What is Cloud Forensics? Top Detailed 2025 Guide
Whenever we talk about digital forensic investigation techniques, most people usually think about traditional investigations. In this investigation technique, experts examine physical devices like computers or smartphones.
Nowadays, Cloud forensics has emerged as a vital field for investigating digital crimes. What is cloud forensics? In simple terms, it’s a branch of digital forensics that focuses on the examination of data stored and processed in cloud computing environments.
Cloud-based forensics has become an essential tool for cybersecurity experts and law enforcement alike. This is so because more businesses and individuals are relying on cloud services like Amazon Web Services (AWS), Microsoft Azure, or Google Cloud. When any cybercrime or social networking security incident occurs, data does not just reside on a single machine but needs to be spread across various locations and servers globally. And from here, cloud forensics comes into play. It enables investigators to access, collect, preserve, validate, identify, interpret, and analyze digital evidence hosted in the cloud service environment.
Cloud forensics requires some sort of specific tools and knowledge to extract the data remotely. That means the investigator needs to work within the confines of cloud provider agreements, data encryption, and sometimes even international law to gather various information, like PII data. The complexity of cloud forensics tools came from handling multi-tenant environments and encrypted data. This adds an extra layer of difficulty.
The rise of cloud services presents a critical question of how forensic professionals collect and analyze cloud data to preserve the integrity of the evidence. Cloud forensics demystified is an essential area of study today for everyone who is somewhere around the other is involved in digital forensics. This combines traditional techniques with the latest cloud-based techniques the latest cloud-based technologies to address the unique challenges posed by modern data storage.
Key Objectives of Cloud Forensics
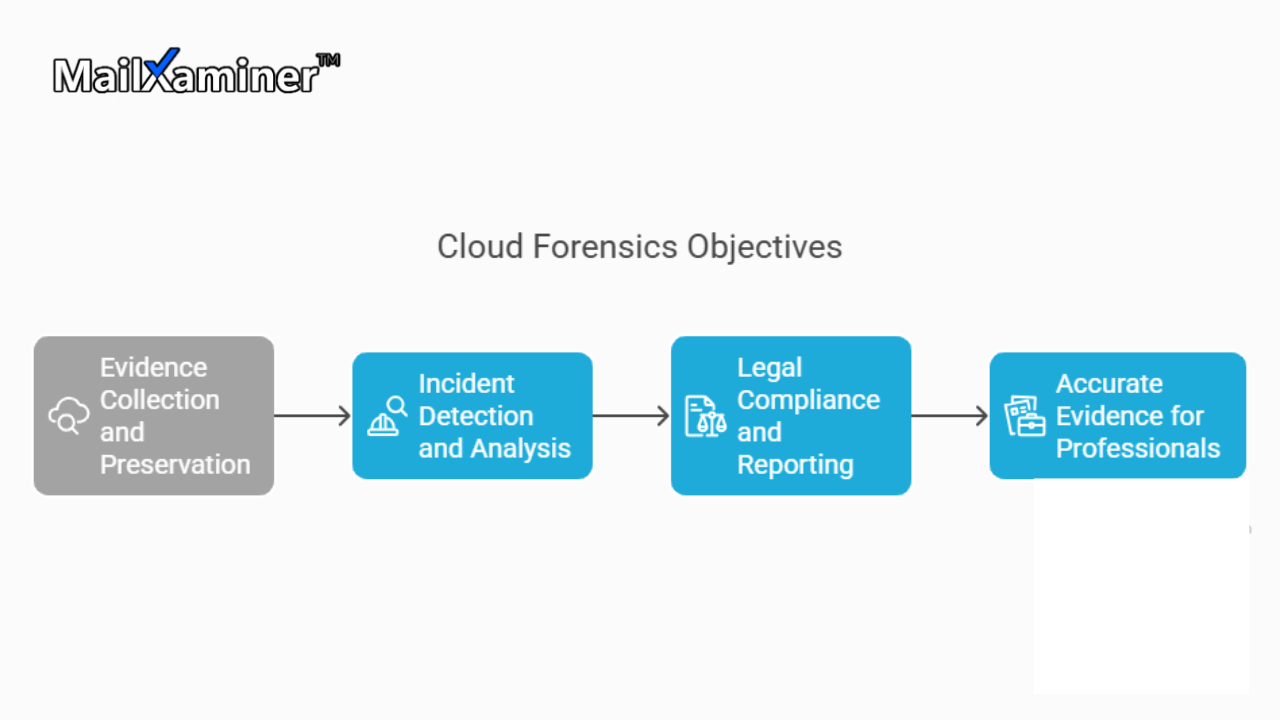
It becomes crucial to understand the key objectives of cloud computing forensics. It is not the correct data, but the right procedures are followed to maintain the integrity and admissibility of evidence.
