Mailplane Forensics for Evidence Examination
An increase in digital crimes related to various email clients has led to the need for forensic investigation for both desktop as well as web-based email service. One of the email applications involved with cybercrime activities is Mailplane. It has been observed that Mailplane email service has played the role of a culprit as well as a victim in many cases involving the adverse use of technology. hence, Mailplane Forensics is a crucial topic to cover now.
Mailplane is a desktop email client, which allows the offline access of Gmail on Mac OS X 10.10 and below editions. The application focuses mainly to use Gmail in offline mode and without using a web browser. However, nowadays cybercrimes are mainly targeting Cloud services, including Gmail. In the following section, we will illustrate the analysis procedure and a possible solution to examine the Mailplane email service.
Analysis of Mailplane Gmail Client for Conducting Mailplane Forensics
Most of the cases that involve cybercrimes are mainly committed by using emails. There are some common ways, which could possibly lead to the usage of user’s data in mysterious ways. It includes emails spoofing, sharing of various codes via emails, spamming, email bombing, etc. To examine the crimes happening in Mac using Gmail, forensic investigators have to perform Mailplane forensic investigation to make an analysis of it.
Mailplane Gmail client provides a wide range of direct and quick options to perform tasks on Gmail. Some common features such as New mail, Reply, Forward, Send, Archive, and Save Clips are at the top of the screen. Along with these options, tabs for Inbox, Search, Navigate, and Bookmark are also available that are useful to open and view the required data instantly.
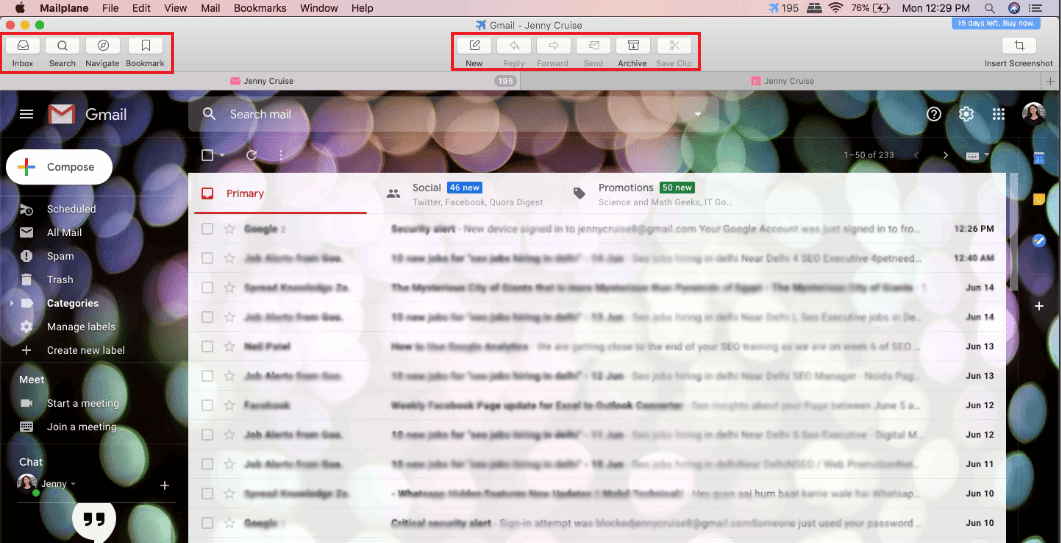
Fetch Required Gmail Data File using Search & Navigation
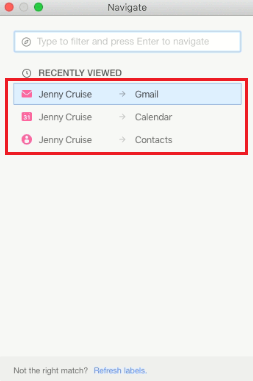
Mailplane email client exists to make Gmail easy and convenient to use. Navigate is one of the amazing features of the email program that can be beneficial to open and view any of the details related to Emails, Calendars, and Contacts. Users can directly click on the “Navigate” option and frequently choose the desired option to view related files.
Data Storage of Mailplane – Crucial Element in Mailplane Forensics Investigations
Local system typically do not save the web emails. Gmail by Google is one of the top preferences by users and is compatible with Mailplane. It offers 15 GB of free storage space with its universal access, quick and easy management of data. The free of cost availability of Gmail makes it more vulnerable at the same time.
Threat Detection in Cloud Data
The body of email message is mainly caught by the recipients through its header, which is the richest source of information from the forensics point of view. While examining an email’s header, users should consider various aspects including Message-ID, Protocols, Received headers, etc.
Sometimes, spam messages on emails, are not only waste but also pose a threat in when come from a malicious email account. Apart from that, enterprises can strictly oppose receiving such emails as they unnecessarily take the storage space on the user’s account.
How to Identify Spoofed Messages?
The basic concept of identifying a spoofed message is that it does not reveal the genuine identity of the sender. This is one of the reasons to look forward to the Mailplane forensics investigations. Various fields help in determining whether an email is spoofed or not. Some of which are there below:
- Sender’s name.
- The message is sent using email client and address.
- Origination of IP addresses for a specific message.
- Received field and Message ID.
Overcome the Challenges In Mailplane Forensic Investigation
There are various steps present in the forensic investigation, i.e. media collection, data validation, interpretation, documentation, and presentation of results at the time of judicial arrangement. However, cloud computing involves resource exhaustion, data lock-in, the unpredictability of performance, and bugs in large-scale distributed cloud systems. Thus, cloud computing is the most challenging part of an investigation. It is the physical acquisition and evidence controlling along with its validation, collection, and preservation.
To overcome the challenges faced by the investigators, they need to use the MailXaminer Email Forensics Software. It allows the investigator to analyze the data easily without any platform dependency. Moreover, it has a user-friendly interface, which makes it easy for users to preview the data in all vectors. It helps to carve out the connection between users and get an easy way to utilize detailed information of various portions in the email header.
Beyond this utility, there are various other ways to analyze Mailplane database. However, these methods are complex and require much more time. As time is valuable and investigation should proceed fast, therefore, the platform of MailXaminer forensic software is always helpful.
Conclusion
Mailplane email client investigation involves the cloud data forensics and cloud computing challenges. However, the understanding of its storage is enough to examine the activities carried out on the platform. Accordingly, using the automated tool is the most convenient way to perform Mailplane forensics. It saves user’s time and effort by automating the investigation with the help of autoload, detailed preview facility, and many other options.

