Know How to Prevent Email Spoofing Attacks – Best Ways
Case Scenario:
“Recently, a guy complained that someone is sending nasty emails to his friend from his email address. Upon complete investigation, investors found that spammers were sending emails to his all friends. The primary intention of the email spammer was to ask for money by sending a link and/or click here to pay. The click here link takes them to the payment portal.”
The above mentioned case scenario is a real life example of email spamming. Spammer targets the person because spammer knows that those who receive these emails will trust because of its genuineness. Under such circumstance as of the above mentioned scenario, the recipient must contact the host of the email address before sending or sharing money or any personal details.
What is Spoofing Attack?
In email accounts fraud, there are various techniques that attackers choose to perform phishing campaigns. One of the widely chosen way to fraud by attackers is email spoofing. Email spoofing is a synonym for Phishing. In this blog, we will discuss in detail what does email spoofing mean as well as how to prevent email spoofing attacks.
Email Spoofing Meaning in Computer Security
Email spoofing is the fabrication of an email header so that the email appears to have come from the actual source, however it is actually originated by someone else from somewhere. Email spoofing is a popular strategy which is used to trick the recipient to theft their sensitive information. Moreover, the spoofed emails are just a problem that needs an action apart from removal and sometimes gives rise to a real security threat.
For example, a spoofed message may pretend to be from a well-known company, asking the receiver to provide his personal information such as credit card numbers, passwords, etc. or asking to click on a phishing link.
How does Email Spoofing Attack Work?
Many of you might have come cross with an instance wherein an email message from your friend looks strange or might be annoying too. It doesn’t mean that someone hacked your friend’s email but instead attackers spoofed the email address that is actually not a tough task to do. Here’s how they do:
Email spoofing is feasible in nature because the SMTP (Simple Mail Transfer Protocol) should not be considered for providing address authentication. It is the flaw in SMTP through which spammers can perform spoofing easily.
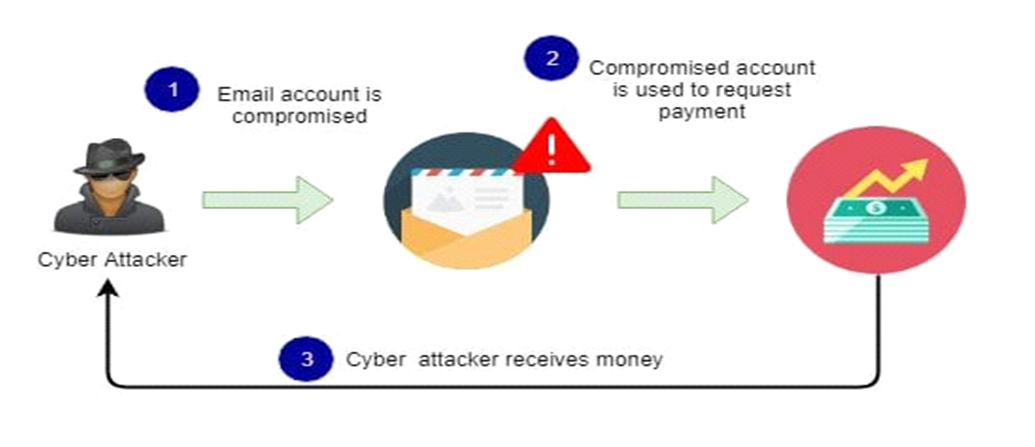
Reasons for Email Spoofing
Email spoofing mostly known for phishing, there may be several reasons behind email spoofing. It can be used to:
- Hide identity: Through email spoofing, senders can easily hide his true identity. It can be done by registering anonymous email addresses.
- Avoid Blacklists: If the sender sends spam emails, it may be blacklisted. To avoid this problem a simple solution is to switch email addresses by spoofing.
- Pretending to be someone else: To ask for personal information or to access personal resources, the sender pretends to be someone whom the recipient knows.
- Identity theft: In order to ask financial accounts from victims, spammers may send+ emails using someone’s name to commit identity theft.
How to Prevent Email Spoofing Attacks?
To prevent email spoofing and spamming, the following practices should be considered:
- Keep the antivirus in system up to date to prevent email spoofing attacks.
