Guidelines to Find Attachments in Outlook Email Chain Investigation
Digital investigation might be done to find attachments in Outlook email chain. However, conversations within email threads can be manipulated, so relying solely on manual findings is not enough. That is why, in this writeup, we have provided the best-in-class utility for email forensic analysis. However, before explaining the workings of the tool, there are a few pieces of information, like the reason for investigating email threads over regular mail.
Table of Contents
Why Find Attachments in Outlook Email Chain Instead of Normal Mail?
Stronger Evidence: As investigators might be aware, isolated emails are a weak form of evidence. Criminals can easily change its metadata, thereby confusing the investigators regarding the timeline of events. However, when a clear conversation between suspected entities is done over multiple email threads, it becomes quite hard to manipulate the evidence.
Chain of Custody: Any crime or conspiracy includes both victims and perpetrators. Establishing a clear distinction between the two is the responsibility of the prosecutor, in this case the investigation agent. That’s why, if one has access to email chain data, it becomes easier to provide a progression of communication.
Unearthing Criminal Network: With the help of email chains and the attachments found within them, detectives can track the collaborators easily. This is not possible with normal one-to-one emails.
Crime Pattern Recognition: Any crime, even if it is digital, has its own distinct fingerprint. This is true for the conversations found in email chains. As law enforcement agencies can audit them to get a better grasp of the situation.
There are many other minor instances where email chain analysis is preferred over the alternative. Let’s now look at what differences exist between the types of email chains themselves.
Kinds of Outlook Email Thread and Related Attachments
Email threads or chains have come in a variety of different forms. Each of these requires a different investigation strategy.
- The most basic form of email thread is a back-and-forth conversation between two individuals. Even here, it is quite difficult to pinpoint the exact origin of the conversation, as criminals can easily delete the mail. So investigators often have to search through the entire conversation multiple times. This is not practical, as these conversations can go back years.
- When more than two people (or email IDs) are involved, it becomes a group email chain. Tallying which mail was sent to whom and at what point in time is challenging. Moreover, investigators now need extra effort to find attachments in Outlook email chain belonging to multiple different personalities. Doing all of this manually is out of the question.
- Cybercriminals might hijack a regular email ID and conduct their nefarious activities from there. In such a scenario, detectives might find a spoke-like thread structure. Here, scam mail originates from a single source and quickly spreads to a large number of hosts by taking advantage of unsecured auto-forwarding policies.
This completes the discussion on the major kinds of email threads that can be encountered during cybercrime investigations. Now that we are aware of the complexities involved, let’s look at how choosing the right tool can ease up the task of finding attachments in the Outlook email chain.
Traditional Means to Find Attachments Inside Outlook Email Threads
Shuffling through the regular inbox to gather all attachments part of an email thread is too time-consuming. Instead what investigators/users can do is trigger the conversation view.
Throughout the lifecycle of Outlook, many GUI changes have brought in some variations in the steps to trigger the conversation view. Not to worry as we will provide you with the exact steps.
Outlook Email Thread Investigation in Classic Version
The following steps are for the 2013 edition but will work for other classic variants as well
- Open the Outlook Desktop portal
- Go to the View Tab on the Top Menu
- There mark the Checkbox that says Show as Conversations.
- A pop-up will appear on the screen asking you if you wish to apply this setting to the current folder or the entire mailbox.
- Choose the option that suits your scenario and proceed with attachment analysis.
Every email that has an attachment will possess a vertical paper clip icon. So use it to your advantage and speed up the investigation. Even if you dont have the classic version of Outlook you can still find attachments in Outlook email threads.
Analyse Attachments in OWA Email Chains
- Login to Outlook web.
- Go to View
- Click on Conversations
- Select Group into Conversations
- Look for the email messages with a slant paper clip icon.
- Open it, extract/download the attachments, or perform a preliminary examination with the attachment preview option.
See Attachments of Outlook Thread Using New Desktop Client
The new version of Outlook has a UI that is almost identical to the OWA so this means the steps to access the conversation view are the same.
