Know About Forensics Hash Function Algorithm
Email application/clients is one of the most important utilities nowadays. Even fraudsters use these to commit various cybercriminal activities. From email forgery to various phishing attacks, the attackers make the best use of emails to conduct crimes. In order to find the alterations with the original email message, hash analysis plays a crucial role. It proves the authenticity of the emails. This blog will help users understand the best approach to perform forensics hash function algorithm.
So, let’s begin!
The forensics hash function algorithm is a cryptographic function, which is helpful to generate a hash value of the original email file. The hash value of the file is a string value (permanent size) of any specific file, which is helpful to various encryptions and authentications purpose. The complete hash value of the data file changes when even a single bit change happens in the data file.
There are various kinds of hash functions that users can perform for different purposes. However, in the upcoming sections, we will discuss the major hash values types for forensic purposes in detail.
What is Hashing in Computer Forensics?
Hash function algorithm in cryptography always has a goal to generate a safe and unbreakable hash.
But, do you know what a hash is?
“A hash is nothing but a value with origin from a base input value by using a cryptographic hashing algorithm.”
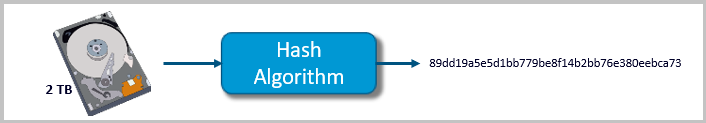
We can say that hash value in digital forensics is the sanitized summary of the original data file. Hash is the string value or block of the data file with the origin from the original data file using a mathematical forensics hash function algorithm. The hash value is generally smaller than the original data file. It can never be the same for two different files. In digital forensics hashing, even if a small change happens in the file, then the hash value of the file will be completely changed automatically.
What Does Hashing in Computer Forensics Use For?
Hash function algorithm is quite trending in IT and Digital Forensics. The hash function value is beneficial in message authentication, digital signatures, and various authentications like message authentication codes (MACs), etc. They are also popular in hashing for fingerprinting, identifications, identifying files, checksums, detecting duplicates, etc.
In data encryption, hashing is the most popular concept. Some popular forensics hash function algorithms are MD5, SHA1, and SHA256. In the upcoming section, we will describe each one of them in detail.
A. MD5 (Message Digest 5)
In cryptography, MD5 is one of the most popular and compatible cryptographic hashing algorithms that produces a 128-bit hash value. MD5 hashing in computer forensics is useful in various security applications. It is a one-way hash function, especially used to check data integrity of the files. One cannot generally decrypt the MD5 hash to get the original message.
It is one of the most widely known cryptographic hash function, which was used and still is in use. It is exclusively used to verify the data against unintentional corruption. Besides data integrity check, it also helps to verify whether email data is not tampered, once it is loaded in the Inbox folder. Thus, it helps to validate the emails in a seamless way.
B. SHA1 Secure Hash Algorithm
SHA1 is yet another cryptographic algorithm that takes an input file and produces a hash value of that file. It generates a string of 160 bits (20-bytes) in length. This hash function in network security is also known as a message digest. It is typically rendered as a hexadecimal number which is of 40 characters in hexadecimal form.
SHA1 cryptographic hash algorithm is most commonly used to verify whether the files are altered or not. This process takes place by producing the checksum before the transmission of the data files. Once the file reaches the destination, the hash value in digital forensics again produces a value to verify the checksum of the same file.
C. SHA256 (Secure Hash Algorithm 256)
SHA256 cryptographic hash (sometimes called “digest”) is also known as a one-way hash. It is almost impossible to reverse the original file from the hash value and it works as the signature for a text or data set. It converts a text of any length into a unique string of 356 bits (32-bytes) in size.
SHA-256 forensics hash function algorithm is majorly used to check the integrity of the data files, including digital signatures, transaction verification, etc. Furthermore, it cannot decrypt the data back to its original form.
How to Calculate Hash Value of Emails?
