OLK File Forensics – Examine OLK14 File and Export Evidence
Do you want to perform OLK file forensics to carve out evidence? Then, read this blog and explore the best approaches to investigating OLK files without any hassle.
OLK files generally belong to Microsoft Outlook for Mac. It is a proprietary file type used by Outlook as a database for storing message information. Typically, the header information of an email is stored in OLK files. Since the data files are stored in the OLK folder, they can be solid evidence for investigation purposes. Therefore, these files are generally used by forensic experts for analysis purposes to carve those artifacts so as to smarty investigate the occurred cybercrime.
Overview – OLK File Format
OLK file format was developed by Microsoft, also known as Outlook Address Book File. OLK14 are the email message files that are created by Outlook 2011 Mac client to store email data. OLK14MESSAGE files manage all the important information regarding the headers of emails collected in Outlook Mac 2011. OLK14MESSAGE file does not have the body of emails, instead, it only contains the header of emails. The body of an email is been stored in another OLK file format, i.e. OLK14MSGSOURCE. Along with this, OLK files store organizational data, addresses, contact information, phone numbers, etc.
But, the thing is that sometimes it becomes impossible to open OLK files.
Why You Are Not Able to Open OLK Files?
You might still run into issues opening OLKs even with the right version of Microsoft Word installed. Other external problems could be to blame if the loading of OLK files continues to give you trouble. Problems unrelated to the software include:
- References to OLK files in the Windows Registry are incorrect.
- Unintentionally deleting the OLK file’s description from the Windows Registry.
- Microsoft Word or another OLK-related program that was improperly installed corrupted the OLK file.
- Malware has compromised OLK file integrity.
- OLK-related hardware uses out-of-date drivers.
- Not enough resources on the system to open files for Outlook Address Book File.
So, when it comes to investigating Mac Outlook data, the forensics examiner looks for OLK files. Why? let’s find out.
OLK File Forensics Investigation
Generally, in a computer crime scene, culprits will first try to destroy the evidence by deleting crucial data which could have helped the investigators reach them.
It may be easier for criminals to delete Outlook data files but not OLK files. Forget about deleting, OLK folders are difficult to locate in the first place. And, there is pretty much a chance that criminals may have skipped about deleting the evidence from these files. Considering the possibility of such a situation, forensic investigators first look at the OLK folders when examining Mac Outlook files.
To examine OLK files, forensic examiners generally use advanced forensics tools like MailXaminer. It helps investigators easily trace the facts of the crime scene and evidence with perfection in a systematic way.
An Ultimate Solution to Examine OLK File Using Professional Tool
Email Forensic Software is the best software used by digital forensic experts to examine email data on a deeper level. The tool has a wide range of advanced features that make the process easy to find evidence. This tool supports 20+ email file formats which include OLK files as well. It has a Search-Based Analytics Feature and Powerful Search Mechanism based on algorithms that help to find the data related to the specified keywords mentioned in the search field. The software also has many more features that make it easy for the investigating officers to smartly analyze huge data.
It is the best way to analyze email files in a secure and risk-free way. The software provides multiple features that are easy to use and give efficient results. It also recovers the deleted data automatically. After the examination process, users can easily export the evidential files into multiple file formats. In the next section, we are going to understand the process of examination of OLK files using this software.
Step-by-Step Process to Perform OLK14 File Forensics
Step 1: Add Evidence into the Software for OLK file forensics
To add the evidence to the software, users first have to select “OLM Identity”. Then, click on the “Next” button for further steps.
