Eudora Mailbox Forensic Analysis – Examine Eudora Data Storage
Eudora is an email application that was acquired by Qualcomm in 1991. It was initially available for free which was later commercialized. Eudora comes in three different modes: Sponsored, Paid, and Light. In Eudora, the availability of facilities, benefits, security level, authentication level, add-ins, etc. completely depends on the mode of application. Paid mode comprises of full features without advertisement, sponsored mode comes with full features along with sponsors’ advertising, and Light mode is an upgraded version of the free version available with minimum facilities.
Eudora application is still involved in several litigation cases regarding theft or fraud issues. Its security layers exist at every level and new challenges are faced by investigators. Eudora’s email application under investigation conceals evidence and thus investigators must have detailed knowledge about this application. This blog will shed light on the forensic aspects of the Eudora mailbox application and its architecture for further analysis.
Find Emails of Eudora for Forensic Analysis
Eudora supports both IMAP and POP mail accounts and in both cases, messages are stored into the local drive of the system. For IMAP accounts, messages are stored on the server, Eudora also downloads a copy of emails and saves it locally. Generally “Dominant” is a directory defined for an IMAP account, it is also known as top level directory which stores its mailboxes. The local storage path for POP and IMAP accounts are given below.
POP Mailboxes Path:
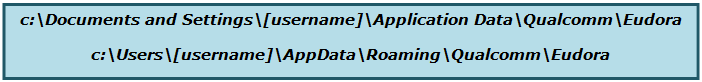
IMAP Mailboxes Path:

Quick Tip: In Eudora, it is possible to customize the data storage location while configuring the settings of the application. So, if in case, you are unable to find the Eudora data files, you can search for “eudora.ini” to get the data files. The directory which comprises this file must be the Eudora data directory.
Eudora Mailbox Forensic Analysis from Data Storage
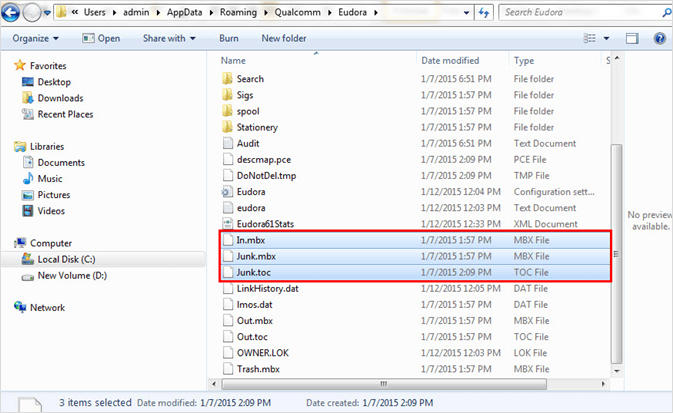
In Eudora, the emails are saved as MBOX files with .mbx file extension. It creates an individual file for each mailbox e.g. for Inbox, it creates “In.mbx file”, and for Junk, the “Junk.mbx” file is created. It must be noted that Eudora saves the attachments in separate “attach” directory. The same is done to the embedded images (images that appear within the messages). These images are stored in a separate “embedded” directory. Investigators should also follow other files available as the mailbox directories and additional file types.
Mailbox: The most important source to extract the evidence are emails stored in mailbox folders with .mbx file extension. Mailbox is a string of emails, so emails belonging to the same folder stores in the same file. The associated files with similar names but different extensions will be available as .toc, .inf, etc. Besides mailboxes, they will store in the top level Eudora directory for POP accounts, and IMAP accounts. Below are few levels available in Eudora >> IMAP >> Dominant directory.
MBX (.mbx): Eudora application’s mailbox files are saved with .mbx extension. These mailboxes don’t need to come with the same extension. File extensions depend on the system’s folders options settings. In.mbx, Trash.mbx, Out.mbx, etc. are created.
TOC (.toc): Table of Contents or TOC is created for every MBX file. There is also a nndbase.toc that comprises the content of Address Book (like nicknames).