Let’s Check Out Some Cloud Forensics Challenges
While dealing with the subjects related to cloud forensic investigation, there are a plethora of challenges that occur frequently. Some of the possible challenges may include:
- Log files cannot be accessed by cloud customers.
- No agreements between the Cloud Service provider and the customer related to the segregation of responsibilities in the scenarios of the investigation.
- The cloud customer might not have to complete access to their data to collect valid data if it is under investigation.
- In Cloud computing, data is stored in multiple machines in different geographic locations. If the data is deleted, then it becomes a challenging task to recover the deleted data, identify its owner, and make use of the data for the event reconstruction.
- Fragmented data and artifacts are present whose metadata has been altered.
Issue Related to Conducting Digital Forensic Investigations In the Cloud
In this section, some of the additional cloud forensics challenges and issues are described, which can affect the quality of the evidence retrieved in the cloud. Moreover, it can also affect the credibility and admissibility of the recovered artifacts in the court of law.
- Multi-Tenancy
Multi-tenancy permits various clients to share a physical server and use services offered by the common cloud computing hardware and software simultaneously. In some scenarios, multi-tenant infrastructures involve the sharing of resources is extensive and involves multiple potentially vulnerable interfaces. The cloud service provider is often not willing to give access to shared memory to the investigator, as it may contain data belonging to other customers. If such data is released, then it could violate confidentiality and privacy agreements.
- Data Provenance
The ownership and process history of data objects is recorded in Data Provenance, which is important for a cloud forensic investigation. The degree to which data provenance can be implemented in a cloud environment depends on the type of cloud model.
For Example, the ancestry of the data artifact in the case of SaaS implementation may be difficult to trace. This is because the service provider would not give access to the application and system log files to the investigator.
- Multi-Jurisdictional Issues
Data stored in a cloud service environment is often distributed over several locations to promote fault tolerance and efficiency of access. However, data distribution raises the issue of jurisdiction, which can present problems in legal proceedings. The situation becomes worse when the data resides in another country. Confidentiality and privacy laws differ from one country to another.
Best Solution to Perform Cloud Forensics
There are many unresolved problems and challenges are exist in the cloud forensic investigation process. Let us discuss the one-stop solution that will help enhance cloud-based forensics investigations.
When it comes to cloud forensics, MailXmainer is the best software that helps you to investigate the cloud data as per your preferences. This can make your tasks smoother and effective with today’s growing complexity of cloud environments. It is the best email forensics software, which is especially designed to effectively collect, preserve, and analyze cloud digital evidence.
Cloud forensic investigation process
Cloud forensic investigation requires a methodical approach, especially when dealing with the complex nature of cloud environments. Through this software, you will be able to perform an advanced level of cloud forensics. Thinking about how? Then let’s understand without any further ado.
- Simply first set up the software on your system and provide login credentials.
- Then create a new case and save the files.
