How to Analyze Outlook Email Header Like a Forensic Expert?
There are several platforms that help in communicating via Email, Outlook being one of them. Outlook is an advanced email service that provides users with a number of features, including calendar, contact management, cloud storage, keyboard shortcuts, email organization, etc.
The software attracts many customers, making it necessary for the platform to detect and secure itself and its users from spams or frauds. A way to detect fraud or any wrongdoing is Email Header analysis.
What do you understand from the Term Email Headers?
Email headers are necessary for finding out a message’s sender, receiver, date among other routing details. Header details, such as from, to, and date, are necessary. The send and receive time stamps of each mail message are included in the additional headers.
When someone sends an email, it goes through mail transfer agents (MTAs). These MTAs can show if the email was forwarded to other addresses before it reached the final recipient.
Users should choose not to interact with the email if the header information seems unordinary . These are crucial for ensuring an email’s legality and authenticity. One can detect possible dangers and ascertain whether an email has been subjected to these checks by looking at these headers.
What are the Different Ways to analyse email headers in Outlook?
Here are the simple manual steps listed below:
- Step 1- Select the email.
- Step 2- Click the (…) button.
- Step 3- Select View > View the details of the message.
- Step 4- Close the window after copying the header data and saving it to a Word or TXT document.
How to View Outlook Email Header in Windows OS?
- Step 1- Launch the Outlook software.
- Step 2- Select the email that contains the headers you wish to see.
- Step 3- Press the Properties button.
- Step 4- Down below, click the Internet headers section.
- Step 5- Close the window after copying the header data and saving it to a Word or TXT document.
