Recovering Microsoft Exchange Artefacts with eDiscovery Export Tool!
During the investigation of corporate cases, dealing with the company’s information and related databases is probably the most crucial and difficult task for the investigators. It also requires getting acquainted with access for involvement in the environment of corporate offices to acquire databases.
Microsoft Exchange is one of the most efficient email servers mainly used in corporate sectors across the globe. Thus, an investigator has to explore the Exchange Server databases if there is a need for cybercrime investigation. Using a Microsoft Exchange eDiscovery export tool makes the process much less tedious.
To fetch the Exchange databases for the analysis process, it involves many processes, like the shutdown of the server. Users tend to perform various methodologies to bring the databases from active Servers to other platforms to analyze them without server. It can be easily done by using the best email analysis software for Microsoft Exchange eDiscovery export. This software is capable to export email data from Exchange databases to PST files, which can be further transferred to the investigation workstation. Let us see how this software works as a progressive product to carry out Exchange Server email forensic analysis.
Need for Microsoft Exchange eDiscovery Export Tool
The necessity of an advanced eDiscovery export tool generates because of the inability of bringing various Servers to investigation workstations for analysis. It is quite impossible to bring all the Servers to one place for investigation. Moreover, in order to analyze any database, it is required to shut down all the Exchange Server of organization that again can bring down the productivity.
