Kerio Connect Forensic Analysis
Considering the wide usage of email messages in business enterprises, it is quite common to come across situations when there is a suspicion of illegal messages received by the company from some hackers. In such cases, the company takes the help of law enforcement agencies which may come and ask for a detail of the logs that will help them to contend against the criminal activity. Since, there are no ways to accomplice this with a Kerio Connect server. System administrators have probably got more important things to do and it is obvious that manually digging out the log files would take long time.
To deal with situations like this, the law enforcement agencies take the help of a forensic investigators but when there is no way out to bring forth suitable evidence, they feel annoyed. However, there are still other ways to bring out the culpable evidence before law so as to punish the defendant. So, here we will see how we can extract evidence from messages of Kerio Connect. Let’s first fret deep into this email client before looking out for its forensic aspects.
Know Your Email Client “Kerio Connect”
Kerio Connect is basically a commercial emailing tool and a groupware server put forth by Kerio Technologies. Presenting the features of a complete robust platform, this application claims of speeding up work. One of the most attributed features of Kerio is its ability to connect and collaborate with any devices and constantly synchronize data, thereby moving the barriers of office boundaries and allowing users to access email messages even through iPhone. Because of its overwhelming capabilities, Kerio has been officially named as the “Office Workhouse”. Users can collaborate calendars, messages, contacts irrespective of the platform.
Now we can work on its forensic aspects. To carve out evidence forensically we need to learn about its file location and the form in which Kerio stores its data.
Forensics Investigations Carried Out on Kerio
The mail folder storage location path of Kerio Connect is as follows.
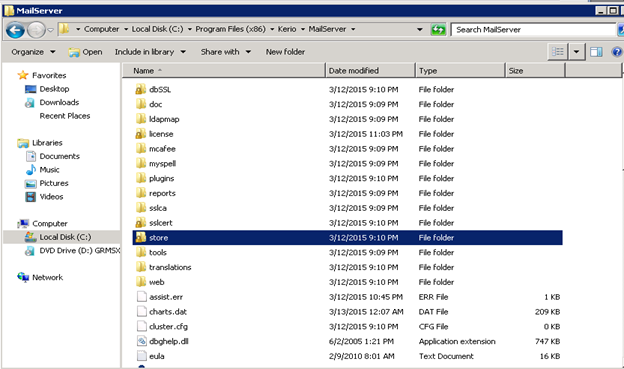
- All the configuration data can be located with following path
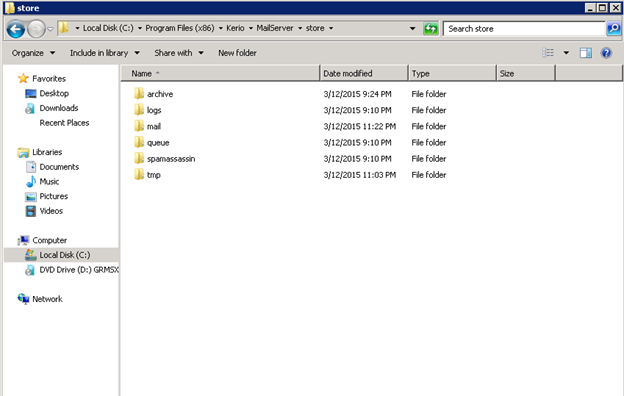
- The store directory is located in the following path.
Importance of STORE.FDB from Forensic Point of View
Firebird (FDB) is a SQL RDBMS system which is open source for users and supports it’s usage on a number of platform like Linux, Microsoft Windows, and a variety of UNIX Operating System. What really happens is that all the email messages, contacts, and calendars are cached in a database file which is known as STORE.FDB which is located in a folder in the user profile. Kerio uses this database for installations that does not contain much of data. In a way forensic investigators can consider this files as OST files of Exchange server.
Kerio Connect stores the emails in the form of separate files in file system directories, where every directory over here corresponds to an email folder. All the messages which belong to INBOX are found in the directory called “Inbox” like _STORE_/mail/DOMAIN/USER/INBOX/#msgs. Similarly, the Sent mails will be present in a system directory known as “Sent Items”. Now, one can easily notice that various indexes are built around those messages.
