Skype Forensic Analysis for In-depth Investigation
Skype is one of the secured application used by millions of users that helps to communicate instantly with the end-users. It is incorporated with numerous services such as instant messaging, voice & video calls, screen sharing between users, and much more. With the increased usage of Skype by the users, cybercrime through this digital platform has been tremendously increased. Hence, there arises a need for Skype forensic analysis to perform an in-depth investigation of the Skype database. This blog will focus on the smart approach to carry out forensic analysis of Skype database in detail.
Skype is a well-known VoIP application which uses the peer to peer architecture instead of a conventional client-server model for instant communication. VoIP (Voice over Internet Protocol) acts as an alternative for telephonic communication. It replaces the traditional cable and phone number by providing communication through internet protocols. In order to manage and secure the connection between the users, Skype uses stronger encoding methods like TLS (Transport Layer Security) & SRTP (Secure Real-time Transport Protocol) protocols. However, the decryption and extraction of the digital evidence/artifacts from this secure encoding are one of the main challenge faced by the forensic investigators during the Skype digital forensics.
Location of Skype Log File
Before going through the Skype forensic analysis process, it is important to know the default location of Skype log files, which will help to extract the evidential Skype data.
Following are the location of log files which is different based on the operating system.
- Linux: ~/.Skype/SKYPE-USER/
- Mac: ~/Library/Application Support/Skype/
- Windows XP & Previous Versions: C:\Documents and Settings\ [Profile Name]\Application Data\Skype\SKYPE-USERNAME\
- Windows Vista & Later Versions: C:\Users\WINDOWS-USERNAME\AppData\Roaming\Skype\SKYPE-USERNAME\
What are the Various Files Generated by Skype in the System?
While performing the Skype forensic analysis, it is one of the most important factors to know the different files associated with the Skype application. Moreover, these files will help to navigate potential artifacts that may relate to cybercrime.
- Skype Main.db: It is the Skype database file that contains information such as call details, messages, chats, lists of contacts, time intervals, visited websites, etc.
