Ultimate Way to Perform Mozilla Thunderbird Email Forensics
,Ever got into a situation in which you have to implement Mozilla Thunderbird email forensics? Are you searching for a feasible solution to execute an email forensic investigation?
Well! Here is the blog for you to help overcome all hurdles which you might face while performing Thunderbird email forensics!
We all are aware of Mozilla Thunderbird, which is a free and open-source desktop email client and it is highly customizable. It can manage multiple emails, newsgroups, newsfeed accounts, and much more. Being a charge-less application, the majority of the users prefer this email client. As a result, it has become both source and target to commit cybercrimes. Therefore, Mozilla Thunderbird mailbox analysis becomes a matter of high concern to reach-out to the suspects and render justice to the victimized people.
Let’s Have a Look at the Case Scenario Furnished Below:
“Being a Digital Forensic Consultant, I used to face a number of challenges. Recently I have been assigned the task to analyze Thunderbird emails. Moreover, there were several suspected MBOX files, which were gathered from the crime location. As a result, it is quite difficult to manually examine bulk emails from each MBOX file. Therefore, kindly suggest some genuine email forensics software to examine Thunderbird emails.”
What could be an adequate solution to tackle such challenges? Come let us explore the blog!
Best Techniques to Analyze & Investigate Thunderbird Emails