The hash value depicts a string value of a specific length generated using a hash function algorithm in cryptography. It may be having different uses, including forensic purposes. It is not a process to be done manually. Several hashing tools for computer forensics are available, which are specially designed to calculate the hash values of the files. One such software is MailXaminer.
It is one of the best software which automatically calculates the different hash values of the email data file without any hassle. Users can preview the hash values of the emails in a single glance, as required.
Let’s Proceed Further to Know How to Do It?
The software lets users obtain hash values of the email data file in a simplified way. It renders a user-friendly interface, which allows forensic experts to smoothly examine the hash values of the emails. Additionally, it is capable to support 20+ file formats and various email clients. The software has many more advanced features that can be beneficial in a forensic investigation, which you can learn by overviewing the tool’s features. Now we are just focusing on the process of obtaining the hash values in the most reliable way without using cryptographic hashing algorithms.
Here’s how you can get the hash values?
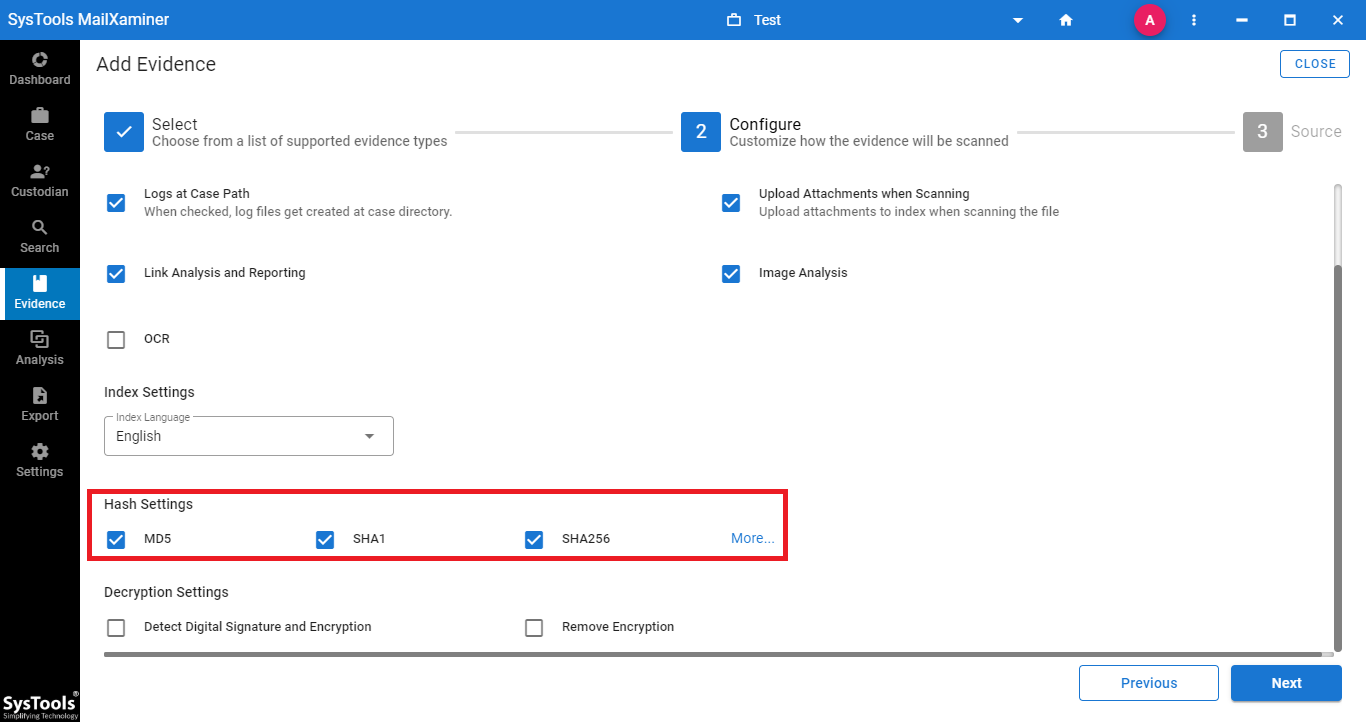
While importing the email file into the software, under the Configure step, one needs to mark the checkbox corresponding to the hash functions option. Users can select one or all the hash values they need to acquire as per the requirement.