- Shared XML File: It is an XML file that helps the investigators to check the timestamps of user activities. It consists of encoded data such as the account’s username, last IP used, etc.
- Skype Config XML File: This is another XML file created on both Windows and Linux operating systems. It stores the configuration information and the timestamp field of the file that shows when the user last used Skype to communicate.
- Chatsync Folder: It contains the chat history of the user in the DAT file format. It has many files of Skype user chat and it also contains the end time of the last chat between the two users.
When it comes to performing the Skype forensics analysis manually, investigating officers may have to face a couple of challenges for the same. This includes consuming a lot of time, fails to extract all possible suspected evidence from the database. All these concerning factors have led the forensic experts to avail some versatile Skype forensics tool that is described in the upcoming section.
Perform Skype Forensics with Advanced Computer Forensics Tool
Considering the various downsides associated with the manual method, the best alternative is to make the best use of third-party software. For that, is an apt MaiXaminer Email Examiner Software that enables the investigating officers to initiate Skype forensic analysis in an efficient manner.
Below mentioned is the steps to be followed to perform the Skype database forensics using the all-rounder Skype forensics tool.
Step 1
Open the software and click on the Add New Evidence button in the Evidence tab to add the Skype database file into the software. From the Add File wizard, select the Skype option from the Messenger tab. The software will allow you to browse the Skype database file from the local system.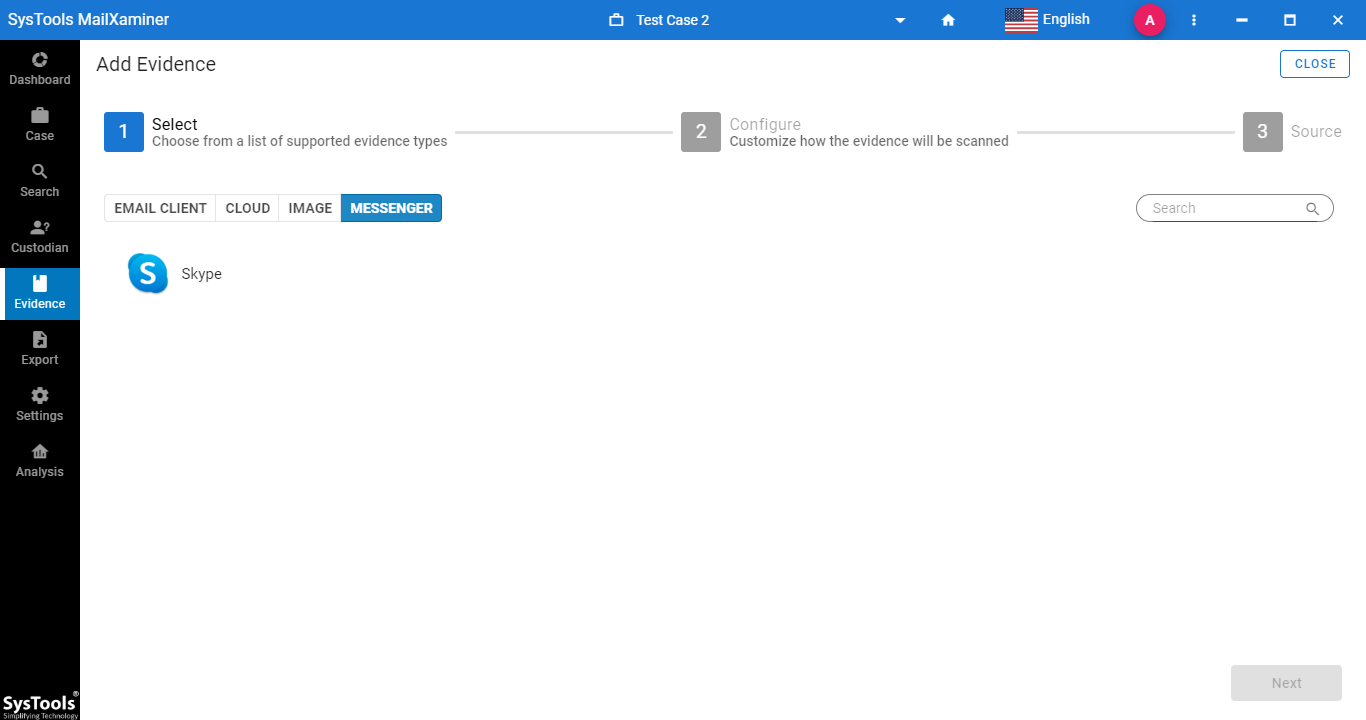
Step 2
To examine the Skype chat while performing the Skype forensic analysis, expand the main.db file from the Saerch section and select Chats option. It will provide information related to the chat between users. The investigating officer can fetch the evidence from different attributes such as “Sender, Receiver, Message, Start Time and Chat Message Type”
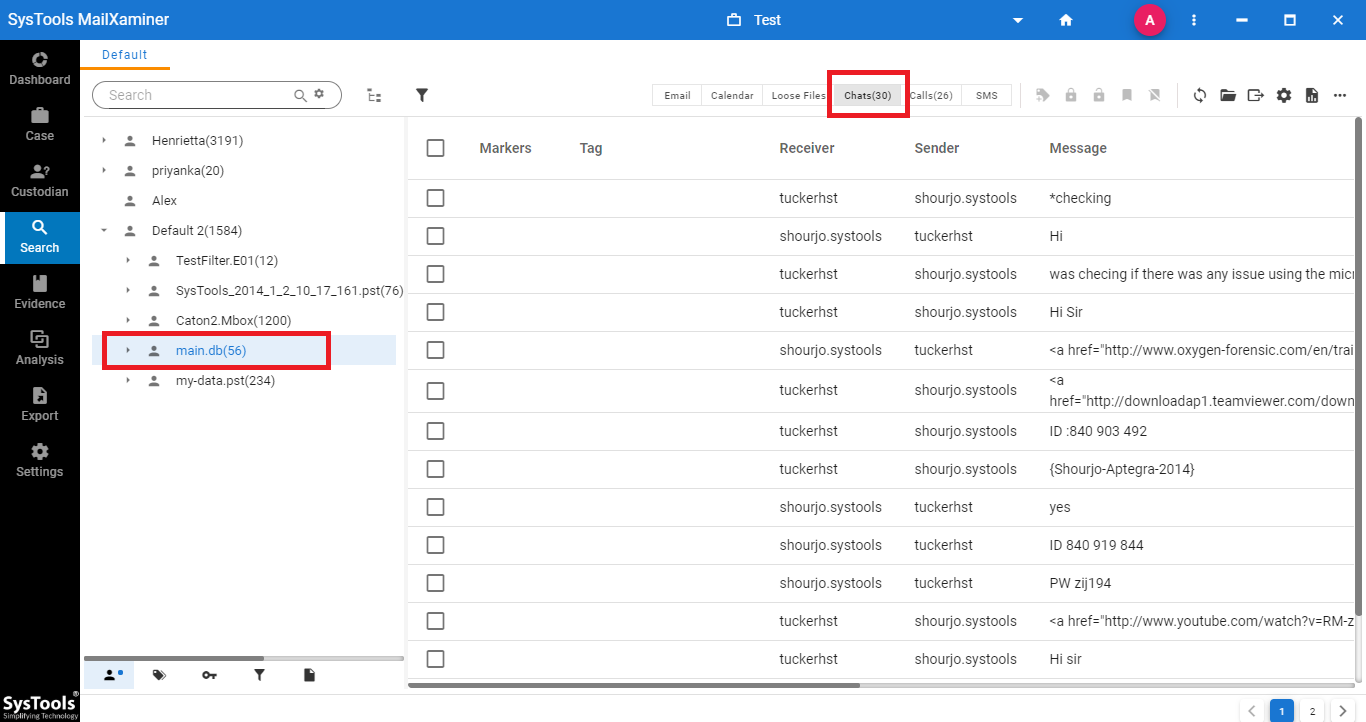
Step 3
During the analysis of the Skype database file, to find and access any call details, navigate to the Calls section from the software panel. This includes various information such as “Initiator, Participants, Start Time and Duration”.