Despite rendering strong security features by Thunderbird application, still the users become victims for several cybercrime activities. To efficiently trace the motive behind carrying out different illegitimate activities such as cyber theft of sensitive data, email spamming, theft of intellectual property, etc. It is important to analyze the email headers. Below mentioned are the different techniques, which prove to be helpful to perform Thunderbird email forensics.
Method 1: Thunderbird Email Forensics Investigation
Though there is various email forensics software, which helps to examine the emails in detail. MailXaminer stands way ahead among other forensics software, just because of its mind-blowing yet result-oriented features.
As it is designed to support both desktop and web-based email clients, it becomes convenient for forensic experts to analyze Thunderbird emails. One of the highlighted features of the tool is the ability to perform advanced search operations. Besides this, one can export the suspected emails in court-admissible formats such as PDF, etc.
How to Analyze Thunderbird MBOX file Using Email Analysis Tool?
Before investigating the MBOX file, one needs to export the MBOX file from the Thunderbird email application. For that, install the ImportExportTools Add-On and export all or suspected emails to MBOX format.
The following are the steps to examine Thunderbird emails using the Email Forensics software.
Step 1: Once the software is installed, navigate to Evidence screen >> click Add New Evidence >> select Mozilla Thunderbird to upload the MBOX file.
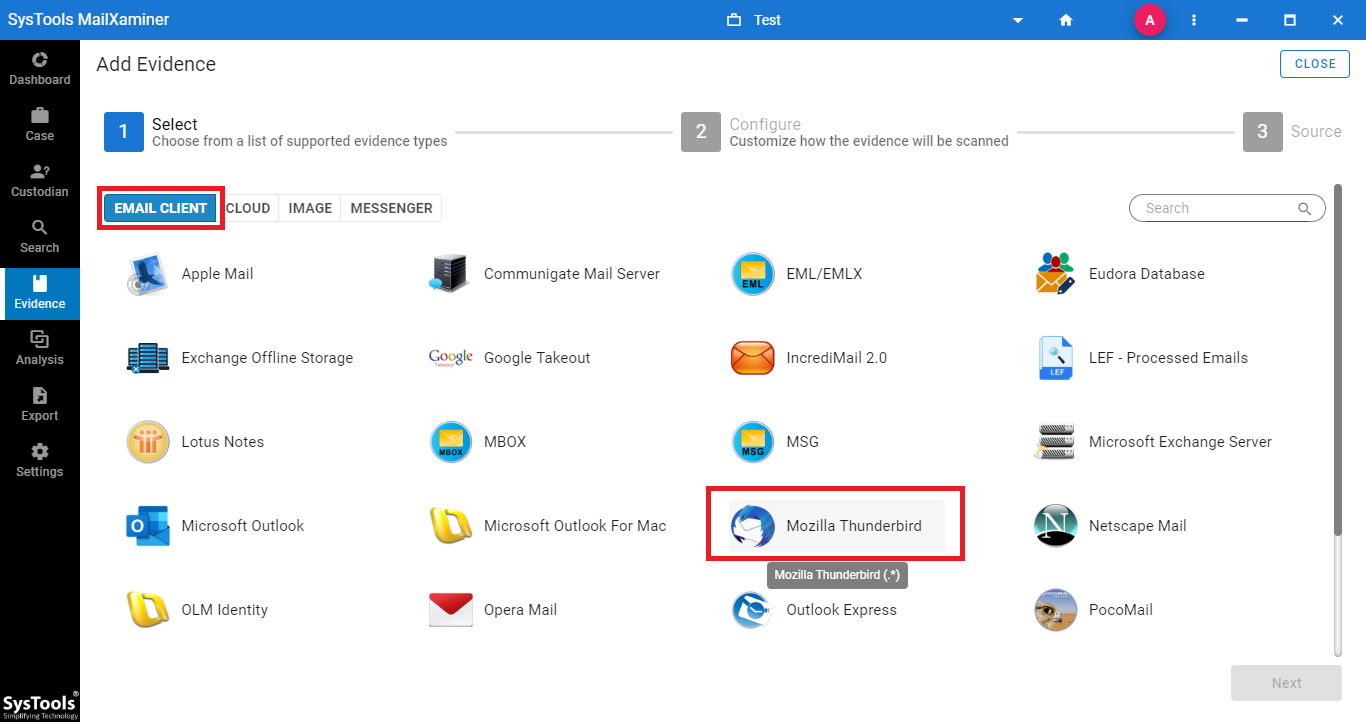
Step 2: After the .mbox file is uploaded, it will be shown on the software interface. Switch to Search screen to proceed further.
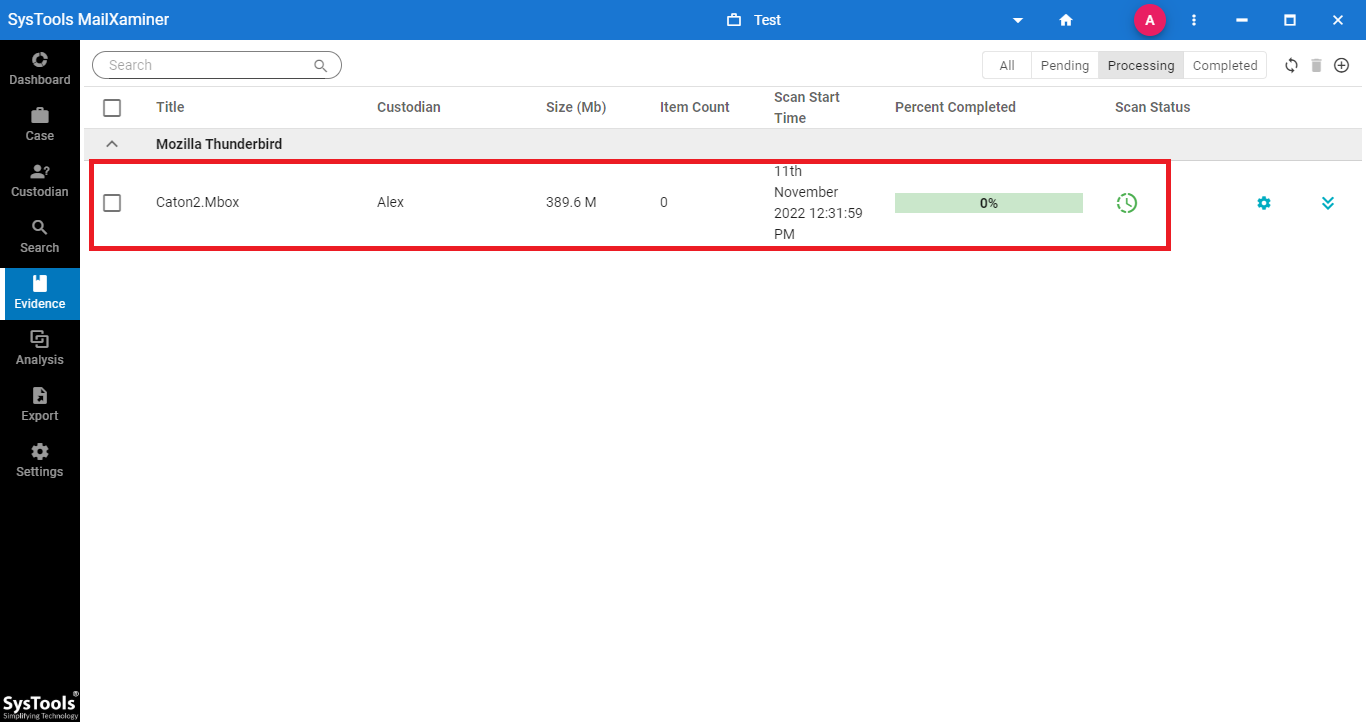
Step 3: Now, one can view the complete emails from the MBOX file. To preview precisely, just click on the email.