Microsoft Exchange e-discovery export tool is essential for the email investigation, especially when it is linked to server-based emails. This software allows users to transport emails from Exchange databases stored on Servers to locally accessible PST files. These PST files can be then easily accessed using MS Outlook application. Some manual procedures can be implemented for EDB to PST conversion. But these manual procedures work only in certain situations and thus it cannot be trusted always. In such instances, investigators need an export tool that will allow performing an organized migration of Exchange email data to Outlook PST files.
E-discovery Advanced Search for Exchange Server
Along with the functionality of exporting Exchange EDB databases to PST files, the E-discovery tool for Exchange, i.e., MailXaminer has several advanced search options. Tool provides searching options that render various filters based on specific algorithms. Using these searches, one can effortlessly navigate the suspected emails within the Exchange databases.
The different search functionalities include General Search, Proximity Search, Regular Expression, Stem Search, Fuzzy Search, and Wildcard Search. The software will perform in-depth search across the EDB emails, once the files are loaded to the application.

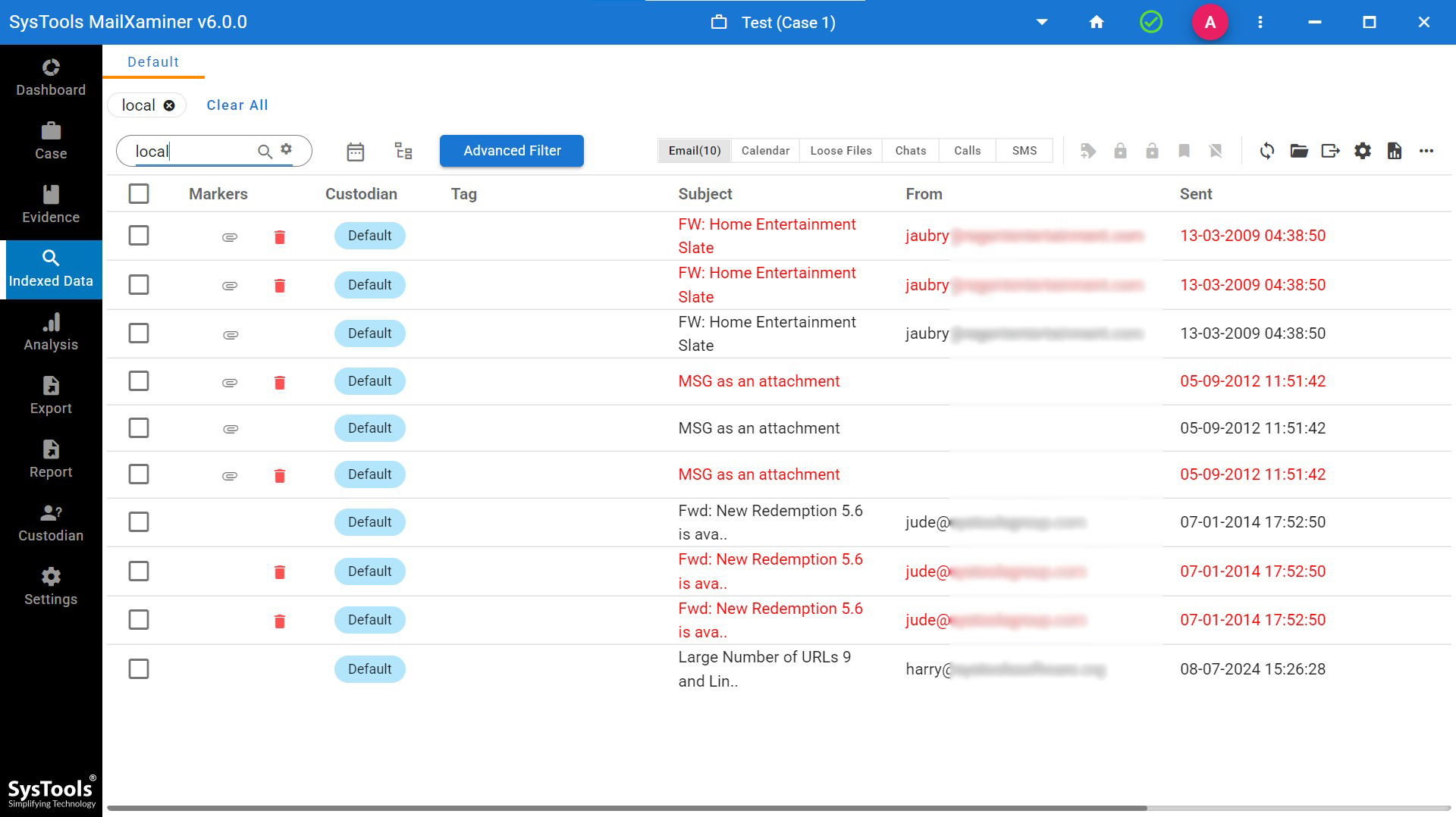
General Search: It is a basic searching option which helps to search for specific keywords against all the emails, subject, recipients, sender, and body. It also allows modifying the search by adding an operator to the keywords like AND/OR/NOT. For example, under the General Search, if user searches by entering “Local’ word in the search box, then tool will fetch all the emails containing “local” word.
