New Insight To Claws Mail Via Claws Mail Forensics

Claws Mail is a free, open source email and news client based on GTK+. The email client supports Windows as well as Unix like operating systems like Linux, Solaris and Mac. In Windows operating system it is included with an encryption suite named Gpg4win. Formerly referred as Sylpheed-Claws, Claws mail started as a development version of Sylpheed in April 2001 so as to test and debug the new features. But in August 2005, it evolved into a completely separate program having bifurcated from Sylpheed-Claws. Although it does not have many inbuilt features, but the plugins that are provided by default extends the functioning of Claws Mail.
Storage Database Of Claws Mail
Claws Mail stores its database in MH and Mbox files. The location of these files is:
C: Drive\Users\Admin\AppData\Roaming\Claws Mail\Mail
Although MH files are the default storage file format of Claws mail, Mbox files are also supported by it.
- MH Files
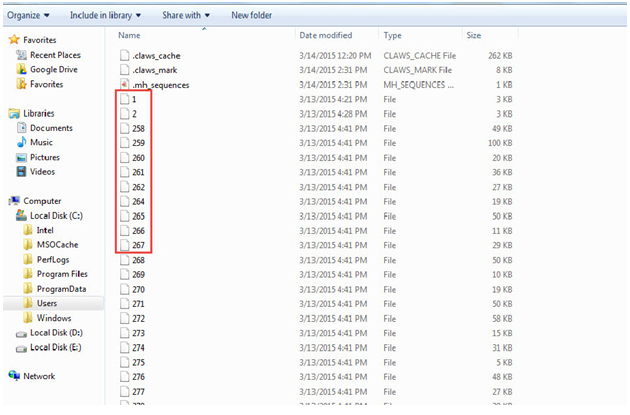
MH files are the default files used by Claws mail. In MH files each message is stored in a single file and directories of the host file. All the mail folders present in Claws Mail like inbox, sent items, trash, etc. are stored in different folders in one main folder.
In each folder each email message is stored in an individual file, with a positive integer as the name of each file. All the new messages are added to the end of the messages already stored in the folder. Therefore, if new messages are to be searched, the user will have to search for them at the end of the message list.MH mailboxes also support sequences which are stored in a file named .mh_sequences in each MH folder. These show the name of emails that have been unread. If there are a large number of unread messages, then the range of the unread messages is shown.
- Mbox Files
Claws Mails does not create Mbox files as its storage files but do support Mbox files. To be more precise the Mbox format supported by Claws is MBOXRD.The Mbox files in Claws mail are imported in it with the help of Import MBOX files option. All the email messages in Mbox format are imported and are then transformed into MH format.Also Claws mail gives an option to export the MH files as Mbox files so that the files can turn accessible in Mbox supporting email clients.
Structure Of Mail Folder In Claws Mail
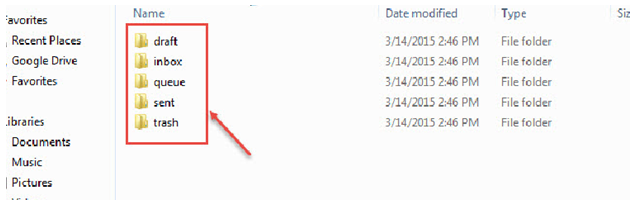
The storage database of Claws Mail shows all the folders separately. The messages are stored in MH format. The files are not easily accessible and can only be read with the help of any file editor.
- Drafts
It stores all the messages that are incomplete and the user have saved for completing in future. This folder comprises of all the emails in drafts and also the three hidden files i.e. .claws_mark, .claws_cache and .mh_sequences.
- Inbox
This folder contains all the received messages as well as imported messages of Mbox format. From an investigation point of view, this is the most important folder as it can reveal all the messages that the culprit has received from his partners indulged in the same crime.This folder also comprises of all the emails s and also the three hidden files i.e. .claws_mark, .claws_cache and .mh_sequences.