Directories: Nested mail directories are created by Eudora to organize mailboxes. .fol extension is used to save the directories for POP accounts. One or more mailboxes may be nested to such type of directory. No such extension (.fol) there for IMAP accounts.
Nicknames: Email address of users and related nicknames are stored in the folder named “nndbase”. Being a part of the Eudora address book, it is available in the top Eudora directory that can also be found in a “Nickname” subdirectory. Outbox messages might show nicknames without the email ID in “To” field.
Attachments: Email attachments are stored in separate “attach” directory. POP accounts have one “attach” directory at the top level. IMAP accounts have “attach” directory nested in associated mailbox directory. In the Eudora application, email messages are marked with the path of the location of its associated attachment file.
Embedded Files: These files include images that are part of messages and available within the message. All of these files are stored in the “embedded” folder which belongs to top-level Eudora directory.
Note: While investigation, only storage files are not important, it is also important to analyze other directory or setting files to interrogate the settings which were applied by the user in his Eudora application. It also helps to trace out the deleted data or re-create files for its examination through various other tools.
Eudora Email Application Settings Files
There is a possibility that the investigator does not get enough time to recreate the Eudora environment by copying the storage and setting files in other machines. In such urgent needs, it is better to examine the available settings and storage files. The below section will enlighten the forensic significance of other Eudora email application setting files.
eudora.ini: The file “eudora.ini” is an important part of Eudora application data as it comprises of all the settings saved by the user in the application. These settings are easy to read and change by opening the file in Notepad. To reset all the settings, the user can delete the settings.
deudora.ini: Online mail settings are stored in the deudora.ini file along with the registration information which retains Eudora application in paid mode.
filters.pce: Names and extensions for Eudora filters are stored in Filters Folder where full information for the filters is available.
Security Layers & Authentication for Emails
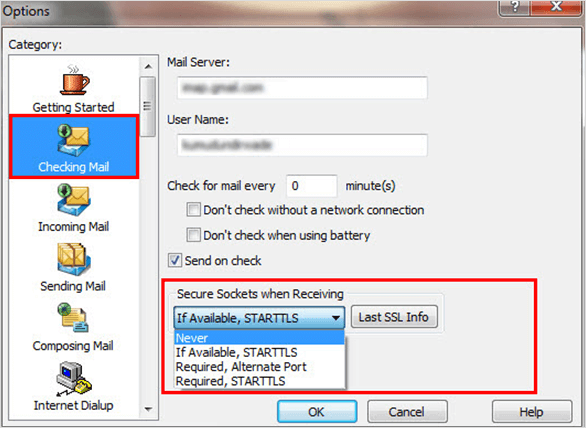
Secure Sockets (SSL) – This security protocol is supported by Eudora for transferring information and available in Paid and Sponsored Eudora modes only.
Secure Sockets while Sending/Receiving: It requires STARTTLS forWindows, and TLS for Mac to secure the sockets. Eudora has improved the handling of SSL (Secure Socket Layers). It also allows authenticating the server while sending or receiving emails.
Authentication: Eudora provides S/MIME authentication that stands for Secure/Multipurpose Internet Mail Extension. It allows us to ensure the email recipients that email is actually sent by you. It is an internet standard for public-key encryption and signing the MIME data or email message data.
Other Security Options for Eudora Mailbox Forensic Analysis
- Bayesian Filtering of Spam was added with SpamWatch in Eudora (6.0.1).
- A ScamWatch feature was added in Eudora (6.2) which flags doubtful or malicious links within emails for better URL protection preventing email phishing. It is available only for Paid mode.
- Ultra-fast Search to trace any email with single or multiple measures was integrated with Eudora (7.0).
- Protocols Support: POP3, SMTP, and IMAP protocols are supported by Eudora.
Conclusion
To initiate a detailed analysis of the Eudora application, it is necessary to know where to start. The availability of storage and setting files can resolve many tasks pertaining to Eudora’s investigation. To perform thorough Eudora mailbox forensic analysis in bulk, professional applications like MailXaminer Email Forensics Software. are authentic ways. Such tools represent the emails in an organized pattern which makes it easy for investigators to carve out necessary artifacts from the collected artifacts.

