Email Evidence in Court can Help You WIN Next Case!

Can I win my client’s next case by finding evidence from popular e-mail services like Gmail, Hotmail, AOL, Yahoo, Comcast or others and whether email admissible as electronic evidence in court?
The answer is YES!
With the innovation in computer and digital media email started to play a key evidential role in our lives. Recent investigation proves that over 150.9 billion emails are exchanged per year, being the most fruitful source of communication both in our business as well as personal lives. But this extreme amount of dependency on email transactions also happened to open the door for criminals to perform their illegitimate activities on confidential data lying on the web in the form of electronic messages. In this blog we are going to discuss how we can extract and use email evidence in court during email investigation.
Can an Email or Electronic Document be Used as Evidence in Court?
Before answering this question first we can take a look into what is evidence and what it includes. Evidence collection of statements that court permits to made before witness by analysing the collected information based on the relation of the facts under inquiry. Generally, evidence contains all documents including the electronic records.
That is we can use email as evidence in court. An email is a form of documentary evidence that can be submitted in the court as in the same way the other documentary evidence are submitting during court proceedings. Even though if you are thinking the email message is a smoking gun in your case, but it is not easy to present electronic evidence in court. The email evidence should be authenticated and protected in a way that it will not be falsified in anyway. Because the reliability of the message will be subjected to critical observation or examination.

How to Make Email Admissible in Court?
1) Hard copy creation
Generating digital backup and hard copy of
2) Authentication
When you present electronic evidence in court, the court often
- Email sender or receiver can testify to authenticate the email.
- Business Signature block in the email consider as the self authenticated
- If the email address contains company and employe name it is enough to prove it send from a valid entity.
3) Practical steps
To avoid the issues related to the integrity and reliability and present email evidence in court admissible form there is a lot of practical steps are available. Some of them are:
- Control the use of email which is under examination to avoid the damaging and manipulation email message content.
- Use and follow the legal procedure limit the disclosure of the email.
- Implement the measures to simplify the disclosure of email where it needed.
- Make use of the system which prevents the falsification of content and enhans the reliability of the email as evidence in court.
Challenges Faced in Extraction of Emails Admissible as Evidence in Court
In this section, we will discuss some key challenges that are faced by forensic investigators at the time of investigation of a suspect’s email data, which can be used as legitimate evidence in court. These challenges include: Web Based Email Client Analysis, Authorship of an Email, Manage (N) Number of Cases, analysis of pornographic images existing in emails, and examine relationship between multiple suspects.
Traversing the Email Services Forensically
Let’s consider a situation in which, a culprit’s data is seized and analysis shows that both desktop based and web based email clients were used by the suspect to perform various illicit deeds. Now, at the time of email investigation, examiner is only able to carve out crucial evidence from desktop based email clients while data will remains undetected on the webmail account without the input of generous manual efforts. This imperfect approach of email analysis creates problem during the reporting of investigation performed due to incomplete procedures implemented. To overcome this issue the examiner needs an email analysis tool that fulfils the investigative requirements of both; desktop as well as web based email platforms.
Detecting Suspect Authorship
Another vital task for an investigator is to detect the authorship of an email account. To overcome this issue, examiner needs to follow a number of footsteps because there is no standardized solution of this problem. The lack of standard procedures that addresses to this issue creates a complexity during email investigation as a major amount of resources, time and efforts will be put into gaining authorized access of the account instead of evidence acquisition and analysis.
Manage Multiple Cases
During an investigation, forensic examiners deal with multiple cases for collaboratively analyzing email artifacts. To perform the task more professionally and effectively investigators need Management of Case. Mainly managing of case involves; Creation of case, management of already running cases and further manipulations. An investigator can perform these entire three tasks and other required management tasks with the help of an email analysis tool programmed to handle such trivial tasks of not only managing multiple cases but also representing them in the court of law without much ado.
Investigation of Objectionable Pornographic Image
Email communication is a fast growing field in digital media. And with the advancement in technology, cyber criminals are also becoming more resourceful in their phishing, spamming, cyber bullying and pharming activities. Staling and sharing of personal information like images through email has become a fast constituent of cybercrime. Forensic investigation of sharing of pornographic images using email poses as a new challenge for investigators due to the feasibility of embedding images within attachments which further helps in concealing them.