Proximity Search: This kind of search allows finding the suspected words across the emails with regards to the distance between the words. One has to mention the keyword in the search box and a numeric digit (1, 2, 3, 4…). This digit denotes the Distance between Words that must be mentioned in the given fields. The tool will scan all the email files and fetch out the required result. For example, if user enters words i.e. server and inbox, and ‘Distance between words’ is 3. Then, tool will fetch all the resultant emails consisting of both the words separated by three words in between.
Regular Expression: This option helps to find the suspicious emails having the arrangements of patterns or string based on symbols, digits, special characters, etc. in it. In this search, users have to enter the string of pattern wherein the pattern which matches the words will be highlighted. For example, an investigator can easily search the emails containing domain email address. For that, a user has to arrange the pattern in such a way to fetch the files consisting of domain email addresses in it.
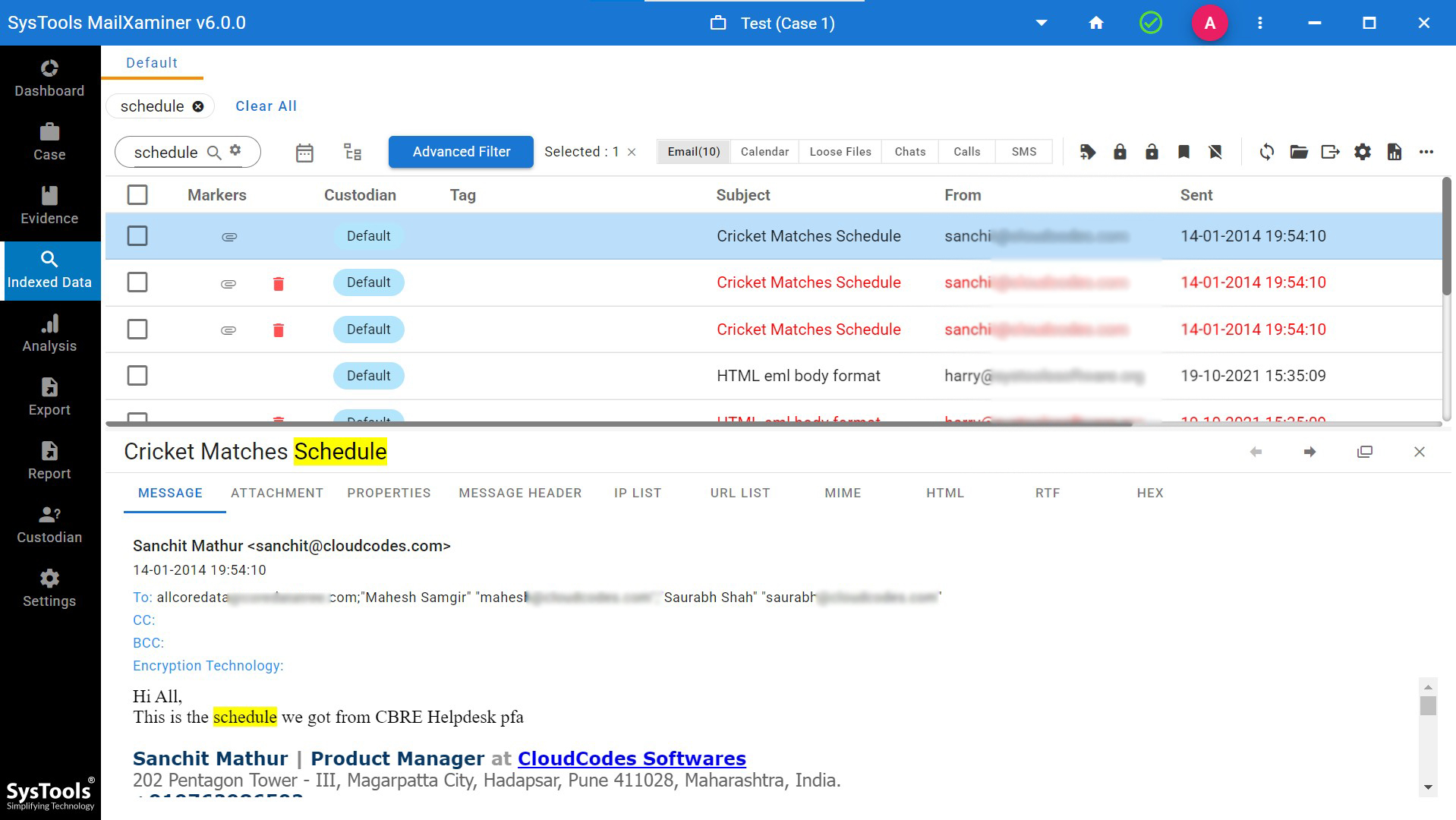
Stem Search: This option provides results based on the entered root word. It will automatically fetch out all the variants of the root word, then extract and show all the resultant words from the scanned data files. For example, if the user enters word ‘Mail’ in the search box, then the software will find and display all the resultant emails containing words like Mailbox, Mailing, etc.
Fuzzy Search: This search algorithm helps investigators to do a precise search. In this search, users can find the required information by inserting keyword without considering the spelling mistakes. It automatically distinguishes the correct word from the input keyword and shows the desired result. For example, if you search for the word “xamin”, the tool will find and show all the emails having similar words to ‘’xamin” such as examine, examining, etc.
