DreamMail Forensics – Proven Tactics for Email Investigation

Wondering to know the perfect solution to perform DreamMail forensics? Then, check out this blog to know the finest solution to easily perform forensic analysis of DreamMail files.
DreamMail is an email client, from the DreamSoftware Studio company. It’s purpose is to be capable of managing multiple email accounts. It supports protocols like SMTP, POP3, eSMTP, and SSL.
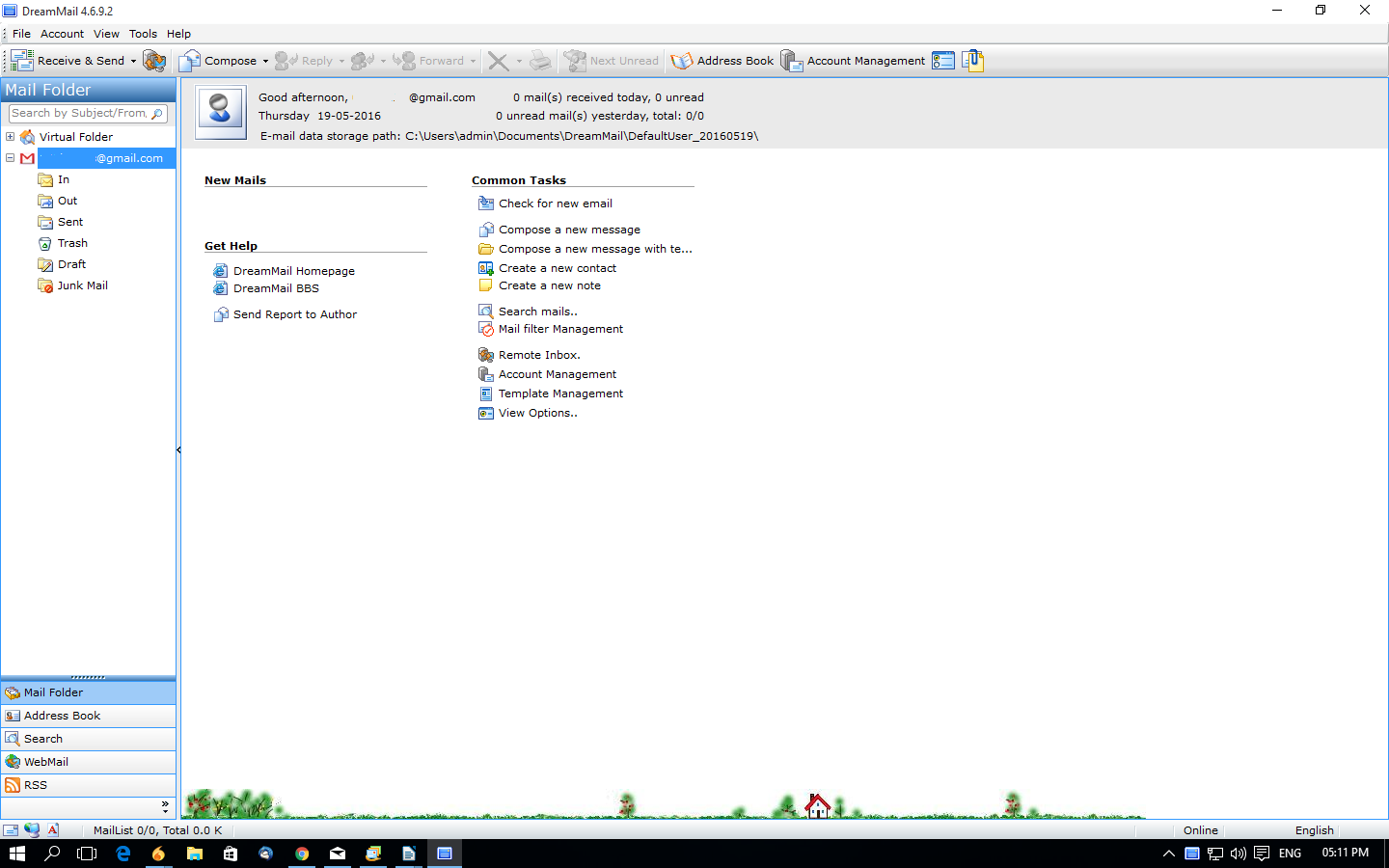
Figure 1: DreamMail Email Client
There are several advanced features such as spam filtration for files with a malware infection, and message rules in managed list of whitelists and blacklists. It has also compressing feature which allow you to compress email data to save space in the hard disk drive.
