Learn How to Identify Fake Emails to Spot Fraud?
Nowadays, cyber-attacks through emails are increasing day by day. The attackers consider email as a safe platform for their illegal activities. Emails are the most commonly used platform for personal and professional communication. Unfortunately, in today’s world emails are used for criminal purposes by fraudsters. The scammers try different methods to trick the users for financial benefits or for stealing their confidential information. In such situations, it is important to know how to identify fake emails in the mailbox and secure yourself from falling for such frauds. In this blog, we are going to target the tips to recognize fake emails.
What are Common Email Threats?
Some of the common types of email threats that use fake emails to attack the users are Phishing, Whaling, Key loggers, Spear phishing, Ransomware, etc. Most of the organization considers email as their primary mode of communication. All legitimate companies and organizations have certain standards for generating their emails but the emails used in case of email attacks normally don’t match these standards. There are always some loopholes in their message which helps the user to spot the fake emails. In the upcoming section, we will learn tricks on how to identify fake emails.
Tips to Spot and Avoid Fake Emails
Some tricks can help users to identify fake and spam emails in the mailbox in the mailbox. By using these tips, one can easily defend themselves from the danger of cyberattacks. Some of the errors in the spam emails are as follows:
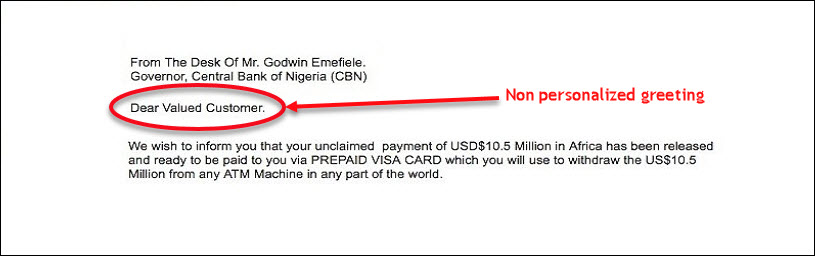
- Non-personalized Greetings
This is one of the most common ways of checking whether the mail is authentic or fake. The emails from the legitimate company will usually address the recipient using their name. But in the case of phishing or fake email, the fraudsters use generic salutation such as Dear Customer, Dear account holder, etc. This is an easy way to find fake emails. But sometimes this information is not helpful. As in some cases, they can manage to get client information and use the proper salutation with the user’s name.
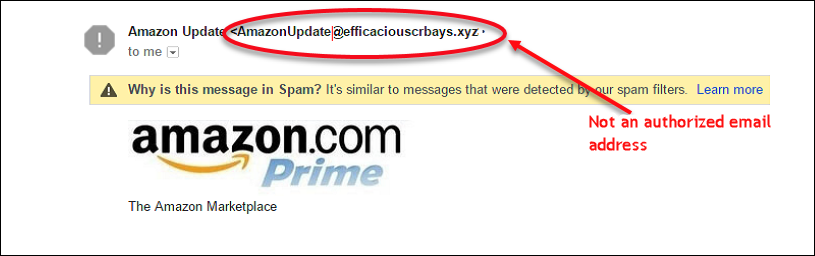
- The Legitimate Organization has Authentic Email Address
To identify fake emails you can also check the sender’s address. None of the legitimate companies or organizations use public internet accounts like Hotmail, Gmail, etc. Fraudsters use email Ids which look similar to the authentic email Ids in order to make the user trust its source of origin. On careful examination, you can observe the difference between fake and authentic email addresses. It in itself is not a foolproof method to find fake emails.
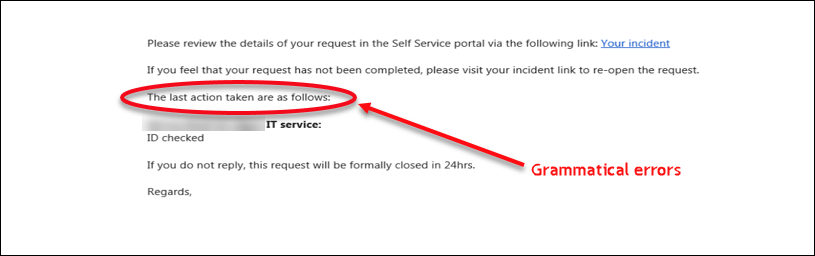
- Check for Spelling and Grammar Mistakes
This is another simple way to recognize fraud emails. The email created by legitimate companies will be well written. Grammar and spelling mistakes are rarely found in such emails. There is a little known fact behind such grammatical and spelling errors in the fraud emails. It is probably because they are trying to target the less observant and less educated users.