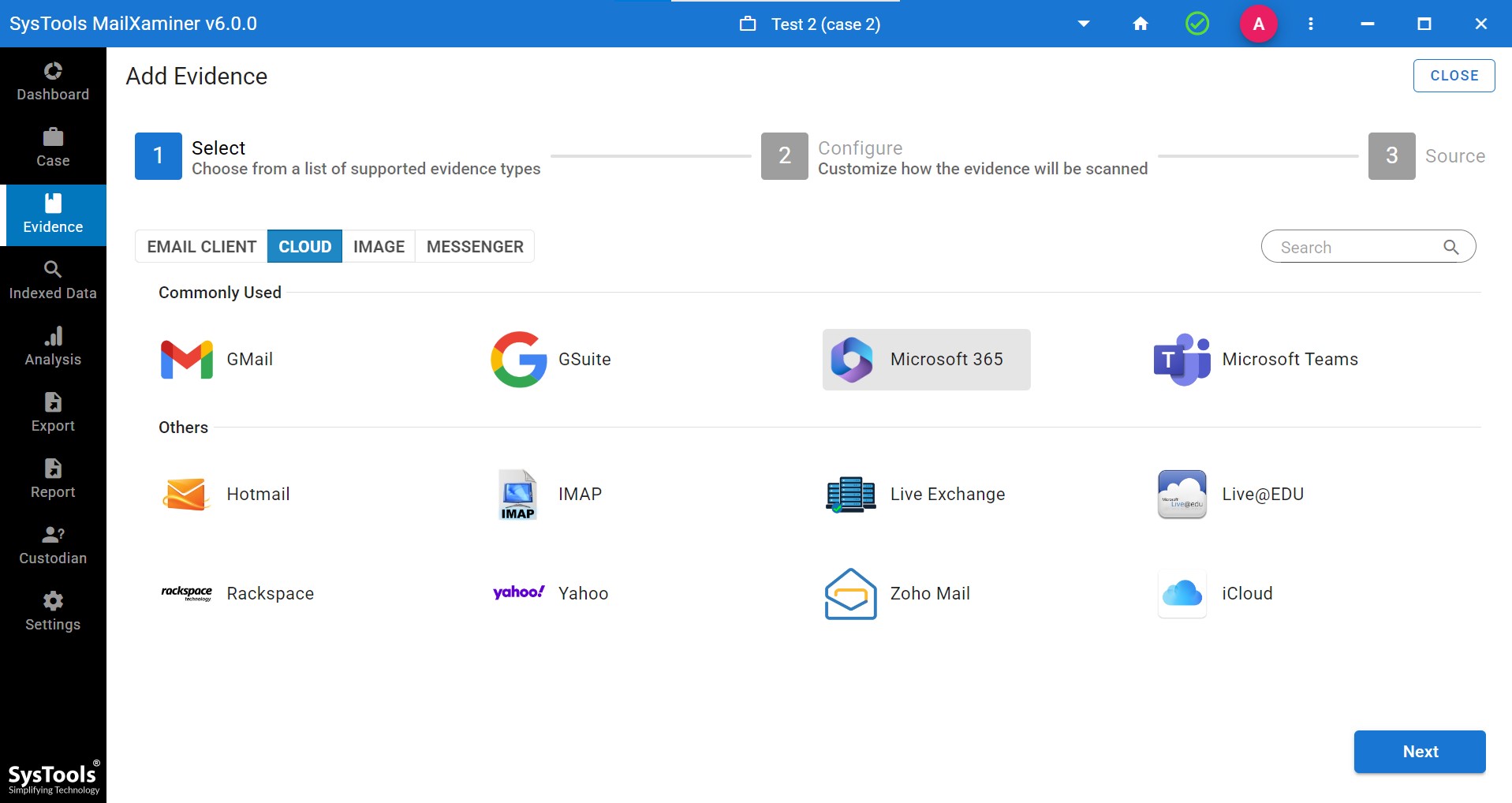
- Now, to add a file, select the Cloud option. Select any cloud platform as per your preference. The software will provide you with a wide range of 12 cloud platform options.