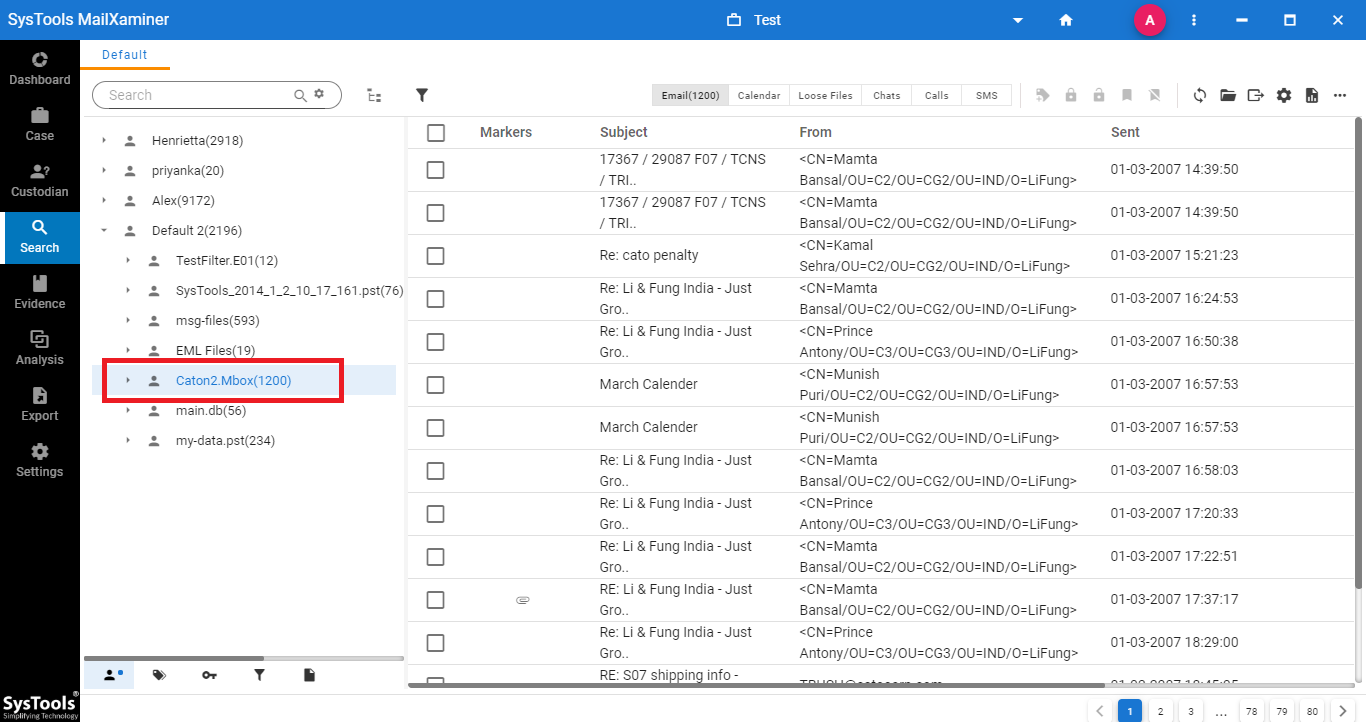
Step 4: The software showcases 7+ View options such as Message, Hex, Properties, Message Header, etc. Each option will provide detailed information of the selected email message