How to Access Email Header in Outlook on Mac OS?
Here are the steps for analyzing Outlook email header on Mac devices.
- Step 1- On your Mac, launch Outlook.
- Step 2- Select the email.
- Step 3- Holding down the Ctrl key, click on it.
- Step 4- Click the context menu and select View Source.
- Step 5- Save it to a Word or TXT document.
What are the limitations of the Manual process?
You can use this technique only for one-time analyses, and it won’t work if Outlook isn’t running. It is also possible to fake the “from” header, which leads to receivers getting emails from celebrities or banks.
One Solution Can Help to Overcome these Limitations
MailXmainer is the perfect solution that can fit into this scenario. It is advanced email analysis software that is especially built with advanced digital forensic investigation techniques. Let’s understand how to analyze Outlook email header more professionally.

Steps to use MailXaminer to analyse Outlook email Header
- Step 1- Installation of the software Investigator Version must meet the Full (Client + Server) requirements. Services can be launched instantly by clicking the Start button. The user will be set up once the login ID and password are entered.

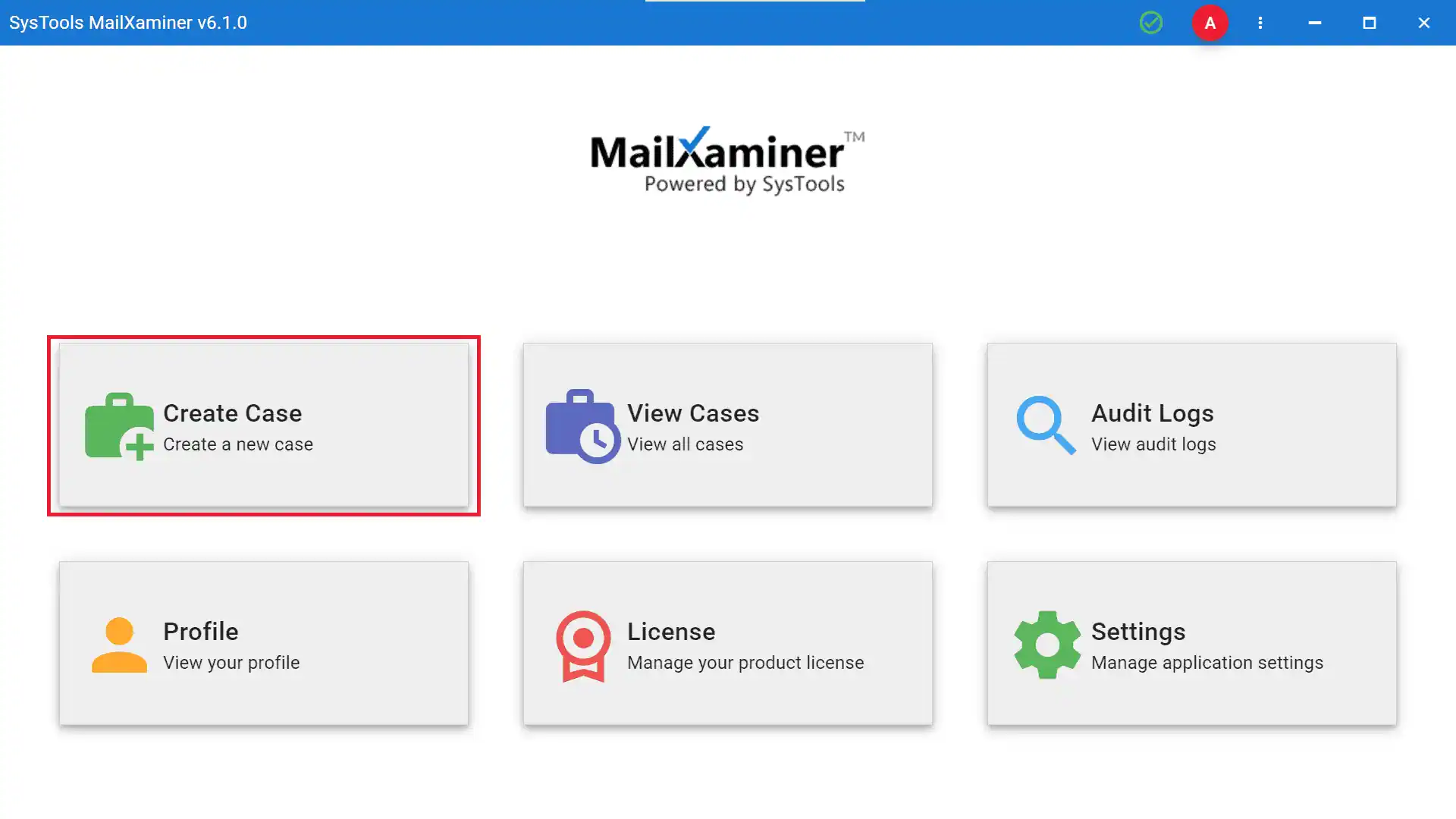
- Step 2- Click the Create Case button and fill in the blanks with the Case Title, Case Number, and Investigator Name to begin an investigation into a file. The Cases window will display the just-generated case.
- Step 3- Choose Email Client and pick an Evidence type from the four options—Email Client, Image, or Messenger—to add new evidence to the program. Use the necessary settings to read calendars, log unprocessed items, scan attachments, analyze links and reports, analyze images, detect digital signatures and encryption (for PST), detect malicious IP, analyze URLs, analyze hash settings, detect digital signatures, and configure rules.

- Step 4- Select “Add New Evidence” to add files to the program. You will see the dashboard, with all the information of the added file.
