidence if the email client involved over here is Pegasus Mail? Before going into the forensic details, let’s first have an understanding of the Pegasus email application.
Get an Insight to start Pegasus mailbox analysis
Pegasus Mail is a free electronic emailing application that has been designed with a myriad of excellent attributes to provide a secure form of communication on the Windows operating system. It has been built around with impressive set of features to filter incoming messages and to control spamming with the use of Content control and Spamhater filtering techniques. Further, the mail client supports multiple POP and IMAP accounts from one single account.
Getting Started With the Process of Extracting Evidence
During the procedure of Pegasus mailbox analysis, we need to understand first its basic mechanism related to the storage of files and folders.
In an email application such as Pegasus, it is normal to interact with two servers. One is for incoming and the other is for outgoing. Whenever a user needs to read out a mail message, the Pegasus email client connects to the specific mail server by employing one of the protocols:
- IMAP
- POP (Post Office Protocol)
- MAPI
Whenever forensic investigations are carried out by examiners, the protocol which is used for gathering incoming messages is not of interest. Here, the most important thing is how the role of these protocols affects where the email messages are saved.
Taking a Deep Dive Into the Storage Location of Messages
Pegasus mailbox analysis shows that messages are saved in the PMAIL folder. Now we need to have a look at the details of the PMAIL folder.
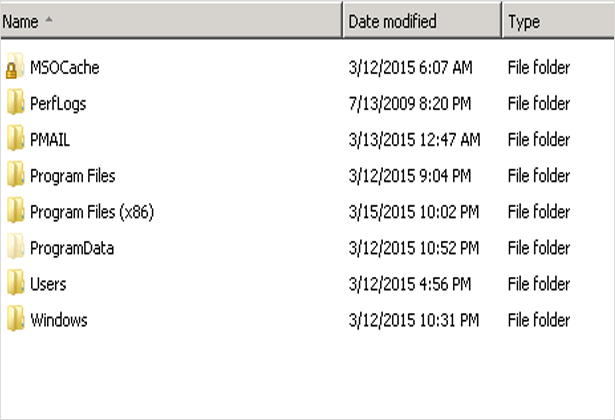
Files Located In Pmail and WinPMail New-Mail Directory
CNM: When a new message arrives, it will have a file extension of .CNM.Thus, this type of file extension refers to the actual arrival of a message. The filenames associated with the mail messages are unique, and so they are referred to as message IDs. The actual name of such a type of file normally begins P which refers to a POP3-delivered message.
The location of the CNM file extension messages is given as follows:
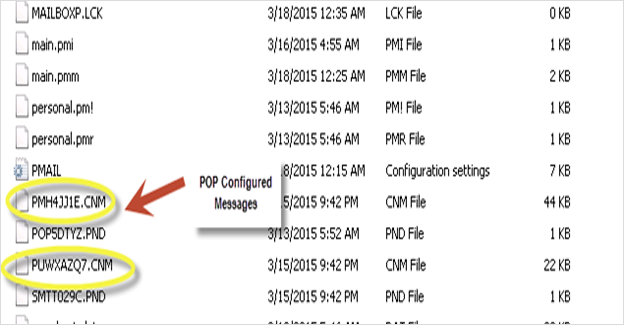
Scooping Out Evidence via Pegasus Mail Forensics
The structure of the messages in the New Mail folder is somewhat different. Here, each message is stored as an individual file, whereas other folders like junk or main folder have all their messages stored in a .PMM file with a corresponding index file that has .PMI extension. So, for each folder, there is a file pair.
PMF: These files are considered to be attachment files. These are formed when local messages are sent with attachments. They are indicated with a message that has a p
PMN: These are referred to as annotation files and are associated with their relevant messages.
PML: These files are associated with a distribution list. Distribution lists are text files with each line having one email address. Suppose a message is sent to @<file>.PML. Here, @ refers to a particular message that is sent to all the email addresses present in the distribution list. So, one can easily find out which email address the employer has sent messages.
CACHE.PM: This file can provide important information about the folder list that was used the last time Pmail was started. So forensic examiners can get a look into the folders in which can provide details about the activities of the employees.
During Pegasus mail forensics, deleted messages often provide a lot of important clues which can bring about an up twist in litigation cases. If important messages about the company have been exchanged by the employee with some other parties or competitors, then recovering deleted messages can provide incriminating evidence. To find out whether there were any messages deleted from Pegasus Mail, forensic investigators can simply perform re-indexing of that folder from Pegasus.
Restoring Deleted Folders
Generally, the employees in such type of cases also deleted the messages folder. If there are any messages in the deleted messages folders, then probably these messages can be retrieved again by selecting the “Reindex folder” option during Pegasus mailbox analysis.