- Avoid sharing private or financial information through emails.
- Turn on the spam filters from the settings option to stop email spoofing or other scams.
- Do not directly click on suspicious links.
- Avoid downloading suspicious attachments.
- Never enter any personal information by clicking on insecure links.
- Perform reverse IP look-ups to know the real sender.
- Analyze email accounts to stop email spoofing. Several frameworks are designed to authenticate email messages.
- SPF (Sender Policy Framework): It recognizes whether a certain IP is valid to send emails from a given domain or not by checking the SPF record.
- DKIM (Domain Key Identified Mail): In this method, cryptographic keys help to validate the incoming messages and sign the outgoing messages.
- DMARC (Domain-Based Message Authentication, Reporting, and Conformance): It gives an option to know whether the sender’s email is protected by SPF or DKIM. It also gives an idea about in case of authentication failure what actions needs to be performed with the email.
Best Ever Technique to Track Email Activities Via MailXaminer
During an investigation, email is one of the most useful artefact that investigators can look to find the potential evidence. Investigators usually track email activities; dated, signed, etc. using forensics software i.e., MailXaminer. With this email forensic software, it helps to track the email activities easily with its amazing advance features. Some of the highlighted features of the software which can help to investigate the emails thoroughly, are as follows:
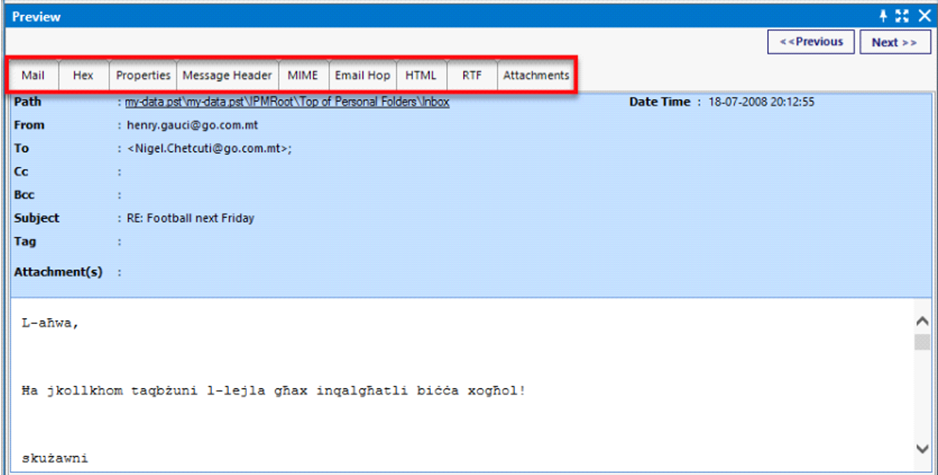
It provides facility to view all the information of Mailbox data in different modes. It gives several options to view and analyze email files along with the attachments in several modes such as Mail, Hex, Properties, Message Header, HTML, etc.