DreamMail is loaded with many other features in which it auto-searches POP3 and SMTP servers for connectivity. You can also create short notes, edit received message and send message anonymously using DreamMail.
DreamMail come up with bulk set of features that lets users to backup emails and contacts in DMD file format. It allows to export emails in multiple file formats EML, HTML, Text and MHT. It also allows to import the emails from EML file, DMD file and Outlook Express Account.
How to Examine DreamMail Emails for Forensic Purpose?
There has been an increase in the number of cybercrime cases wherein fraudsters make use of DreamMail application to conduct crimes. However, the main question is that how to get access of DreamMail emails for searching potential artefacts. It is really important to find the user data storage location of DreamMail. However, there is no such location to find the user data from DreamMail. Therefore, the investigating officers can make searches in DefaultUser folder from the computer.
User Data Folder
Note: Folder location depends on the user who is using DreamMail because it allow users to store data at any location in computer.
As you can see in the below image, that all files & folders inside DefaultUser folder are displayed. You can see two different files with the name of BlackList.txt and WhiteList.txt. Both files work for spam filtering, all spam related email IDs are listed in BlackList.txt file.
Figure 2: Search User Data
Investigators have to take DefaultUser folder with all user data for investigation purpose. However, it is not always a good idea to take User data in a folder. As there might be a probability of data corruption in folders. Therefore, it is suggested to store data into a TAR file and then take it into any removable device for investigation.
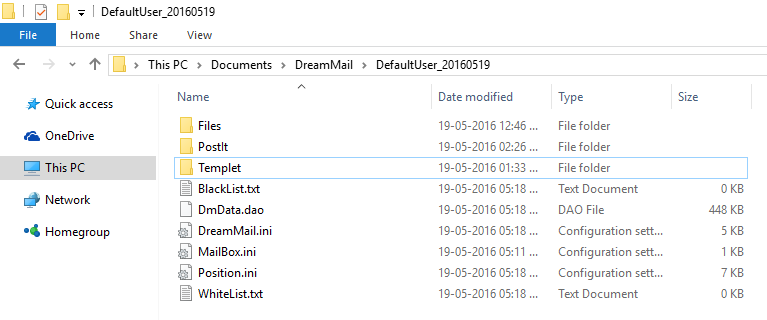
Figure 3: User Data Folder
Suggested Tip:
MailXaminer Email Examiner Software is a one-stop solution to examine and analyze suspected email data files effortlessly. The software offers some advanced features that allow investigators to analyze files from 20+ email file formats. Besides this, it provides multiple advanced features such analytics option, which includes link analysis, timeline analysis, word cloud and entity analysis.
Some Remarkable Features by MailXaminer Software
Here are some additional features of the futuristic email examination software.
- Supports email data files from both desktop & web email client
- Multiple search options such as General, Fuzzy, Proximity, etc.
- Avail OCR technology to carve contents from uneditable files
- Geolocation image mapping to find image’s geographical location details
- Instantly analyze all the data from Skype DB file
- Analysis of obscene images via advanced image analysis feature
The Final Note
DreamMail is a perfect email application for those who want to use multiple email accounts on a single platform. Evidently, DreamMail keeps backup of emails and other data items in DMD file format. Using MailXaminer, one can easily search and analyze suspected email files wherein it instantly finds out the potential evidence in a hassle-free way.

