Spam Email Analysis – Understand the Entire Procedure
Spam Email Analysis - Spamming is the practice of using electronic messaging systems like emails, cellular text messages etc to send bulk messages in unsystematic ways. Spam emails are also known as Unsolicited Bulk Email (UBE).
Nowadays spamming is a common process used for commercial purpose and which are economically valuable. Most of the spam messages are commercial advertisements but some of them contains virus and scams which are seriously affect the security of data.
Spam email header & content analysis help to detect malware in email and prevent email spam attack. In the current era the enhancement of the technology also leads to the rapid growth of email spamming.
Spamming is commonly used for email fraud. That are most commonly used for extract personal and confidential information of the victim. Email spam comes in various forms such as educational and training, Personal finance, IT etc.
Nowadays most of the email clients and servers provides the mechanism to avoid the spamming by filtering email from Server side and store the filtered emails in Junk folder or Spam folder. To check out all the emails email servers first find out that email is properly designed or not if it is not then, emails are deleted by users or move to Spam folders. This process can easily executed by external software designed for email investigation. MailXaminer is one of the powerful spam email analysis tool which help the investigators to analyse and detect the spam emails. Procedure for analyzing data of emails is really easy with this brilliant application.
What are the Spamming Techniques Used?
- Using Botnets: Botnets are the collection of internet connected devices which are infected and controlled by malware. If a device is infected by a malware then it will be a part that network. It will be controlled by attackers.
- Blank email: In this method the attacker sends blank emails with empty message body and subject line. This method of email spam attack is mainly used to directly attack the server or distributing worms or virus.
- Image spam: This is the technique mainly used for escaping from the text based spam filtering. In which the textual data will be stored within the image using computerized methods.
- Snowshoe spam: It is the email spamming technique used to distribute spam widely using a wide range of email address and IP.
Why Email Spam Analysis Needed?
Like cross examination of your files stored into computer via anti-virus system, you should take care while you are sending or receiving emails and you should follow proper email examination to find whether email is spam or not. Cybercrime email examiner with few steps to analyze the database stored into emails makes you confident that emails are with likeliness. So, you are free to examine emails for its likeliness via our spam email analysis tool. If you are thinking for the same then, do not need to roam the query like how to analyze spam emails in your mind.
Common Methods to Identify Spam Emails
Nowadays altering of email header to make message appear like it comes from someone else other than the actual source. During the email spam analysis, one of the common method used by forensic investigators is spam email header or message structure analysis. We can see some of the common methods used to identify spam emails.
1) Unknown or spoofed email address: Spoofing is the common method used by the attackers to hide their identity and pretend as another person during email spam attack. Spoofing can be done in many ways the common methods are:
- Changing the name of the sender. This will help to not match the sender name with the email address. So if the receiver only care about the namer the attacker can succeed easily.
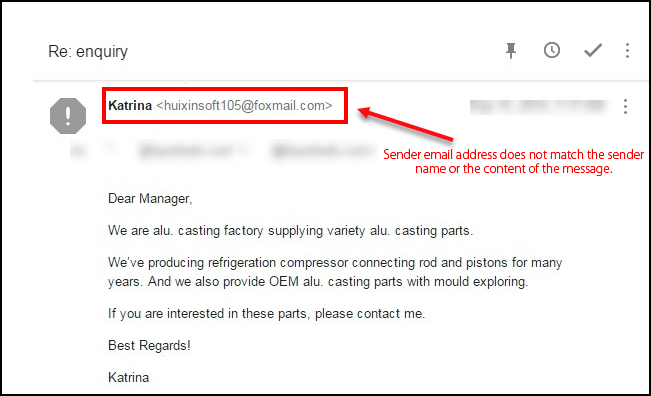
- Using characters similar to the actual letters. This is an another method is used to perform email spamming by making sender email address look like an email from a valuable source. Most commonly this method is use when there is an actual address exist with the same address.
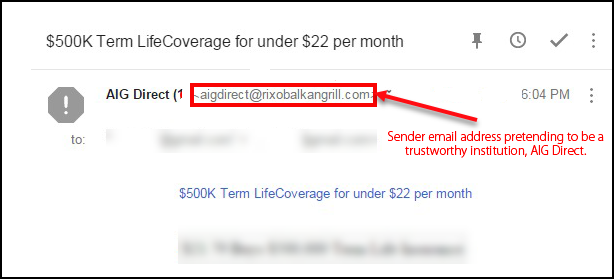
2) Asking for Personal Information: Spam email attack likes Phishing scams are comes as legitimate business. They will request for your personal informations in the name of Bank or Government agencies and provide informations to make you believe that they are actually belongs to government.