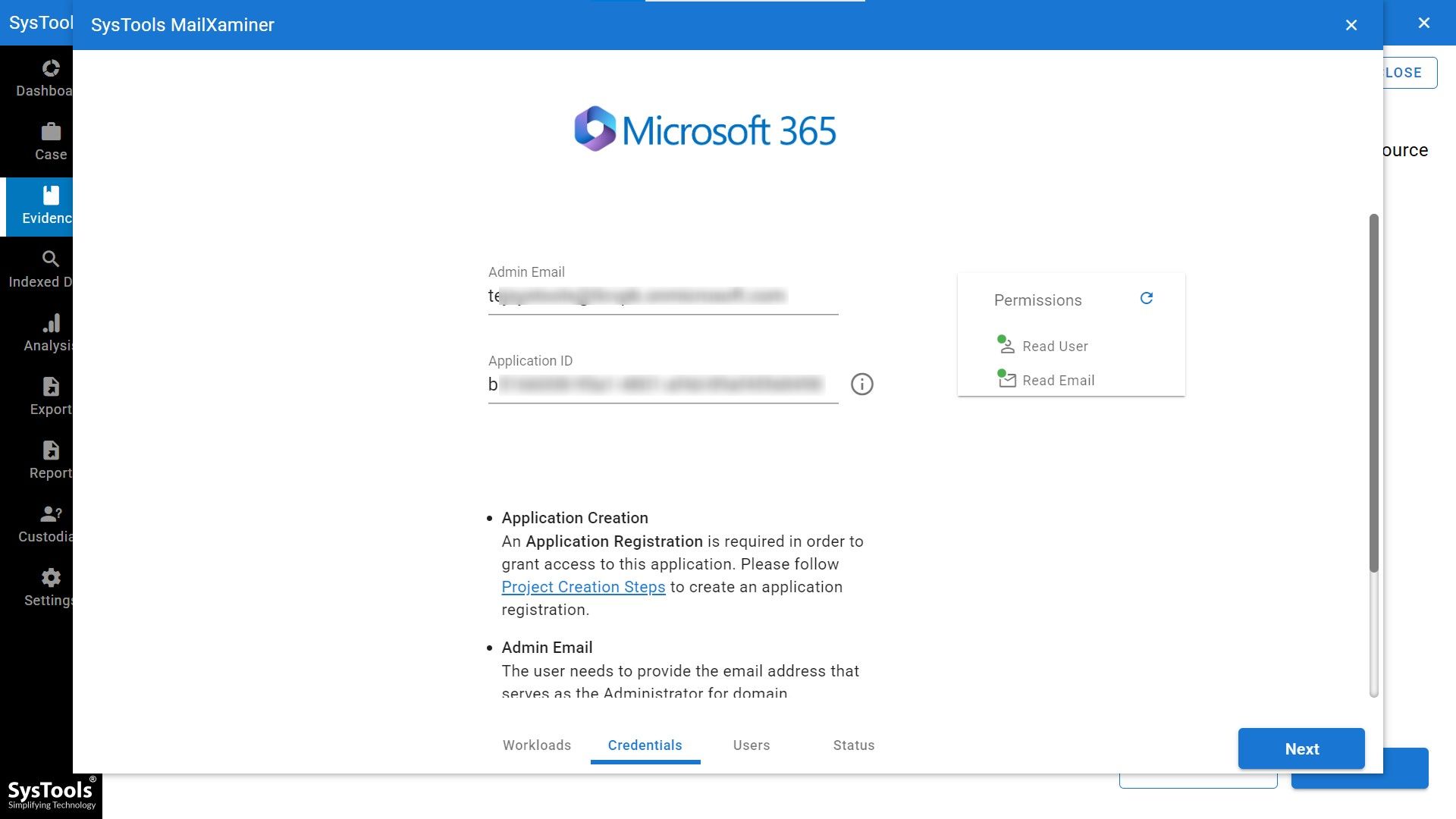
- Then, add the details of the domain and credentials. [Here we have taken Office 365 as a cloud platform]
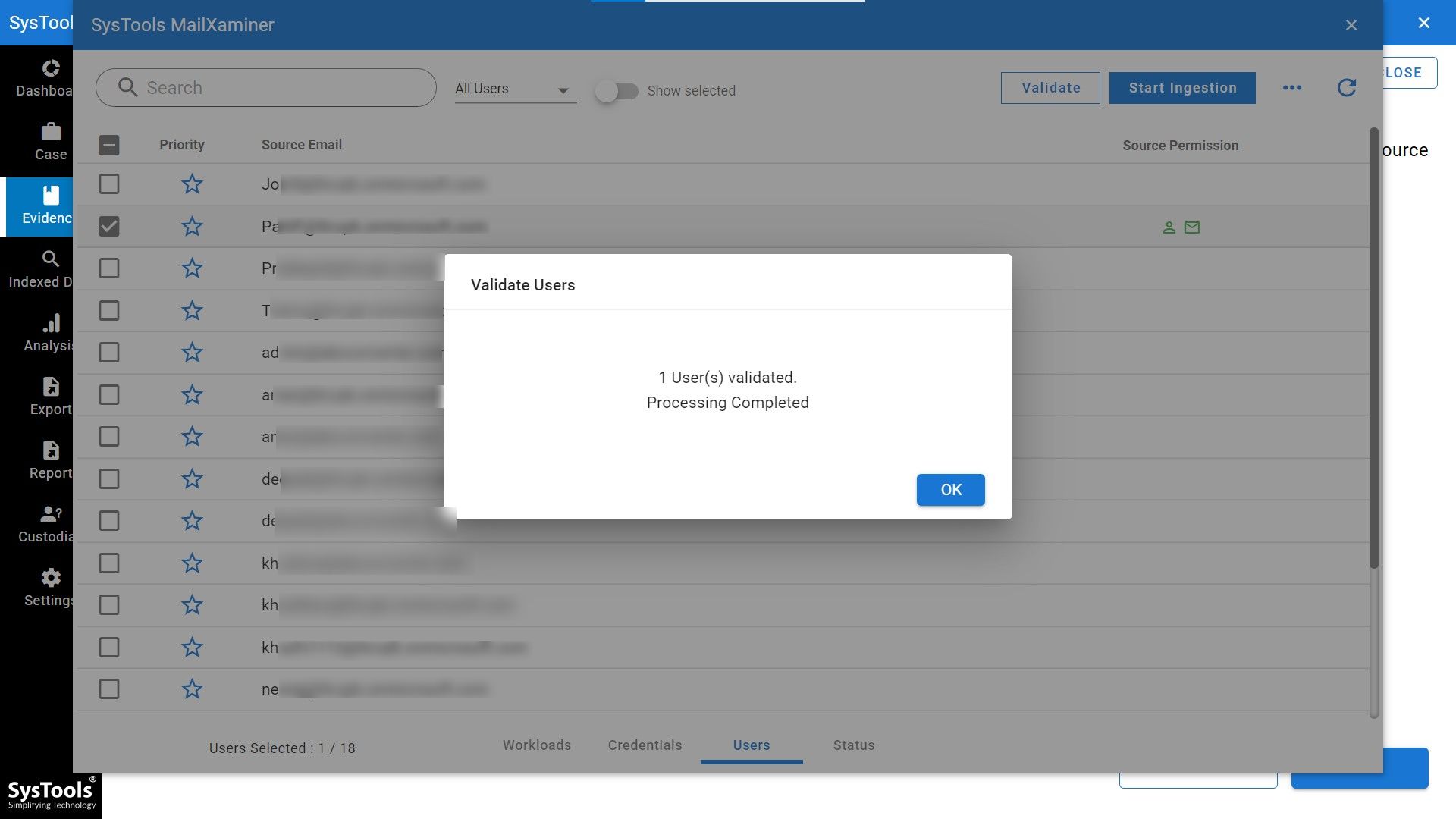