Launch the new Outlook Desktop app and replicate the steps as outlined in the OWA section.
How a Professional Tool Helps in Attachment Analysis of Email Threads
MailXaminer is the first choice of law enforcement agencies for any email forensic requirement. With the user-friendly interface and inbuilt advanced filtering mechanisms, any investigator can pick out the relevant details regardless of the experience they have. The tool is purpose-built to limit the technical know-how involved, unlike traditional email forensics. It does so by laying out all the tools at the click of a button.
During specific digital investigations, like when detectives want to find attachments in the Outlook email chain, the tool easily outperforms the rest of the competition. Here is a reduced version of the long list of features present in the tool.
The tool highlights the deleted emails separately in the preview section. Using it, investigators can reconstruct the entire conversation that took place between the suspects. Moreover, it also restores the deleted attachments present in those emails, which can prove quite helpful in uncovering hidden details.
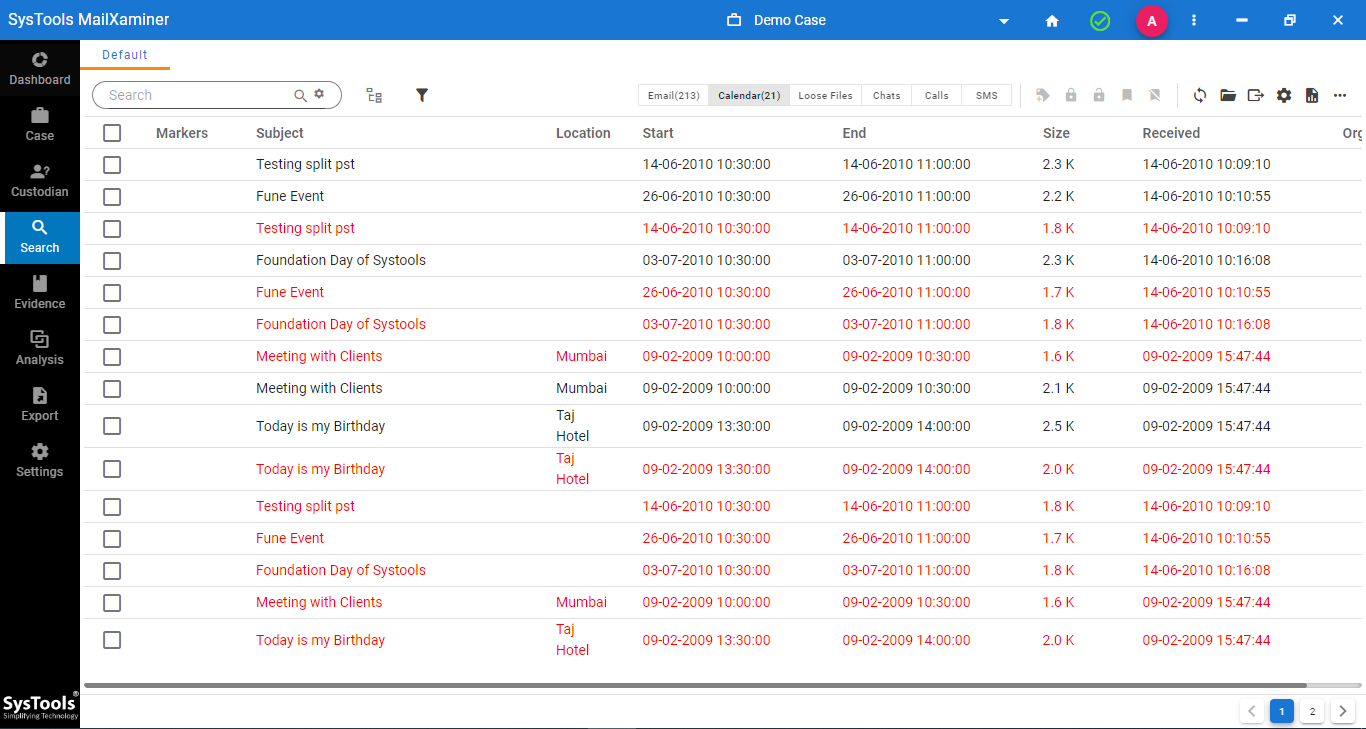
There are 8 different viewing options available within the tool to conduct email analysis. Each one has its own unique characteristics to give out all the information present in the source file. These are Message, Attachment, Properties, Message Header, MIME, HTML, RTF, and HEX.