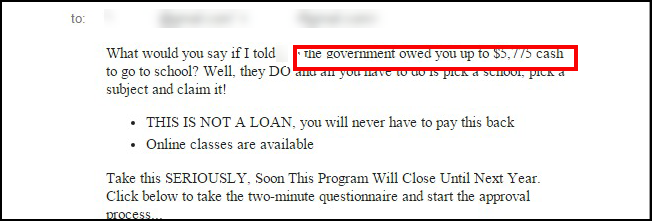
3) Strange attachments and Links: The common method used by attackers are providing links to the malicious site or make you to download malicious attachments. It is better to don’t open any links or attachments unless you trust the source.
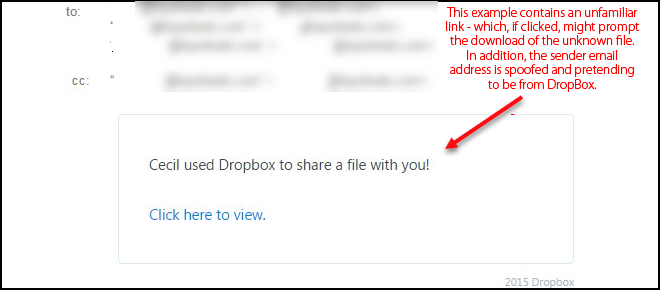
Most of the spamming emails follow similar structure to create their email message. Phishing is a common email spam attack that we can see around. For understanding the spam email content analysis more clearly we can examine the structure of email by taking phishing email as an example.
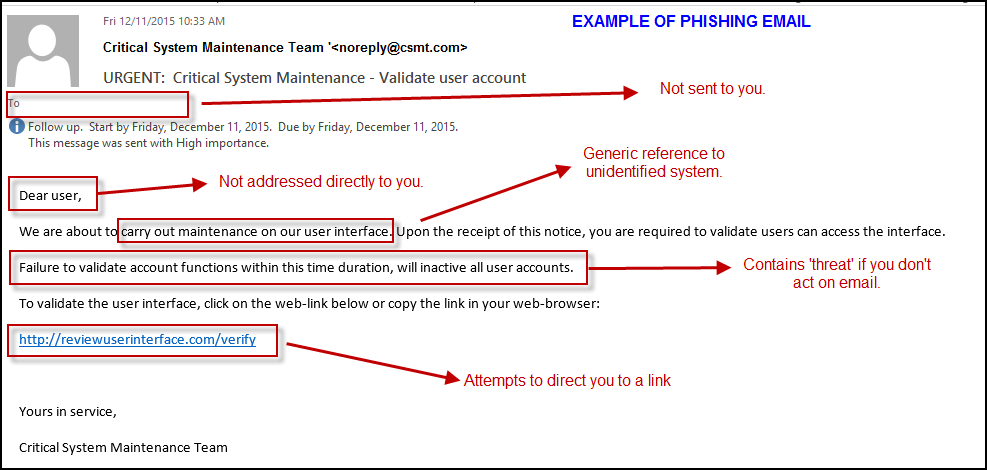
When you check the To address from spam email header section you can understand that it is not send to you or the To section doesn’t contains your email address. After that if you move to the addressing section you can find it is not addressed you by you name. Instead the spamming mails will use Dear user, Respected Sir or something similar to that. This is method is mainly used to target a set of people instead a particular person. The generic reference to undefined system – spam emails use the common terms to reference the system instead of specific site or service because they are not aware of which sites or services are you are using. One of the main trick using in email spamming by the attacker is message indicating threat or danger this will make the user to take action according to the message. Anther method used by attacker is direct you to a link. Most probably that link contains any type of malware or any other mechanism to find PII data in emails.
Examine Email Attack by Spam Email Analysis Tool
With our email examination tool you can properly examine emails via different views. After finishing emails' search complete scanning for emails gets wind up and then, you are free to have a view of particular email. MIME view, HTML view, HEX view, normal view, attachment view, property view etc. you can go for well-suited option. Spam email analysis is really helpful while you are in need to find out the specific email is spam or not.This forensic investigation software can be used before being purchased with the help of its trial version for analyzing email messages. The trial edition is available for free and allows users to make sure that the software works fine and is what they had been looking for. You can only use it for spam email content analysis but can’t export the data into other file formats as part of the demonstration limitation.