- All the emails have been fetched by the software. Just select the emails and validate to proceed.
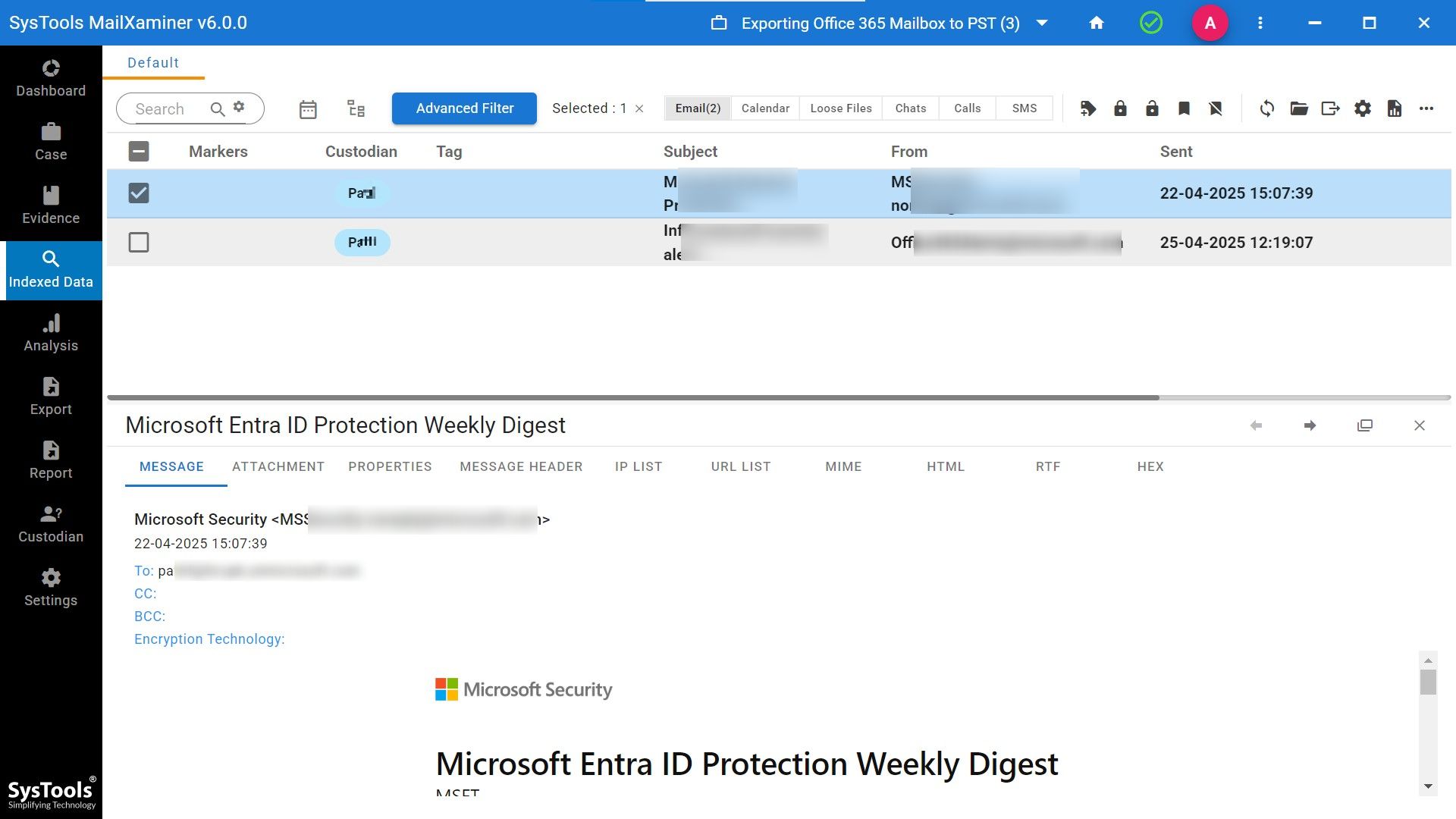
- Now you can simply analyze cloud data by various features provided by the software.