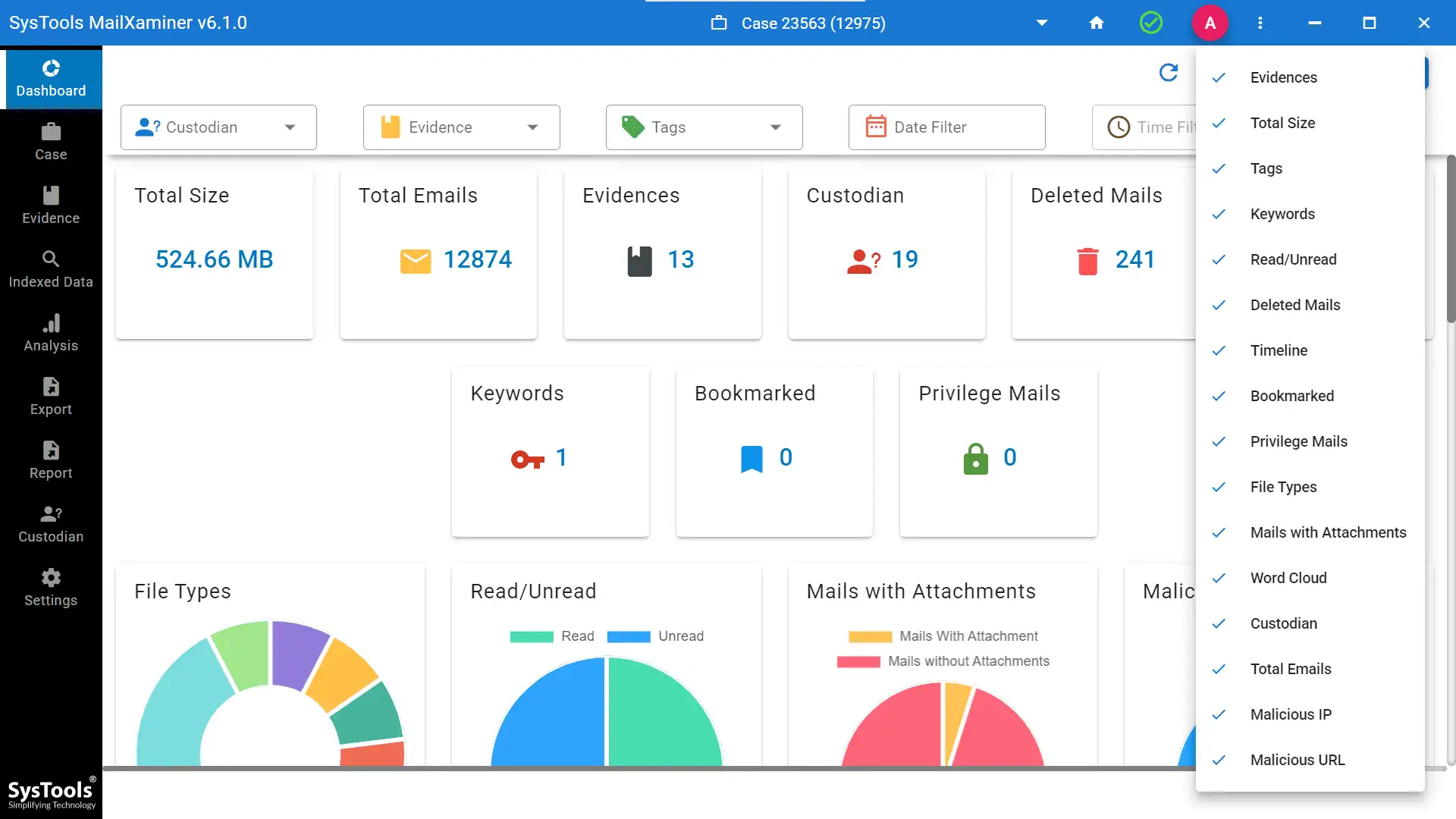
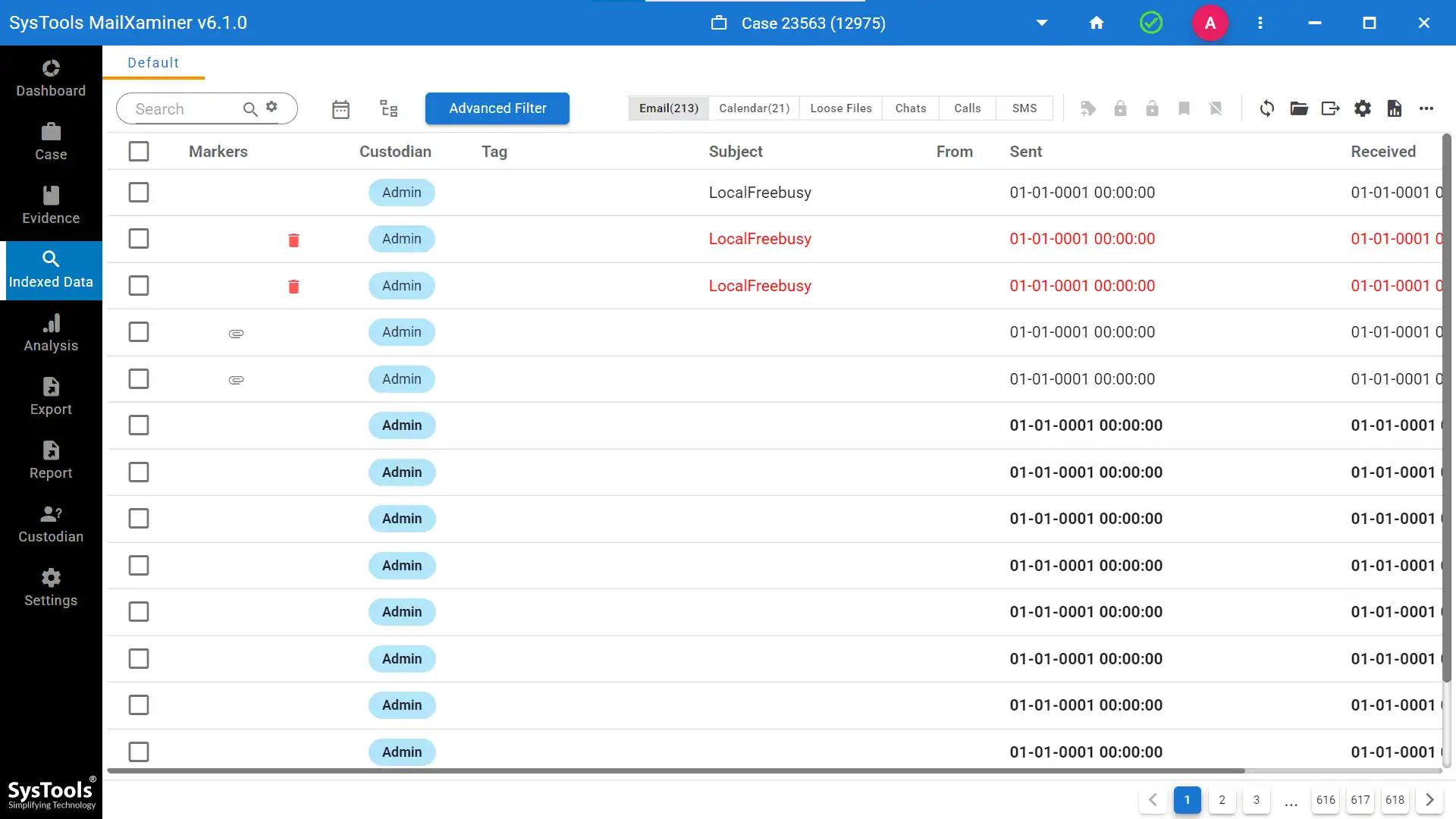
- Step 5- To obtain a preview of the emails in the evidence file, select the indexed data tab.