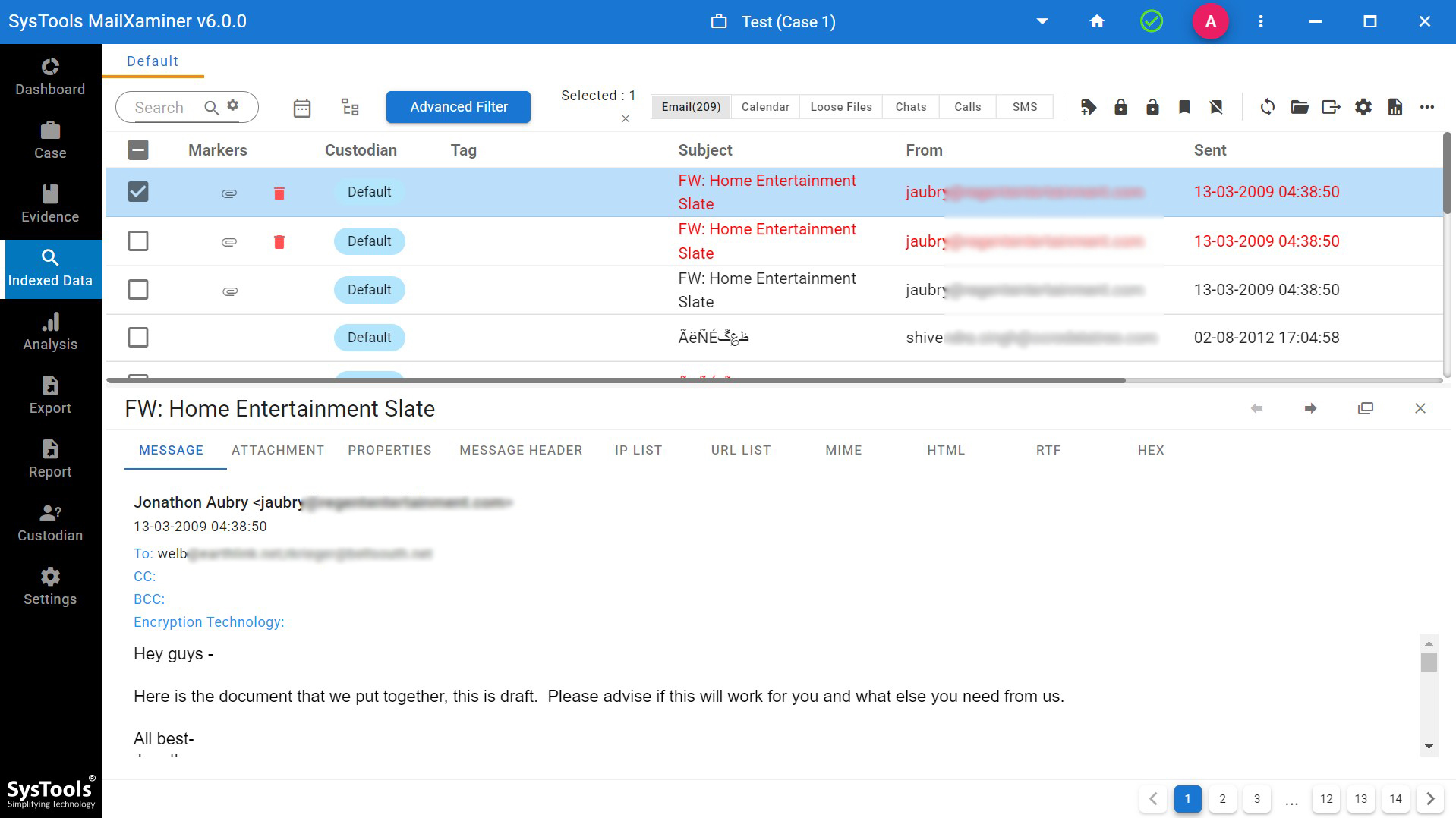
Message: Mail view of spam email analysis tool allow the examiner/ investigator to examine email message body in user perspective. Which helps to find the hidden messages they try to convey through the email messages. It will also help the investigators to identify whether the message is trying to spam using the structure of the content.