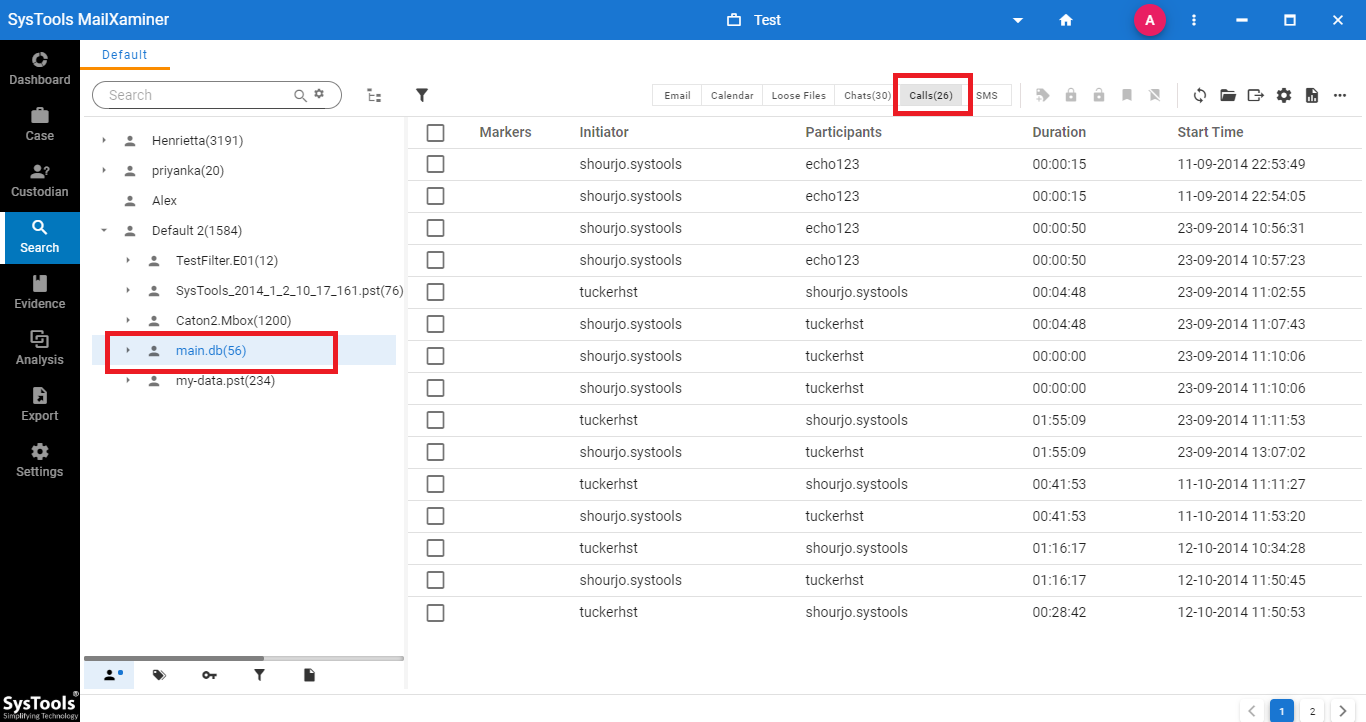
Step 4
To analyze the communication that took place through the Skype SMS, go to the SMS section of the software. It will provide different information such as “Sender, Receiver, Message, and Price”.
Closing Remarks
Skype forensics is an emerging field of forensic investigation which mainly focuses on the criminal activities that have taken place through Skype communication. The Skype forensic analysis help the investigating officers to examine the Skype communication and extract the forensic artifacts from the Skype database. With the help of the Skype forensics tool, it becomes easy to efficiently perform the analysis of the Skype data which includes various communication details.