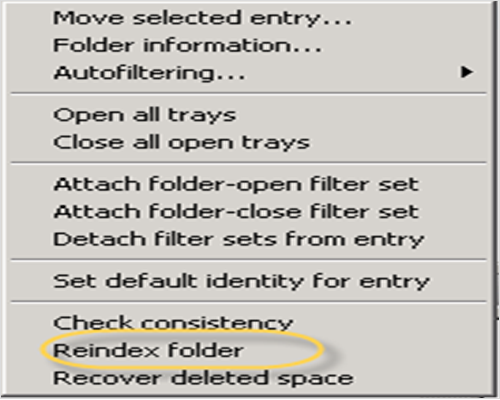
Once this option has been selected, it will display a message given as follows
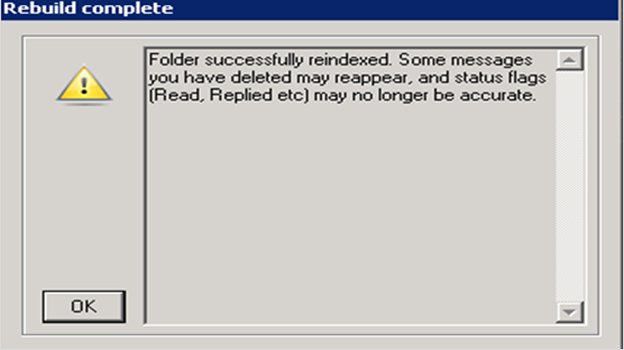
And the deleted messages will be shown once again in the list of folders.
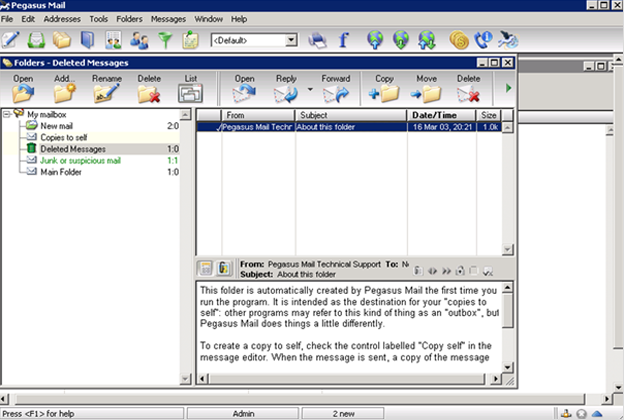
Extraction of Password
Normally, it’s not possible for investigators to gain access to the configured POP client in Pegasus Mail. However, a small kind of work over can make this possible to forensically analyze the Pegasus mail password.
In the Pegasus Mail interface, under the “Tool” option, select Internet options, and when a window appears, enable the option “Create internet session logs (advanced diagnostic use only).
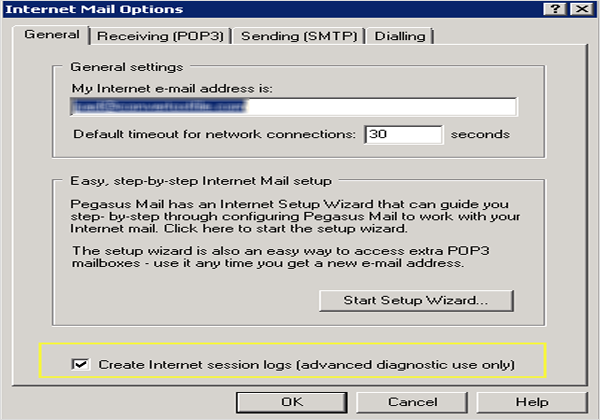
This will create a file TCP0001. WPM in the mailbox directory.
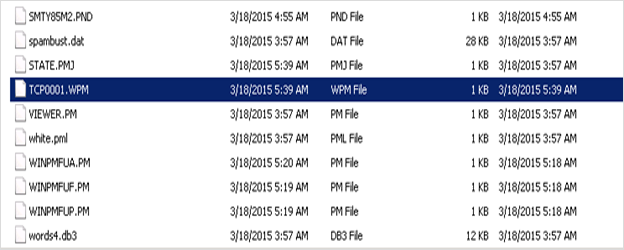
On opening this file with a text editor, one can find out the Pegasus mail password for the configured POP client.
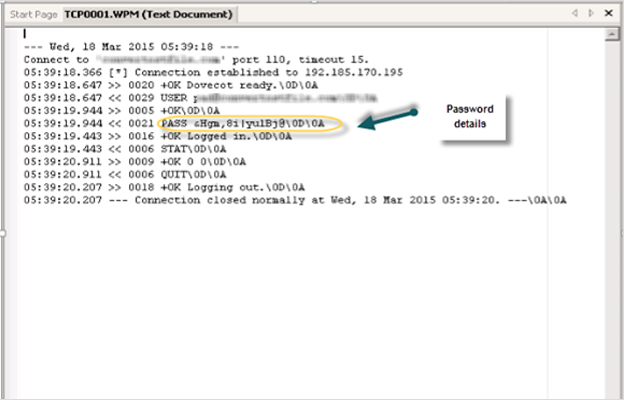
By logging in with the credentials in the text file, we can carve out other evidence from the configured email client.
As such of crime proliferates on a wider scale, it is obvious that law enforcement agencies will never have the required time and effort to investigate these cases. For fairer prosecution of internet-related criminal activity, they take the help of investigation agencies that have the potential to scoop out evidence. All those procedures mentioned above can help forensic investigators to carve out important clues from Pegasus Mailbox analysis. This evidence can act as inculpatory or exculpatory evidence; therefore, if presented before a law can prove the defendant guilty or free of crime. Further, there are many better forensic tools available in the market that can help forensic examiners to exhibit information related to the crime more precisely.