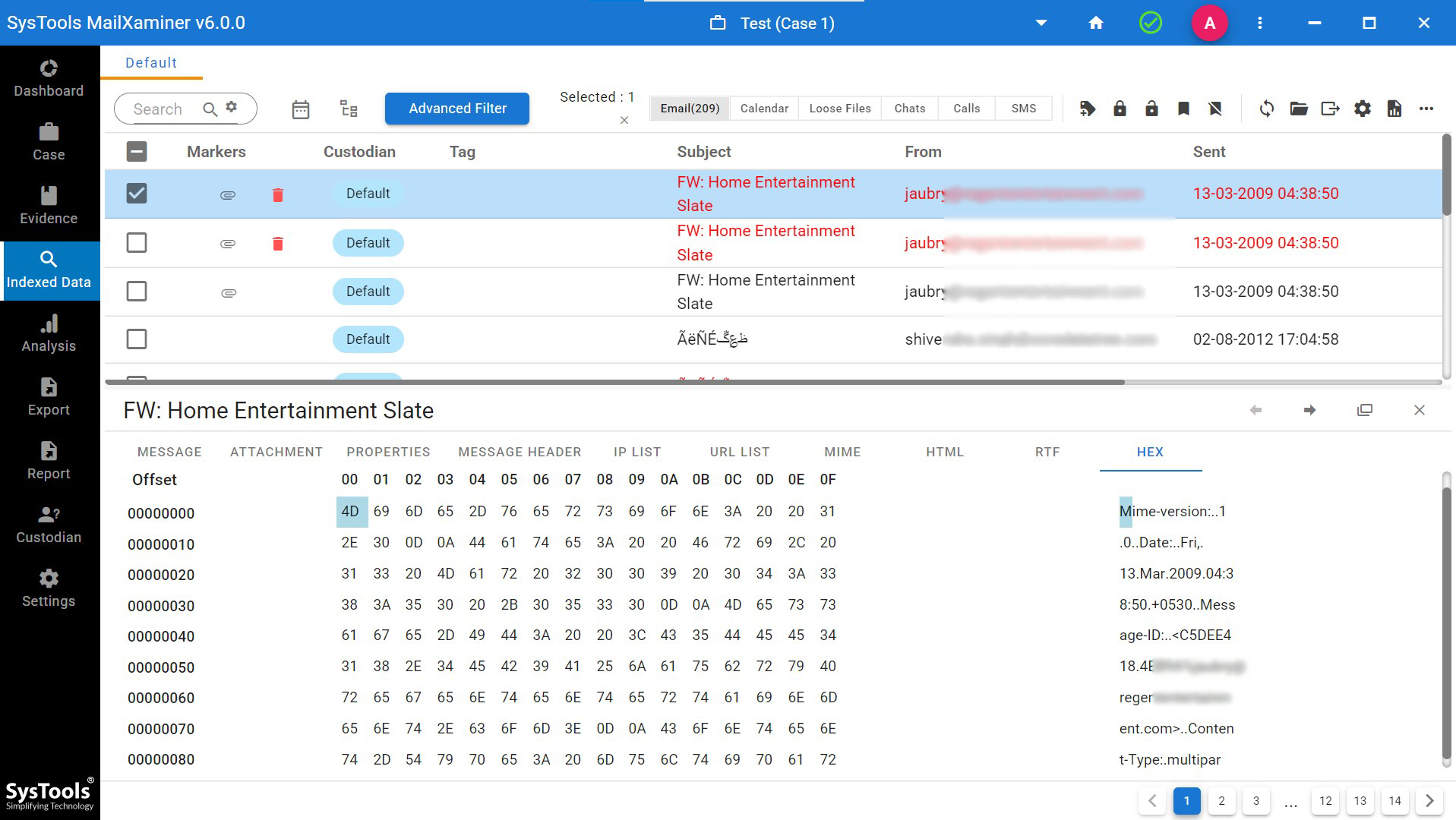
Hex: Hex view of the tool allow to spam email content analysis through the hexadecimal values This is the common view used by the digital forensic investigators to find whether the criminal try to remove the originality of email message by alter the content or by modifying the structure.
Property View: This view help the investigator to briefly examine the entire properties related to the email data. Which gives the informations such as “Body Details, Dates, Message