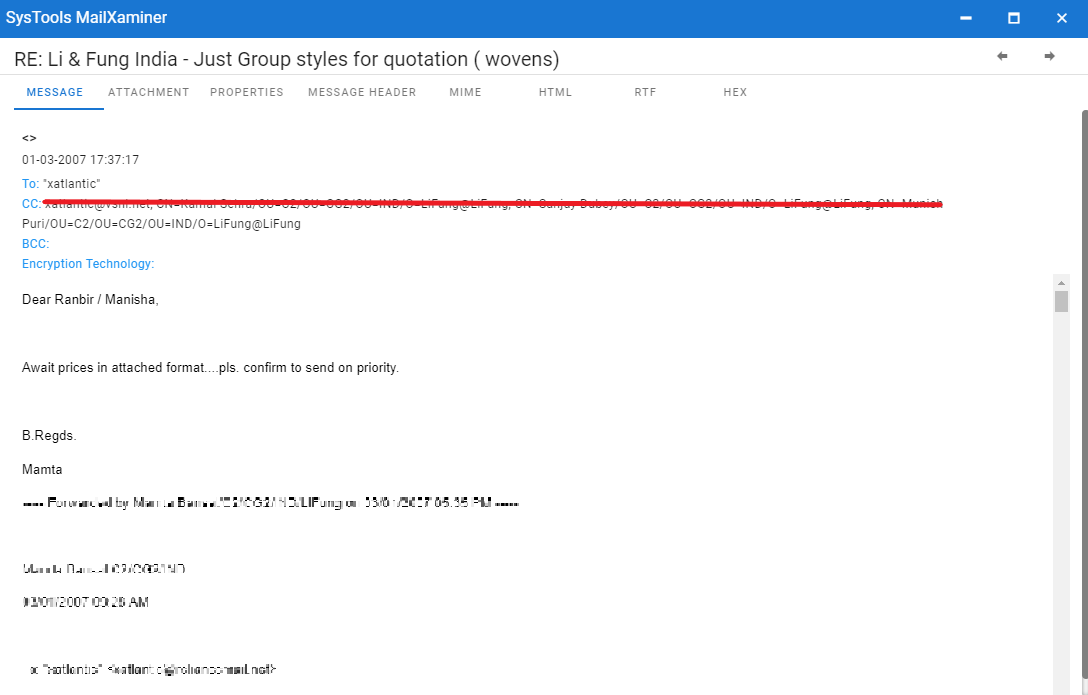
Step 5: Forensic experts can save suspected email messages in different file formats such as EML, HTML, PST, etc. After choosing the required email messages to