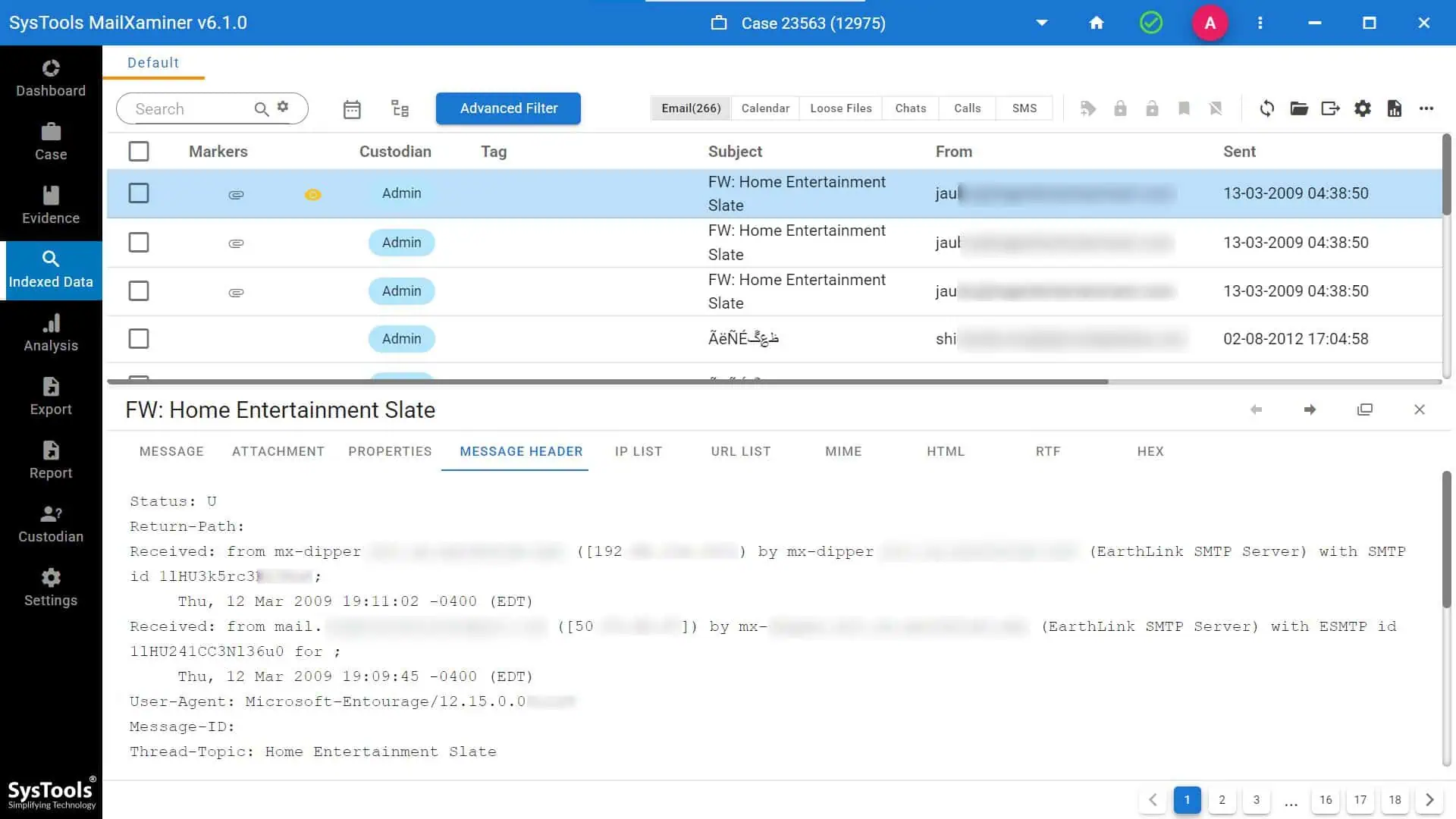
- Step 6- To examine an email, click on it. Examine emails using the header preview mode as shown.
- Step 7- The search results may also be exported by users.