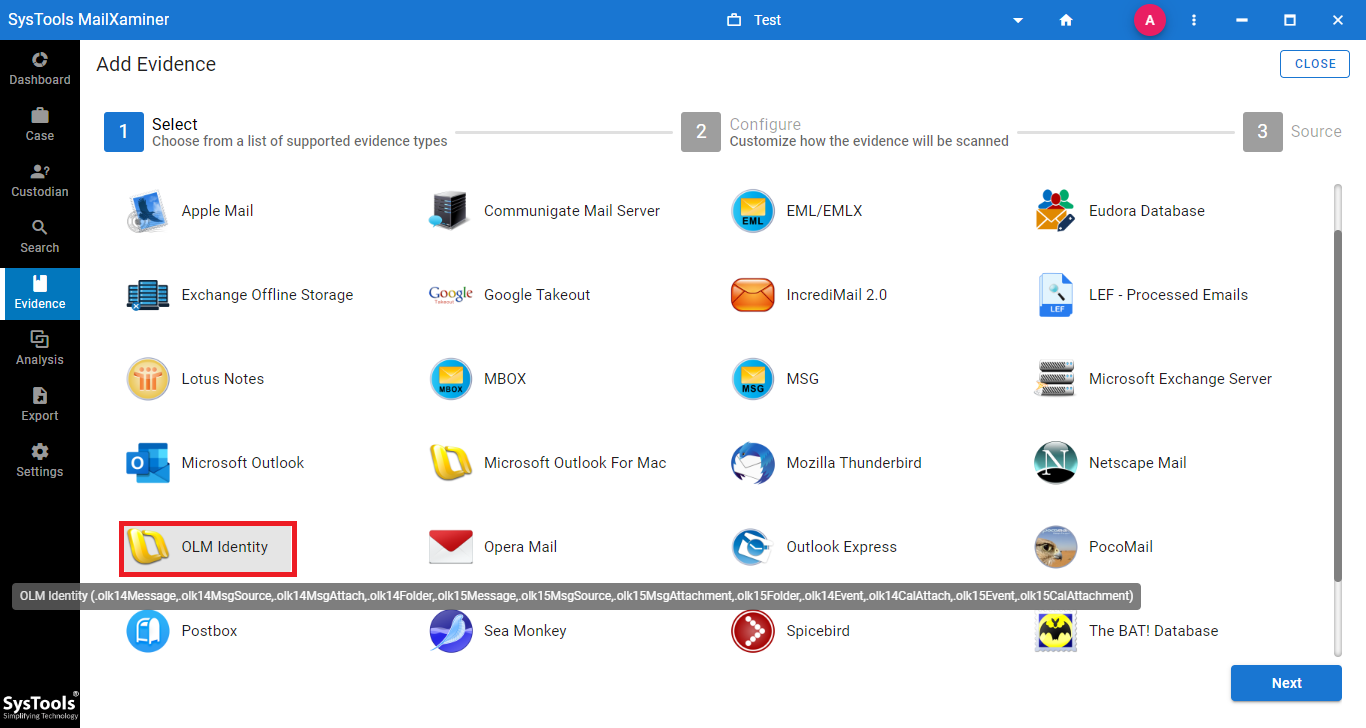
Step 2: Customize How The Evidence Will Be Scanned
After selecting the file format, the investigating officers need to select the desired options to customize how they want to scan their evidence.
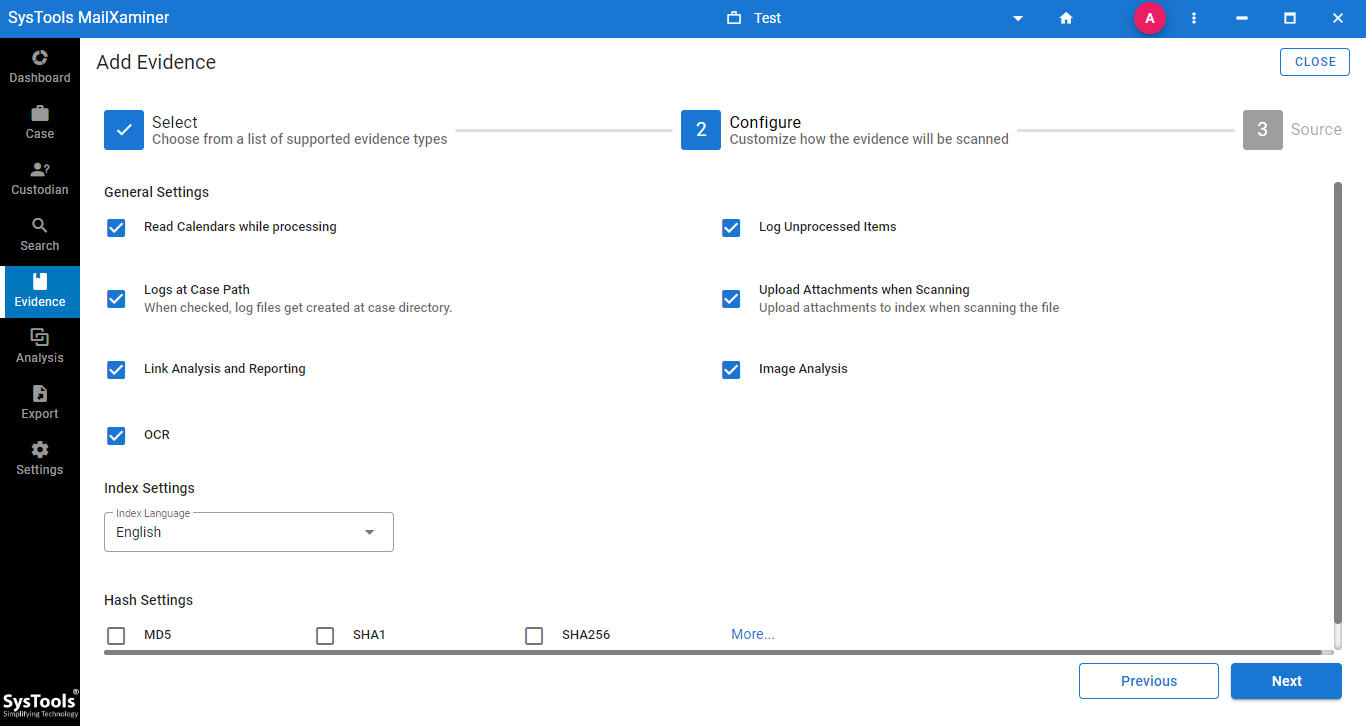
Step 3: Add Folder to Analyze the Evidence