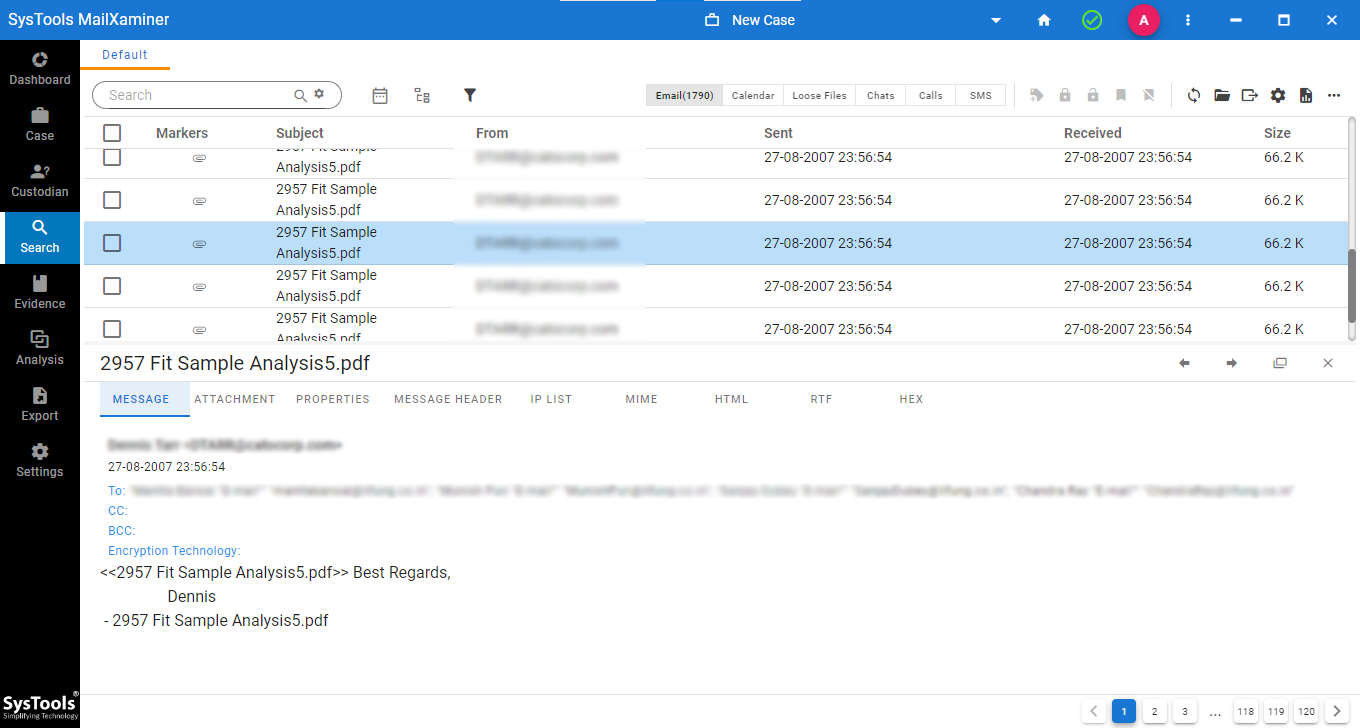
The tool has the option to automatically remove encryption and provide link analysis between the parties involved.