export, right-click and select the Export option.
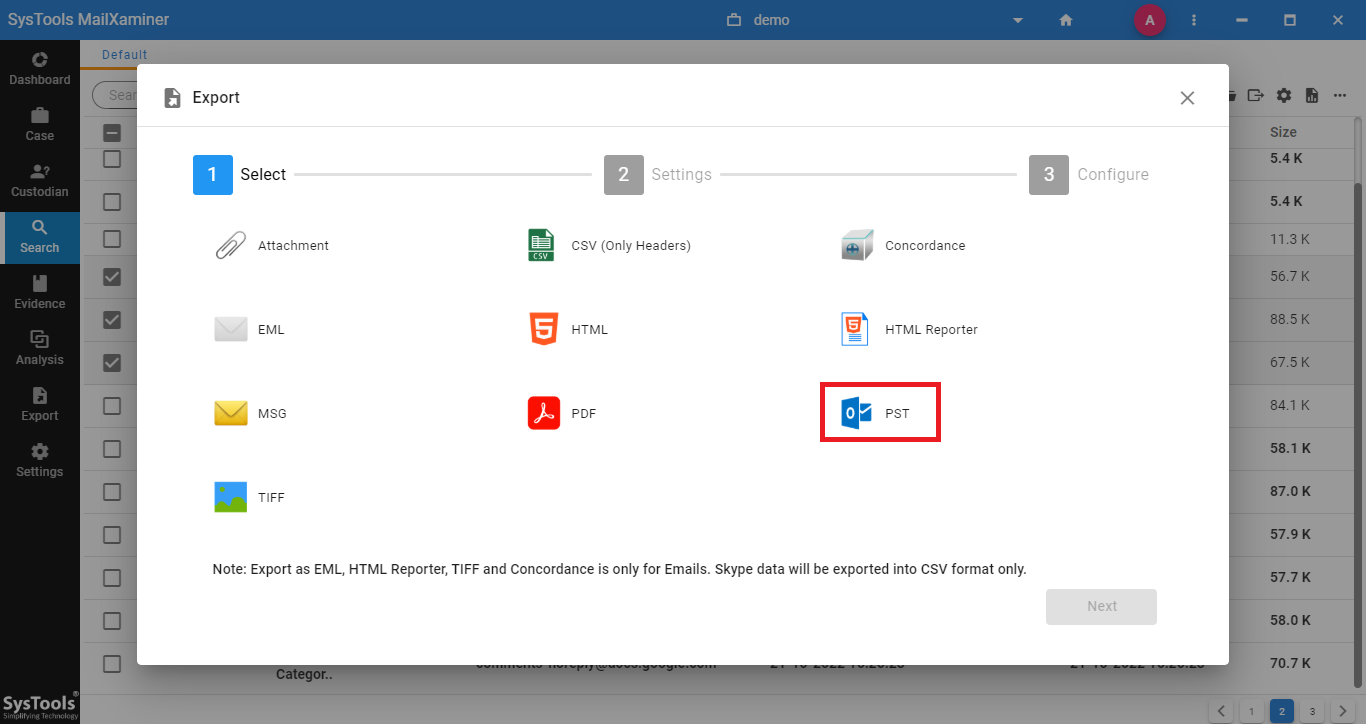
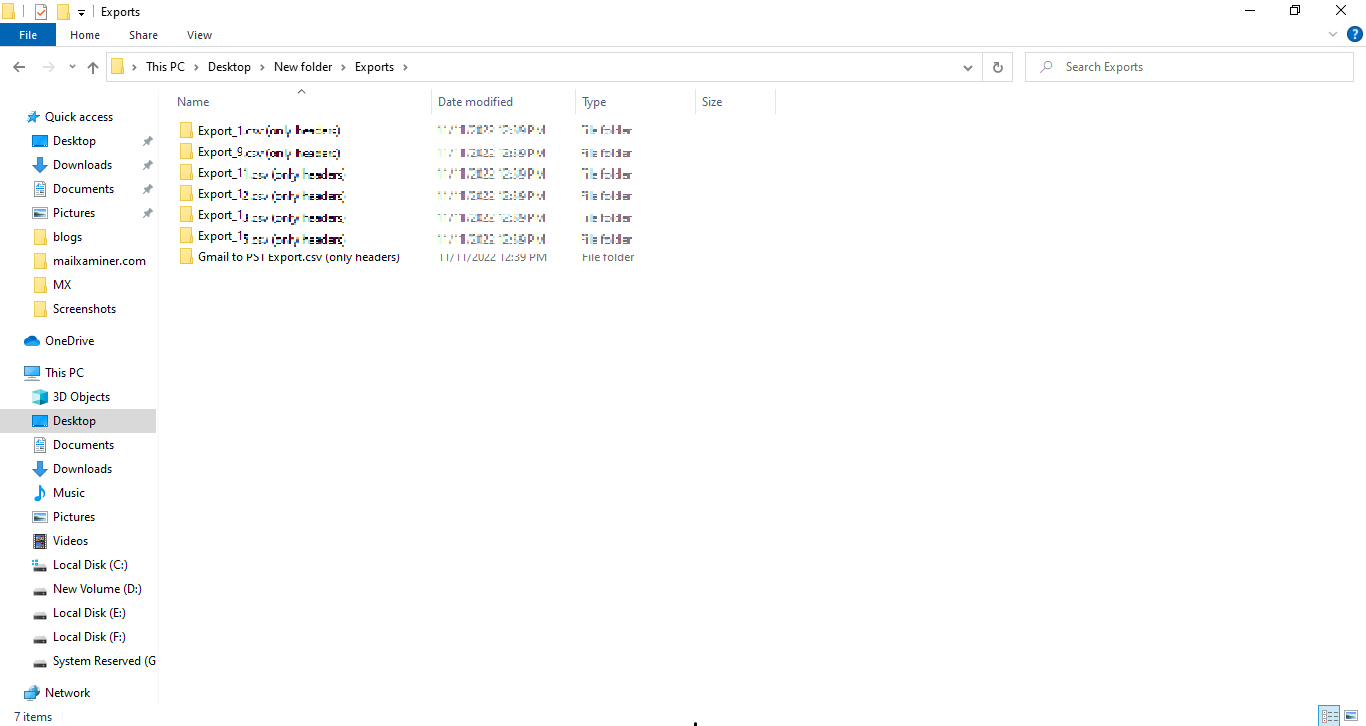
Step 6: One can view the converted email files at the destination location as shown below.