Flags, Recipients, Represent Sender, Sender Details, Subject, Addition Info”. This informations help the investigator to summarise the email related information before the deep analysis begins.
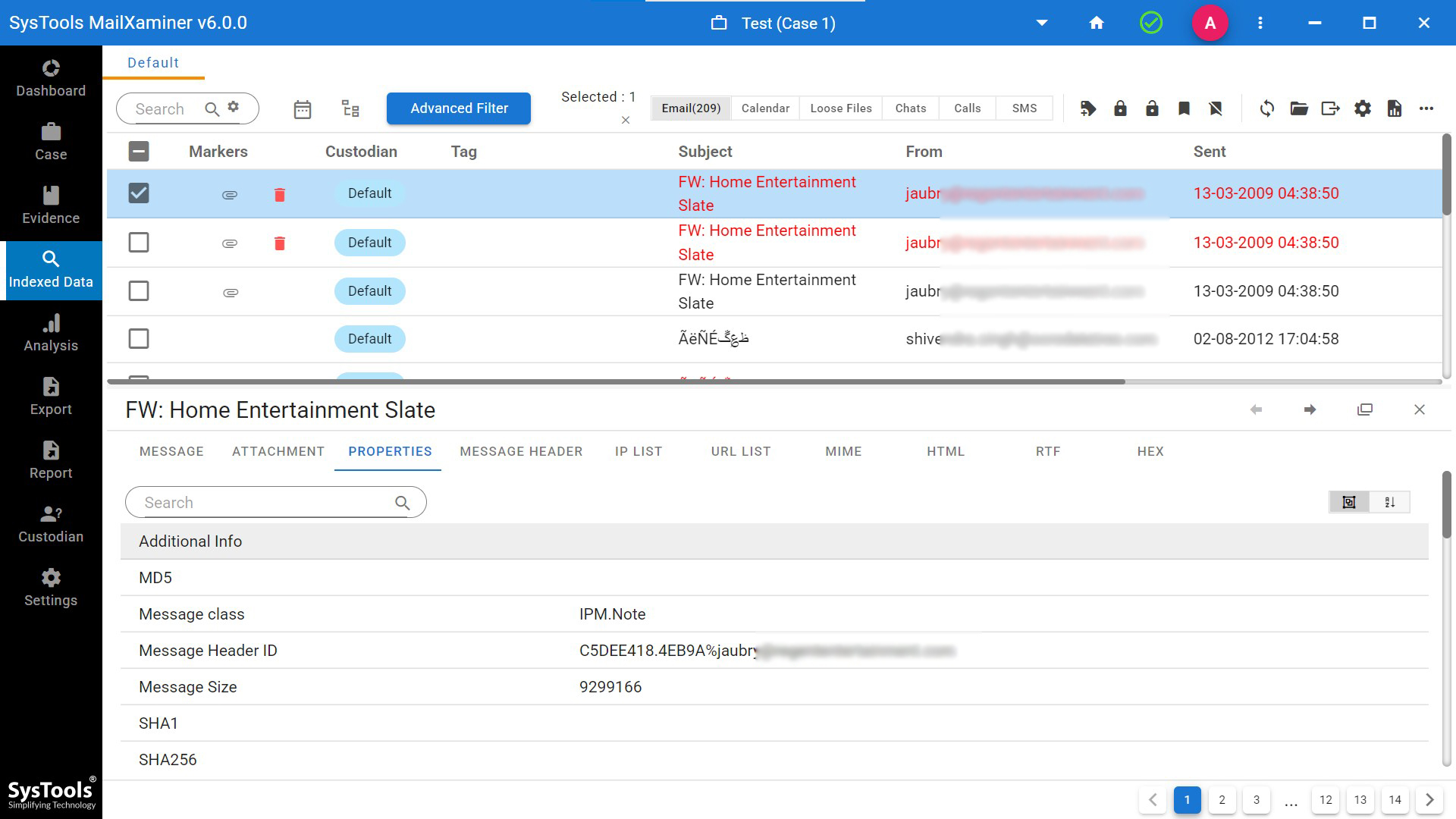
Message Header: During the email investigation investigators give more priority to spam email header than the message body. The header view of the spam email analysis tool help to identify particular routing information which includes Sender- Receiver address, Date, subject, Device