After making the necessary configuration, investigators need to add folder for OLK file forensics.
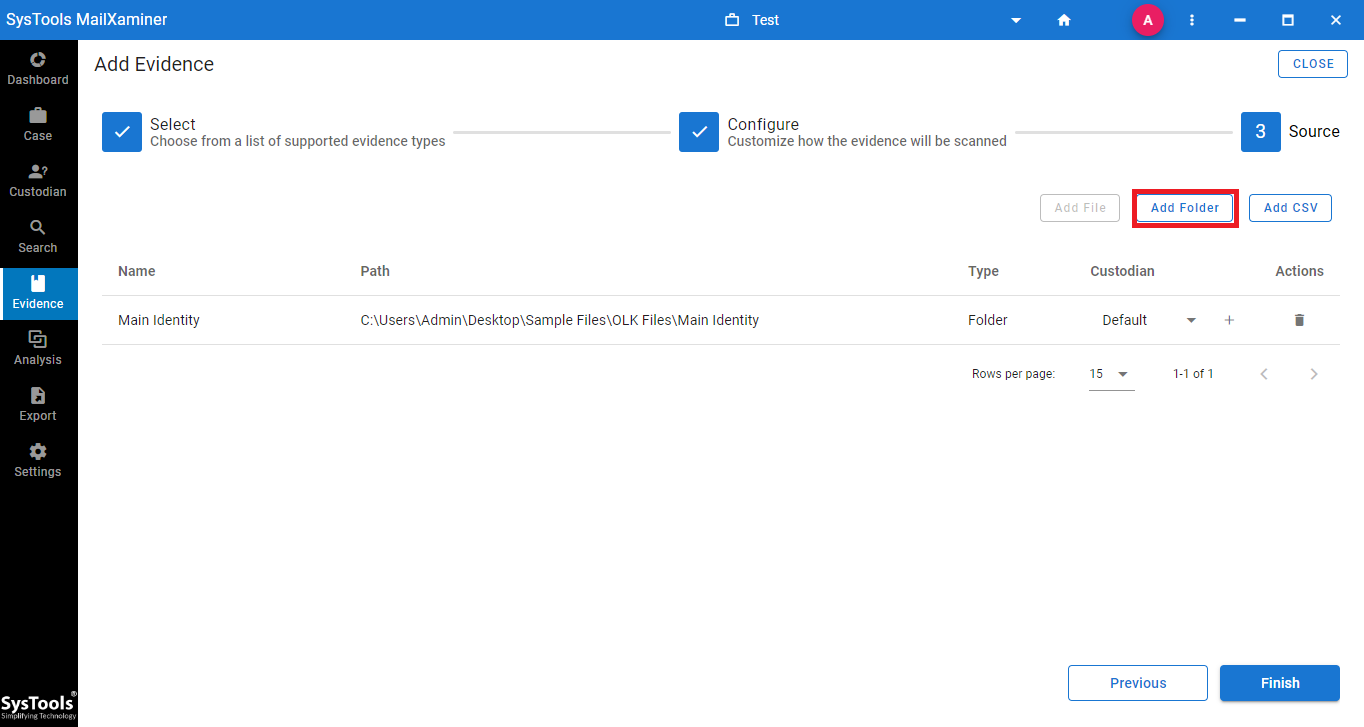
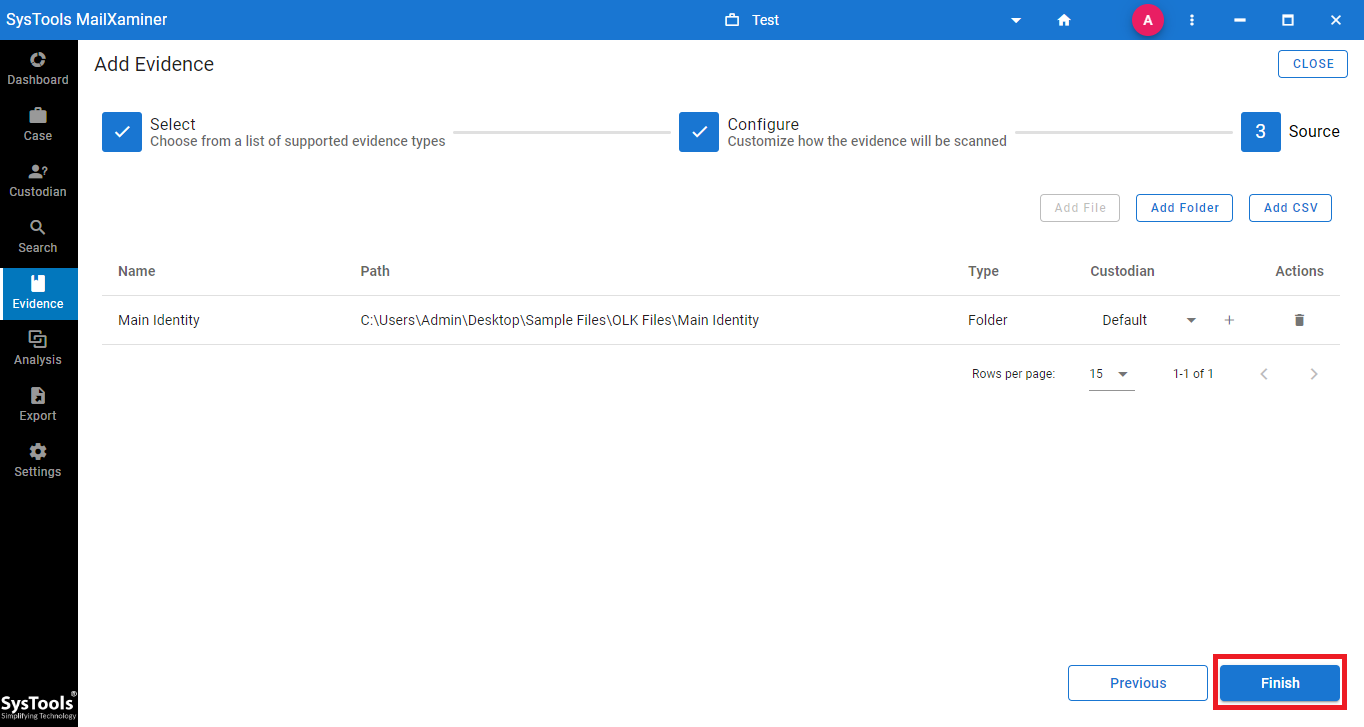
Step 4: Click “Finish”
After that click on the finish button to proceed further as shown in the figure.
Note: The software offers advanced search functionality. Users can find suspected data by providing related keywords for the same. It provides various search options such as General Search, Proximity Search, Regular Expression, Stem Search, Fuzzy Search, and Wildcard Search. Besides this, logical operators such as AND, OR, and NOT can also be availed from the software panel to perform a precise search.