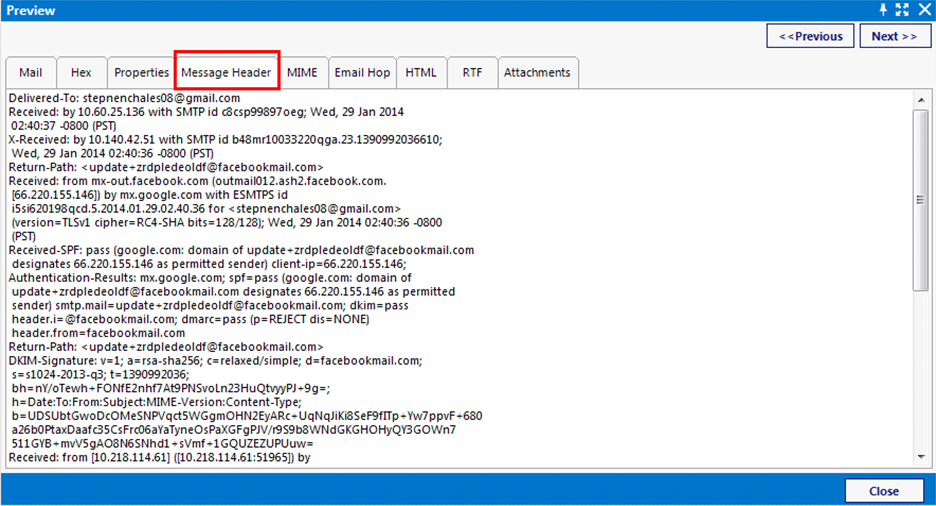
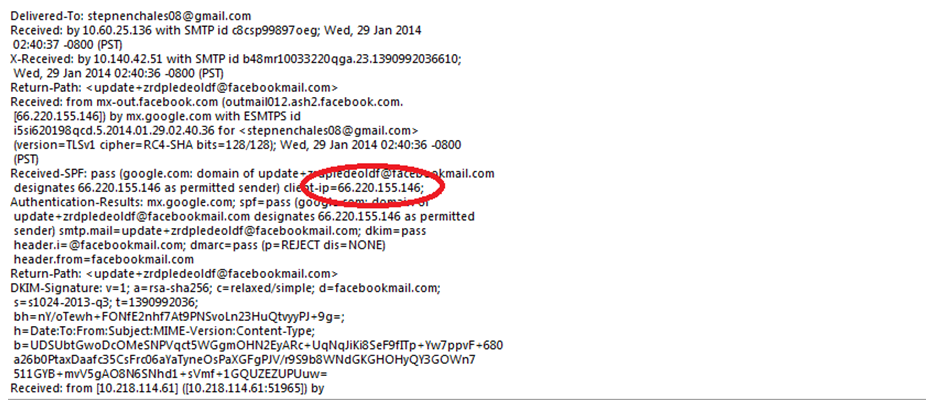
MailXaminer provides an option to view the email in “Message Header” mode. It helps in header analysis of the email.Moreover, users can easily examine the components of the email header such as Sender address, Receiver address, Message ID, MIME version, Content type, etc. It plays a significant role to track email activities.
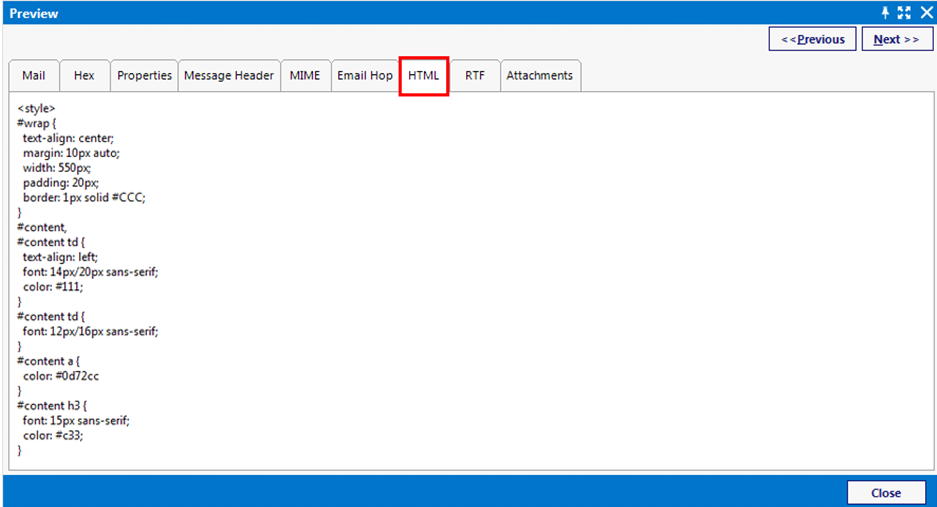
HTML View:
MailXaminer has the ability to show email data in HTML format. It helps to analyze the internal structure of email message with the help of HTML script.
IP Tracking:
Another highlighted features of the tool is that one can easily track the IP address of the person. By tracking the IP address, it becomes easy to check the geographic location that the IP is assigned to.
Conclusion
In the above article, we have discussed that email spoofing is very popular in cyber crimes and there must be some strict action which should be implemented by every individual to curb this activity. Some parameters have been adopted but they are not that enough to stop this. Hence, an email forensics software is mentioned in this article which is exclusively designed to track the various email activity.