Detect Relationship Among Multiple Suspects
All investigations require an in-depth analysis of the suspect’s emails to create a comprehensive and organized case file. Analysis of the link between users and domains plays an important role in examination of criminal entities performed by a culprit. In simple words, link based analysis provides detailed information that is shared between multiple suspects in a crime. It is mainly based on graph theory and to examine and extract evidence, an investigator needs the best link analysis tool that is automated to generate existing links (between users/domains) for further simplification of examination.
After the in-depth R & D of issues that are faced by investigators during an investigation, our aim is to provide a forensically sound technology for the same. A technology that can examine, analyze and extract evidence from email artifacts. One of the major solutions that
is currently helping Forensicators in carving evidence from emails and help them win cases in the court of law is – One stop solution; “MailXaminer”.
Carve Evidence from Email Clients Using MailXaminer
The tool can analyze evidence from both; desktop-based as well as web-based email client applications. Investigators can also access other crucial features of the forensics software like; link analysis, case management, skin tone analysis, export option, etc., that proves greatly helpful in an investigation. Gathering of complete email evidence and creation of well-informed case report also plays a major role in winning the case
The very first need of investigators is to manage the multiple case repositories. Thus, MailXaminer offers a proficient option to manage the complete case report in detail. And whic help the investigators to extract court admissible emails as evidence.
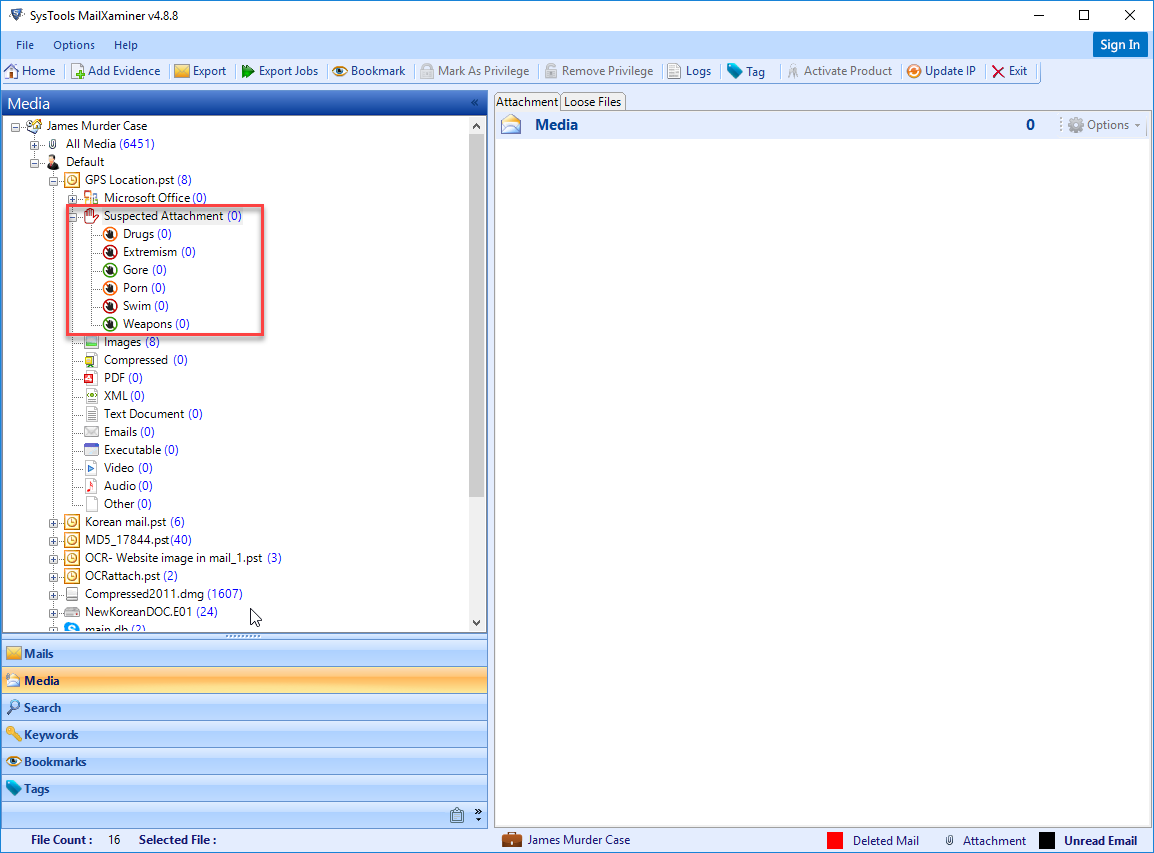
Skin Tone Analysis is one of the most unique features of the software. Using this feature, investigator can easily analyze the presence of objectionable images in the emails.