- Queue
It stores the messages that were completed but not sent. In Claws when the user choses Send later option, the message is saved in trash folder. This can reveal all the messages which the user had intended to send in future.
- Sent
This folder stores sent mails and reveals all the messages that the culprit has sent to other users while carrying out the cybercrime.
- Trash
Trash folder stores all the mails which have been marked as trash in the Claws mail. Also, when the user uses Bsfilter plugin, all the messages filtered by the plugin are stored in this trash folder. Also if a user marks an email as trash, the email will be stored in the trash folder.
How Are Mbox Files Recognized In Claws Mail?
Mbox files imported in Claws mail from all the email clients that support Mbox files like Mozilla Thunderbird, Eudora, etc.In case a criminal has imported some Mbox files from another email client so as to initiate a crime using the imported mails, the Mbox files can be accessed in Claws mail. The imported Mbox files get converted into the MH format and it becomes difficult to differentiate between the imported Mbox files and the existing MH files. a forensic investigator can analyze each mail message by checking the header structure of all the mails by enabling the Show All Headers option in Claws Mail. But in case the email client cannot be accessed, with the help of the Hex Editor, the mail headers can be analyzed.
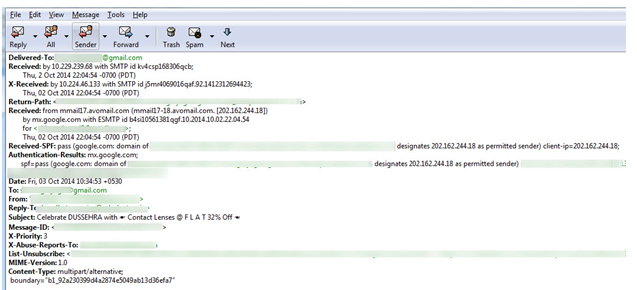
The MH files header is shown below as by selecting Show All Headers option in Claws Mail. This is identified as in Claws Mail, the header of a mail starts with Delivered To.
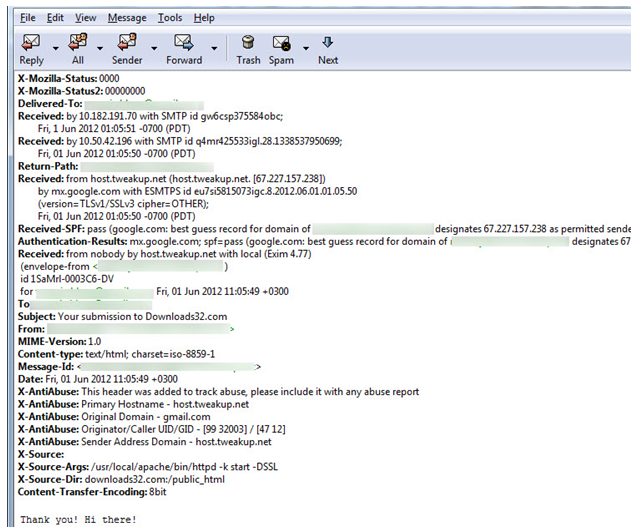
Mbox message is identified with the help of the header as the initial entries in the header signify the same. As shown in the following image, the message belongs to Mozilla Thunderbird. This is identified by the initial entries in the header-X-Mozilla-status.In a similar manner an investigator can easily identify the mails that were created in Claws Mail and the Mbox files that were imported.
Conclusion
Carrying out forensic analysis of Claws mail can become ineffective and may not give desired results if each and every mail is analyzed manually. It will consume loads of time which proves to be a drawback for any investigation process. Therefore, forensics can be made easier and effective by deploying professional tools like MailXaminer. It is an eDiscovery tool that efficiently examines header of each mail in different views like Hex, RTF, MIME and many more. Also the tool gives you an option of link analysis by which you can see a graphical link between the culprit and the contacts he has sent or received mails from. By clicking the link between the two contacts, all the mails exchanged between the two can be seen.