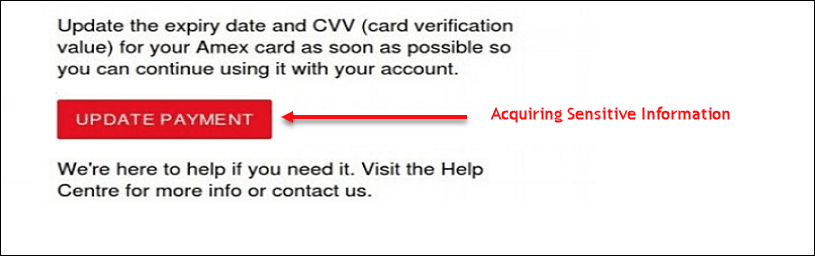
- Requesting for Sensitive Information
Another method to find fake emails is that they will directly request for confidential information. The main focus of the fraudsters who send such fake emails is to make the recipient believe that the origin of such emails is authentic. By this, it enables them to gain sensitive information from the intended recipient.
In most cases, the attackers try to create a panic situation and try to scare the user. The outcome of such activities leads the victim to take some careless step in a haste thereby enabling the attacker to take advantage of such a situation.
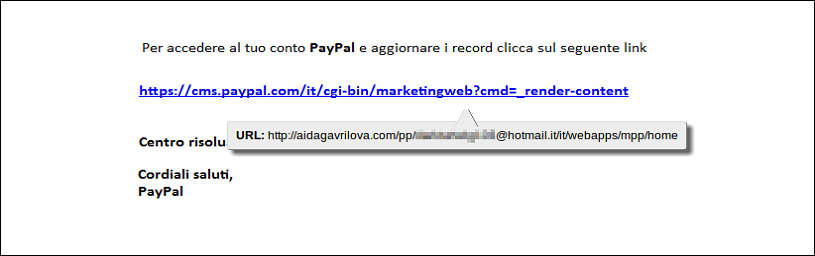
- Containing Incorrect URL
Generally, the phishing emails or fake emails contain malicious hyperlinks which are placed there by the attacker in order to steal the data. Clicking on such links will redirect the user to a fake webpage or download some malicious software into the user’s system. So before opening the emails, make sure the link is authentic. This will help you to identify fake emails accurately. Before clicking on any hyperlink follow the process mentioned below to make sure the hyperlinks are trustworthy.
a) Take the cursor of the mouse over the link. It will show the complete link through which you can see the complete address and ensure that it is authentic or not.
b) If you are using a mobile, use link preview to view the actual URL.
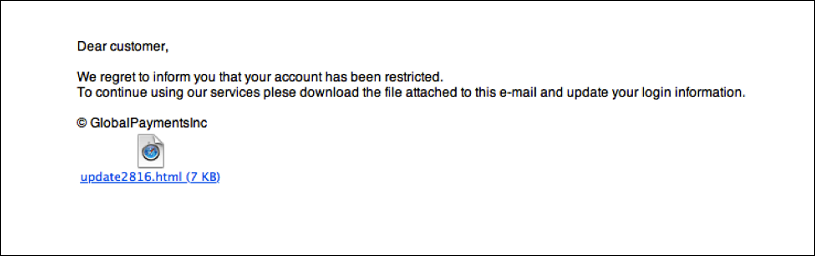
- Contains Unsolicited Attachments
Another way to recognize fraud email is by checking the attachment. The authorized organizations never send a random email with attachments. They always try to send the message with a proper reason and description of the attachment. The most common technique used by the attackers is sending unsolicited emails with attachments. Such attachments can contain malicious software. If a user downloads this attachment there is a possibility that the attacker can get access to the user’s system without their knowledge.
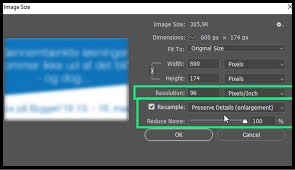
- Low-Resolution Image
Another method is, to check the images in the email. The false sites generally don’t care about their image quality. The poor image quality of the logo and other graphics can indicate that the source of the email is not authentic.
Final Words
Understanding various email threats and how to identify fraud emails will help the users to protect themself from the cyber-attack. In the above blog, we discussed various tips to find fake emails and avoid them. The above methods will help you in distinguishing fraud emails from the authentic one with the help of careful observation.