information, MIME version etc. Detailed analysis of header information helps to extract crucial information related to the crime and help to track the attacker.
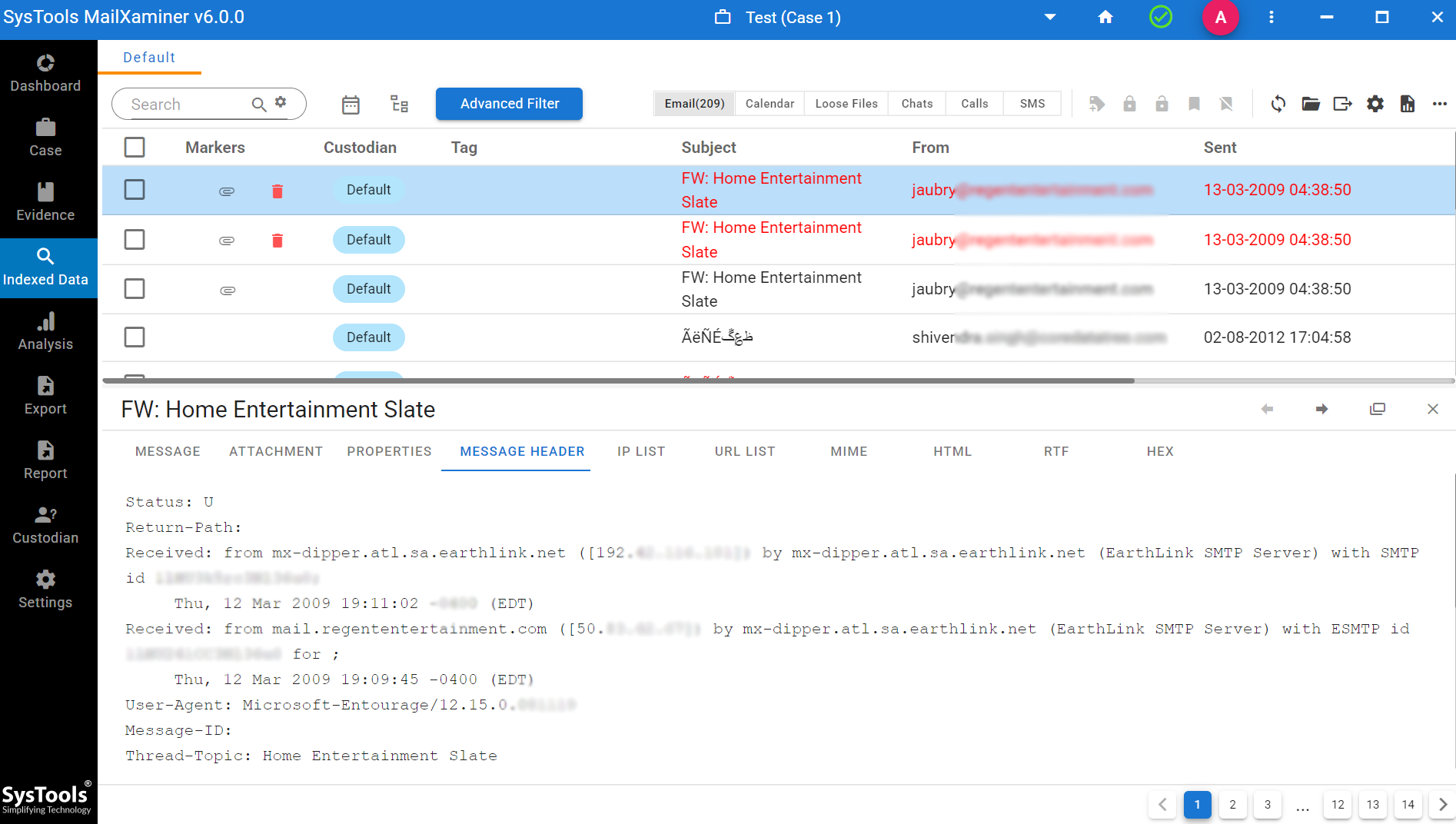
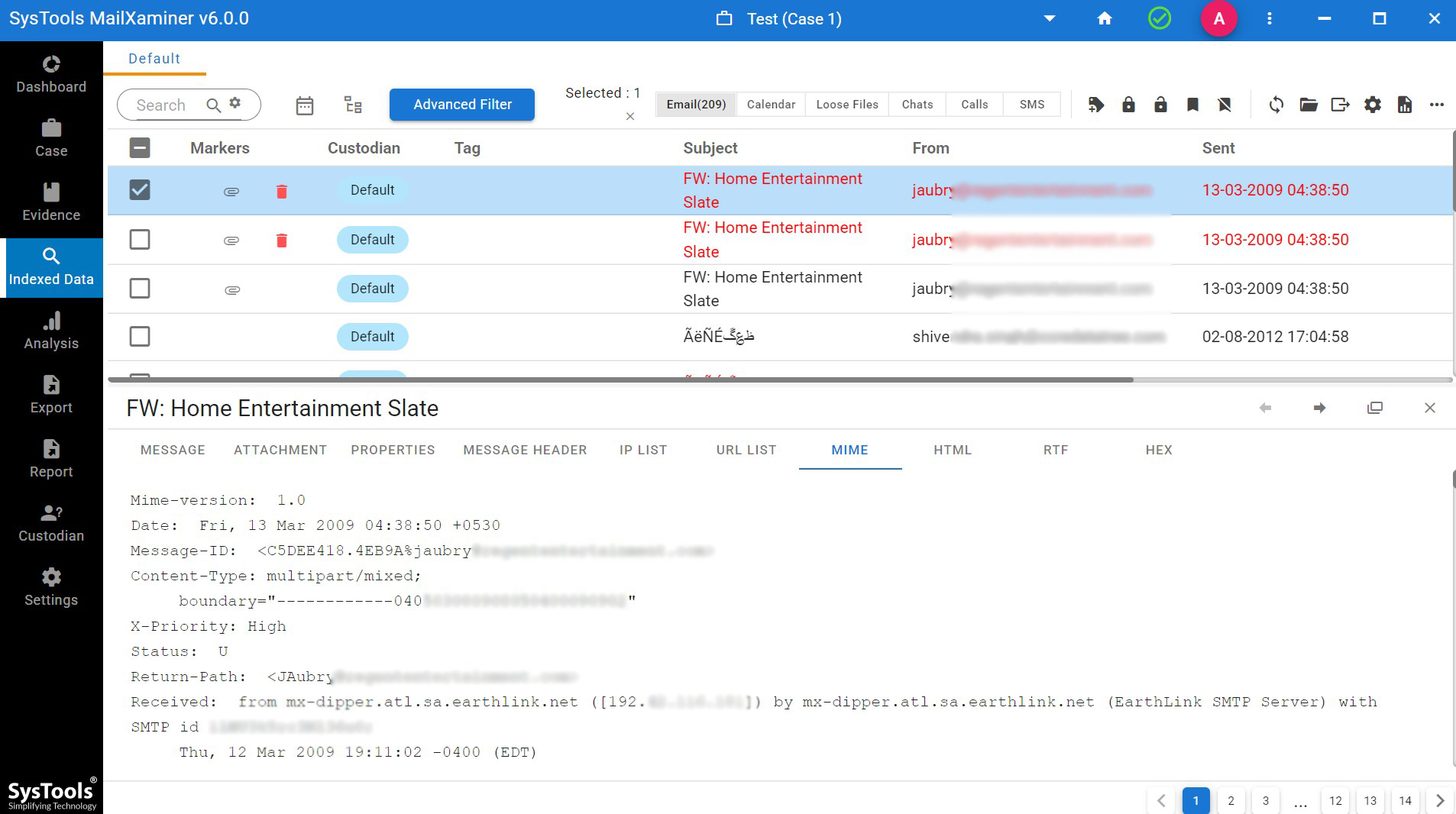
MIME: MIME view of spam email analyzer provides the MIME related informations such as “MIME Version, Message ID, Content Type, Content Transfer Encoding etc.” Which help to understand whether the email contain any multimedia content or attachment, What type of content it have etc.