Method 2: Thunderbird Email Investigation Via “Header Analysis”
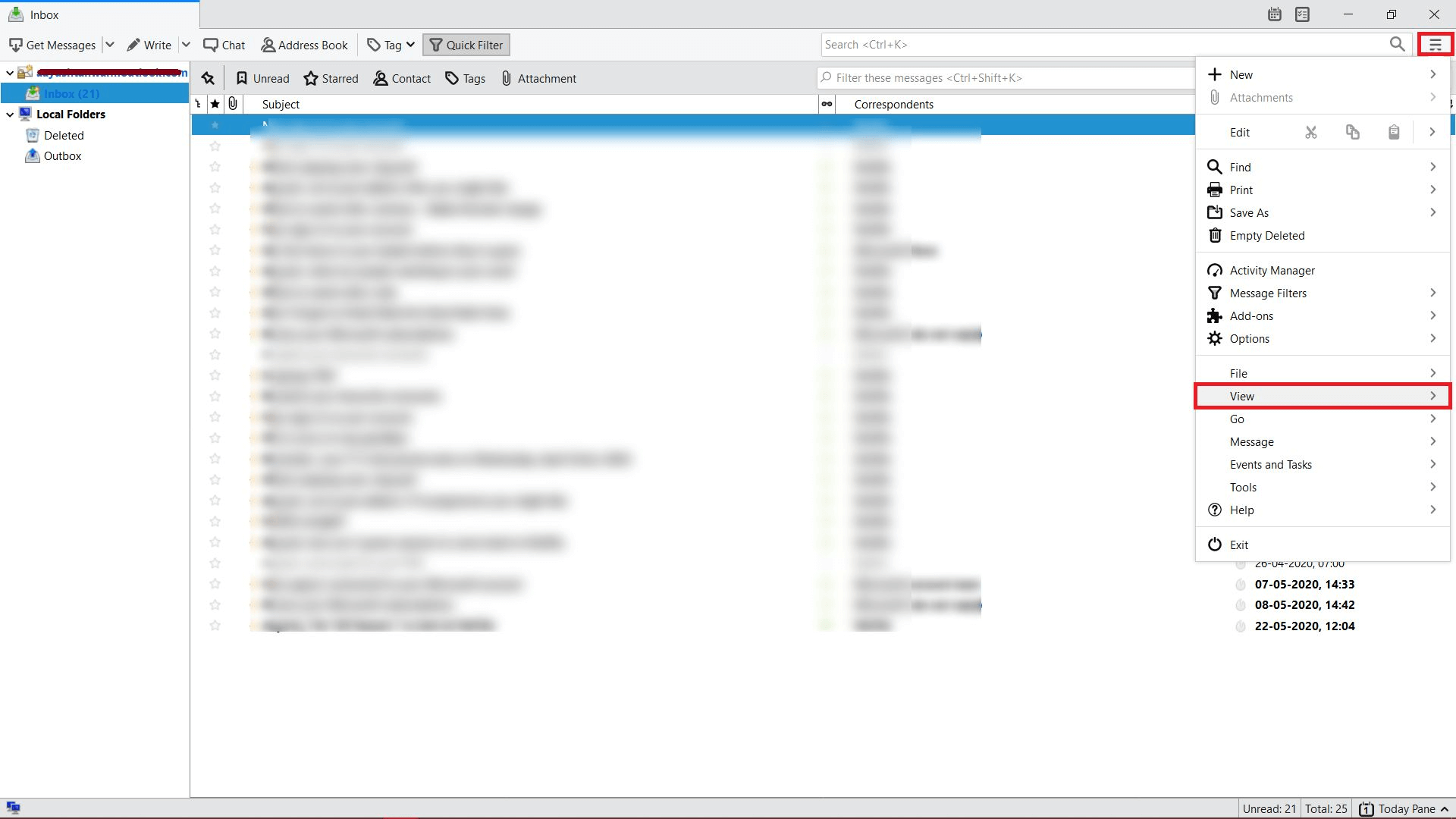
In order to extract the email message, follow the steps mentioned below:
- Open Thunderbird email application, then select Menu option >> choose View option >> click Message Source
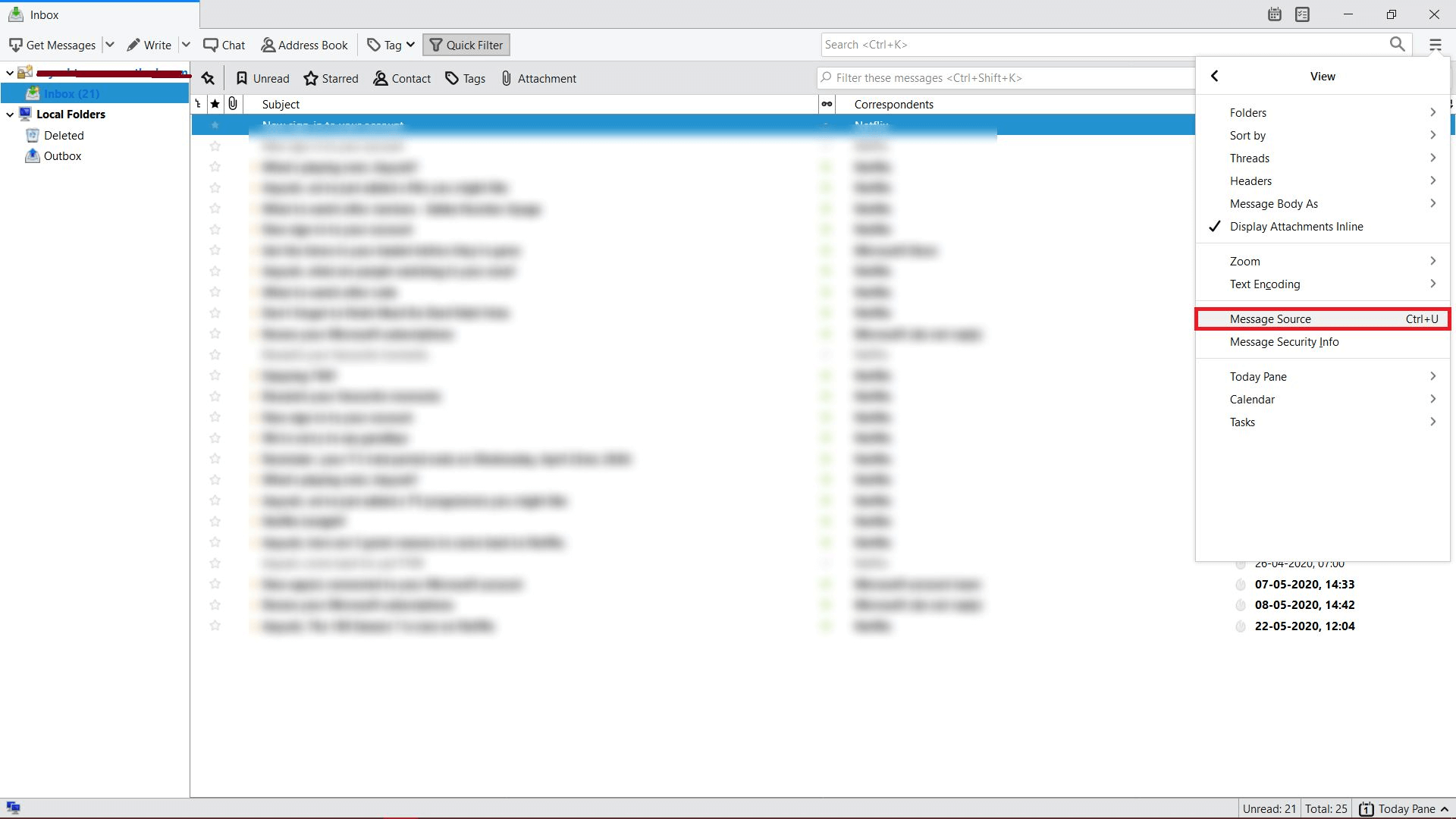
- After this, it will provide a Preview of the email header which can be saved by choosing File >> Save As option
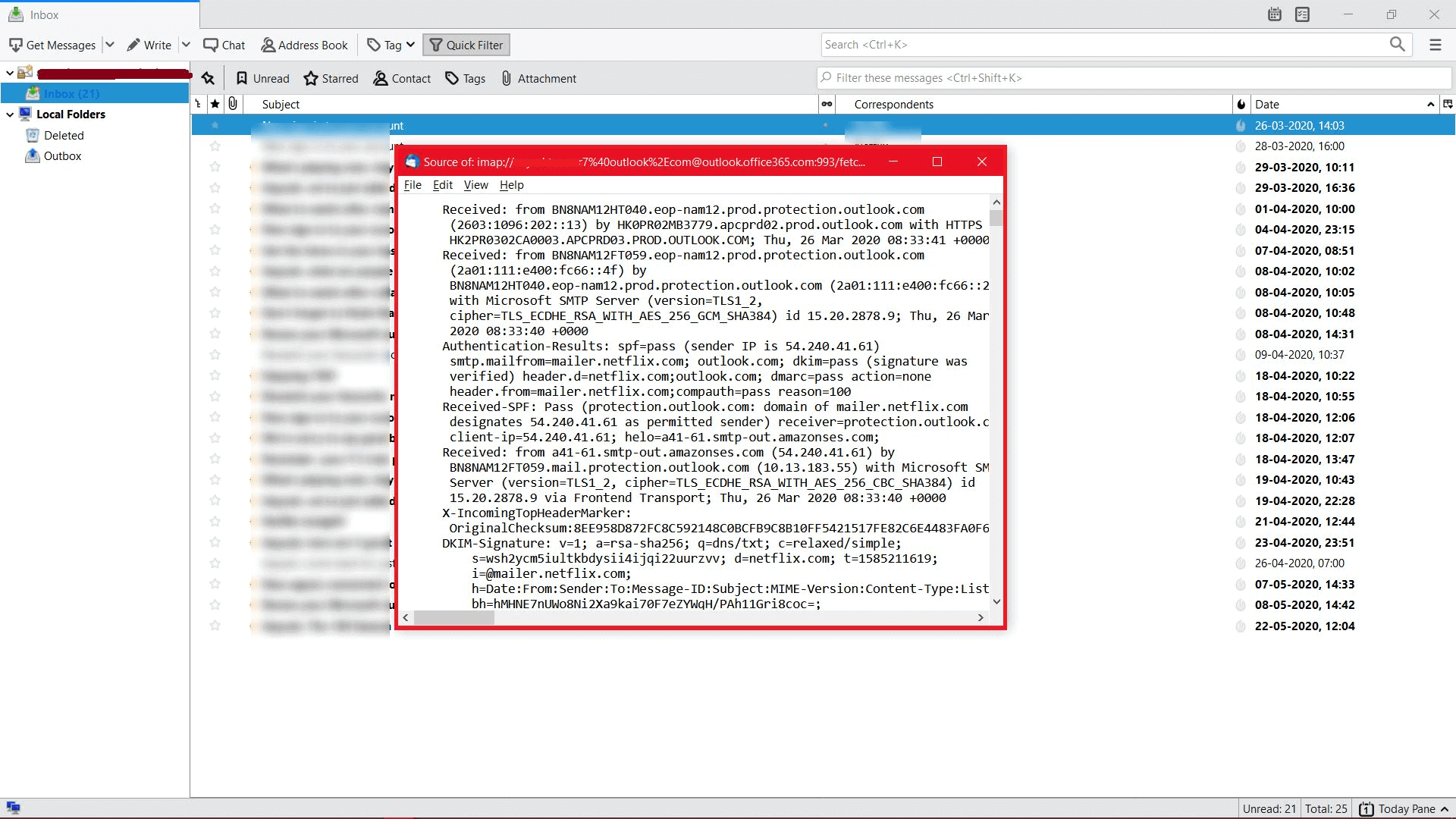
- Finally, the Message Header appears on the screen.
The various attributes of the Thunderbird email header consist of Received, Authentication-Results, Received-SPF, DKIM Signature, etc.
Method 3: Email Investigation by “Bait Tactics”
In a bait tactic exploration of Thunderbird email, an email with https: “<img src=””>” tag having image source is sent to the sender of email. Here, it must be acknowledged that the computer system remains in the custody of the investigators. When the email is opened, a log report having the IP address of the recipient is recorded on the HTTP server hosting the image. With this approach, the sender who has sent illegitimate email is being tracked.