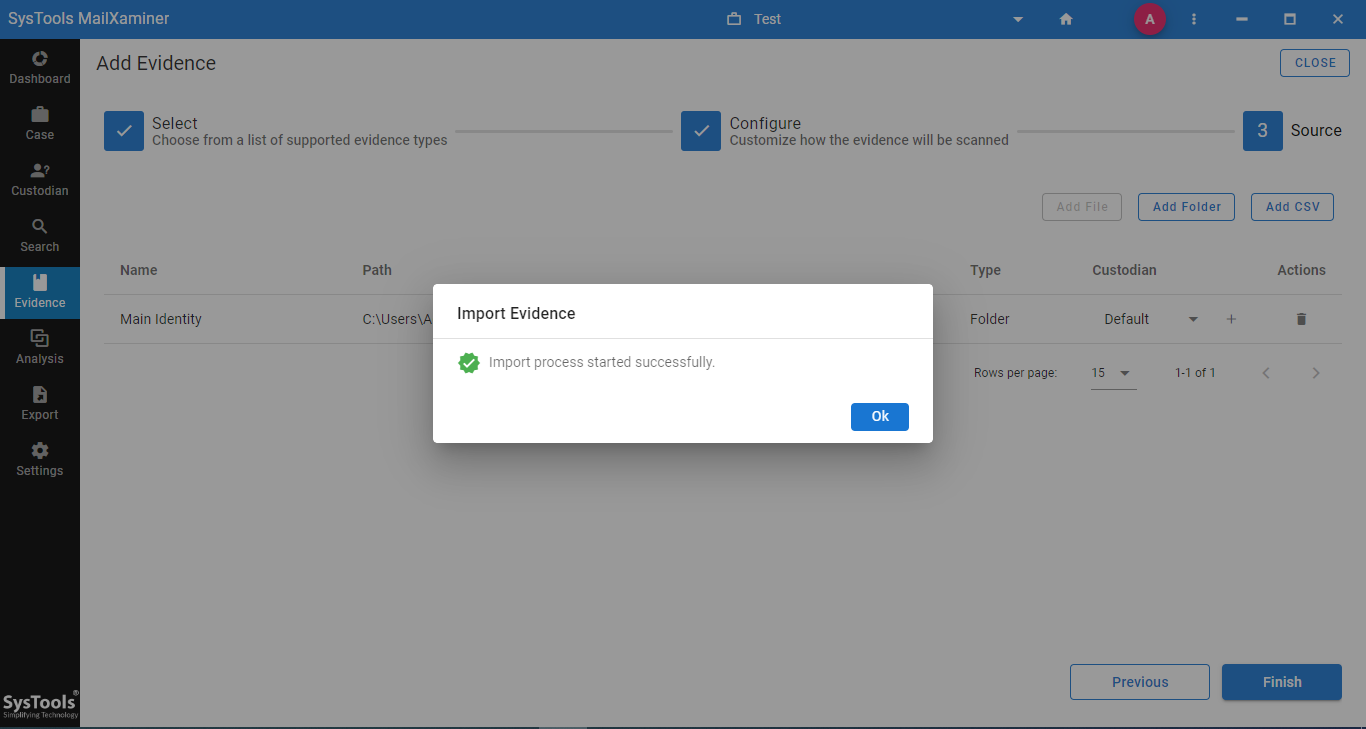
Step 5: Import Process Started Successfully.
Once you follow the above steps carefully, you will see the below on your screen.
Important Note:
Multiple search analytics helps to find the relation and connections between the users and other entities of the data. It provides four features such as Word Cloud, Link Analysis, Timeline Analysis, and Entity Analysis. This analytics function of the software represents the connection between related data in a graphical representation and helps to analyze the emails conveniently.
Word Cloud – Word cloud analysis is used to represent the frequency of words of a particular email message by differ in size and color.
Link Analysis – It helps to find out the connection and relation between multiple emails that are connected to each other.
Timeline Analysis – This analysis feature helps the investigators to analyze the frequency of emails by particular month, year, and date.
Entity Analysis – This analysis has the ability to show the location-oriented words used within the email message along with their frequencies.
Step 6: Export Evidence Report
After the analysis process, investigators can easily export the evidence report using the “Export” option. The tool provides multiple export file format options such as CSV, EML, MSG, HTML, TIFF, PST, PDF, etc. to export the analysis report. Users can save the report at the desired location of the local system.
Final Words
The OLK files created by Mac Outlook store the copy of email attachment files and OLK14Message files store the header information of emails. To analyze these files, investigating officers rely on professional OLK file forensics software. Thus, we recommend digital forensics experts use the above-mentioned software for carrying out a smooth investigation.