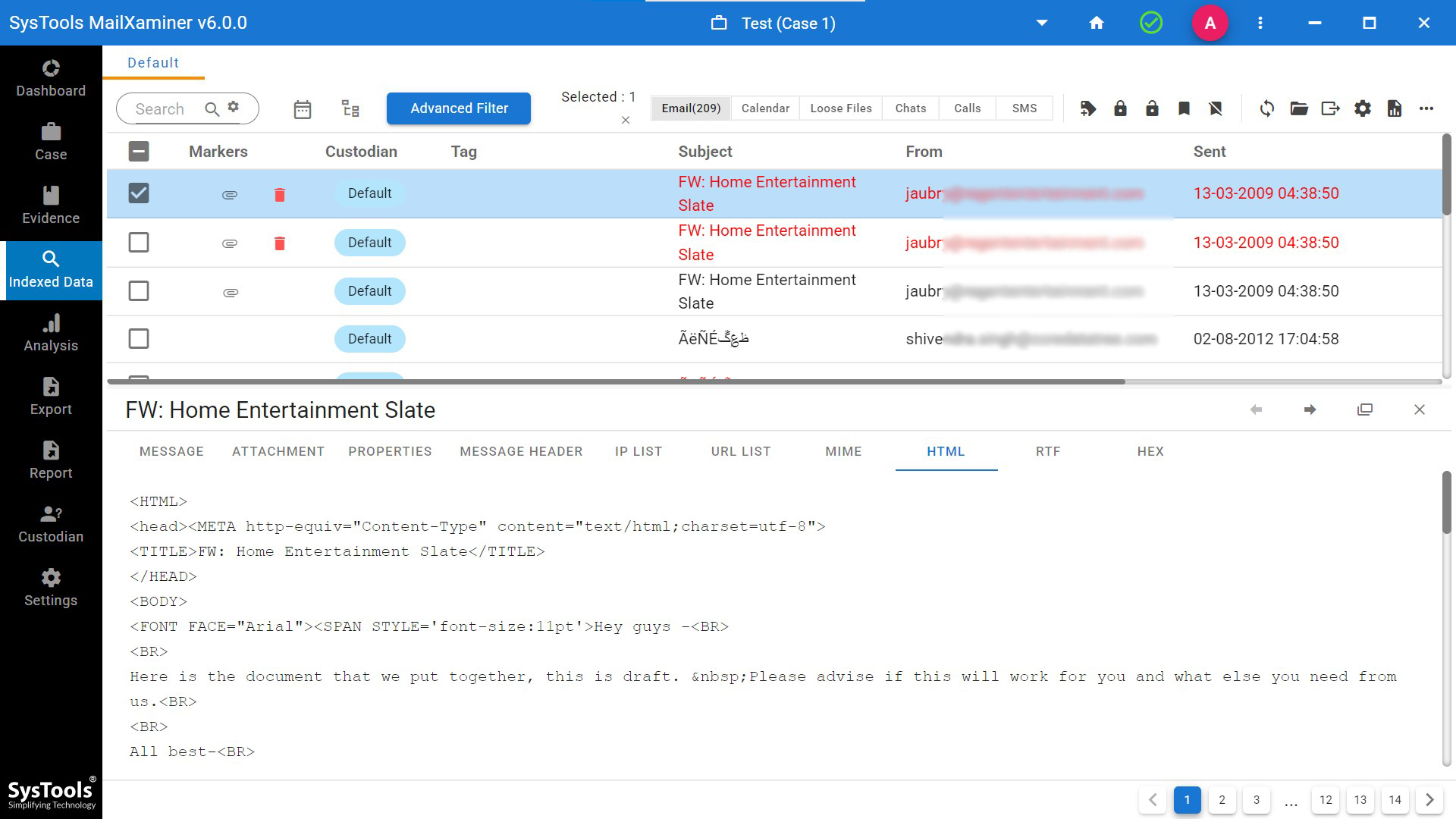
HTML: This view provide the HTML code representation of the email data. Which allows the examiners to analyse the email data through its code structure that helps to easily identify the alteration or modification done on the email data to remove its originality.
