What is Digital Forensics and How is it Used in Investigations?

Digital forensics comprises of techniques that deal with the investigation and search of digital evidence. It is a branch of forensic science involving the process of identification, collection, preservation, examination, and presenting digital data or evidence. Digital forensics aims to reconstruct the sequence of events that took place at the crime scene. Also, digital data and media can be recovered from digital devices like mobile phones, laptops, hard disks, pen drives, floppy disks, and many more.
Digital forensics is the process of investigating digital data collected from multiple digital sources. During the investigation process, a step-by-step procedure is followed in which the collected data is preserved and analyzed by a cybercrime investigator. Further to this, it can be used as a potential source of evidence in a court of law. As cybercrime investigators are digital forensics experts so, they carry out the investigation process and perform analysis of digital data. Moreover, they ensure the authenticity of evidence is maintained. In this blog, we will focus on the different approaches to investigating the gathered digital evidence during the process of digital forensics.
Different Types of Digital Forensic Investigations
Before knowing the procedural steps of digital forensics, let’s go through the different investigation types of digital forensic investigation, as mentioned below.
There are mainly two types of investigations:
1. Public Investigation: It includes investigations that are conducted against the suspected people to detect the crime scene. Generally, government agencies handle such types of investigations that relate to the public sector. Moreover, public investigations are generally investigated under the process of criminal investigations as they are primarily dealt with like criminal cases.
2. Private Investigation: These investigations are carried out for crimes related to businesses, offices, and organizations. Any kind of violation of the terms and policies of private sectors will fall under this category of investigation. Private investigations are generally referred as corporate investigations.
How Forensics is Used in Investigation: Step-Wise Procedure
The investigation process in digital forensics is a step by step procedure carried out meticulously. It ensures that no original evidence is destroyed in the process while maintaining the chain of custody. There are sequential steps for the digital forensics investigation procedure that is as follows:
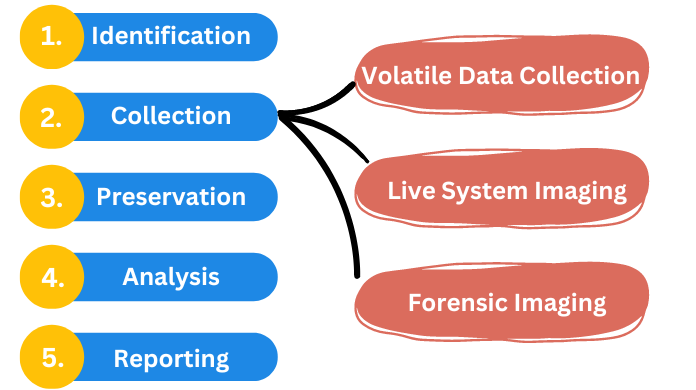
1. Identification: Identification is the foremost step carried out during any kind of investigation process. It involves the identification of all potential digital sources which are capable to store digital information including media. Further, it can be used as a source of evidence. Primarily, it is mandatory to be aware of the devices which can be useful in the investigation procedure.
2. Collection: All the digital devices, which are potential sources of evidence are removed and properly collected from the crime scene. Collection of all the digital devices, in its true form, is ensured to maintain authenticity.
The data collection can be further divided into four main types:
- (i) Volatile Data Collection: It includes the collection of all the executing data like user-logged in details, date, time, and other RAM data. The system should remain turned ON during the investigation process.
- (ii) Live System Imaging: It includes the imaging action performed on data during the examination. During the investigation process, the system should remain turned ON.
- (iii) Forensic Imaging: Duplicate copy of the original device is created to perform imaging actions. Exact copy of original device is created to perform manipulations. Hashing techniques are employed to ensure the privacy factor. The system should remain OFF during the investigation process.
- (iv) Seize Digital Devices Physically: When the above three methods fail, then this method comes to rescue. Here, the digital devices are seized and then all the possible digital evidences are collected. The system may remain turned ON or OFF depending on the suitable circumstances.
3. Preservation: Preservation is an important step as it is necessary to preserve the place where the crime occurred. It is also important to preserve all the Electronically Stored Information (ESI) which could be obtained from the crime scene.
4. Analysis: Analysis involves in-depth examination of all the digital evidences. Proper imaging is performed to ensure that the original evidences do not lose the authenticity. The examination and study of the criminal scenario helps the investigator to come to a conclusion.
5. Reporting: This is the final step carried out during the investigation process. Reports are way of presenting all the facts and events linked with the crime in a systematic manner. These reports are then presented in the court of law as the source of evidence to solve the crime.
A Perfect Tool to Analyze Emails with Speed & Accuracy
MailXaminer Email Examination Software is an efficient digital forensics tool. It helps in analyzing emails providing precise results. Using this, investigators carry out digital forensic processes. In fact, it further guides them on how to use this tool efficiently. For your information, this software supports 20+file formats, as well as supports a wide variety of web-based applications. Certainly, one can rely on this impeccable tool for investigations related to digital forensics.
Conclusion
In criminal cases, the systematic approach to carry out the digital forensic investigation process confirms the authenticity of the evidence. In this blog, we have focused on the basic concept of, ‘What is Digital Forensics, and “How it is Used in the Investigation Processes”.
A detailed investigation of digital devices is elaborated along with a forensic software which helps cyber crime Investigator to come to a conclusion in order to solve the case diligently.