- Also, you will be getting different analysis features, like link analysis to track the communications.
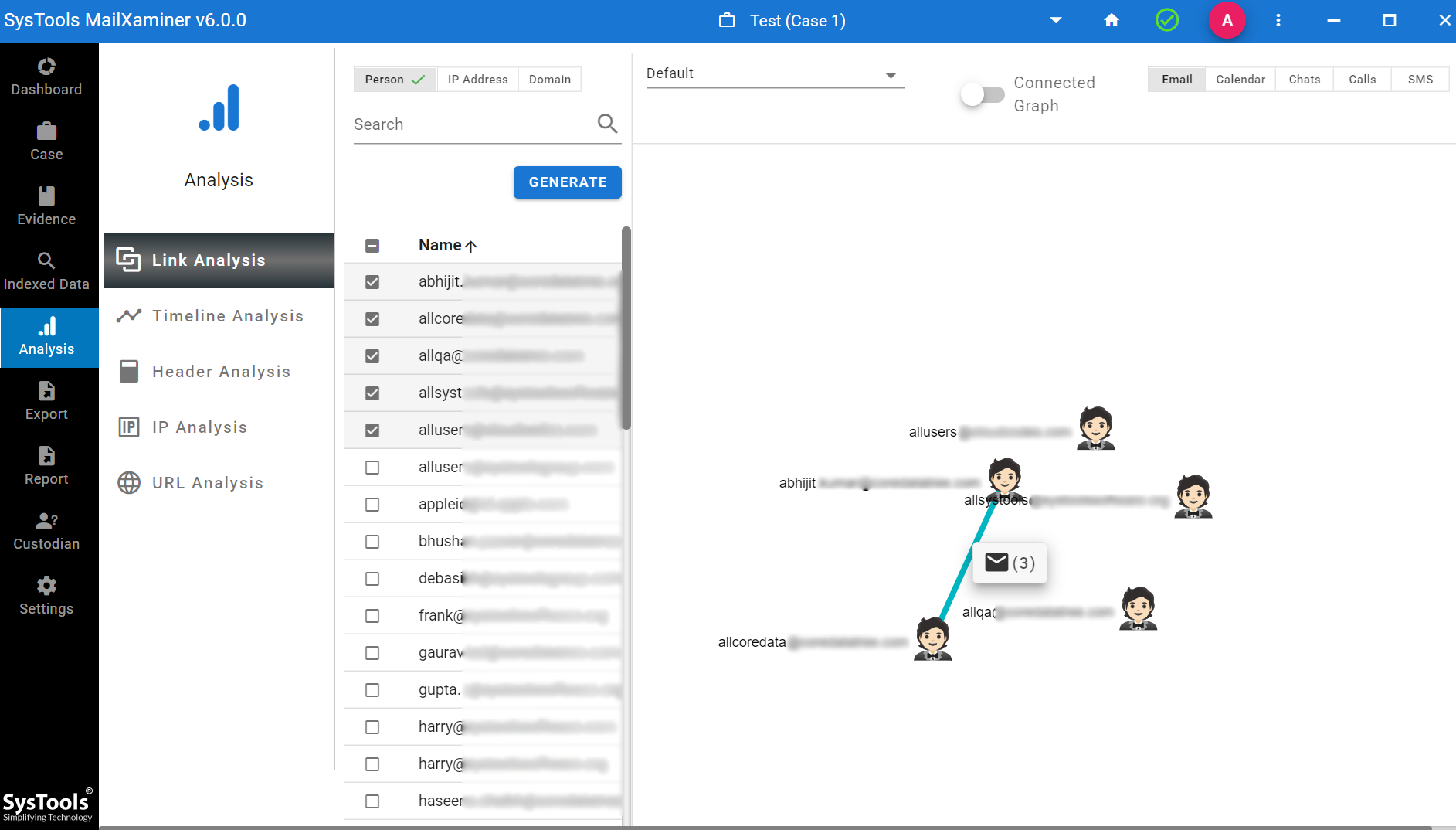
The use of timeline analysis for identifying the time gaps in the email conversations.
