Know About Need of Digital Forensics in the Emerging IoT World

In this era of digitalization, technology is considered to be one of the most convenient & useful medium of communication. It helps to connect individuals in a sophisticated way. Nowadays, the Internet of Things (IoT) has extensively emerged in the world of technology. Because of this, ordinary devices are uniquely identifiable, contactable, and addressable. The need of digital forensics is also there to counter unlawful activities.
It’s possible with the help of internet service that helps humans in making manual tasks easy. Need for digital forensics in the IoT world increases because it’s vulnerable to data breaches leading to cybersecurity threats.
From the “Amazon Echo” to the smart “Smoke Detectors”, people are using IoT devices in their day-to-day life. It helps to ease the work truly to a great extent. However, these home automation appliances, physical devices, etc, are a part of IoT. Therefore, in this blog, we will describe the importance of computer forensics & IoT forensics challenges in a precise way.
Overview of Internet of Things (IoT)
The ultimate goal of the Internet of Things is to make the lives of users more convenient and dynamic. Additionally, IoT devices generally exchange information with connected devices to develop an innovative environment for the end-user. IoT technologies have emerged in different areas such as medical care, social domains, smart home, smart city, etc. At the same time, it is also a gateway to cybercrimes attacks that may impact the users directly.
Thus, it leads to an increase in the need for digital forensics. One of the downsides of IoT technology devices is that they don’t have any special security and encryption features. The major concern is to minimize the cost and size of the product. As a result, these devices have a deficiency in their security. Therefore, it is the reason that increases the significance of computer forensic with the IoT environment.
To analyze a device for forensic purposes, each IoT device allows providing important artefacts to begin the investigation process. However, the standard forensic workflow comprises identification, interpretation, preservation, presentation, and analysis. Similar such workflow is integrated for IoT devices for forensic investigation. To know more about the role of the computer forensics investigation process, go through the below section.
Need of Digital Forensics in IoT World!
Altogether, IoT technology is a combination of various technology zones that includes IoT Zone, Network Zone, and Cloud Zone. Moreover, all these zones can be a source that can be useful to collect the IoT digital evidence. During the digital forensics investigation, investigators collect evidence from the smart IoT device.
These devices can be sensors, internal networks like firewalls or routers, outside networks, or any similar application. Now, based on these zones, IoT consists of three aspects with regards to forensics investigation that includes: Cloud Forensics, Network Forensics & Device Level Forensics.
Cloud Forensics – While talking about Cloud Forensics, most of the IoT devices are connected with the Internet to share the resources to cloud services using the applications. Hence, the sensitive data stored at the cloud is being targeted by hackers or attackers. Moreover, examiners may face a tough time collecting the evidence. This is because they’ve got limited control and access to seize digital equipment.
Network Forensics – In the case of Network Forensics, IoT devices use different types of networks to send and receive data. For instance, if an incident happens with an IoT device, then all the logs to which the traffic flow has passed such as firewall or IDS logs could be a piece of potential evidence.
Device Level Forensics – When it comes to Device Forensics, examiners can seamlessly collect digital evidence from IoT devices such as graphics, audio, video, etc. For example, all the potential graphics and videos from the CCTV camera or audio from the Amazon Echo device are the strong evidence that may found in the case of device-level forensics.
What Could be the Possible IoT Forensics Challenges?
There are some of the major IoT challenges that cause difficulties and issues in the investigation process. The need for digital forensics is increasing day by day. Moreover, these are some common situations that all should know to perform the proper investigation in the IoT world.
Data Location: This is one of the foremost challenges that the forensic investigator faces while collecting data, which goes to different locations. Additionally, IoT data can be located in different countries and also may be varied with the information of different users.
Finding Accurate Cloud-based Accounts: Most of the accounts at the cloud service are anonymous because it does not ask for proper details before using it. In today’s digital world, the need for digital forensics investigation is increasing rapidly.
IoT Security Challenge: Due to the lack of security in IoT technology, the evidence from an IoT device is prone to deletion or alteration. Hence, this evidence is not solid enough that the law court can easily accept the same.
Identifying the Device Type: At times, a digital forensic investigator has to undergo a tough time identifying the type of device used in the digital crime scene. This makes the process of acquiring the evidence quite complex to process the forensic examination.
Maintenance of Data Format: Oftentimes, the format of the data that is generated by the IoT device is not matched with the data that is saved in the cloud. Moreover, the user has no direct access to his/her data and also the file which is there in different file formats.
Well, now you got the importance of computer forensics and the IoT forensics challenges faced by the investigators during the process of investigation. But now you all start to think about the best way to perform the investigation in the IoT environment.