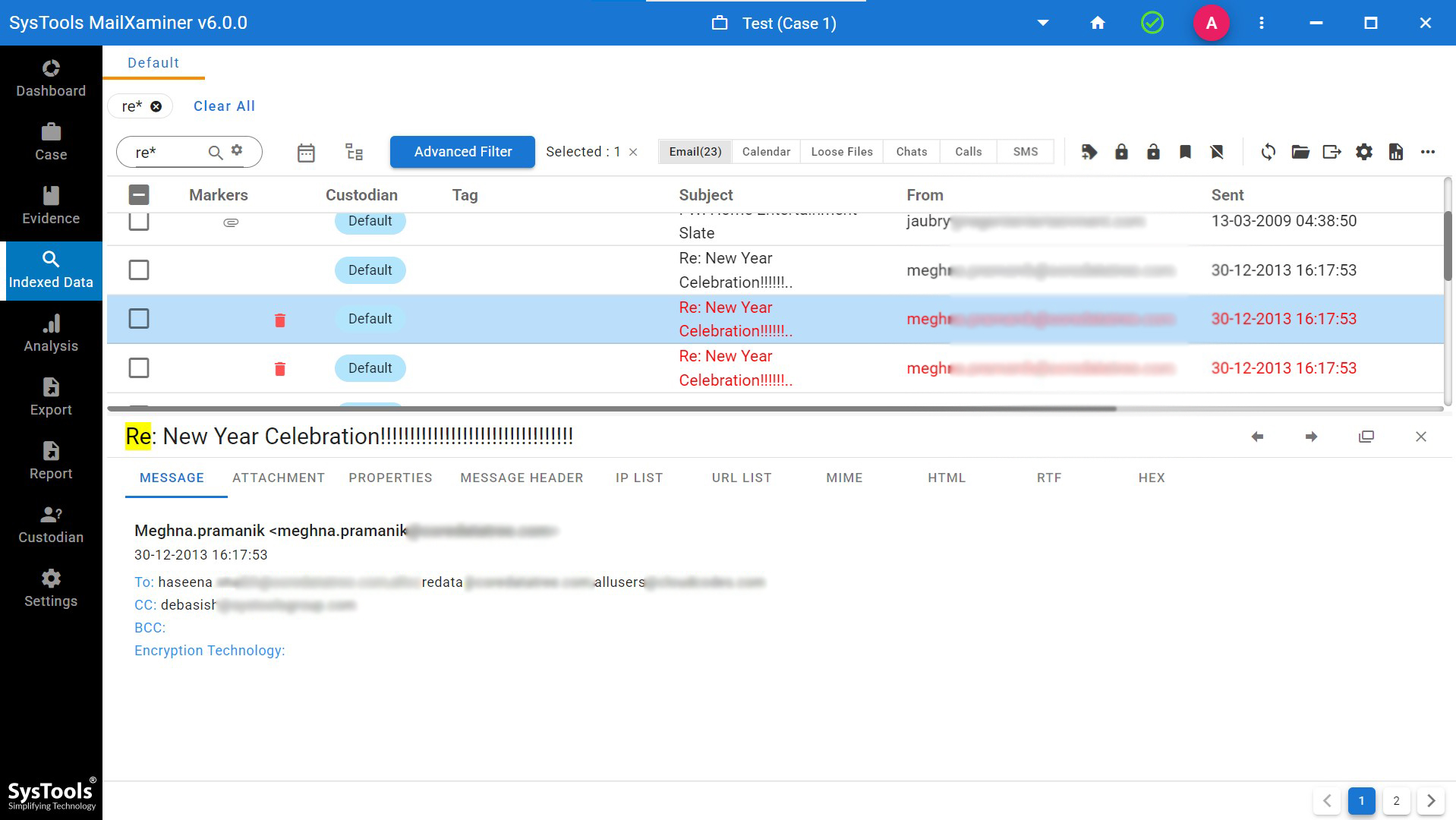
Wildcard Search: This is an advanced search option that helps to find the suspected data based on the input characters by utilizing two wildcards i.e. *(Asterisk), and ?(Question Mark).
*(Asterisk) – Using the Asterisk wildcard, one can easily search the relevant words by entering asterisk (*) just after the given characters. For instance, if a user enters ‘up*’, it will fetch all the related words having the initial characters as mentioned in the search box from the emails such as upcoming, upper, uploading, update, etc.
? (Question Mark) – During the investigation if user is not sure about the exact word, then all the possible keywords can be gathered using this search. For example, if a user searches for A??, then tool will extract all the email files starting with words ‘A’ and followed by two letters like Ant, And, etc. The number of question mark (?) denotes the number of character or letter.
Above mentioned search algorithms are sufficient to find and view suspected data from the uploaded file. It helps investigators to search the evidence in a precise way and saves a lot of time. Moreover, this software provides the facility for Keyword Search, Search Filters etc. Additionally, it allows scanning and processing a huge volume of data at the same time.