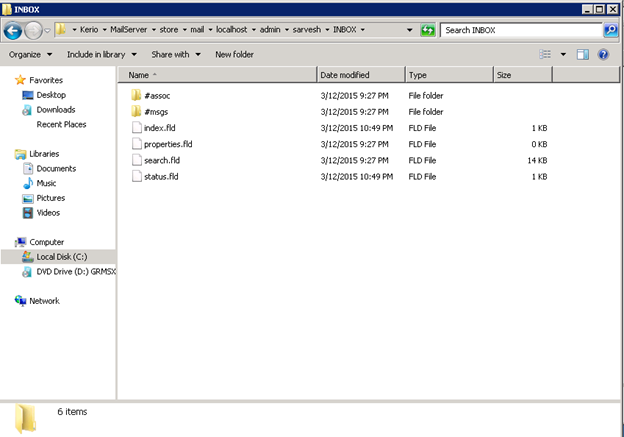
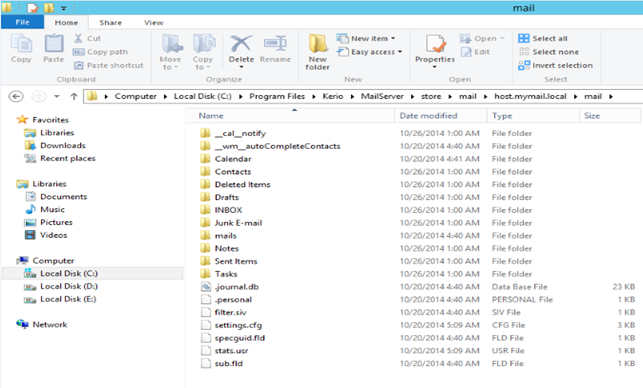
Now, one can easily notice that various indexes are built around those messages.
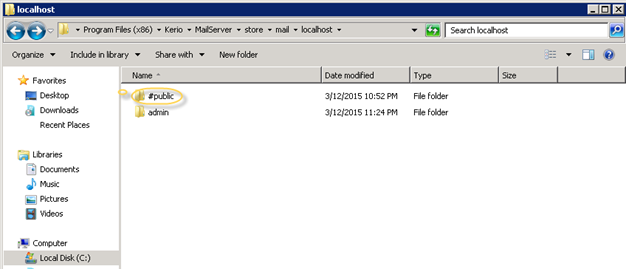
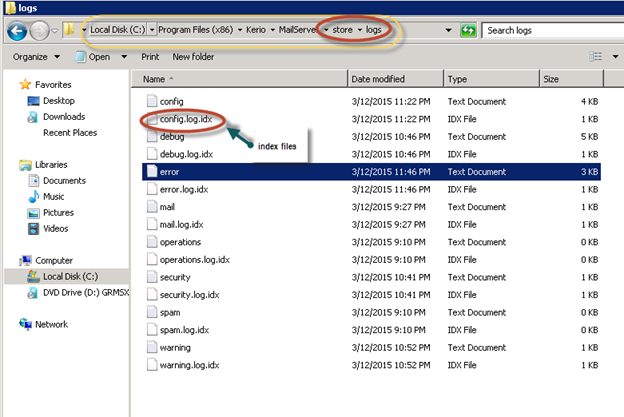
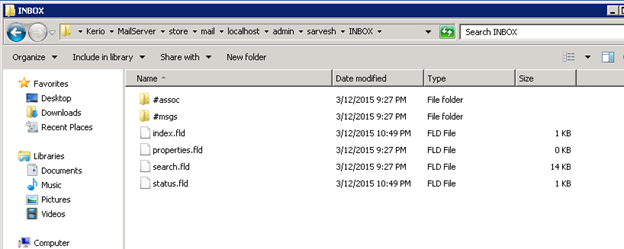
One mailfile in the mail queue contains the actual mail and a Meta file. One mail in a mailfolder consists of the actual mail stored in one file and one sets of files in each folder such as for INBOX folder: index.fld, properties.fld, etc.
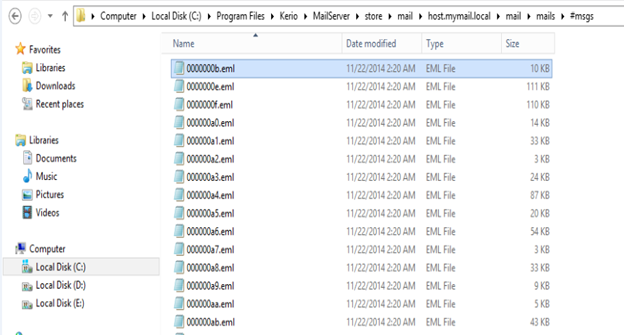
The messages present in the inbox are further found to be in EML file format.
Analyzing the EML Messages
Now, these messages which are present as .eml files can be further analyzed. All these messages can be individually examined with the help of a text editor. The investigators can take a look at the creation date and time which can be taken from the timestamp present in the Date line of the message header. Further, to check whether the message has been modified or not, they can extract the last modification date and time from the timestamp present in the Delivery-date line of the message header of the EML file format messages.