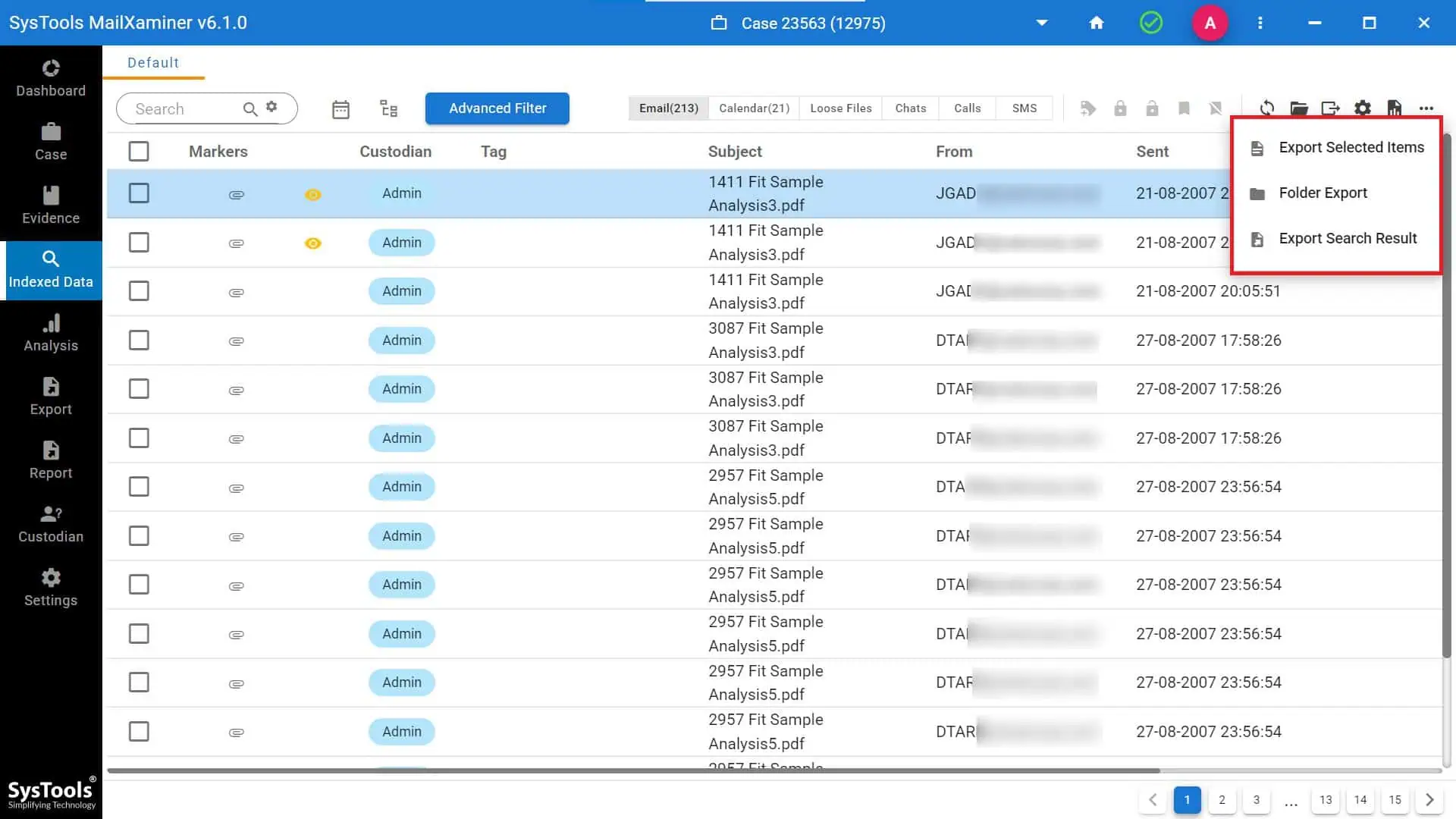
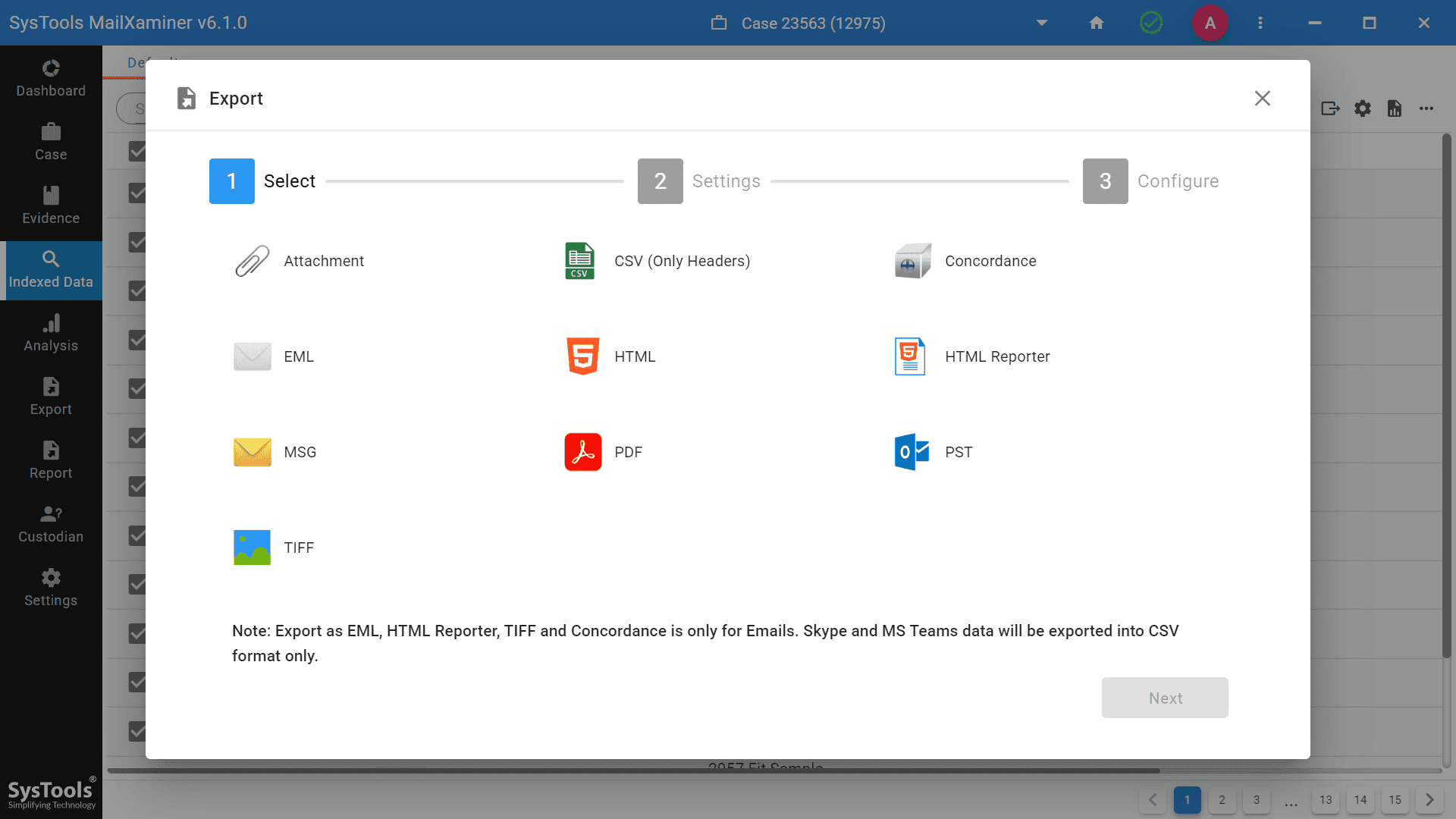
- Step 8- You can choose from different export choices to save the data in the format of your choice.
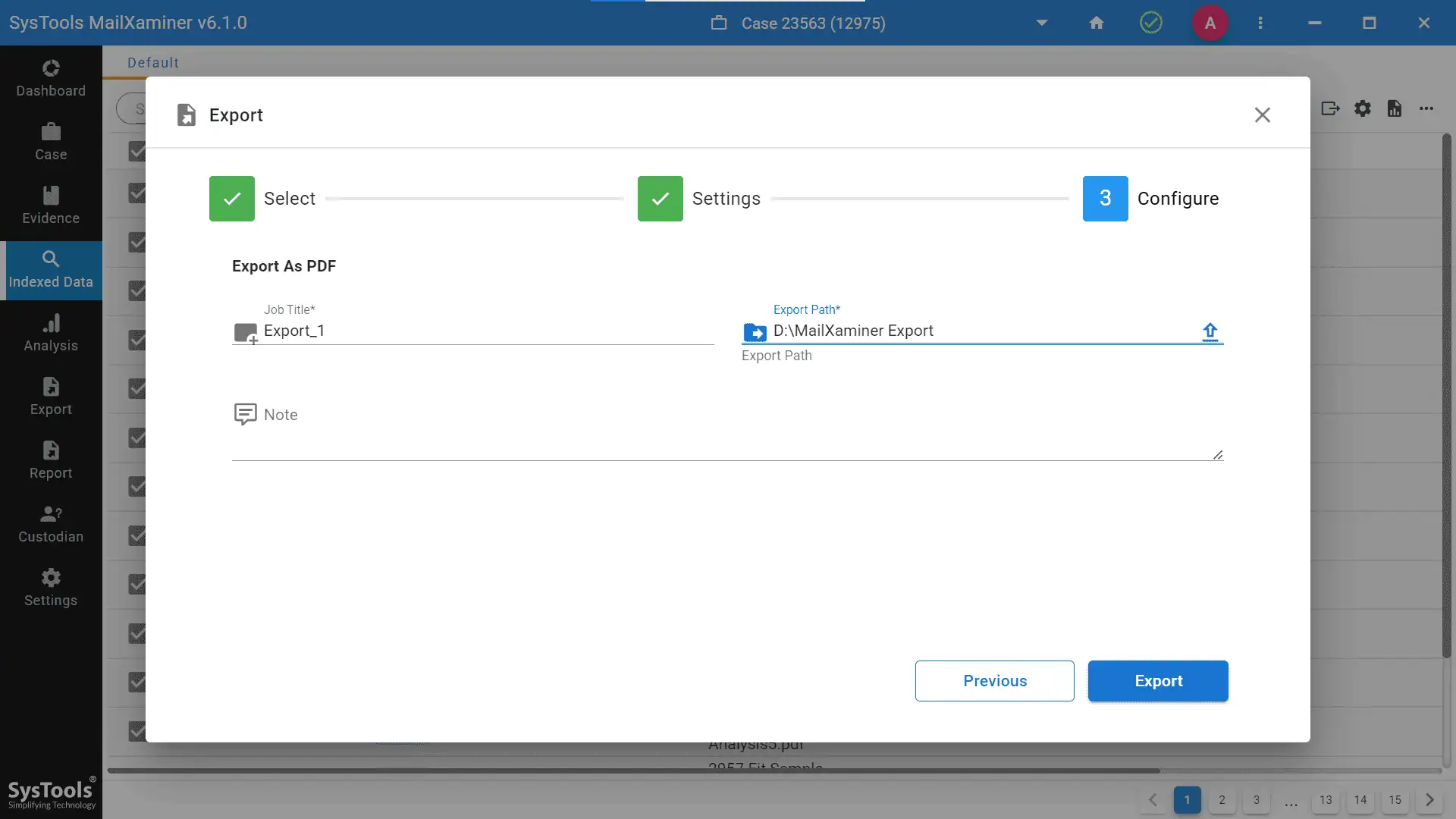
- Step 9- Select the Destination Path where you wish to store your data. One can also include an extra Note in the export procedure. Lastly, press the Export button.
What are the Striking Features offered that would help analyze Outlook Email Header?
- To see, analyze, and investigate the harmful communications between any number of suspects, use the sophisticated link analysis approach that is incorporated into the program. Examine the emails and information exchanged, and ascertain the suspects’ relationship as soon as possible. Use advanced Boolean operators to find connections between many individuals. Analyze and show their email conversation using the suspicious keywords.
- Following the Forensics Recovery & Analysis procedure, you may use several operators to look for evidence in the email and contacts body (To, Cc, Bcc, Subject, First Name, Last Name, Sender Name, etc.). One can also look for a digital footprint in attachments and eliminate duplicate emails that have been searched.
- Examine deleted, read, unread, or password-protected emails from a forensic standpoint to get all of the information contained in them. Investigate emails from several perspectives to identify any fabricated or corroborating evidence.
- You can find digital footprint in any disk image file by using the Enhanced Loose File Support option. To read files without any issues, experts must verify the Document or Loose file option.
Conclusion
Email headers are crucial for determining a message’s sender, receiver, and date, as well as other routing details. Moreover, they are essential for tracking an email’s path and detecting potential dangers.
The automated software explained above can help by providing advanced link analysis, high-tech operator search, suspected keywords in search, email, and check suspicious email attachment, and improved support for documents. With this program, you can easily analyze emails to see if someone deleted them, read them, left them unread, or locked them with a password. It also helps you find any fake or supporting evidence.