After scanning the file, the software will provide a preview of all the uploaded data files.
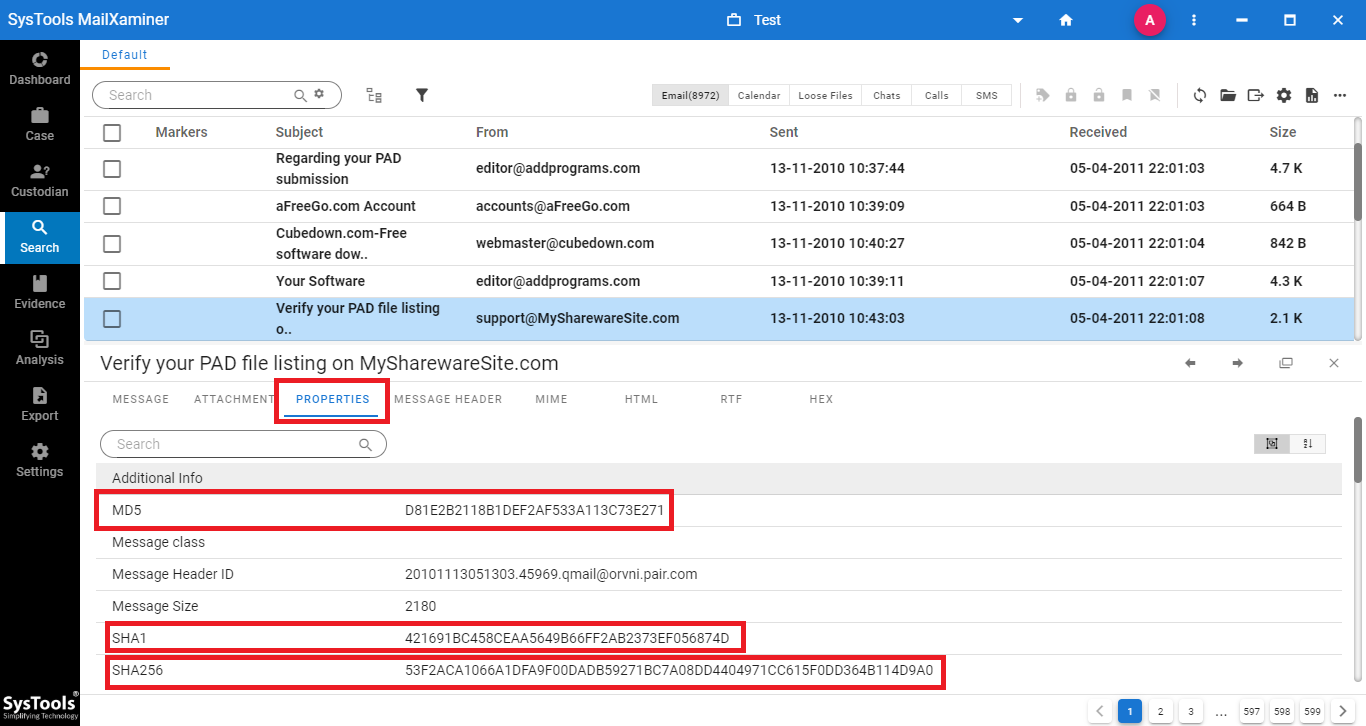
In addition to that, upon clicking on any of the emails, the software will provide a preview of that particular email in 7+ modes as shown in the below image. Moreover, under the Properties tab, investigators can also view the hash values i.e., MD5, SHA1, and SHA256. If you have selected all three hash value options, then the tool will display all the hash values for each file as shown in the below screenshot.
Concluding Lines
In today’s times, the cryptographic hash function may be pretty useful. In order to keep the security standard, it is always necessary to follow the advanced technologies, especially for security purposes.
Here, we have briefly described one of the most widely used forensics hash function algorithm. And, suggested a reliable way to calculate the multiple hash value in digital forensics using the most trusted Email Forensic Tool tool.