Best Approach to Perform Digital Forensics in IoT Environment!
We have already discussed the need for digital forensics in the IoT environment. Well, most of the existing forensic tool does not pose as a proven technology to examine the heterogeneous infrastructures of the IoT world. A hacker can easily take over the collected evidence from IoT devices.
It is because of the weakness exhibited by the IoT devices while considering the security factors. Thus, there’s no point to extract or collect such evidence from devices that’re not acceptable in a court of law. This means, with the increase in the significance of computer forensics, digital forensic examiners have to face a tough time in collecting evidence from different mediums without having proper forensic software.
To collect the evidence from different computer applications that are involved in the crime scenes, simply make the best use of MailXaminer Email Examiner. It is the most popular & reliable utility which is a gift from best technocrats. It enables users to easily locate and collect evidence in a simplified way from different computer applications. Learning the need of digital forensics, it can be more beneficial.
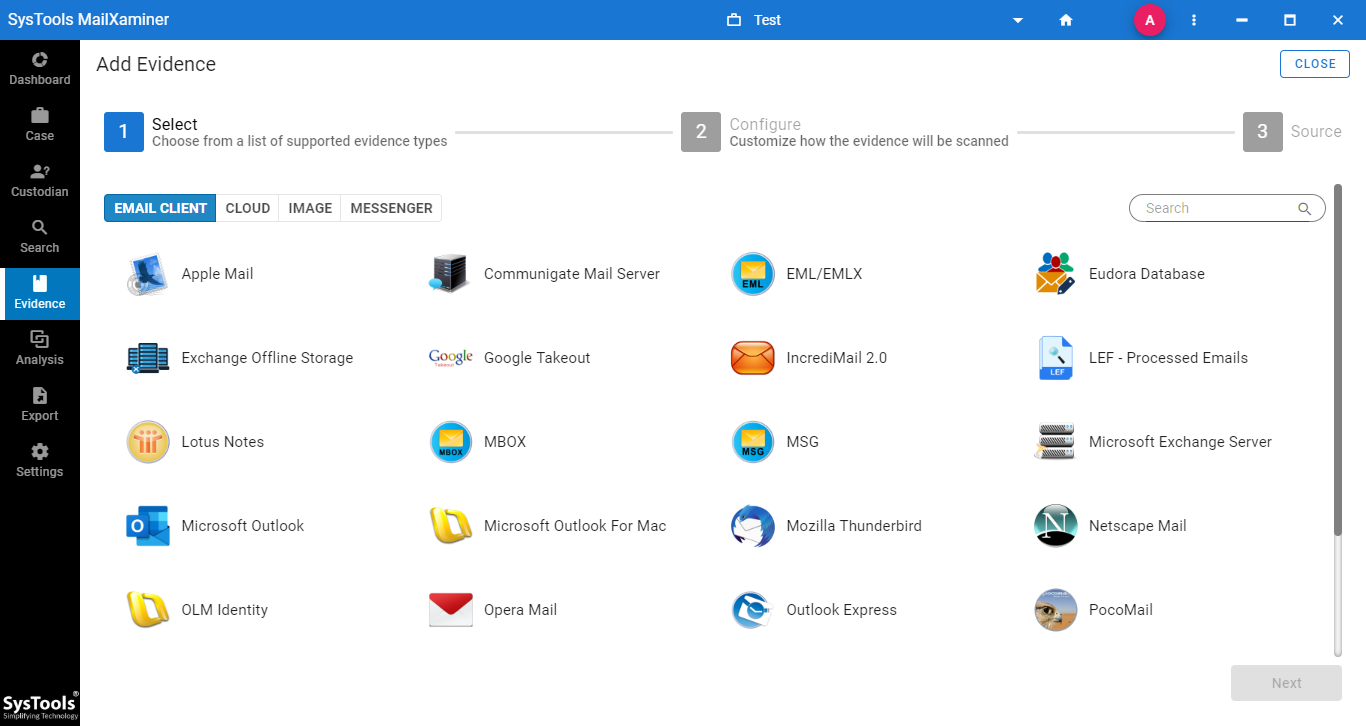
Concluding Lines
Due to the existing security challenges in IoT devices, the need for digital forensics is increasing day by day. No doubt, forensic experts need to face multiple challenges to analyze and examine IoT devices for forensic analysis. With the various forensic limitations exposed by IoT devices, forensic experts need to play smart enough to examine the data. However, the aforementioned software is the most unique and full-fledged forensic software. It allows us to smoothly investigate all IoT-related crimes in a hassle-free way.