However, if the recipient is using a proxy server, then the Internet Protocol (IP) address of the proxy server is noted down. The log details on the proxy server are utilized to trace the sender of the email, which is under investigation. If the proxy server’s record details are unavailable due to one or more causes, then the investigators may send the tactic email containing either Embedded Java Applet that runs on the receiver’s PC or an HTML page with Active X Object. With this, it helps to dig out the IP address of the receiver’s machine, which is then informed to the investigators.
Method 4: Email Forensic Scrutiny by “Server Investigation”
In Thunderbird email investigation by the server, copies of the delivered emails and server logs are examined to identify the exact source of the message. The emails eliminated from the sender or receiver client, whose retrieval seems impossible may be requested from the servers, i.e. either Proxy or Internet Service Provider. This is because these servers preserve a copy of all emails that are being delivered. Furthermore, the stored logs maintained by the servers can be investigated. Moreover, it helps to trace the address of the machine responsible for making the send/ receive operation of the particular email.
SMTP servers that store information such as credit card no. and other data belonging to the owner of a mailbox can be used to identify the person. However, it should be noted that the servers keep the replicas of the transacted emails and server logs for a limited time period only.
Method 5: “Network Device Investigation” for Analyzing Emails
In this, the logs recorded by the inter-networking devices like modems, routers, switches, firewalls are used to investigate the source of an email message. This form of investigation is rather complex and is used only when the logs of servers either proxy or ISP are unavailable due to different reasons. For example, when the ISP or proxy servers do not form and maintain the log report. Network device investigation helps to assist the investigators to analyze the emails by finding the offenders.
The End Note
Now, its easy to implement MBOX email analysis using various approaches that enables the investigator to perform Thunderbird email forensics. This can be done by availing the efficient email forensic software, analyzing the email headers manually, etc. However, to precisely dig the artifacts from the suspected emails, it is suggested to use the aforementioned email investigation software.