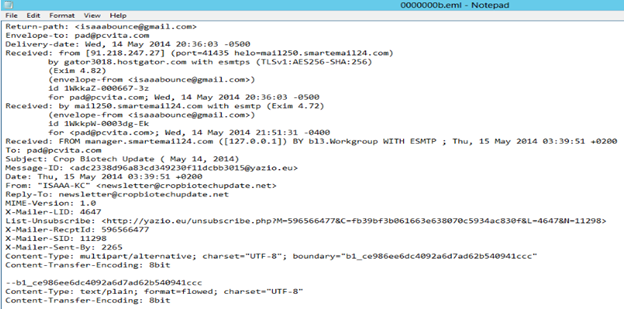
Tracing Messages by Carefully Reading Email Headers
The message ID located in the message header is a unique identifier that is assigned to the messages by the email server. By successfully correlating the message ID with the server logs, one can easily make out the data relevant to the messages that are received and sent from a particular system. The email header can provide investigators with health of data such as the record path traversed by the message from its journey from the sender to the receiver. One way of analyzing the email headers is to access them from the bottom to the top. Considering a sample header from a message given above, one can decipher several data. In such cases, forensic utilities like MailXaminer can provide great assistance to investigators for examining the data in EML messages carefully. Further, this email analysis tool can provide investigators to view messages in different view modes.
How to analyze whether a particular Kerio Connect account has been compromised or not? Whenever investigators doubt the possibility of the Kerio Connect server being compromised, they can find it out by the following indications
- Kerio Connect will show slow performance
- All the users will get their email messages as bounce back because they have not sent them
- The external IP address will get backlisted
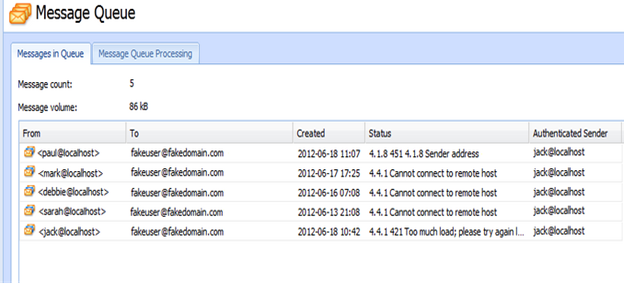
- Then one can notice that there will be a large mail queue, which will have a list of several email messages that are sent to an address about which users are practically unaware.
If all these things are noticed, then the investigators can make it out that the account has been compromised. To find out the specific account that has been compromised from the multiple accounts maintained on the server, investigators can enable a column in the mail queue view within the Kerio interface, which will reveal the account that has authorized the email messages to be sent.
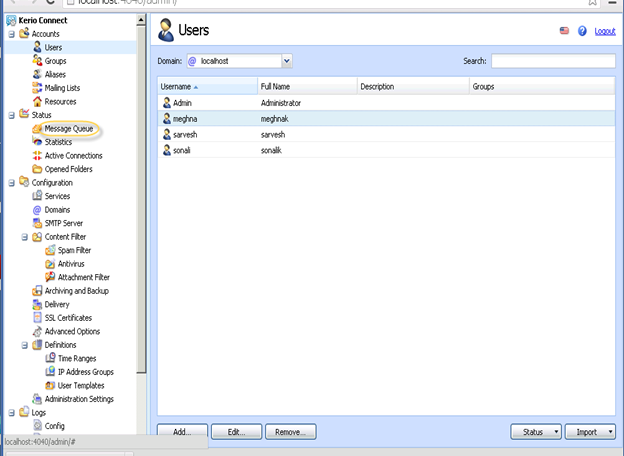
For this access, Kerio Connect Web Administration interface.
Move to the section ‘Status’, then ’Message Queue’.
Now, enabling the option would help the investigators locate where the message has been sent from which particular account. The sender IP will help to locate whether the message has been sent internally or externally, and the authenticated sender will reveal information related to the matter that the password of some account has been compromised or not.
Email accounts that are hacked have the potential to severely compromise the confidentiality of a business organization and therefore pose a very vulnerable threat to the company’s proprietary data. The above-mentioned ways can well assist forensic investigators to carve out inculpatory as well as exculpatory evidence from the Kerio Connect program, which can be well presented in the judicial court by law enforcement agencies. Besides that,t forensic experts can take the help of several forensic tools which may assist them to save time and bring out legal evidence clearly.