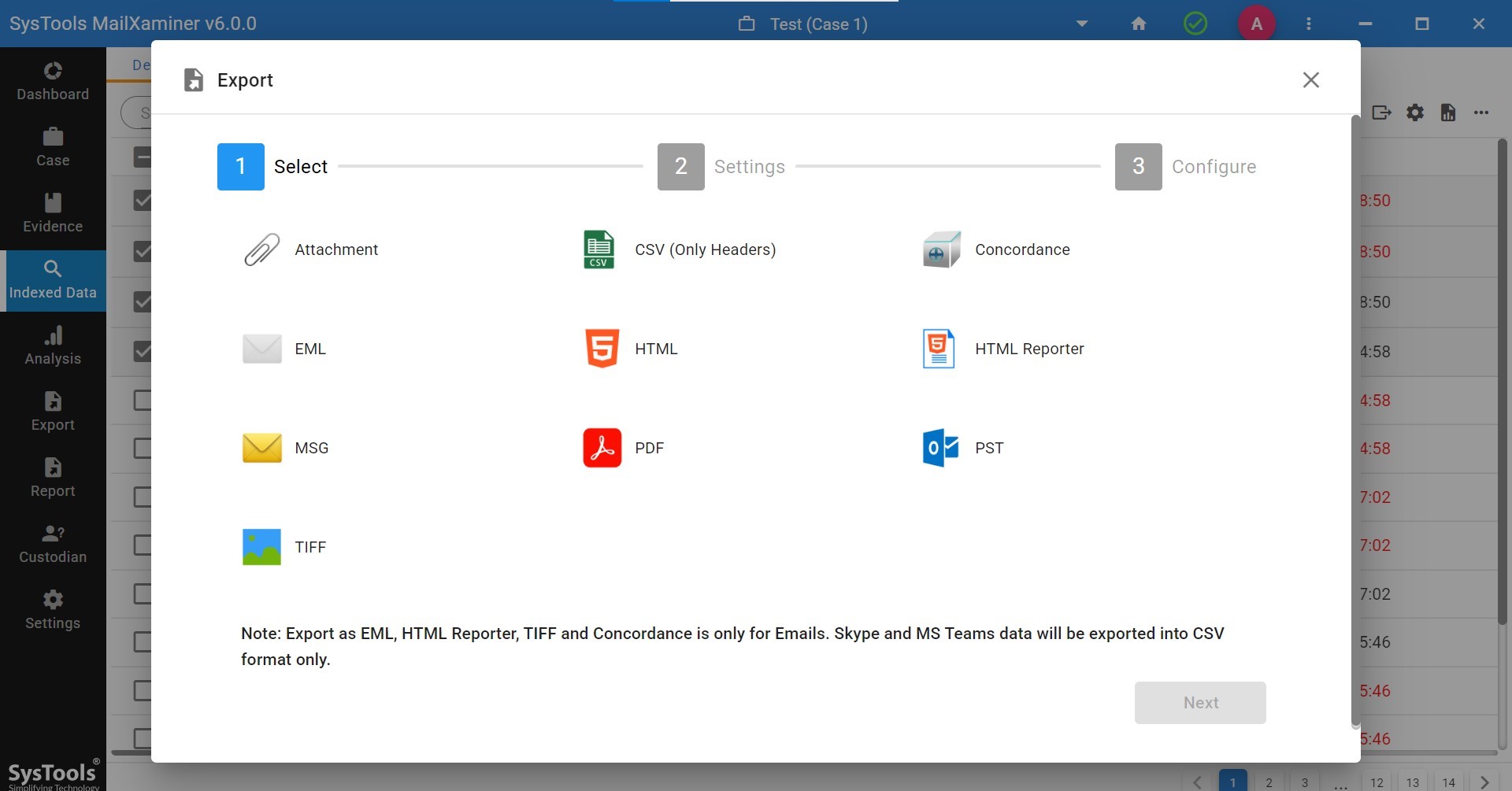
Export to PST Files Using Microsoft Exchange eDiscovery Export Tool
There might exist emails that are suspicious within the inbox folder and may contain some form of evidence inside the file. Exchange mailboxes and public folders, both can be exported easily to the PST file. Once the emails are exported to PST files, it can be further analyzed using the MS Outlook application to access the emails and analyze the data in a seamless way.
This article introduces one of the dominant e-discovery tools, it allows EDB to PST conversion for all or selective emails which consist of evidentiary elements in it. The extended support of the tool is towards all the versions of Exchange Server including the latest ones.
Conclusion
To perform a thorough analysis of the Exchange databases, one has to extract the emails to a better platform to have full access to it without any server restrictions. EDB to PST conversion is the best option to perform Exchange Server forensics and this can be done in a systematized way using this Microsoft Exchange eDiscovery export tool, which delivers 100% authentic results.

