The Bat! — Email Forensics

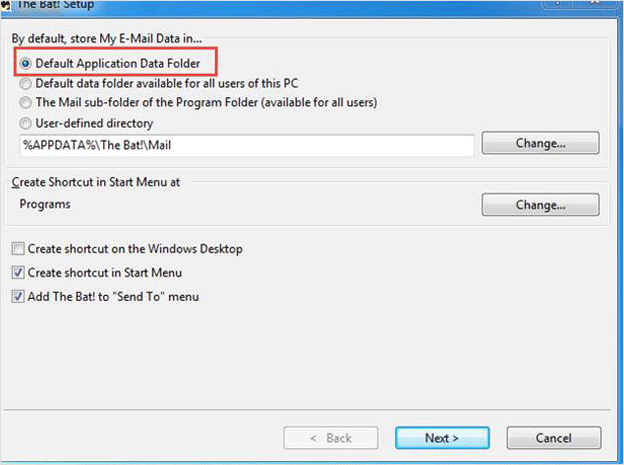
The Bat! email-client is considered as one of the most secured email client designed for Windows OS. It comes as a trial-ware software which is provided to users for a certain time and then after that a user has to buy the license for its continued services. On installing The Bat application on a system and successfully synchronizing with any of web-based email clients. A user can locate its synchronized messages from the given path : – C:\Users\<user name>\AppData\Roaming\The Bat!\Mail\profile folder
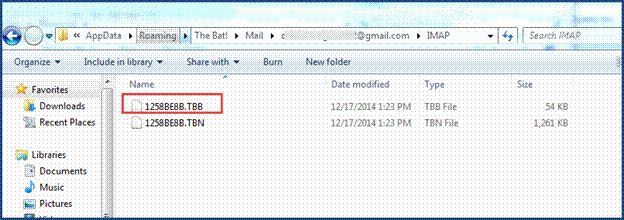
Further, a user can locate all its messages from the synchronized IMAP folder which stores all the messages in .tbb or in .tbn file formats. The Bat! uses TBB file format to save its messages.
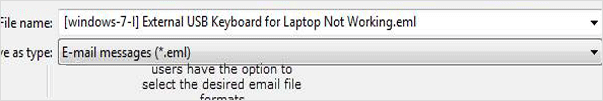
However, a user has the option to save TBB messages of The Bat in other file formats such as EML, MSG, MBOX, and HTML. This feature facilitates users to export TBB files in other supporting email-clients, thus facilitating the forensic investigators too for The Bat email forensic analysis.
Some TBB Related File Extensions
Manipulation of Messages in The Bat Client – The Bat Mailbox Analysis
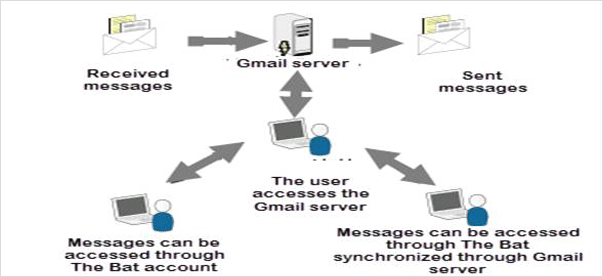
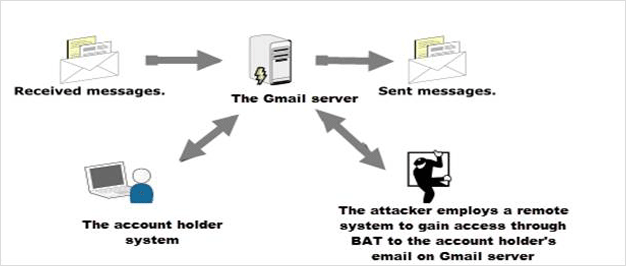
Here, a remote attack has been illustrated where the attacker has the email account holder’s account credentials. The attacker is able to access the Gmail server by synchronizing through The Bat email client and is able to forge and embed messages.