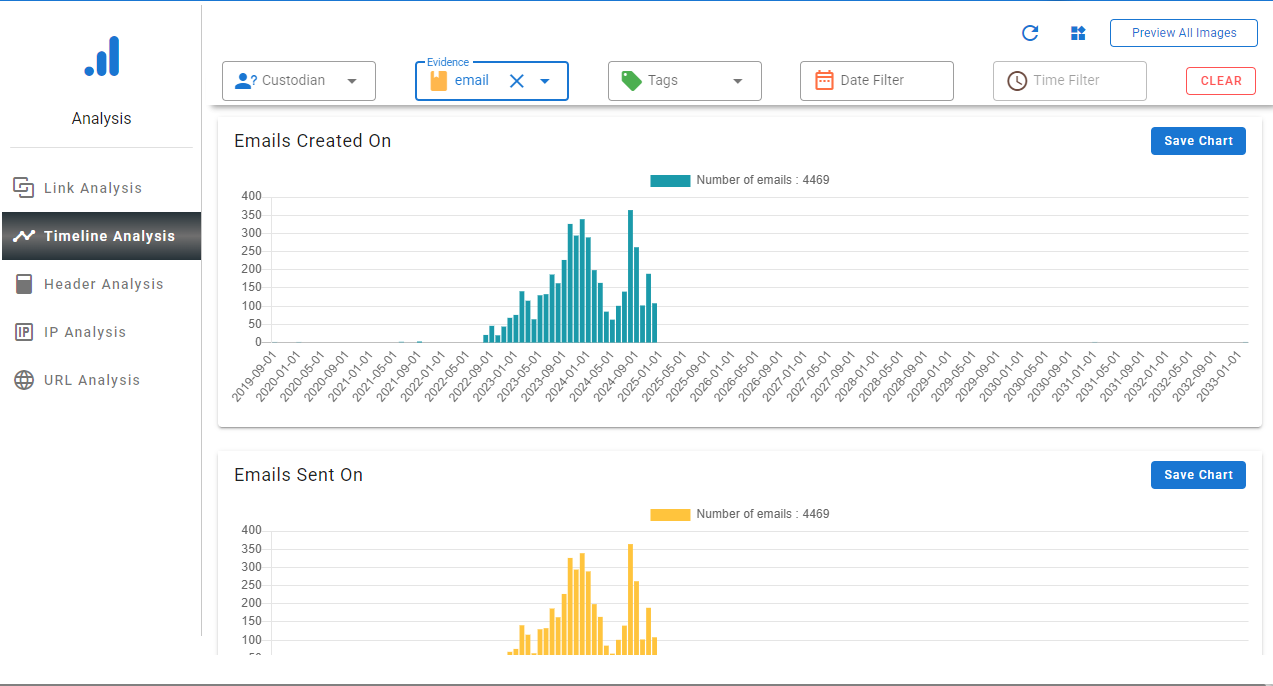
- After performing the complete analysis procedure, you will also get the option to export the report.