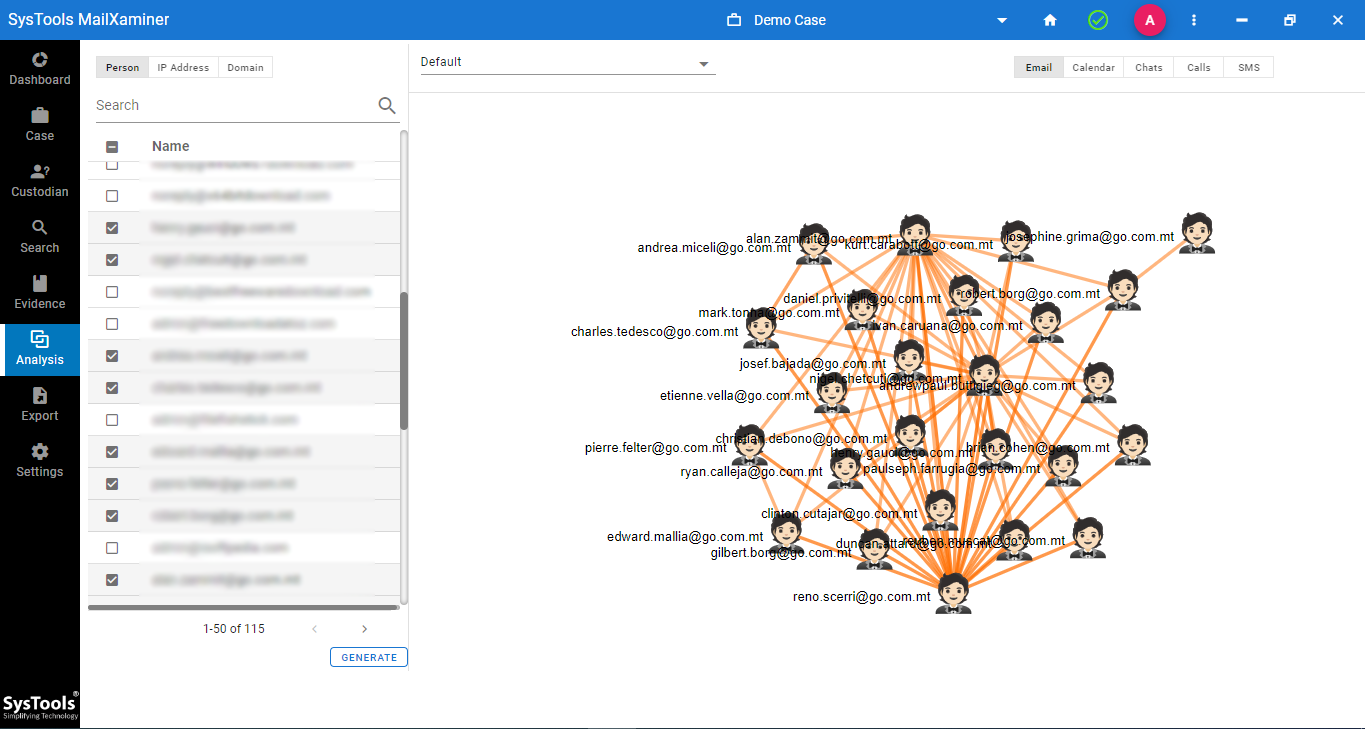
With the help of an OCR scanner, investigators can find text within the file while searching images in Outlook all within a single dashboard.