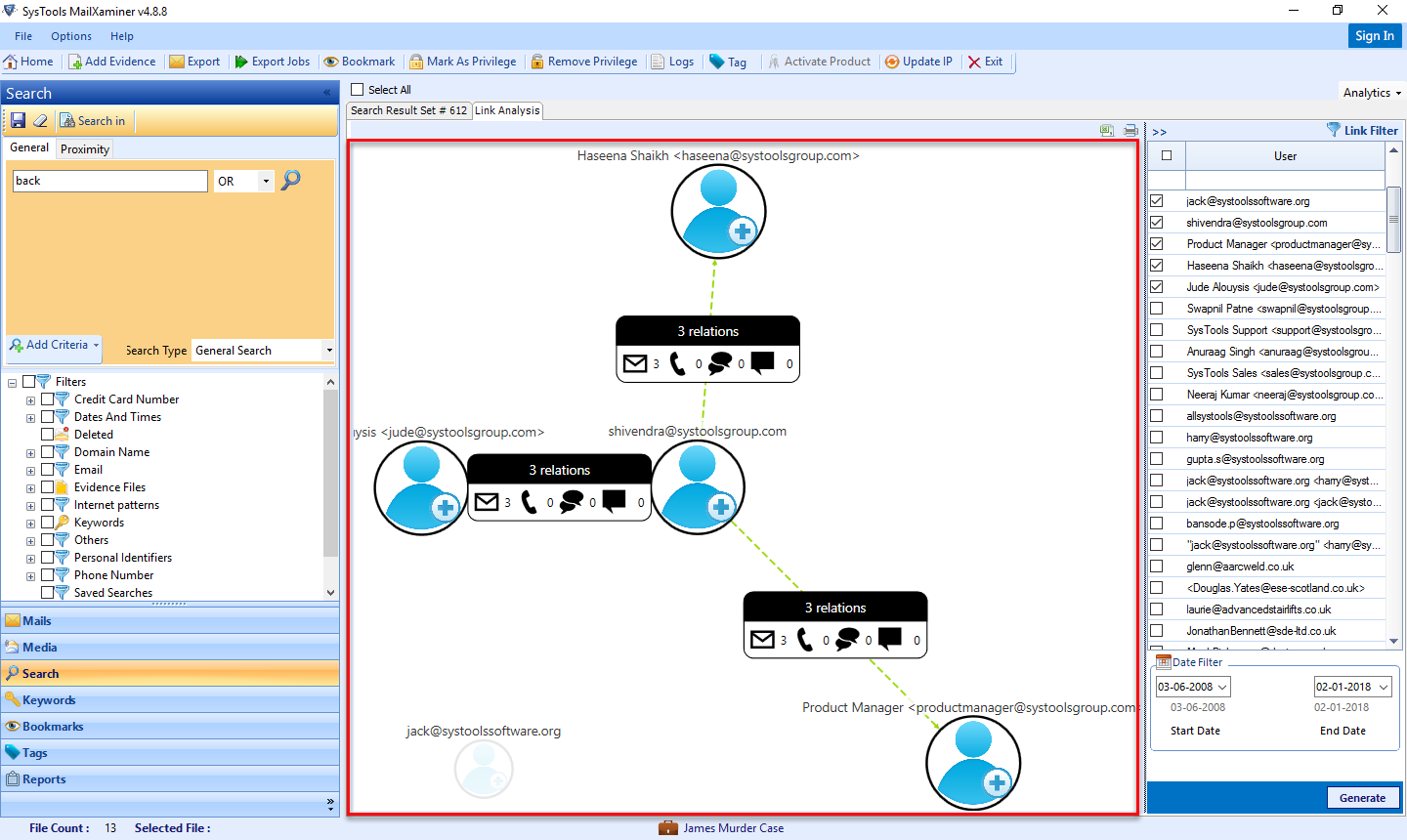
Link Analysis network chart helps the investigator to understand the number of suspects involved in a crime and how they are related to each other. This will help to how the facts are related on the basis of it investigators can extract and present electronic evidence in court.
MailXaminer is the most versatile and robust email analysis software that guides investigators in carving out the emails admissible as evidence in court and create a complete report of an entire case from its management, to analysis and findings, before representing the email evidence in court as an appropriate evidence.