Here, it has been shown that how The Bat email client on a user’ machine synchronizes with the Gmail account placed on the Gmail server. The Gmail account is added to The Bat using the user credentials associated with that specific account. The account of The Bat is accessed on the user’s system and a message is chosen for forgery is simply dragged from The BAT inbox by the employing the drop & drag feature provided to user and is positioned on the desktop. The original message that is present in the inbox is deleted to hide the falsification. The message which is extracted is again structured by using a text editor such as Notepad, then saved and dragged back into the inbox of The Bat. The account is then again synchronized with the Gmail server.
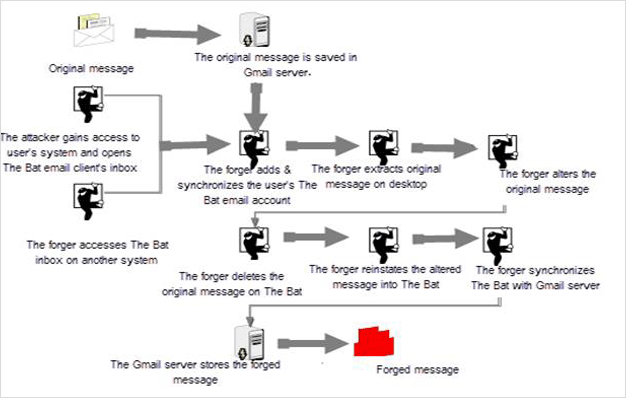
On the occasion, when a forger takes hold of the user’s system and commences an invasion from another machine, the bat email header analysis have proved that the fraudulent has the capability to access user’s account via The Bat email client manipulation either on user’s system or on the forger’s system .The method of email message altering or intruding and interjection is illustrated below in the figure
In the first two cases, it has been shown clearly how tampering are subjected to the user’s system and the Gmail server. In the extrinsic attack, confirmation of forgery is located on the attacker‘s machine and on the Gmail server, server oriented users relies on suitable server logs and retention time of the logs.
Evidence of Tampered Messages from Log Records
The forensic investigator can make use of a number of techniques to determine the factualness of the messages in The Bat email client’s inbox and obtain substantial proof related to the forgery of email messages. In any forensic investigation, it often becomes necessary to detect the source and the path through which the message has traversed. System logs are referred to determine the path and the address of the email message. Before we move to the process of how to analyze the logs of email-server, let’s first know the importance of log records.
Importance of Log Records
Log records prove to be beneficial because they maintain the account of commands or other data communicated through the web. For example, log records can be indicative of the locations visited on the internet by showing all the activities of a user on its system. Log records may bring to light some identifiable data, such as the details of operating system and the web browser which were used by the system while initiating the request.
In addition to keeping a track of internet activity, log records are also important as they provide necessary evidences related to intrusion and botnet cases. Log records can exhibit connections to systems which are managing the botnet.
Using Logs to Analyze Messages of The Bat!
The routers and firewalls through which an email message comes across provide a valuable authentification of email-server and the path details which are present in the head of the email message through their log information. During The Bat mailbox analysis, as we know that, it is quite possible to tamper the message head of an email message but it is next to impossible to vitiate the email servers and network devices which are involved during the transmission of a message from source to recipient’s system.
By conjoining network and system logs from the sender, receiver, interposed devices, and the email servers involved in the path of the message, an investigator can authenticate the validity of data present in the email of message of The Bat. If the forensic examiner notices any kind of dissimilarities across machines and the system logs, then there is a good probability that the message heade has been falsified.
How to Validate Information from Network Devices Logs
By thoroughly examining the routers and firewall logs involved in transmission of a message from source to destination, it is quite possible to determine the IP address which is present in message head of an email. The routers and firewall can be established to trace and log egress and ingress network traffic while the message moves through them. While carrying out this process, routers, and firewalls brings forth logs files. These log files can determine the source address and recipient address of the server which was employed to send messages.
The above-mentioned process illustrates a method of how to obtain evidence regarding the tampered messages of The Bat by analyzing the system and network logs appropriately. Often forensic investigators require third-party tools to analyze the forged messages. One such tool which suitably helps to examine message details of The Bat! is MailXaminer. It also provides a facility to analyze the attachments present in the email messages.