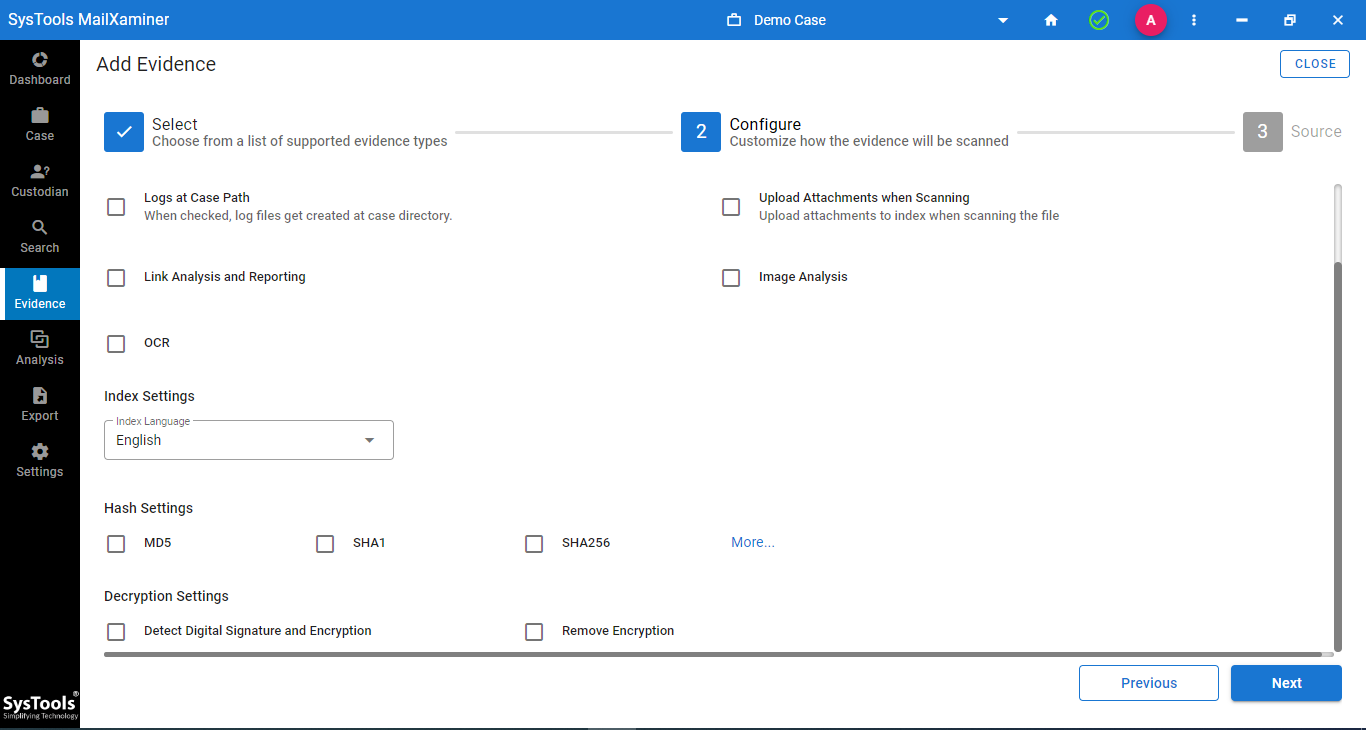
Detectives can export their search results in many different formats right from the tool and generate a complementary report as well.
Conclusion
Through this write-up, we established how important it is to find attachments in the Outlook email chain during email forensics. Here we found that manual searching and sorting methods often prove impractical. This is due to the inherent limitations in Outlook’s chain management.
Moreover, editing features present in the Outlook email service can be misused by nefarious entities to manipulate the information. Apart from the obvious, investigators may miss out on analyzing the tremendous amount of metadata present in those threads.
That’s why experts across the globe trust the leading tool in the field of email forensics for all digital investigations.
Frequently Asked Questions Regarding Attachment Extraction Inside Outlook Email Threads
What is the difference between a regular email and an email thread inside Outlook?
The only noticeable difference is that in email conversions there is back and forth exchange of messages that reference each other. On the other hand, regular emails have a single intent i.e. to inform the recipient. Both can contain attachments and involve more than two people.
How are email chains different from email threads?
These closely resemble each other so may cause confusion. It is better to understand it via examples. So, an email chain can be a marketing mail that encourages users to forward the mail to get discount coupons, cashback, etc is an email chain.
Whereas, email threads most commonly occur when for example a person is communicating to the support staff regarding a product or service.
What kind of attachments are present in an Outlook email thread?
The email thread is just a regular email with a specific structure so all attachment rules/ boundaries apply here as well. Most common email attachments would be images, documents, spreadsheets, audio, video, and other media.