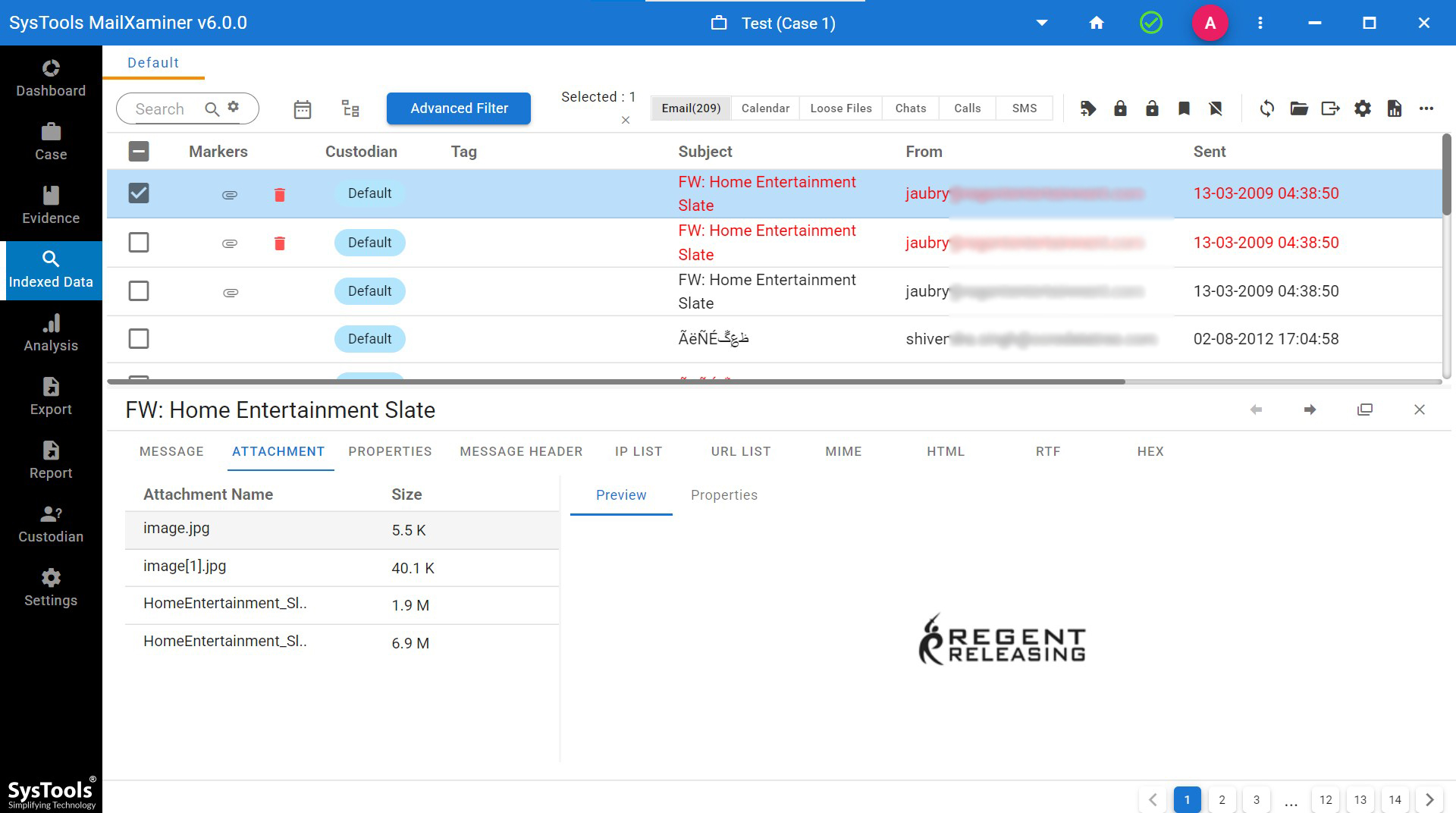
Attachments view: This view help the investigator to examine the attachments within the particular email. It allows to view the entire list of email attachments and preview it directly to perform spam email analysis on it.
Conlcusion
Investigation of emails is one of the toughest task. It is becoming more challenging today. So, if you want to analyze your data comfortably with more advanced features. You should surely give a try to t with email examination procedure then, try the product as a freeware before purchase, then, go on for purchase for uninterrupted spam email analysis.