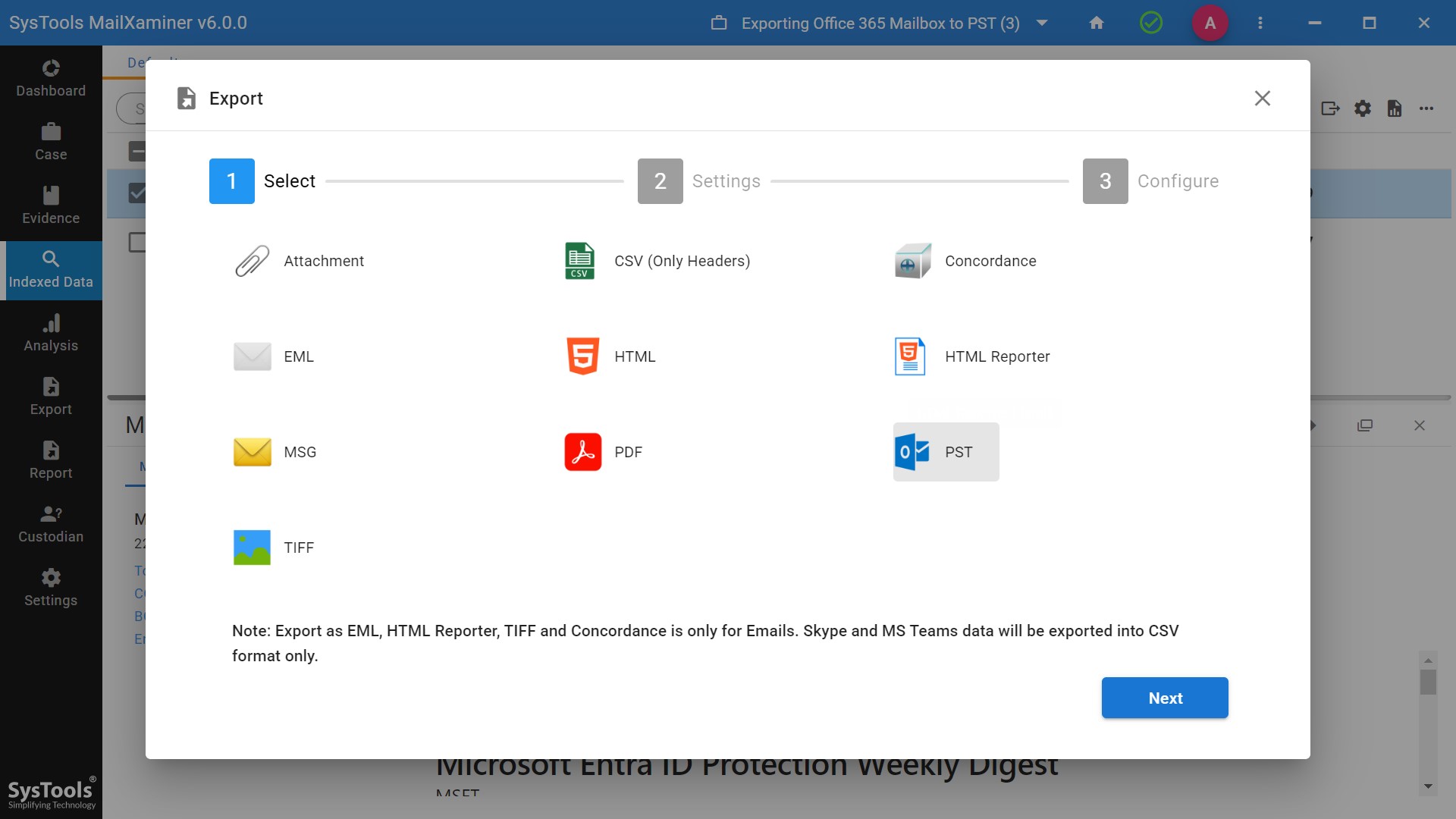
Lastly, you can see the whole export Office 365 mailbox to PST process so smoothly without any delay. A complete report of the process will also be provided to you in various file format options. It can be used for further investigation proceedings, and it can also be admissible in court.
Final Words
The rapid growth in the number of cloud storage users leads to an automatic increase in the importance of the cloud forensic investigation. There are several challenges are occur while conducting the investigation. These cloud forensics challenges are occurring due to the highly dynamic, distributed, multi-jurisdictional, and multi-tenant nature of the cloud environments. To deal with all the issues, one can opt for solutions such as cloud forensic Tools Testing, Transparency of Cloud Services and Data, Service Level Agreement, Forensic-as-a-Service, etc., to enable high-quality forensic investigation in the cloud service environment.